An electronic bank flow authenticity identification method and device
A technology of electronic banking and running water, applied in the fields of instruments, finance, data processing applications, etc., can solve the problem that the authenticity of electronic bank running water is not easy to determine, and achieve the effect of saving economic costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
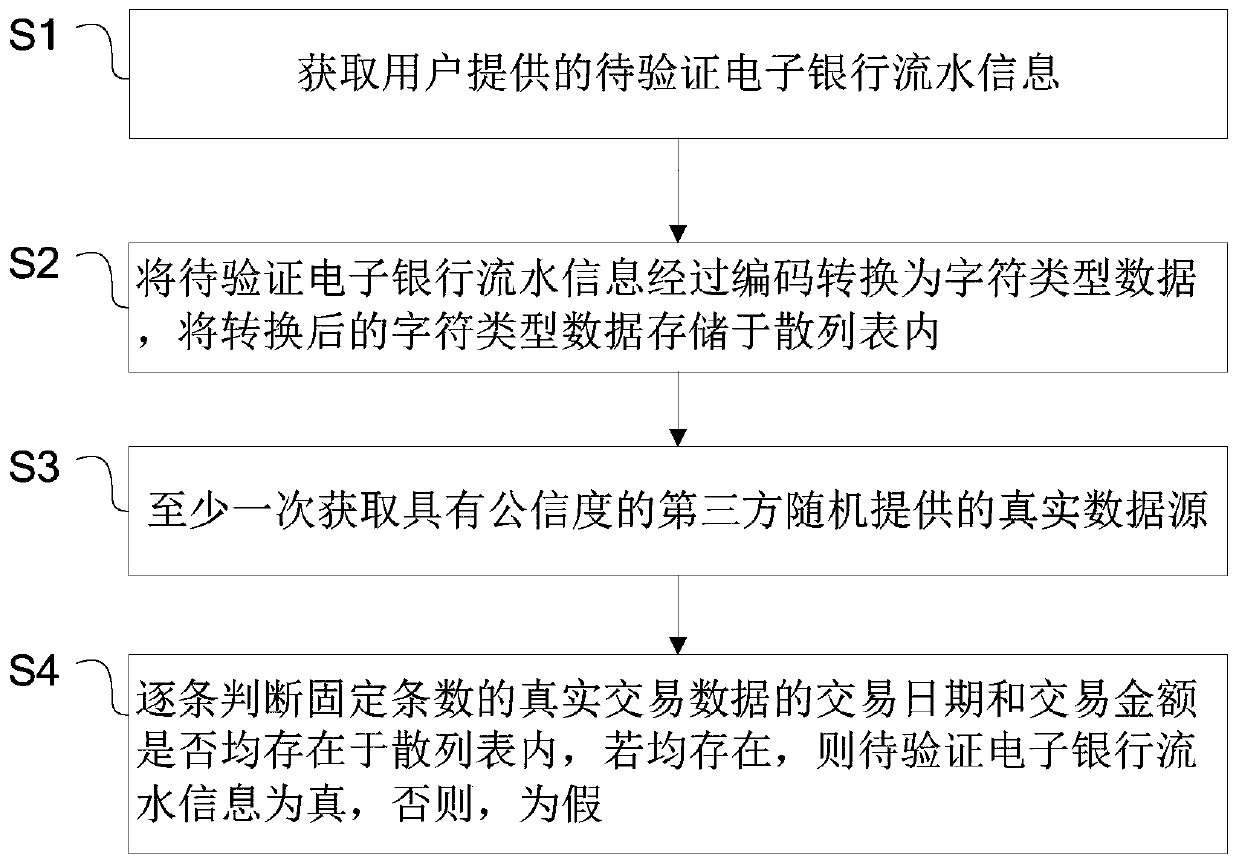
[0043]Because it is very difficult to determine the authenticity of the electronic bank statement, this application provides a method for identifying the authenticity of the electronic bank statement. The flow chart is as follows figure 1 As shown, it specifically includes the following steps.
[0044] S1: Obtain the electronic bank statement to be verified provided by the user.
[0045] Among them, the electronic bank statement information to be verified is the data information including the transaction date and transaction amount within the designated bank account and within the designated time period.
[0046] S2: Convert the electronic bank flow information to be verified into character type data through encoding, and store the converted character type data in the hash table.
[0047] A hash table (Hash table, also called a hash table) is a data structure directly accessed according to the key value (Key value). In this example, the key value of the list in the hash table...
Embodiment 2
[0070] Based on Embodiment 1, this example provides a device for identifying the authenticity of electronic bank flow, including:
[0071] The first acquisition module is used to obtain the electronic bank flow information to be verified provided by the user, and the electronic bank flow information to be verified is the data information including the transaction date and the transaction amount of the designated bank account and the designated time period;
[0072] The processing module is used to encode and convert the electronic bank flow information to be verified into character type data, and store the converted character type data in a hash table, wherein the key code value of the list in the hash table is the transaction date, list The content of is all transaction amounts corresponding to the transaction date;
[0073] The second acquisition module is used to acquire at least one real data source randomly provided by a third party with credibility, the real data source ...
Embodiment 3
[0089] Based on Embodiment 1, this example provides a device for identifying the authenticity of electronic bank flow, including:
[0090] processor;
[0091] memory for storing instructions executable by the processor;
[0092] The processor is configured as:
[0093] Obtain the electronic bank flow information to be verified provided by the user, the electronic bank flow information to be verified is the data information including the transaction date and transaction amount within the designated bank account and within the designated time period;
[0094] The electronic bank flow information to be verified is encoded and converted into character type data, and the converted character type data is stored in a hash table, wherein the key value of the list in the hash table is the transaction date, and the content of the list is the transaction date All corresponding transaction amounts;
[0095] Obtain at least one real data source randomly provided by a credible third part...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com