Method, device and computer storage medium for wirelessly unlocking electronic equipment
An electronic device, a wireless technology, applied to a method of wireless unlocking equipment, devices and computer storage media, can solve the problems of inability to meet the unlocking requirements, achieve the effect of eliminating the possibility of pairing and enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
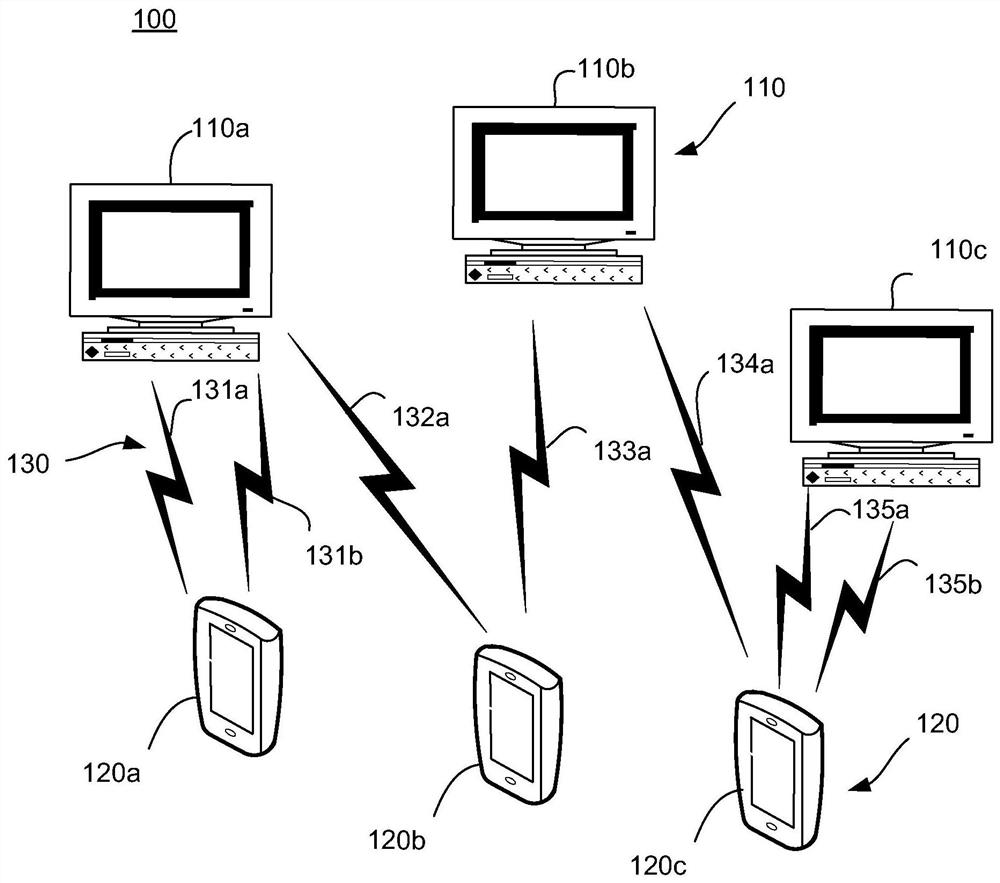
[0060] This example can be found in figure 1 The exemplary implementation environment shown, or variations thereof.
[0061] In this embodiment, the portable electronic device 120 is selected to initiate a scan in the master mode to call the operable device 110 , while the operable device 110 is in the slave mode to initiate a broadcast and wait for the portable electronic device 120 to call. Once the connection 130 is established between the two, the portable electronic device 120 can unlock the operable device 110 .
[0062] Portable electronic device 120 needs to be able to obtain the address of operable device 110 in order to initiate a scan. To this end, the portable electronic device 120 is first paired with the operable device 110 , so as to obtain its address from the operable device 110 .
[0063] Figure 4 It is a flowchart of device pairing according to an embodiment of the present invention. refer to Figure 4 As shown, the pairing process includes the followi...
no. 2 example
[0096] In this embodiment, different from the first embodiment, before step 613, when the signal strength between the portable electronic device and the operable device (for example, the signal strength of the transmitted first identification) reaches the first threshold Only proceed to step 613 . Figure 7 It is a flow chart of device unlocking according to another embodiment of the present invention. refer to Figure 7 As shown, it may be judged in step 612c whether the signal strength reaches the first threshold (for example -60dB), and if so, proceed to step 613, otherwise return to step 611 to re-scan. Setting the signal strength ensures that the portable electronic device is close enough to the operable device to initiate a connection.
[0097]In a preferred embodiment, while maintaining the connection, the signal strength can also be monitored and judged, and unlocking is performed only when the signal strength further increases to a sufficient level. A further incre...
no. 3 example
[0104] This example can be found in figure 1 The exemplary implementation environment shown, or variations thereof.
[0105] In this embodiment, the portable electronic device 120 is selected to initiate a scan in the master mode to call the operable device 110 , while the operable device 110 is in the slave mode to initiate a broadcast and wait for the portable electronic device 120 to call. Once the connection 130 is established between the two, the portable electronic device 120 can unlock the operable device 110 .
[0106] Portable electronic device 120 needs to be able to obtain the address of operable device 110 in order to initiate a scan. To this end, the portable electronic device 120 may receive an input of one or more authorized operable device identifiers and store them in a list of authorized operable device identifiers. refer to figure 1 and image 3 As shown, each portable electronic device 120 (such as 120a, 120b, and 120c) can receive an identifier of an a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com