Methods of Realizing Privacy Protection in Blockchain
A privacy protection, blockchain technology, applied in the field of privacy protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0044]
[0045]
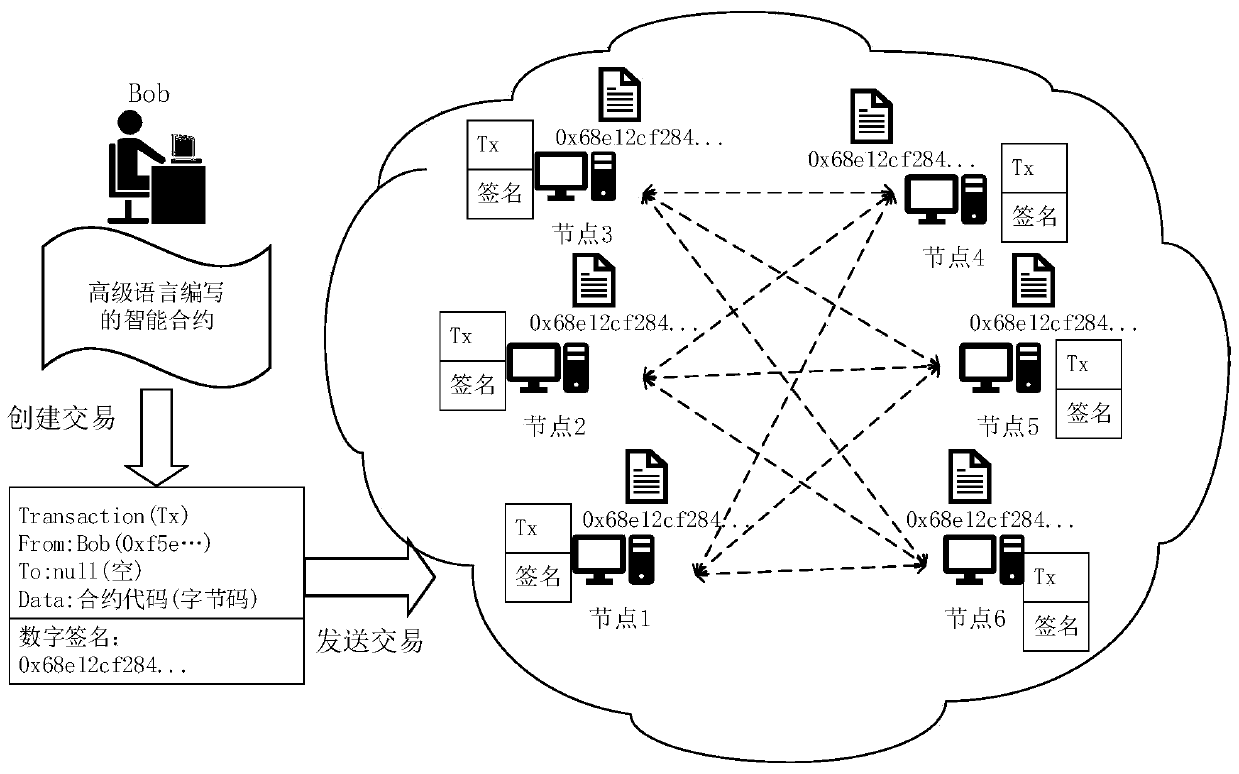
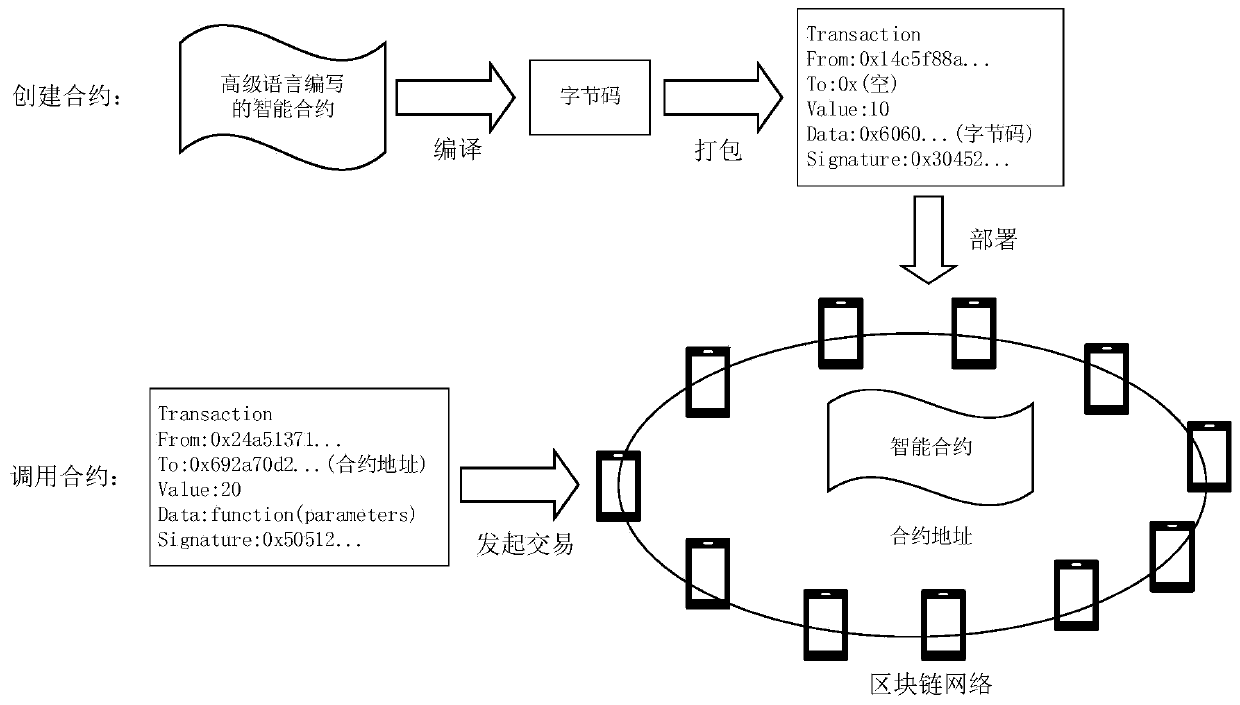
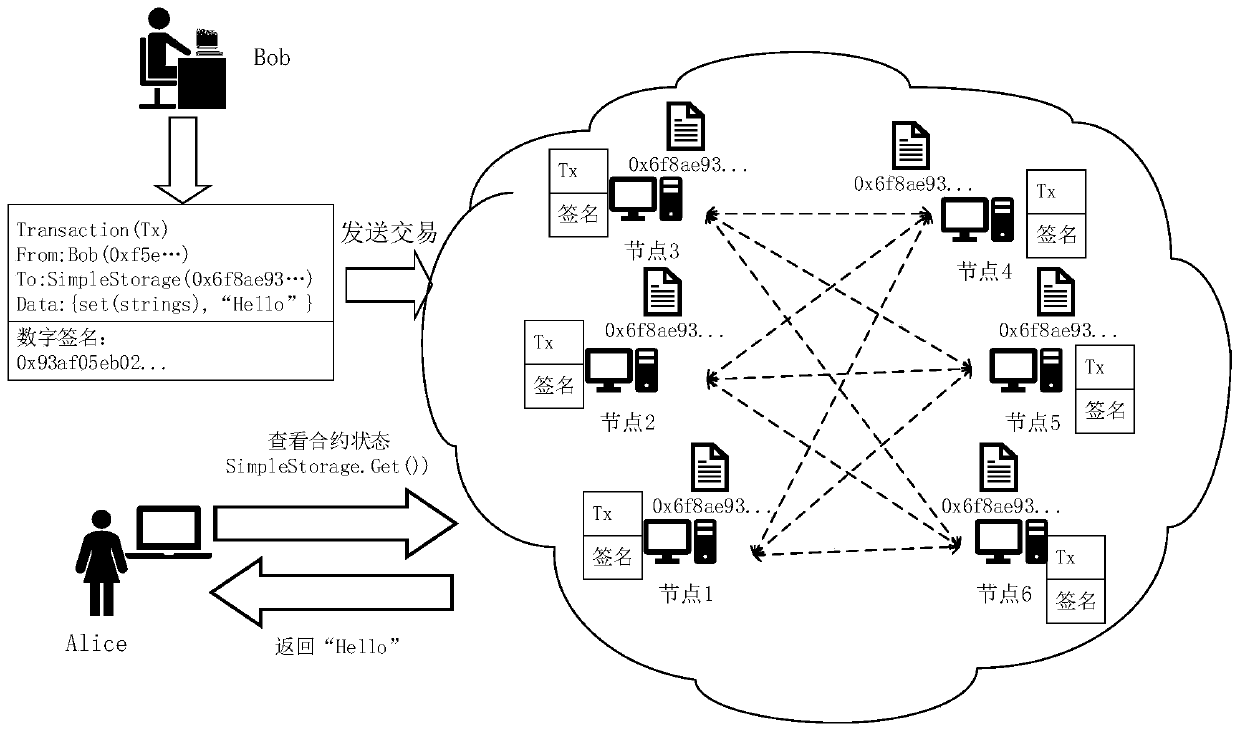
[0046] Generally, after this contract is deployed on the blockchain, the storage state corresponding to the state variable "balance" is plain text, and anyone can see its state, without privacy protection settings and capabilities. If users want to protect state privacy, the current zero-knowledge proof and homomorphic encryption solutions need to rewrite this contract to make the state variable "balance" encrypted and protected, and it needs to support all operations of balance in the encryption domain. . Generally, this kind of encryption method is complicated in operation, and it is difficult to design a suitable algorithm to support it in the encryption domain. In some solutions that combine blockchain and TEE, in order to achieve privacy protection, all contract states of smart contracts are stored on the blockchain as data that requires privacy protection. The blockchain is a data set stored in a database of a node and organized by a specific logic. Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com