Method, system, device and equipment for verifying credibility of alliance chain
A verification method and reliability technology, applied in the information field, can solve problems such as poor experience and achieve the effect of improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
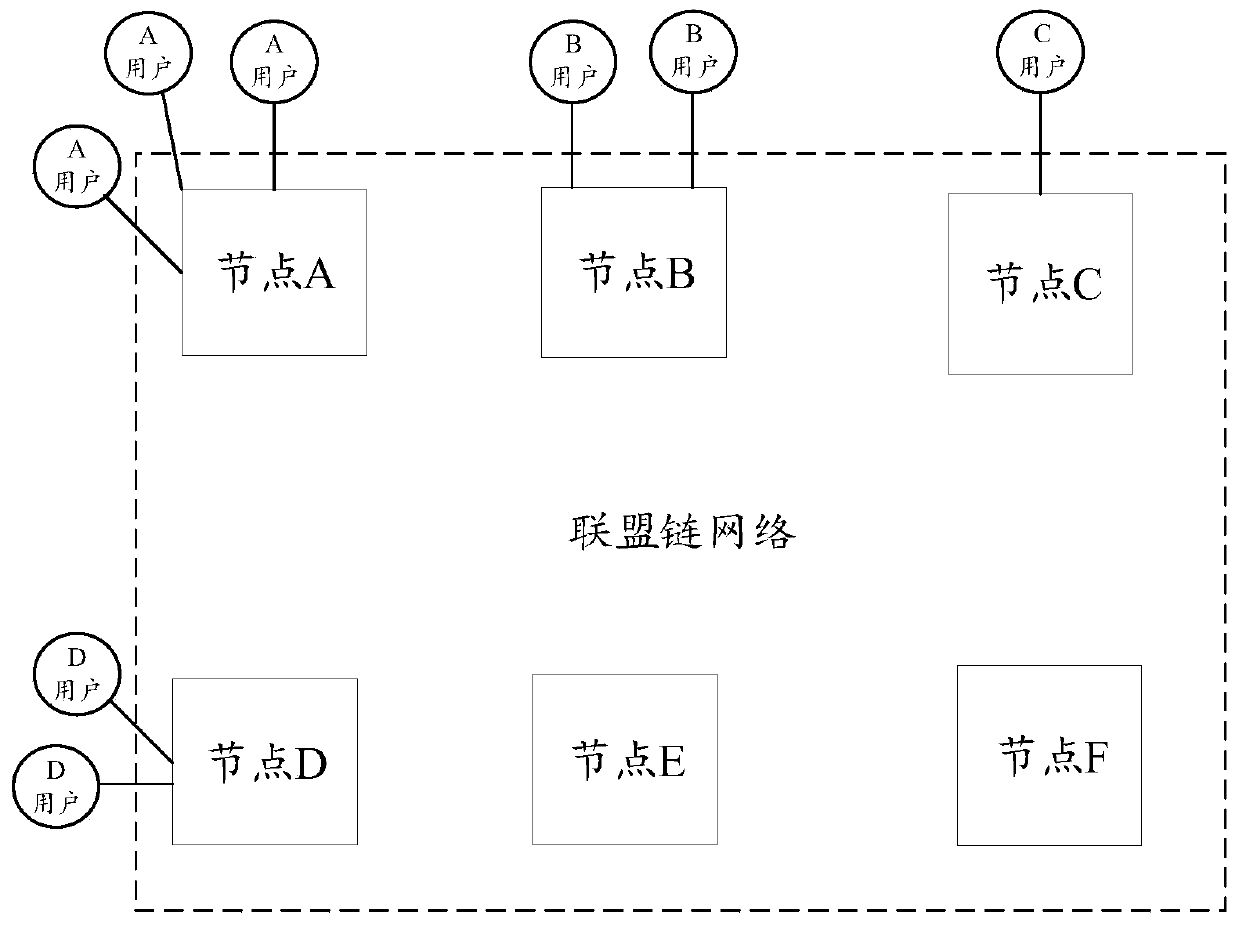
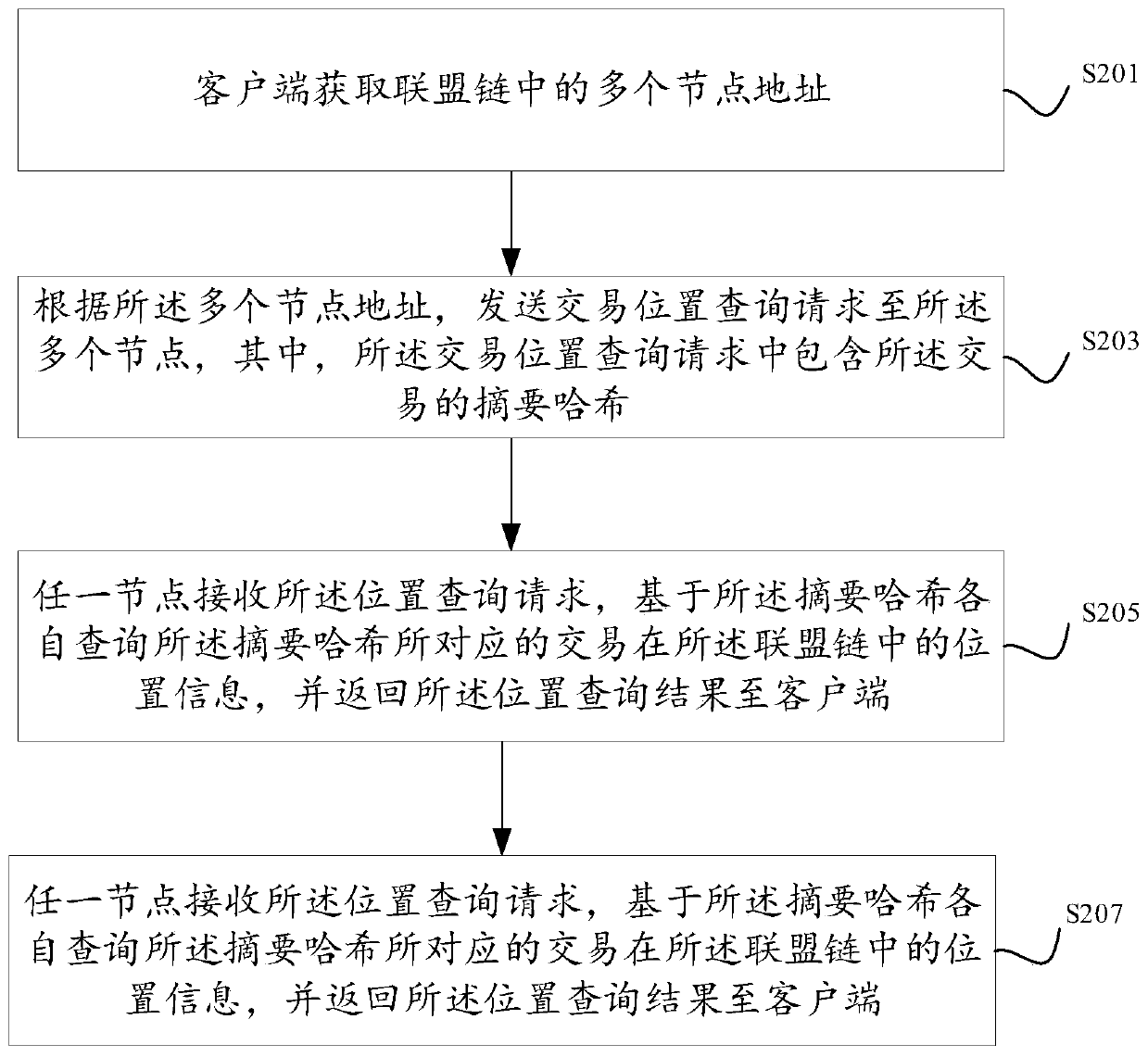
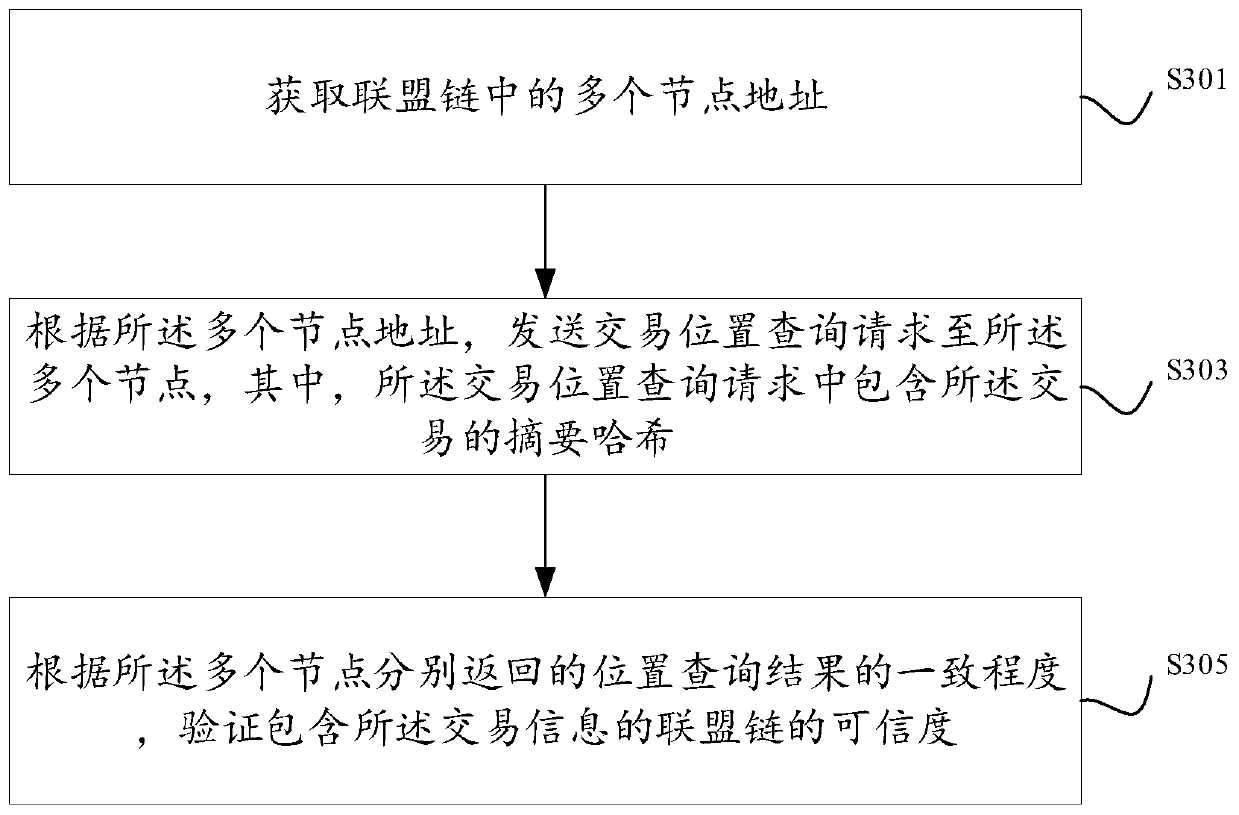
[0061] In a specific implementation, the client obtains multiple node addresses in the consortium chain. The client can randomly obtain multiple node addresses in the consortium chain. Randomly obtaining node address verification can make the verification result more fair on the one hand. On the other hand, it can also make the user's request evenly flow to each node, so as to avoid the heavy load of some nodes with many users. Alternatively, the client obtains multiple node addresses in the consortium chain that include the address of the docking node. In this way, the user can first select a batch of node addresses, and then add the addresses of the docking nodes. When adding a docking node for verification, the returned result also includes the verification result of the docking node, which can make the verification more targeted and improve user experience.
[0062] In a specific implementation manner, the user may also send a simple payment verification SPV request to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com