Attack source tracing method based on frit
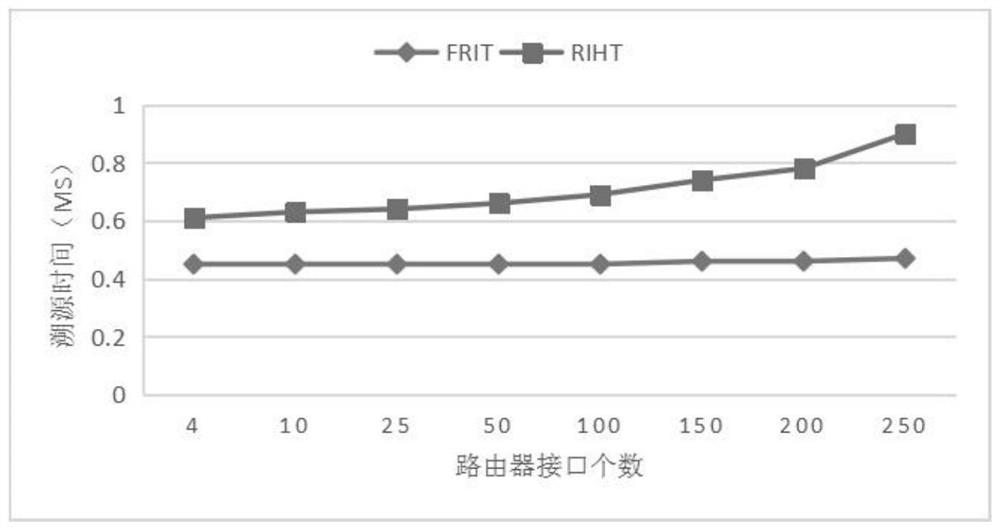
A data packet and router technology, applied in digital transmission systems, data exchange networks, electrical components, etc., can solve the problem of high logging time, reduce logging time, quickly and accurately trace the source, and reduce computing overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
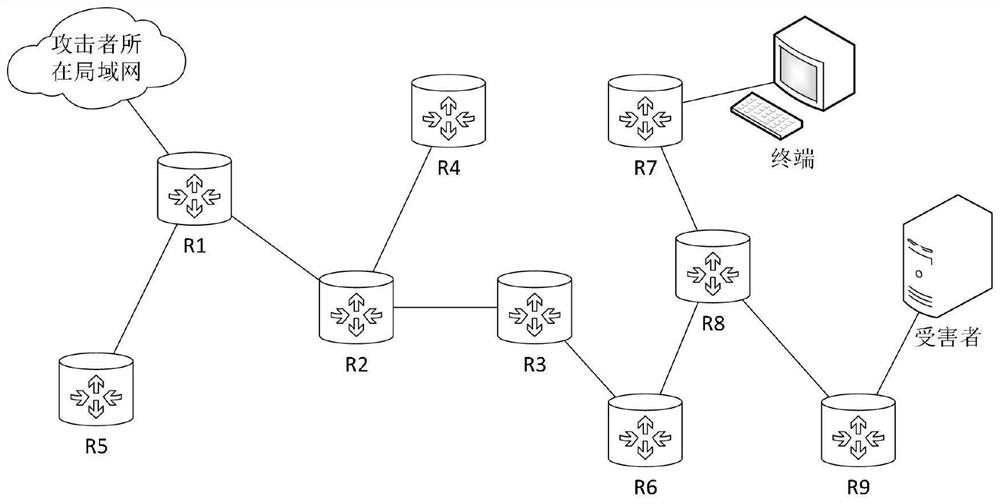
[0030] figure 1 Topology is a schematic view of the invention, based on figure 1 Brief description of the workflow of the present invention:
[0031] (1) labeling process
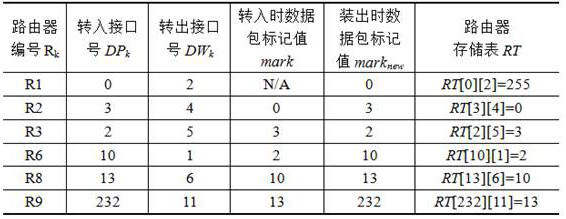
[0032] Table 1 shows the values of the data packet stored on the router and changes the attack path during forwarding tag value. Suppose the attacker to attack a packet sent from the router R1 is connected in a local area network, the attack packets from entering R1 is 0, 2 roll-out, i.e. UP 1 = 0, mark = UP 1 , DW 1 = 2, i = UP 1 , J = DW 1 , R1 because this is the border router routing process is provided RT [I] [j] = 255, i.e., RT [0] [2] = 255, then transmitted to the router R2 of the core router the packet interface 2; R2 is received by a packet from the router 3 and coming from the interface 4 forwards the packet out of the interface, this packet flag value 0, then, into the relevant variables obtained. At this time, the interface number of the received packet marknew 3, i.e. marknew = 3, and forward t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com