SILK security steganography method based on LSF coefficient statistical distribution characteristics
A technology of statistical distribution and statistical analysis, applied in speech analysis, instruments, etc., can solve the problem of SILK speech steganography method, etc., to ensure the effect of hearing concealment and good security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] In order to facilitate those of ordinary skill in the art to understand and implement the present invention, the present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the implementation examples described here are only used to illustrate and explain the present invention, and are not intended to limit this invention.
[0019] At first the technical term that the present invention adopts is described as follows:
[0020] 1) Compressed audio: Refers to audio that has undergone lossy compression, such as MP3, WMA, and AMR are all lossy compressed audio.
[0021] 2) Cover: Carrier audio, that is, audio without embedding secret information.
[0022] 3) Stego: Confidential audio, that is, audio with secret information embedded.
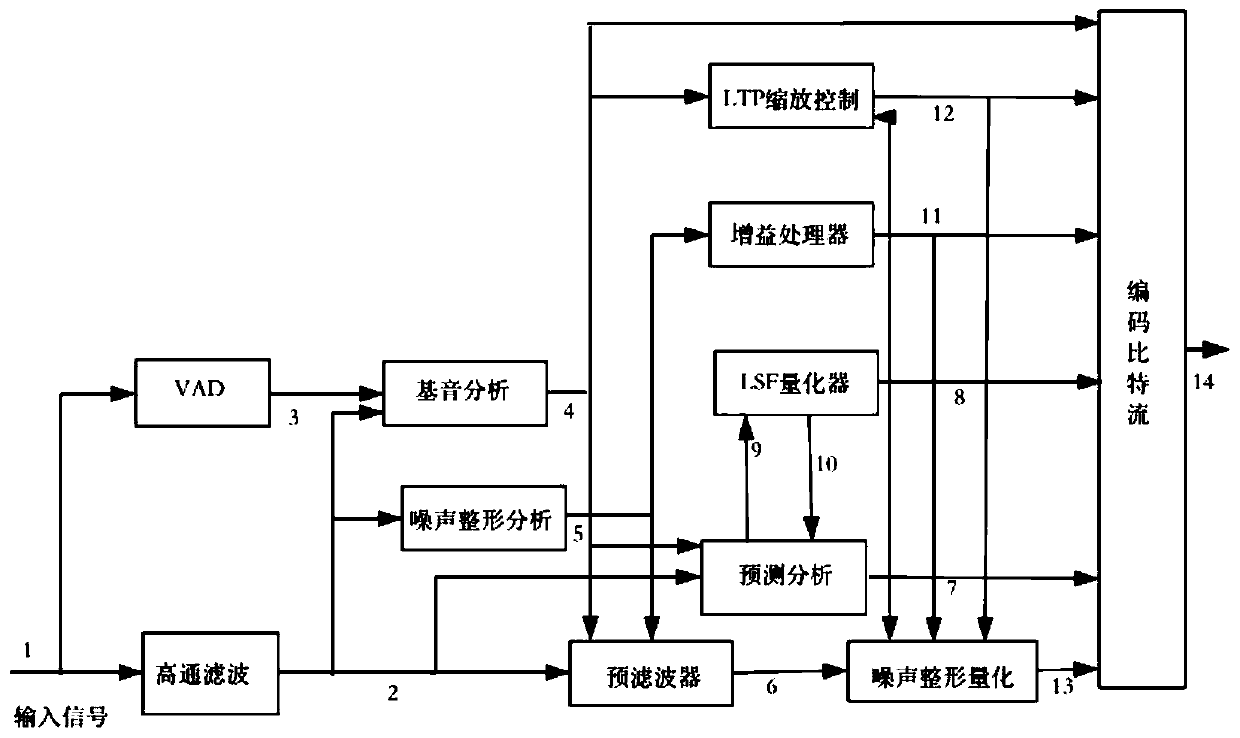
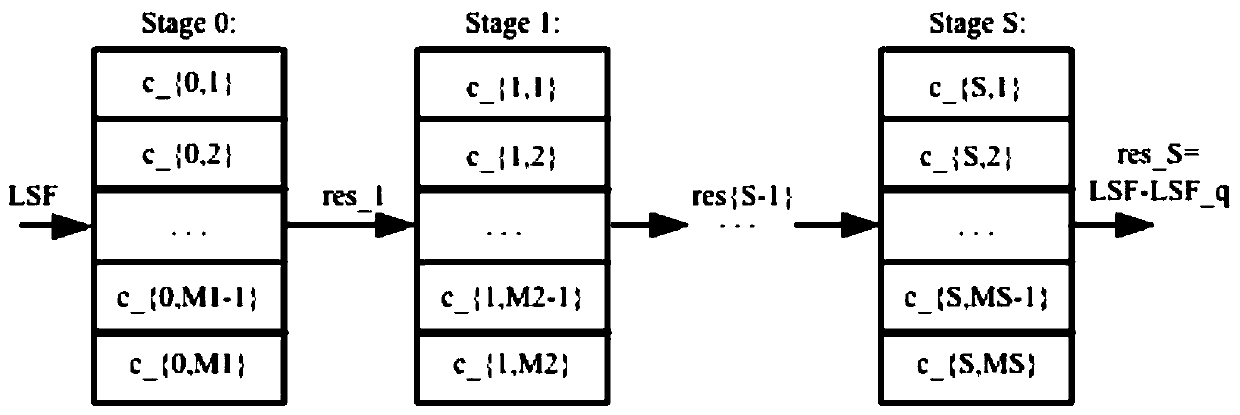
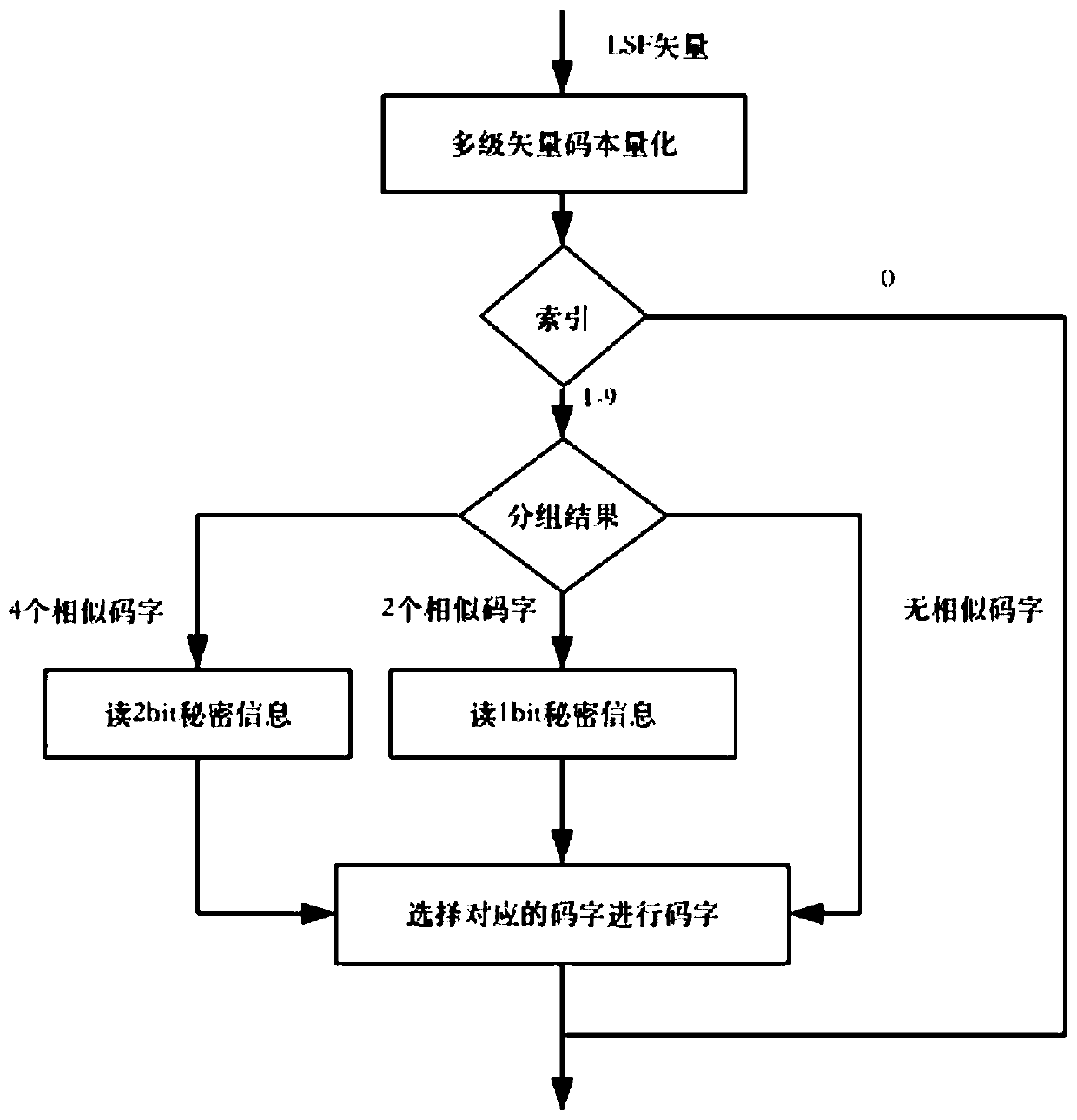
[0023] 4) LPC coefficient: each frame of AMR speech includes 4 subframes, the first subframe and the second subframe form a subframe group, and the th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com