System and method for programming and/or management of core network slices
A network slicing and management system technology, applied in the field of programming and/or managing mobile wireless networks, can solve problems such as low efficiency, and achieve the effect of preventing network errors, preventing damage, and preventing resource allocation problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
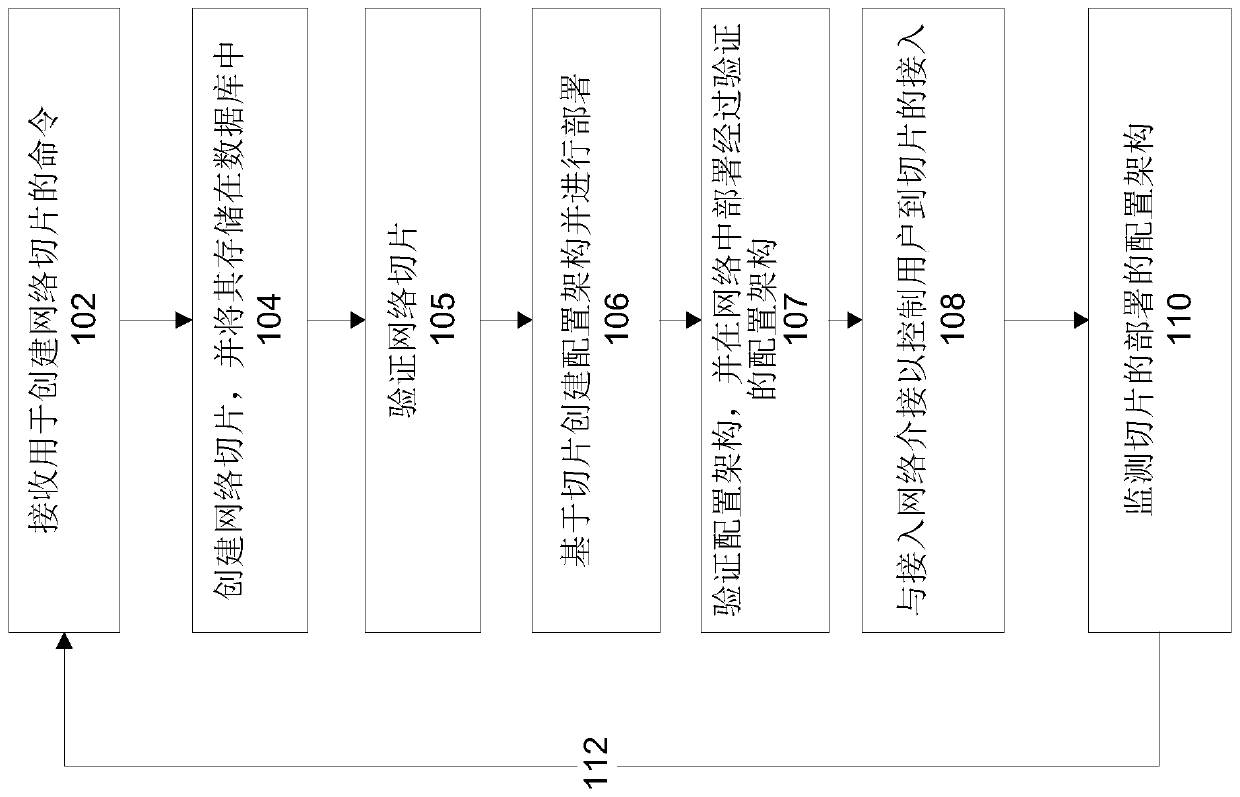
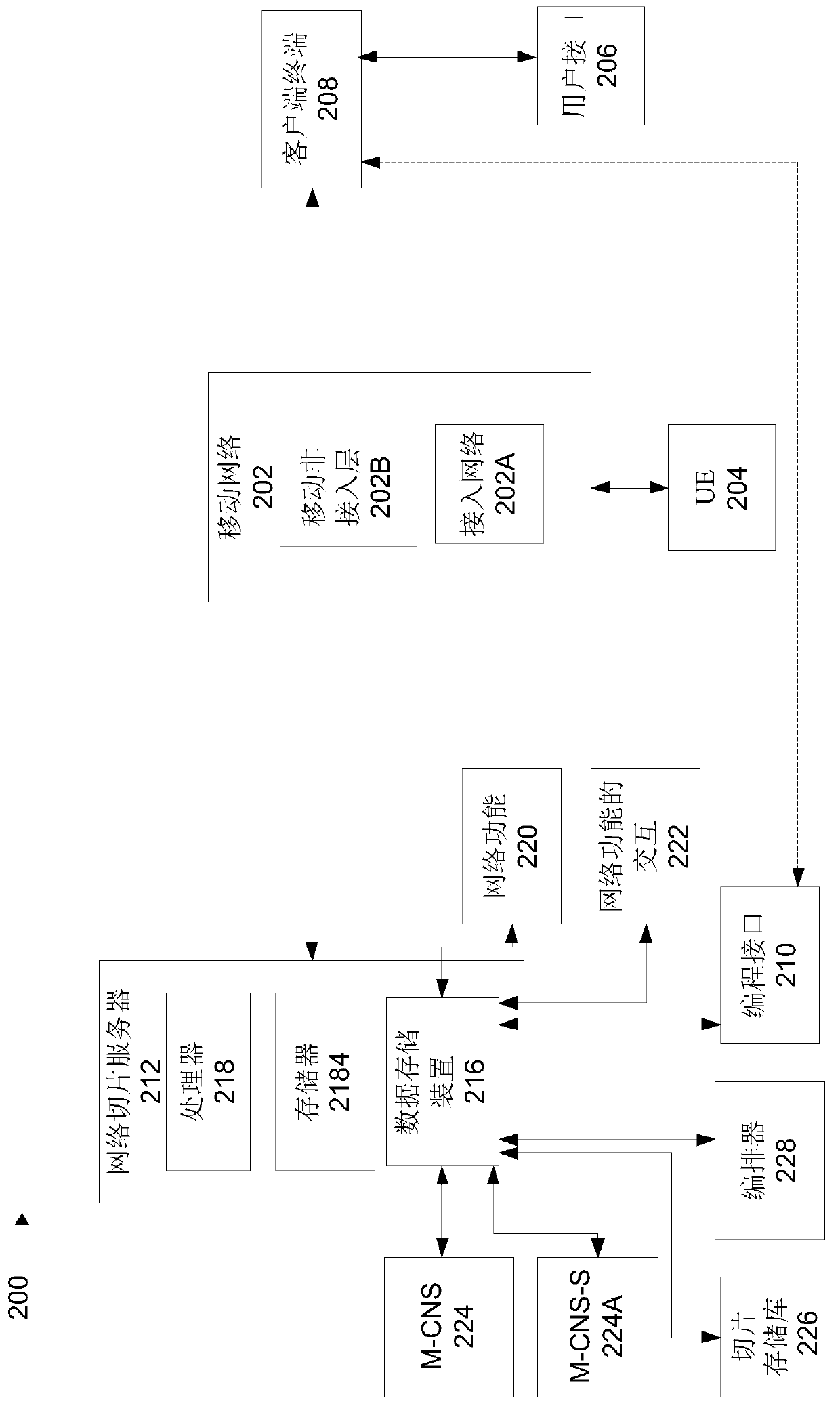
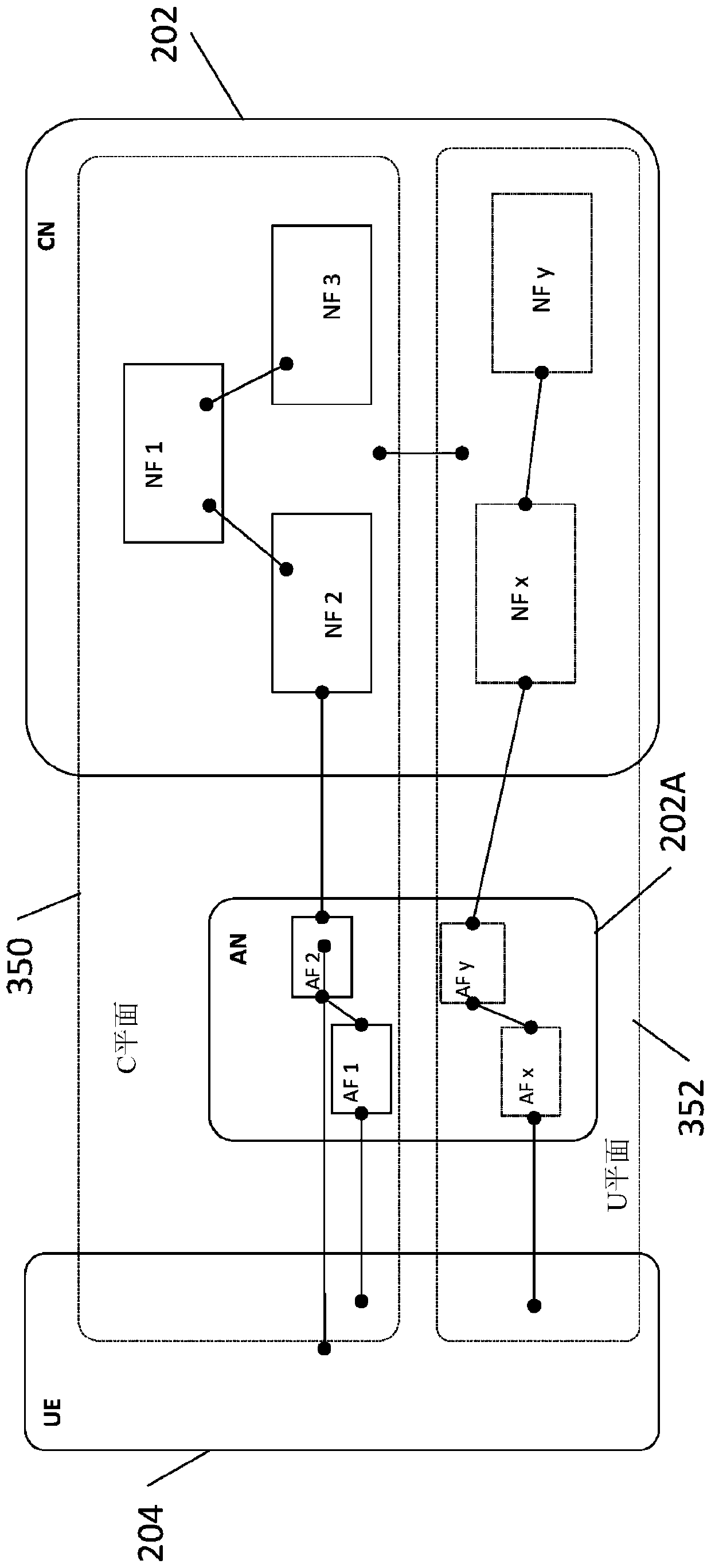
[0041] The present invention, in some of its embodiments, relates to network management, and more particularly, but not exclusively, to systems and methods for programming and / or managing mobile wireless networks.
[0042] An aspect of some embodiments of the invention relates to an apparatus (e.g., a network slice server), a system (also referred to herein as a network slice programming and management system), a method (e.g., implemented as a code instructions executed by one or more processors in the device), and / or a computer program product that defines slices of the mobile communication network as groups of logical network slices. Each network slice is associated with a set of logical network functions, which are optionally virtualized network functions. Each network function is dedicated to support a specific corresponding use for the user of the slice. Sliced network functions define architectures for specific purposes, eg, devices and / or applications, eg, real-time ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com