Method for realizing computer software protection based on network communication
A software protection and network communication technology, applied in the computer field, can solve problems such as tampering, and achieve the effect of preventing piracy and protecting software
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
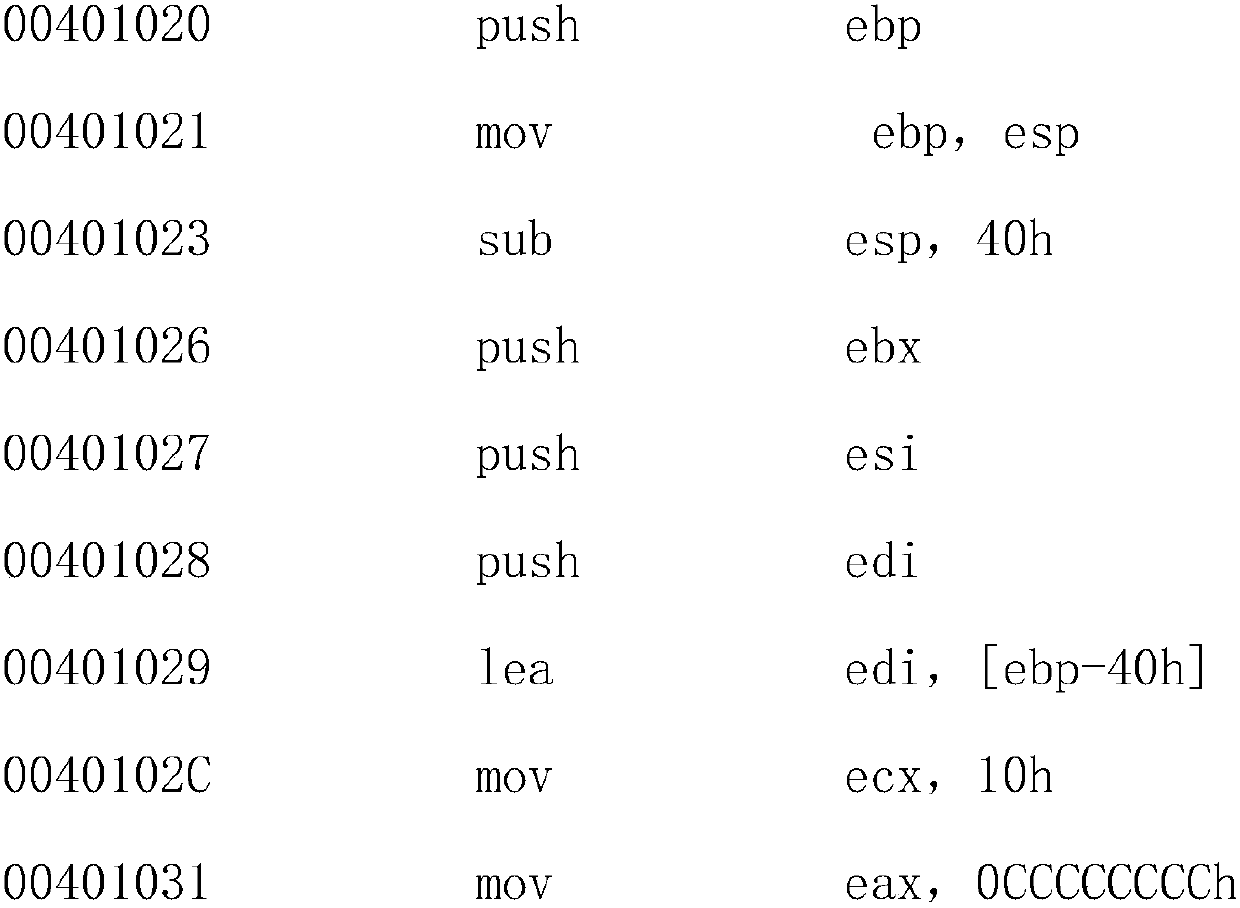
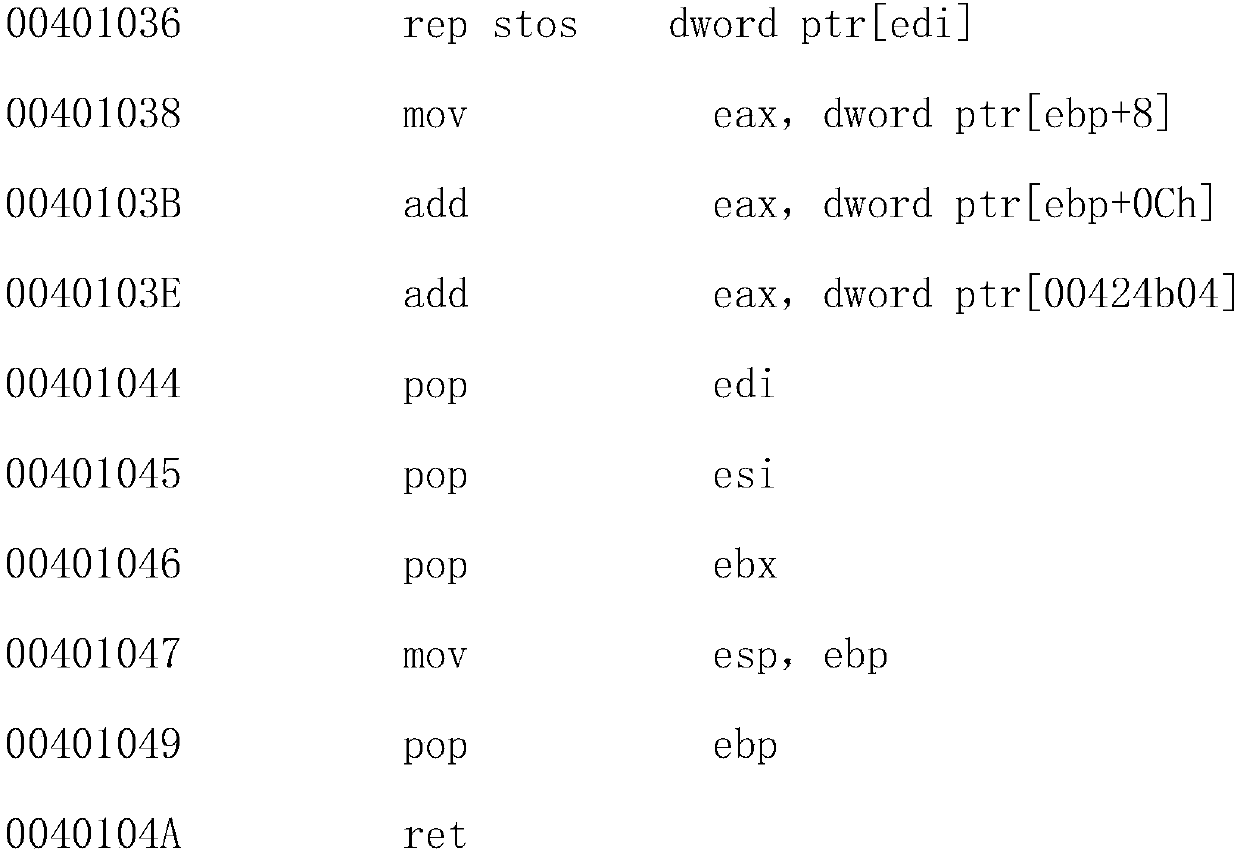
[0032] A method for realizing computer software protection based on network communication, comprising the following steps:
[0033] S1, setting module: the first device is used to set HOPT, DES, RSA and SHA algorithm, 2834 key and dynamic factor 1900 in the software, set the same HOPT, DES, RSA and SHA algorithm, 2834 in the information security equipment The key and dynamic factor 1900, when executing the transplanted code, trigger the dongle to execute the transplanted code. The dongle processor executes the transplanted code, and returns the execution result of the transplanted code to the target platform.
[0034] S2. Communication module: the second device is used to obtain software and information security equipment and after installing the software, when the software needs to be run, it establishes a connection with the information security equipment and communicates with the information security equipment for custom functions The loading method, the working mechanism o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com