Data transmission method and device and network node
A data transmission method and node technology, applied in the field of communication, can solve the problem that the interests of data or service providers cannot be truly protected, and achieve the effects of less transmission delay, improved security and reliability, and improved security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0191] This embodiment uses intelligent shared equipment and / or shared big data as technical scenarios to illustrate the technical solutions of the present application. This application scenario is only an example for understanding the technical solutions of the present invention, and the present invention includes but is not limited thereto. .
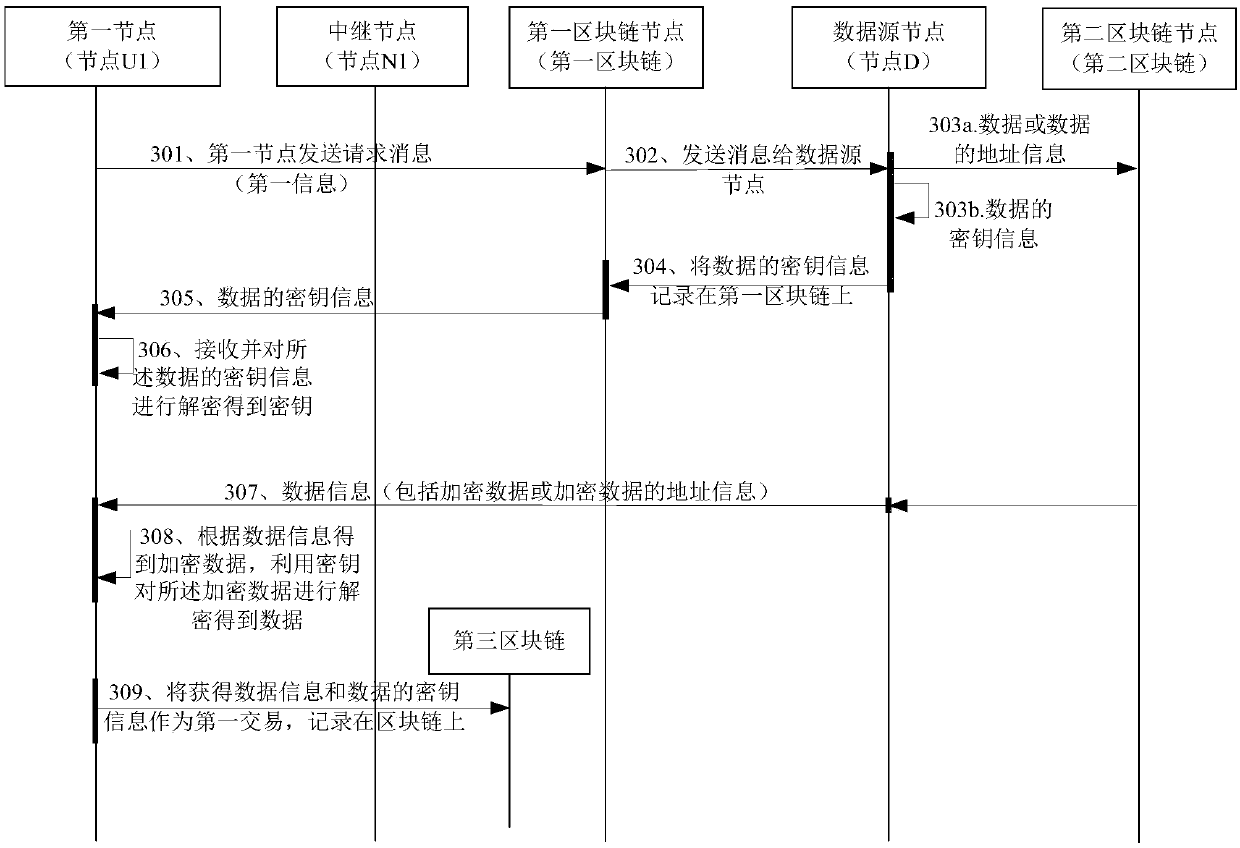
[0192] Such as image 3 As shown, the application scenario may include the following devices: node U1 (representing UE1), node N1 (representing Node1), node D (representing data source node Data source), one or more blockchains, and each blockchain has It consists of several blockchain nodes. This embodiment uses the above scenario as an example to illustrate the content of the invention, but the method provided in this embodiment includes but is not limited to the above scenario.
[0193] This embodiment provides a data access method, which specifically includes the following steps:
[0194] Step 301: A first node (for example, nod...
Embodiment 2
[0278] This embodiment provides a data transmission method, which can be used for nodes that do not apply for data access for the first time, for example, the first node initiates a process of data access to the blockchain network. This method can also be executed on the basis of Embodiment 1, that is, after the first node applies for accessing data for the first time, the first node in this embodiment initiates an access request for the same data. In addition, this method can also be executed independently, and the first node initiates a data access request to the blockchain node.
[0279] This embodiment describes in detail the first node's request to access the same data based on the method steps of the first node's first request to access data in Embodiment 1.
[0280] First, according to the description of Embodiment 1, the first blockchain is used to record key information of data. Specifically, the key information of the data has been recorded in the first blockchain a...
Embodiment 3
[0341] This embodiment also provides a data transmission method, see Figure 5 , the method includes three parts of the process, which are part A, part B and part C, wherein the method of part A describes the process of the first node (U1) requesting access to data, and the method of part B describes the process of the second node (U2) requesting access to data The process of , part C method describes the process of the third node (U3) requesting access to the data.
[0342] Among them, these three parts of the method flow can be executed independently, or combined in pairs, such as the combination of part A and part B, the combination of part B and part C, or the combination of part A, part B and part C. This is not limited.
[0343] The following describes and introduces the method steps of each part of the process in this embodiment.
[0344] Part A process
[0345] The method flow in part A describes the process of the first node U1 requesting access to data.
[0346] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com