Single sign-on method and device and computer readable storage medium
A single sign-on and logged-in technology, applied in the Internet field, can solve problems such as session insecurity, hidden dangers, and inability to achieve cross-domain, and achieve the effect of increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific example
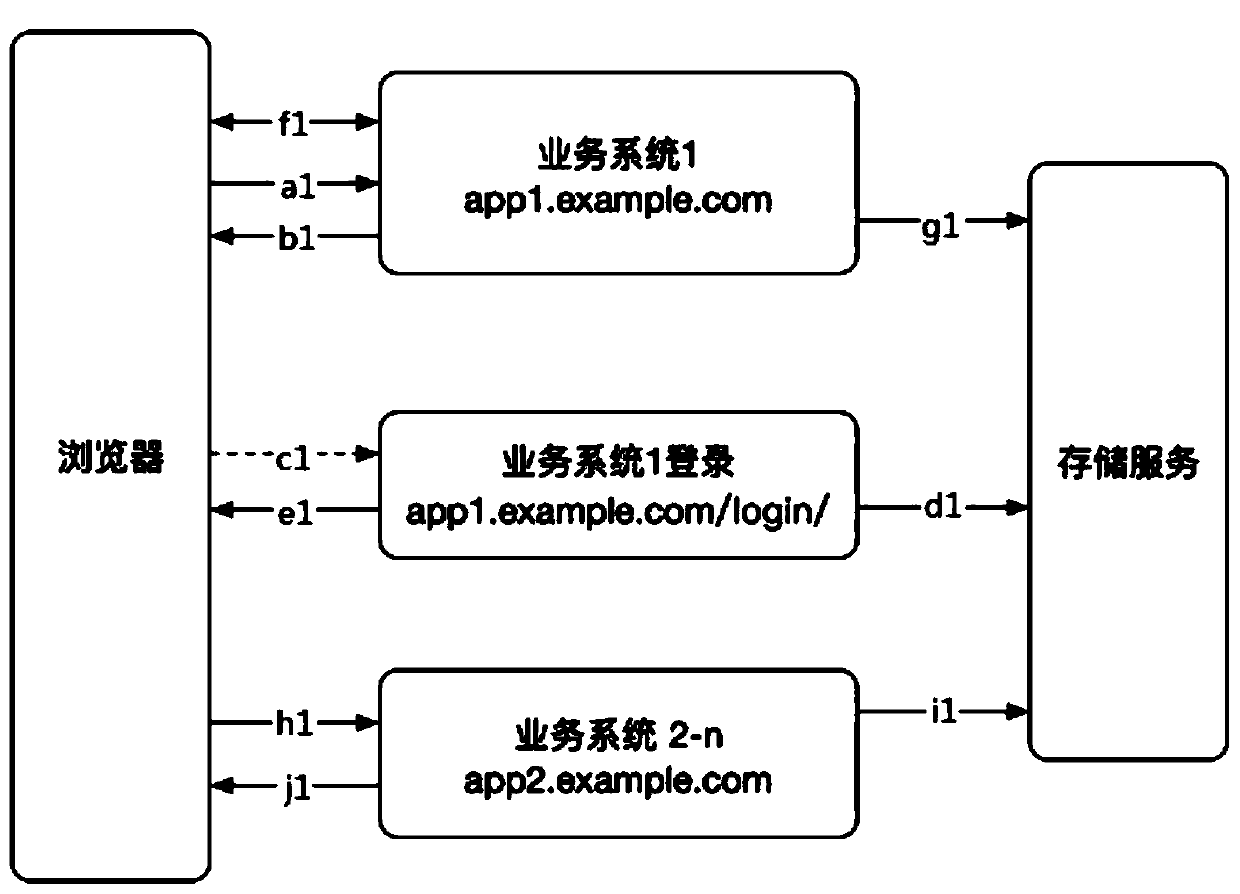
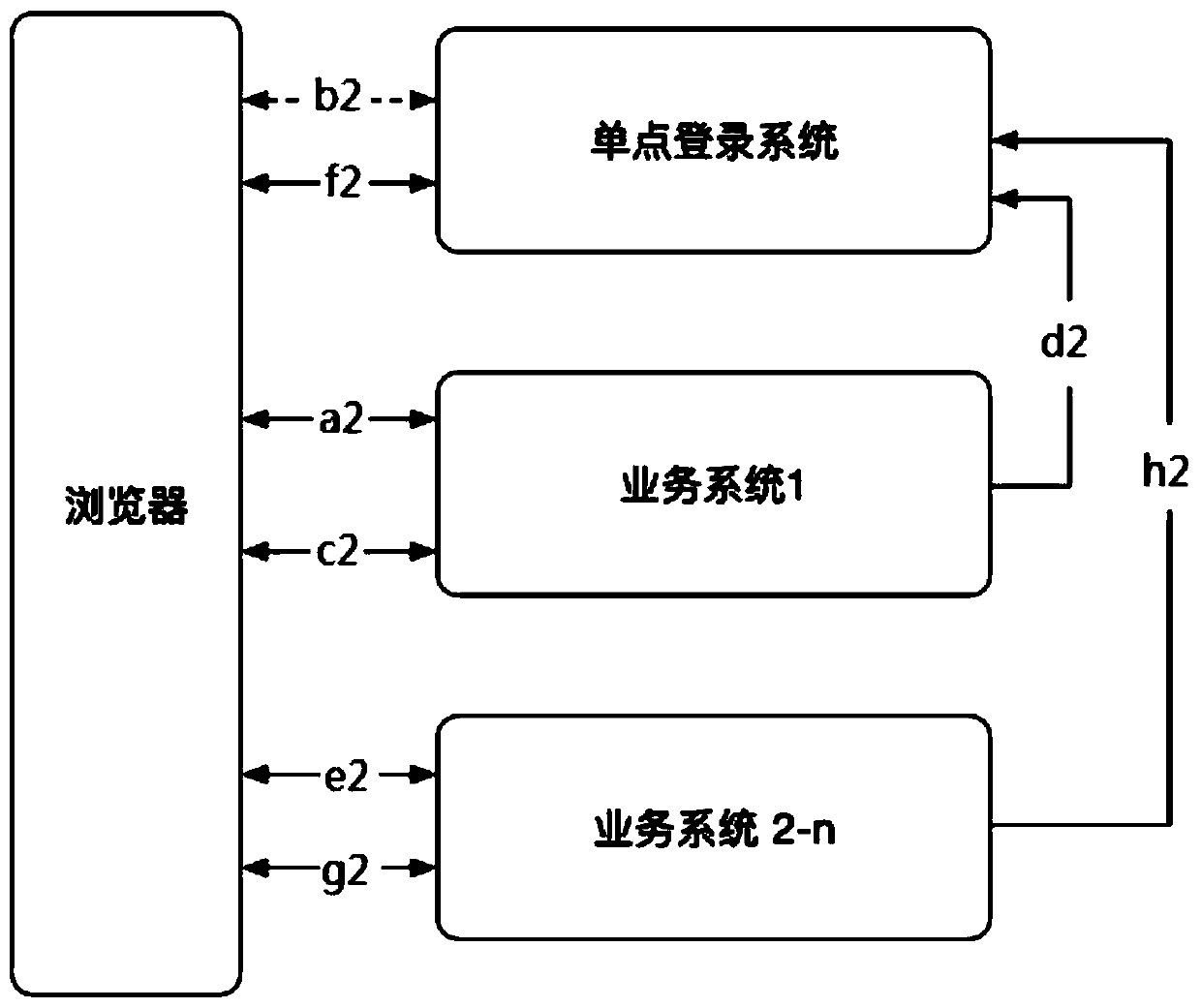
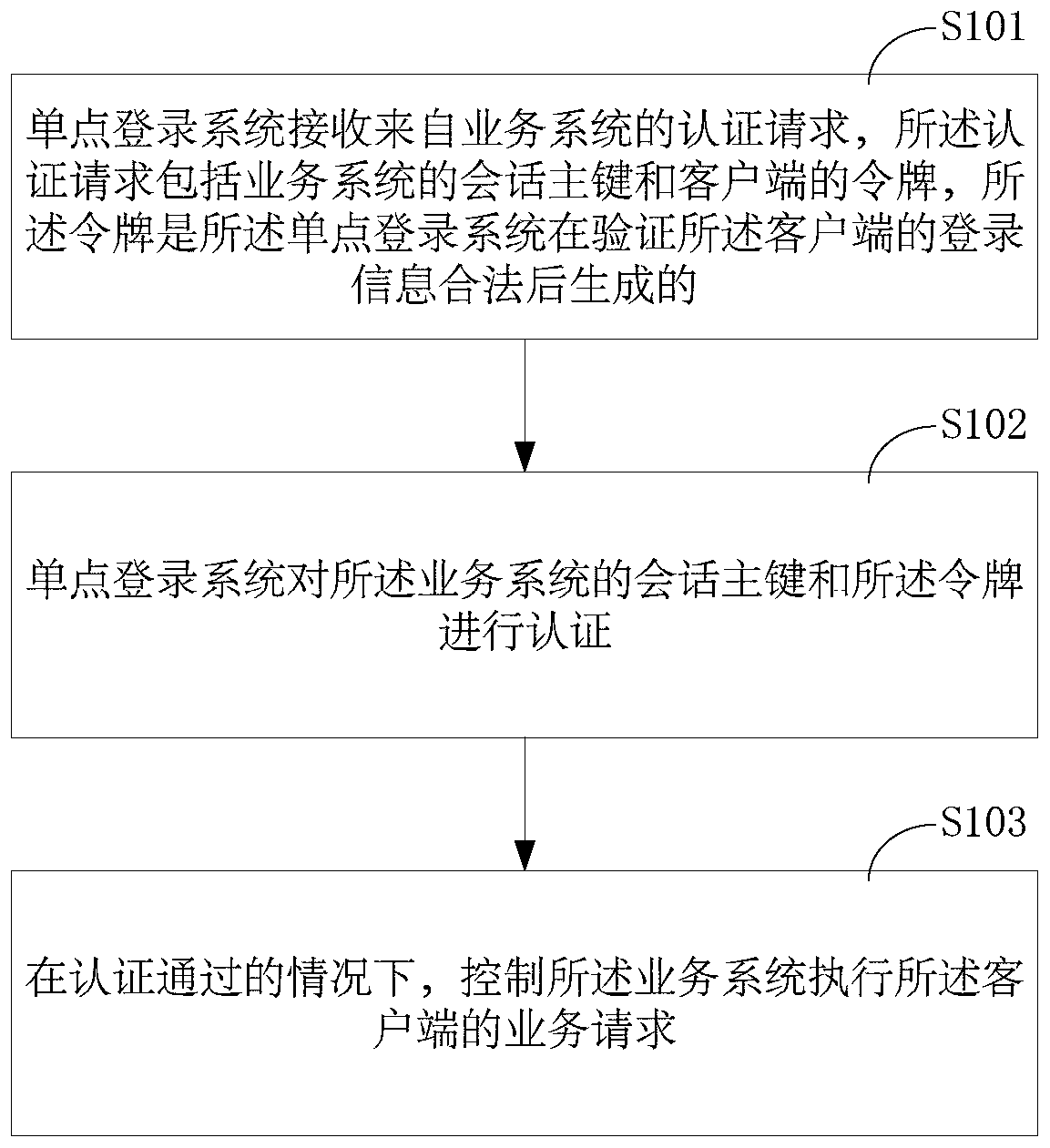
[0161] Such as Figure 9 Shown is a specific example process of the single sign-on method, including the following steps:
[0162] a: The client initiates a service request to the business system 1 through the browser. The business system 1 detects that the client is not logged in, and jumps to the single sign-on system with the session primary key of the business system 1.
[0163] The client issues a service request to the service system 1 through a browser. When the client visits for the first time, business system 1 will generate a session record for the client's browser, and the session record is stored in the database or cache service. This session record has a globally unique field as the session primary key (session_id_app1). Other information can also be stored in the session record, such as client ID, login mobile phone number and other information. Subsequently, the business system 1 makes an HTTP response, and the cookie of the response contains the session prim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com