Security monitoring system based on multi-feature change identification and working method thereof
A technology of security monitoring and working methods, applied in anti-theft alarms, electric alarms, voice analysis, etc., can solve the problem that monitoring methods cannot meet various monitoring needs, reduce the probability of misleading identification, increase Identify information sources and improve the effect of identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0050] refer to figure 1 as an example.
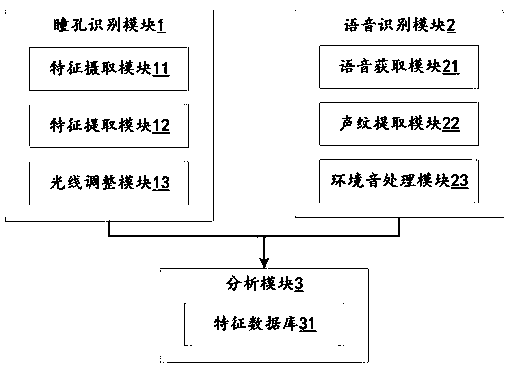
[0051] A security monitoring system based on multiple feature change recognition, including: a pupil recognition module 1 , a speech recognition module 2 , and an analysis module 3 .
[0052] The pupil recognition module 1 includes a feature capture module 11 , a feature extraction module 12 , and a light adjustment module 13 . The feature capture module 11 is used to capture the eye features of the identified person. The feature extraction module 12 is used to extract the pupil feature of the identified person. The light adjustment module 13 changes the light value in the recognition area. The feature extraction module 12 is connected to the analysis module 3 , and the feature extraction module 12 outputs the through-hole features of the identified person to the analysis module 3 .
[0053] The feature capture module 11 can be a camera, which is set in the recognition area, and captures the specific facial position of the person t...
Embodiment 2
[0066] refer to Figure 2-6 as an example.
[0067] A working method of a security monitoring system based on identification of multiple feature changes, comprising the following steps:
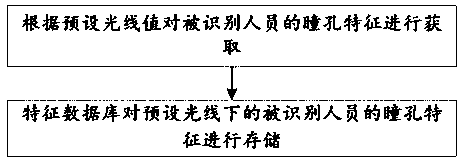
[0068] The feature capture module 11 captures the eye features of the recognized person in the recognition area, and outputs the eye features to the feature extraction module 12 .
[0069] The feature extraction module 12 extracts pupil features from the eye features and outputs the pupil features to the analysis module 3 .
[0070] The analysis module 3 acquires the pupil features and compares the pupil features with the features in the feature database 31 .
[0071] The voice acquisition module 21 acquires the voice information of the recognized person in the recognition area, and outputs the voice information to the voiceprint extraction module 22 .
[0072] The voiceprint extraction module 22 extracts the voiceprint in the speech information, and outputs the voiceprint to the analysis ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com