Authentication management system, method and device
A technology for authentication management and authentication requests, applied in security devices, electrical components, wireless communications, etc., can solve the problems of leaking account numbers, passwords, user economic losses, monitoring, interception, etc., to achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
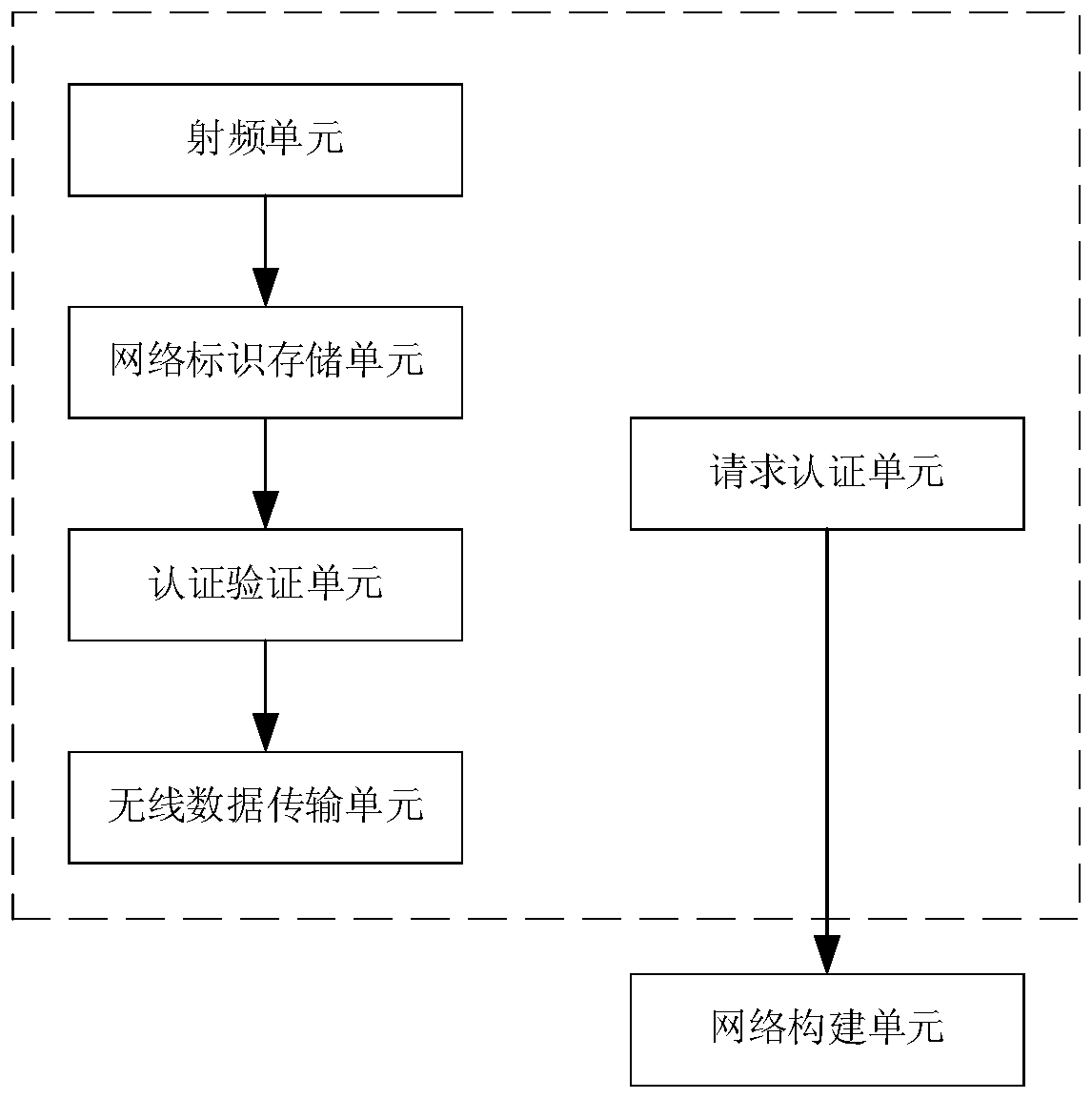
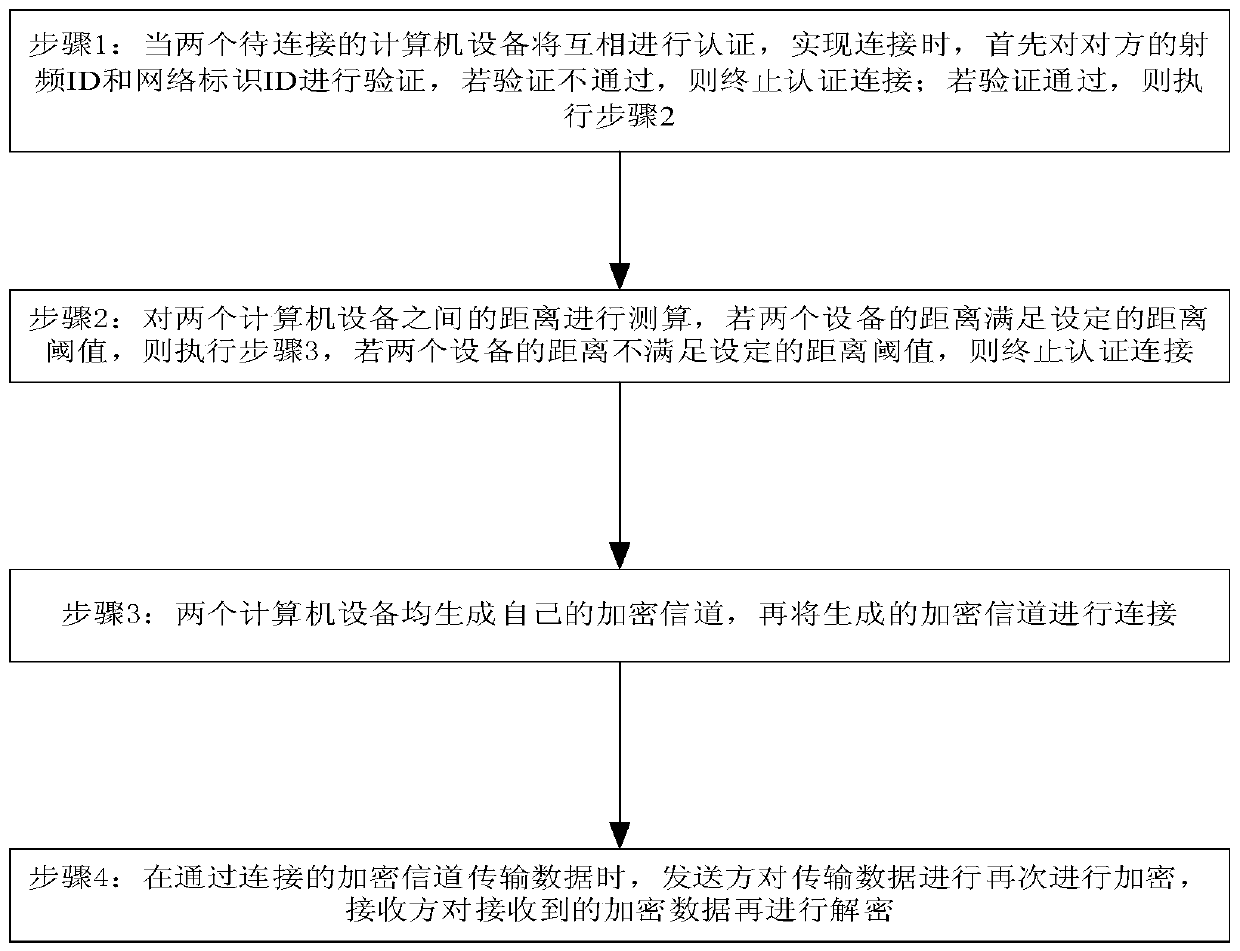
[0024] An authentication management system, the system includes: authentication requesting units arranged on different computer devices; each of the authentication requesting units at least includes: a radio frequency unit, a network identification storage unit, an authentication verification unit and a wireless data transmission unit; The system also includes a network construction unit arranged on different computer devices; the network construction unit responds to the command of the authentication request unit to construct an encryption subnetwork, and the encryption subnetwork is used for data transmission between two computers that have passed the authentication verification .
[0025] specific,
Embodiment 2
[0027] On the basis of the previous embodiment, the authentication verification unit includes: a radio frequency identification ID verification module, a network identification ID verification module and a distance verification module; the radio frequency identification ID verification module verifies the radio frequency ID of the other device; the The network identification ID verification module is used to verify the network identification ID of the other device; the distance verification module is used to verify the distance of the other device.
Embodiment 3
[0029] On the basis of the previous embodiment, each computer device has at least one network construction unit.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com