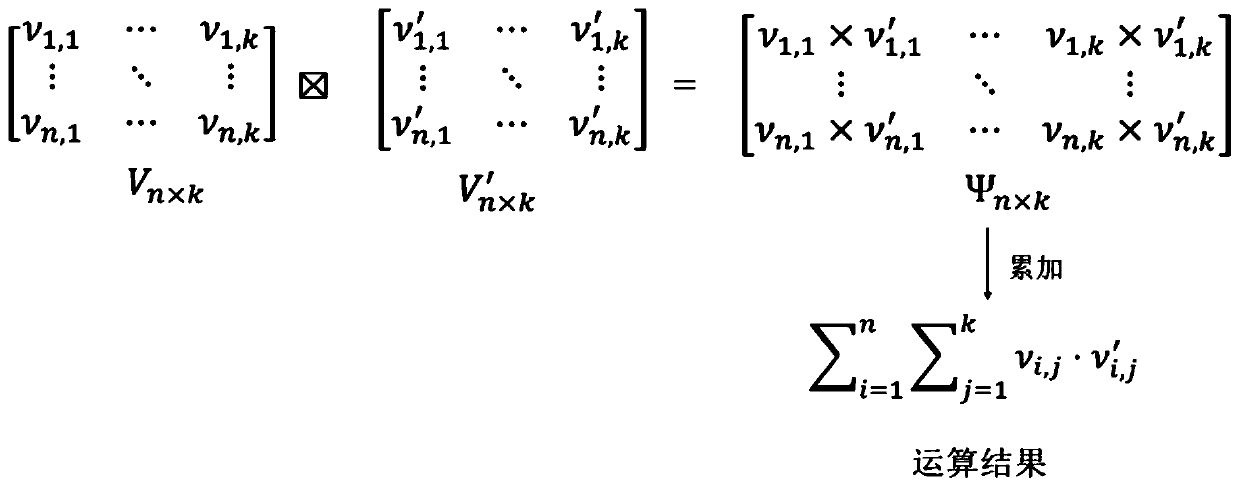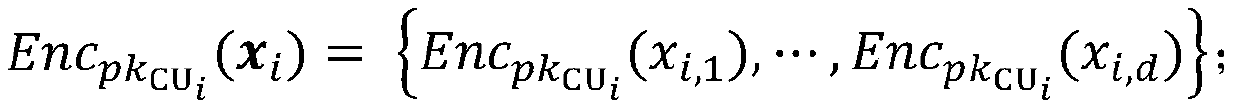Privacy information protection method based on K-means clustering
A privacy information, K-means technology, applied in the field of information security, can solve the problems of endangering personal security, not revealing additional information, loss of users' personal property, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
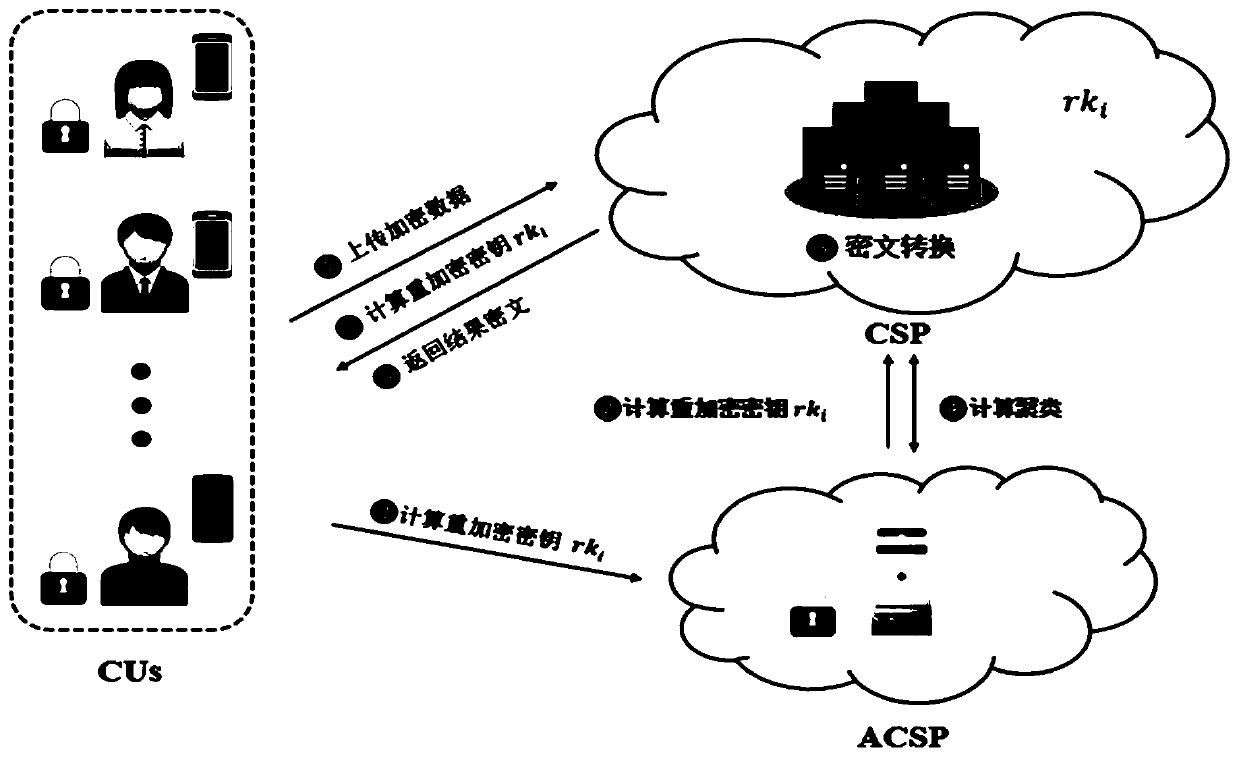
[0078] In this embodiment, it is assumed that the two cloud servers in the community do not collude, and at the same time, the two-way additive homomorphic proxy re-encryption algorithm is used to realize the clustering of ciphertexts with different public keys, and the clustering results under the same public key are converted into different The clustering results under the public key are returned to the client, while protecting the privacy of the client's private data and community information (clustering center).
[0079] Such as figure 1 As shown, this embodiment provides a privacy information protection method based on K-means clustering, and the specific steps are as follows:
[0080] S0: key pair generation steps:
[0081] First, the cloud server CSP calls the Gengroup function in ElGamal encryption to generate the public parameter PP=(p, G 1 , g), G 1 is the multiplicative group of prime p, where g is the multiplicative group G 1 Generator, and send the generated p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com