Network asset fingerprint identification method, system and device
A fingerprint identification and network asset technology, applied in the field of network security, can solve problems such as lax asset supervision, easy to attack and difficult to prevent security loopholes, and inefficient event handling
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
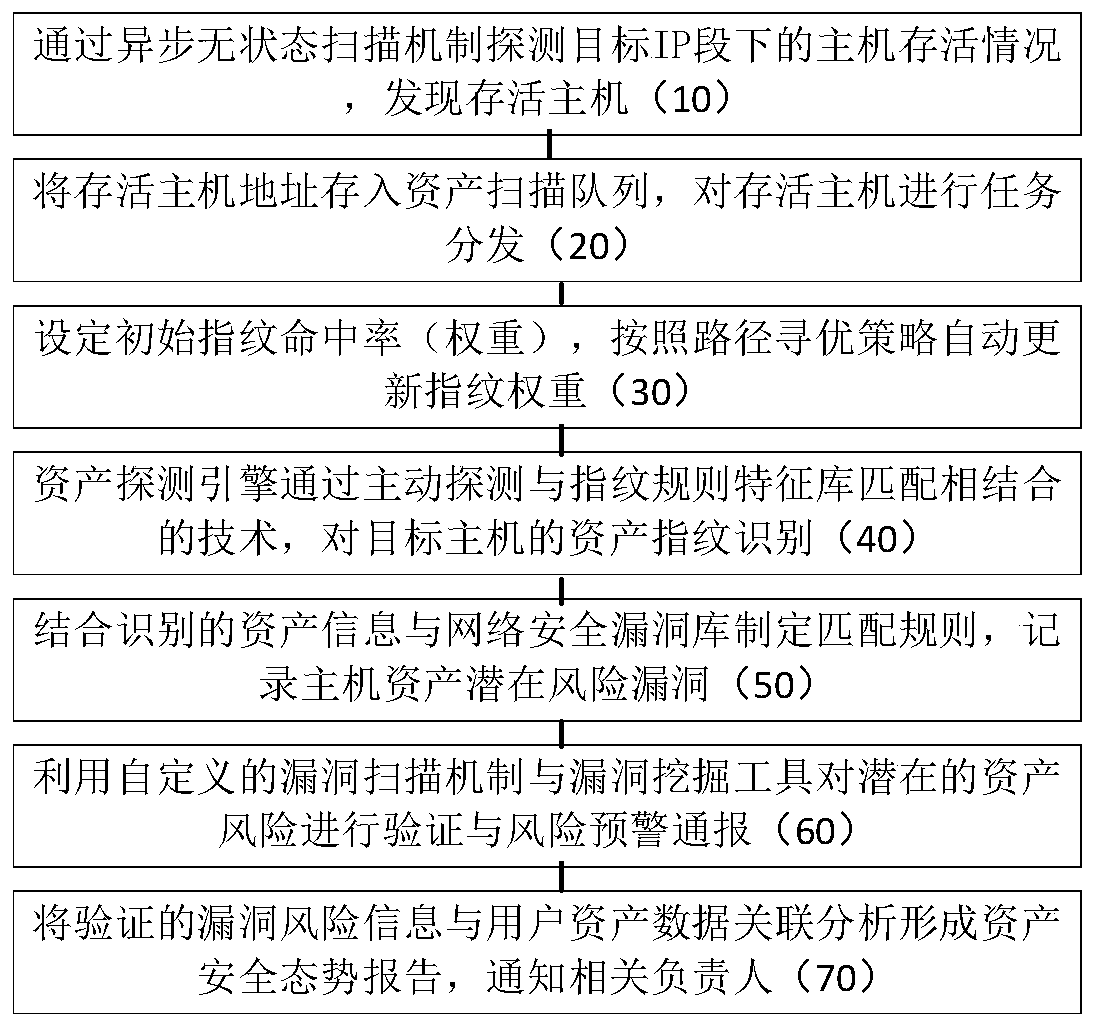
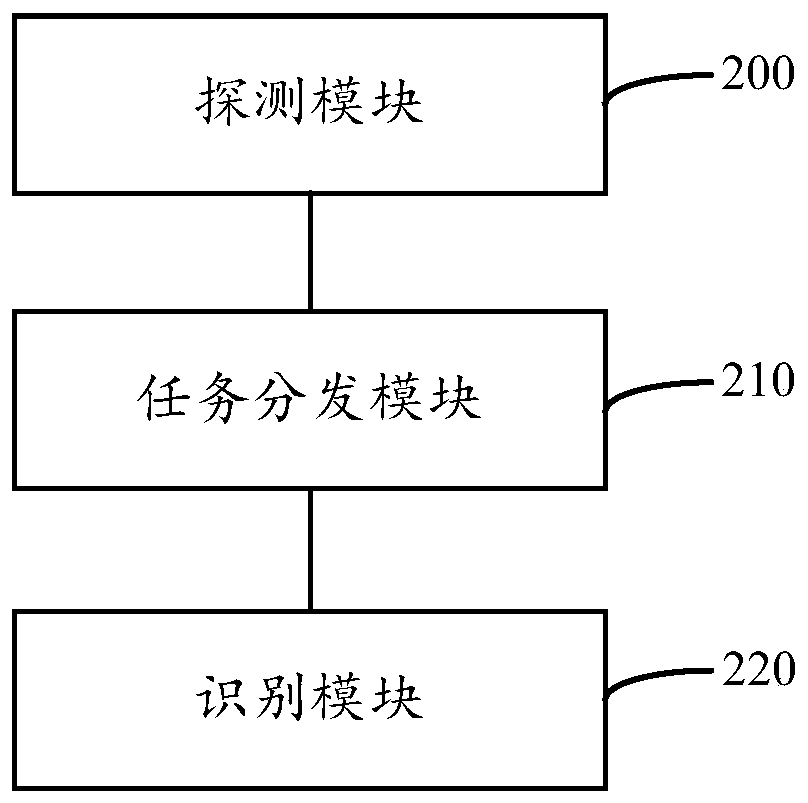
[0065] The embodiment of the present invention relates to a method, system, and device for network asset fingerprint identification and risk warning. The technical solution of the embodiment of the present invention detects surviving hosts in network space through an asynchronous stateless scanning mechanism; identifies surviving hosts through task distribution and scheduling strategies The asset fingerprint information and update the fingerprint weight; use the method based on fingerprint feature rule matching to discover potential risks of host assets; execute custom vulnerability scanning programs and vulnerability mining tools to verify potential risks, and issue risk warning notifications.
[0066] Exemplary embodiments of the present disclosure will be described in more detail below with reference to the accompanying drawings. Although exemplary embodiments of the present disclosure are shown in the drawings, it should be understood that the present disclosure may be embo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com