Application arrangement method and device and electronic equipment
A target device and application deployment technology, applied in the information field, can solve problems such as not easy to find the cause, difficult to debug, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
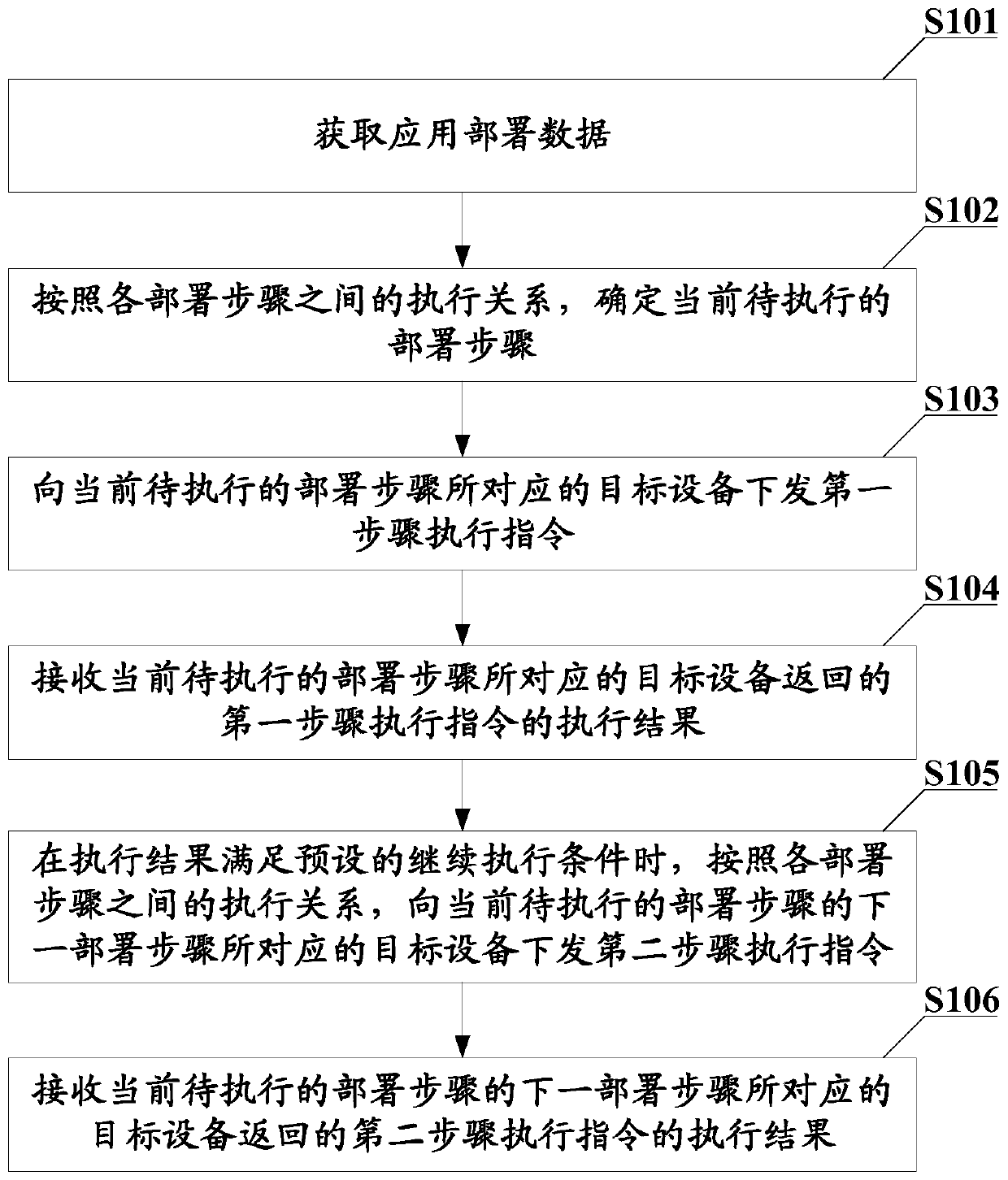
[0042] Please see figure 1 , figure 1 A schematic flowchart of an application orchestration method applied to an orchestration engine provided in the embodiment of the present application, including:
[0043] S101: Obtain application deployment data.
[0044] In the embodiment of the present application, the application deployment data includes each deployment step of the application, the execution relationship between each deployment step, and the target device corresponding to each deployment step.
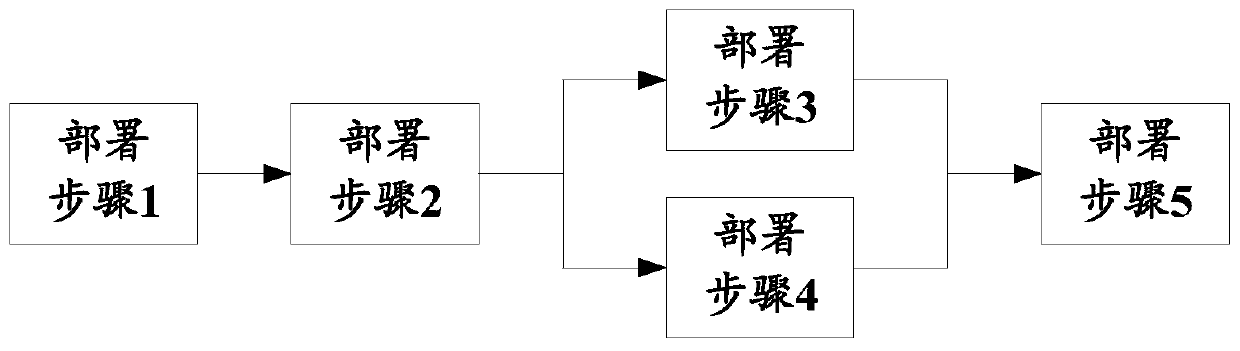
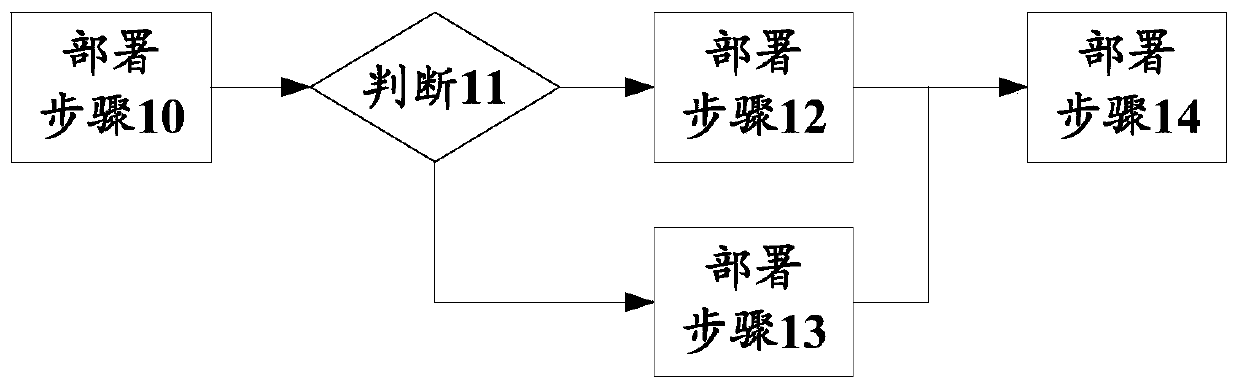
[0045] It should be noted that, in the embodiment of the present application, the application deployment data may be preset by an engineer and then input into the editing engine. For example, engineers can decouple a large script or a group of scripts of the application to be deployed into multiple small deployment steps according to the execution relationship of serial, parallel, branch selection, etc. in advance. After decoupling, engineers can obtain each deployment step o...
Embodiment 2
[0075] On the basis of Embodiment 1, this embodiment takes an application orchestration process with two deployment steps as an example to further illustrate this application.
[0076] see Figure 5 shown in Figure 5 In , the entire implementation process involves three execution subjects and a transit device, which are the editing engine, the first target device, the second target device and the message bus.
[0077] Let the two deployment steps be deployment step A and deployment step B respectively; the execution relationship between deployment step A and deployment step B is a serial relationship, that is, deployment step B is executed after deployment step A is executed, and the target corresponding to deployment step A The device is the first target device, and the target device corresponding to the deployment step B is the second target device.
[0078] see Figure 5 As shown, application orchestration methods include:
[0079] S501: The orchestration engine acquir...
Embodiment 3
[0101] In this embodiment, on the basis of the first and second embodiments, two specific deployment examples are used to further illustrate this application.
[0102] Let the hosts in the cluster be host A and host B.
[0103] see Figure 7 as shown, Figure 7 An instance of data synchronization. After the cluster system is initialized, the orchestration engine can issue a master node setting command to host A to configure host A as the master node, and issue a slave node setting command to host B to configure host B as a slave node. After the configuration of host A and host B is completed, the orchestration engine sends a data synchronization command to the slave node (host B), so that the slave node obtains data from the master node to achieve synchronization.
[0104] see Figure 8 as shown, Figure 8 It is an example of system connectivity test. After the cluster system is initialized, the orchestration engine can issue a TLS (Transport Layer Security, secure trans...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com