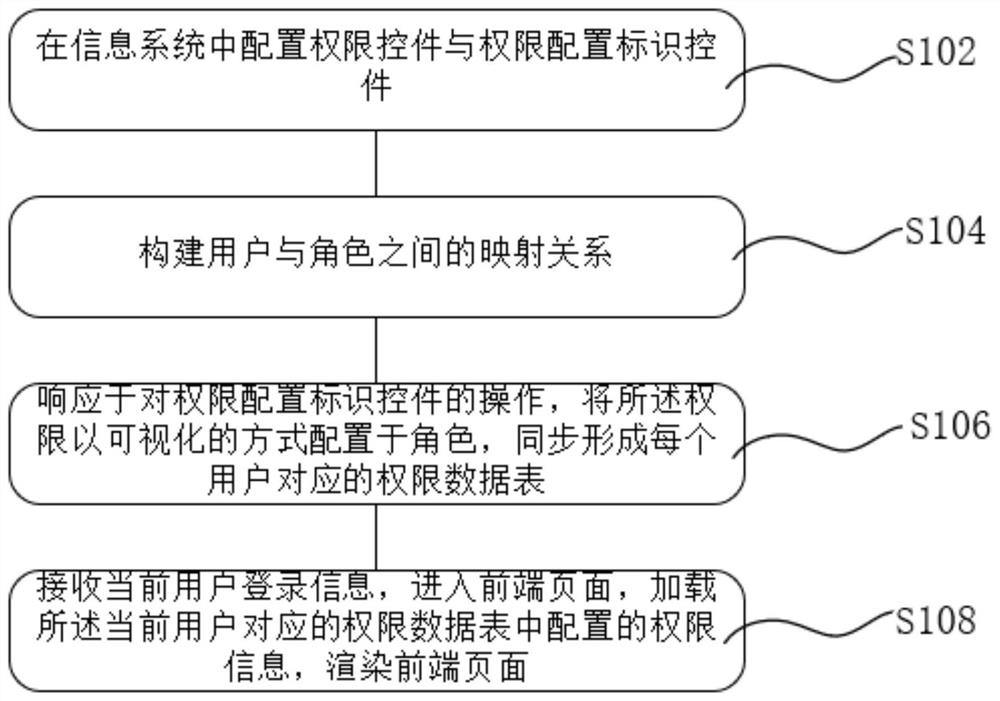
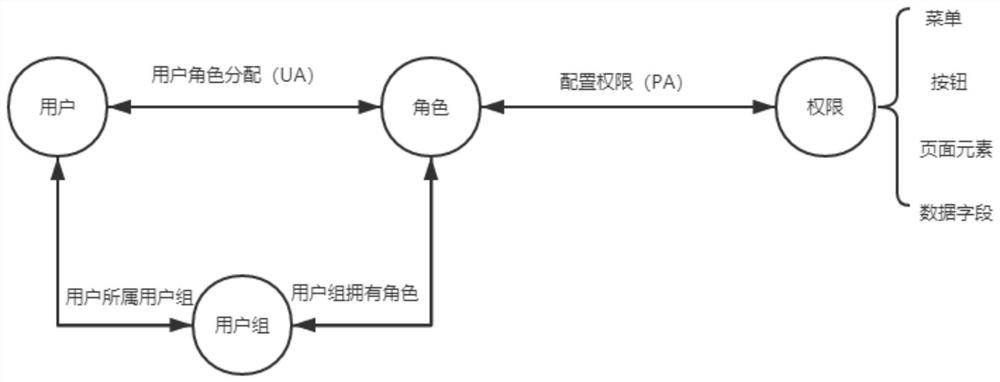
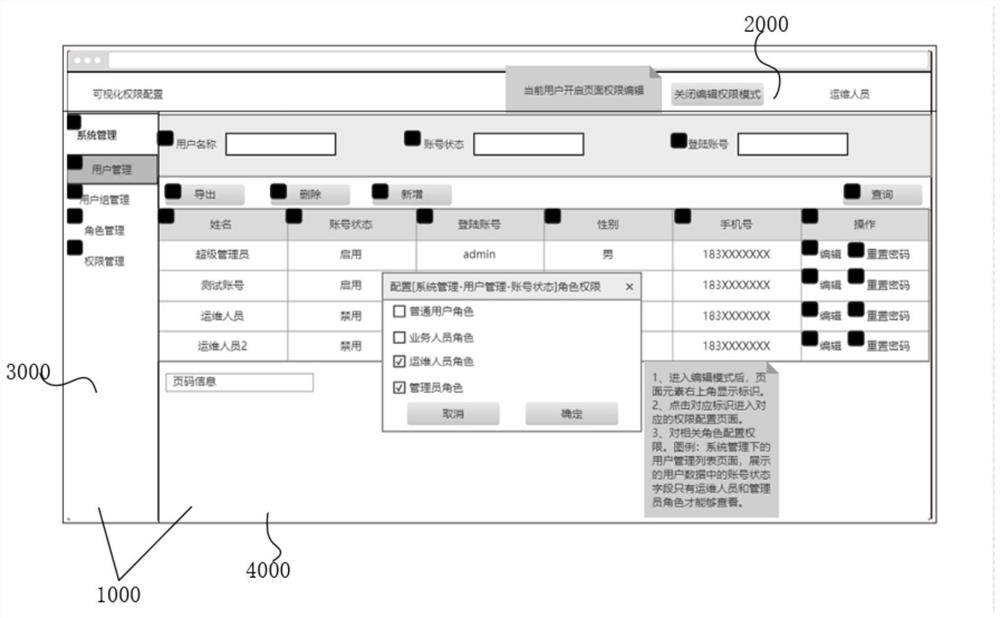
A method, device, terminal and storage medium for visual configuration control of rights in an information system
A technology of authority configuration and information system, which is applied in the direction of instruments, electronic digital data processing, digital data authentication, etc., can solve the problems of process redundancy, inconvenient operation, and low efficiency of authority allocation, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054] Here is an explanation of some technical terms:
[0055] Directives: Directives are special features prefixed with v-. The responsibility of the directive is to react to the HTML element with its associated effects when the value of the expression changes.
[0056] HTML elements: HTML uses "markup" (markup, also known as tag) to annotate text, pictures, and other content for display in a web browser. HTML markup contains some special "elements" such as , , , > , , , , , , , , , , > , , , , , , , Wait.
[0057] Vuex: Vuex is a state management pattern developed specifically for Vue.js applications.
[0058] Routing: Routing (Router) is to find a program or module that can handle this URL according to the URL.
[0059] Bit operation: All the numbers in the program are stored in binary form in the computer memory; bit operation is to directly operate on the binary bits of the integer...
Embodiment 2
[0083] The difference from Embodiment 1 lies in that the representation method of the permission is stored in a binary value. Further define the identification and text description of N kinds of permissions in the data dictionary, sort the N kinds of permissions, and the attribute value of the i-th permission is 2 i ;According to the checked permission, assign a value to the permission attribute value of the corresponding role, and convert the permission attribute value into a binary expression; if the i-th value in the expression is 1, it means that the role has the i-th permission .
[0084] Specifically, for example, you need to configure N permissions, define the identifiers and text descriptions of N permissions in the data dictionary, sort the N permissions, and represent each permission in binary, for example, a role has the first to nth The value of each permission can be expressed as: 2 0 +2 1 +2 2 ...2 n , its corresponding binary representation is 111....
Embodiment 3
[0094] This embodiment provides a terminal, including a processor, an input device, an output device, and a memory, the processor, the input device, the output device, and the memory are connected in sequence, and the memory is used to store a computer program, and the computer program includes a program Instructions, the processor is configured to call the program instructions to execute the method described in Embodiment 1-2.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com