A retransmission method based on finite state machine and its validity verification method
A finite state machine and three-state technology, applied in the information field, can solve problems such as poor communication quality and poor security, and achieve the effects of high authentication success rate, high security, and reasonable authentication delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044]The objects and functions of the present invention and methods for achieving the objects and functions will be clarified by referring to the exemplary embodiments. However, the present invention is not limited to the exemplary embodiments disclosed below; it can be implemented in various forms. The essence of the description is only to help those skilled in the relevant art comprehensively understand the specific details of the present invention.
[0045] Hereinafter, embodiments of the present invention will be described with reference to the accompanying drawings. In the drawings, the same reference numerals represent the same or similar components, or the same or similar steps.
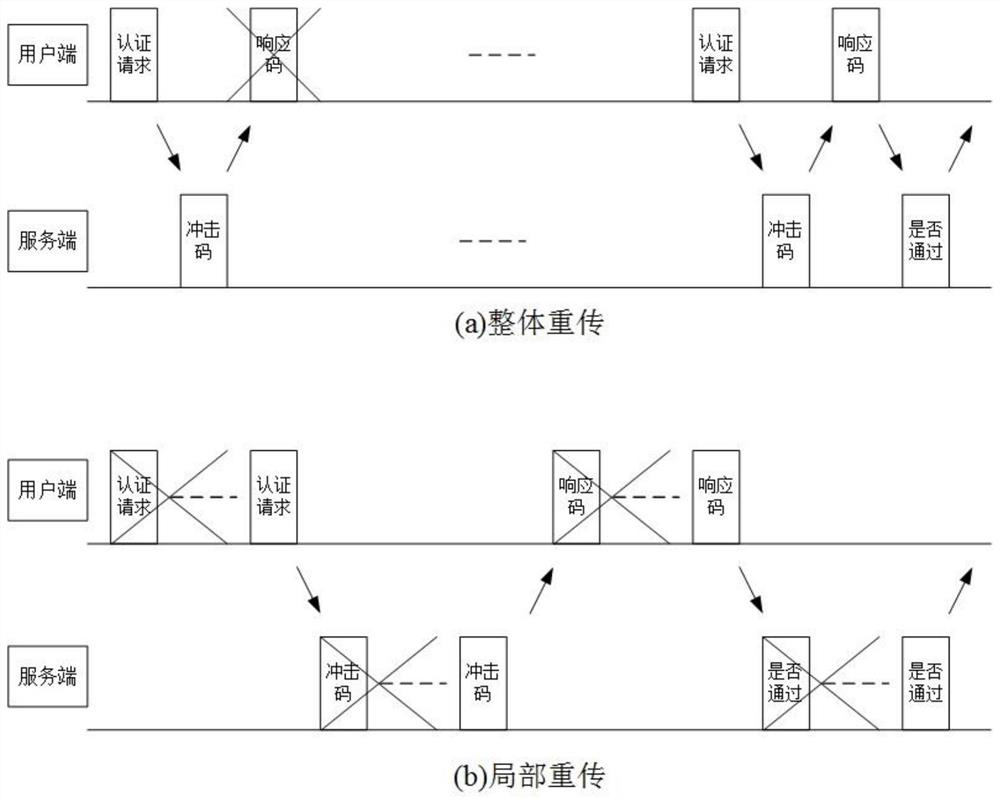
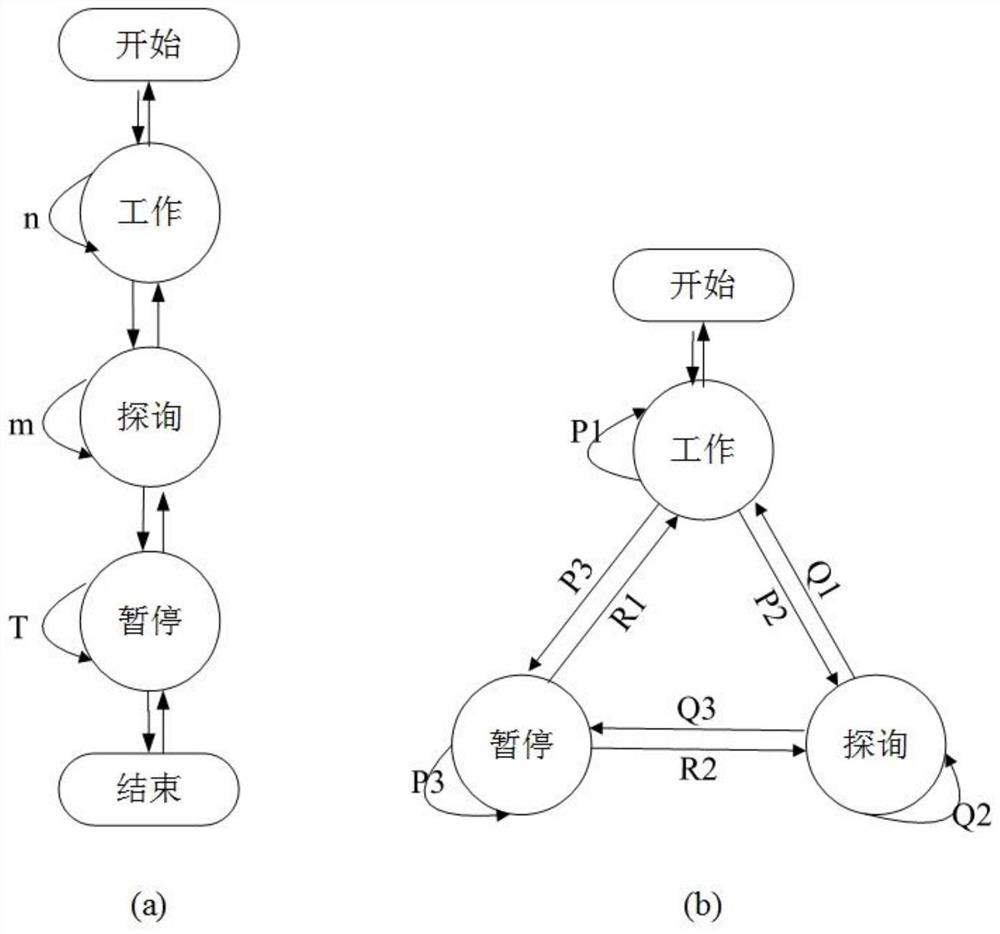
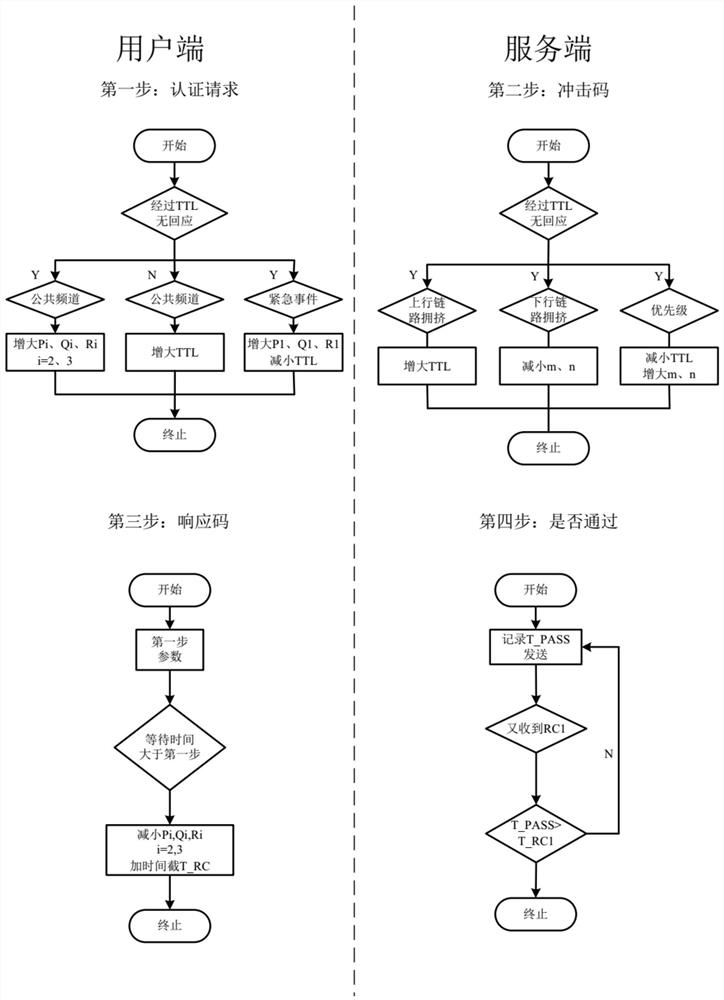
[0046] According to the present invention, this embodiment provides a retransmission method based on a finite state machine. In this embodiment, a retransmission method based on a finite state machine will be described in detail by taking the user authentication communication process as an ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap