User track similarity judgment method and related device
A trajectory similarity and user trajectory technology, applied in the field of network security, can solve the problem of low accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
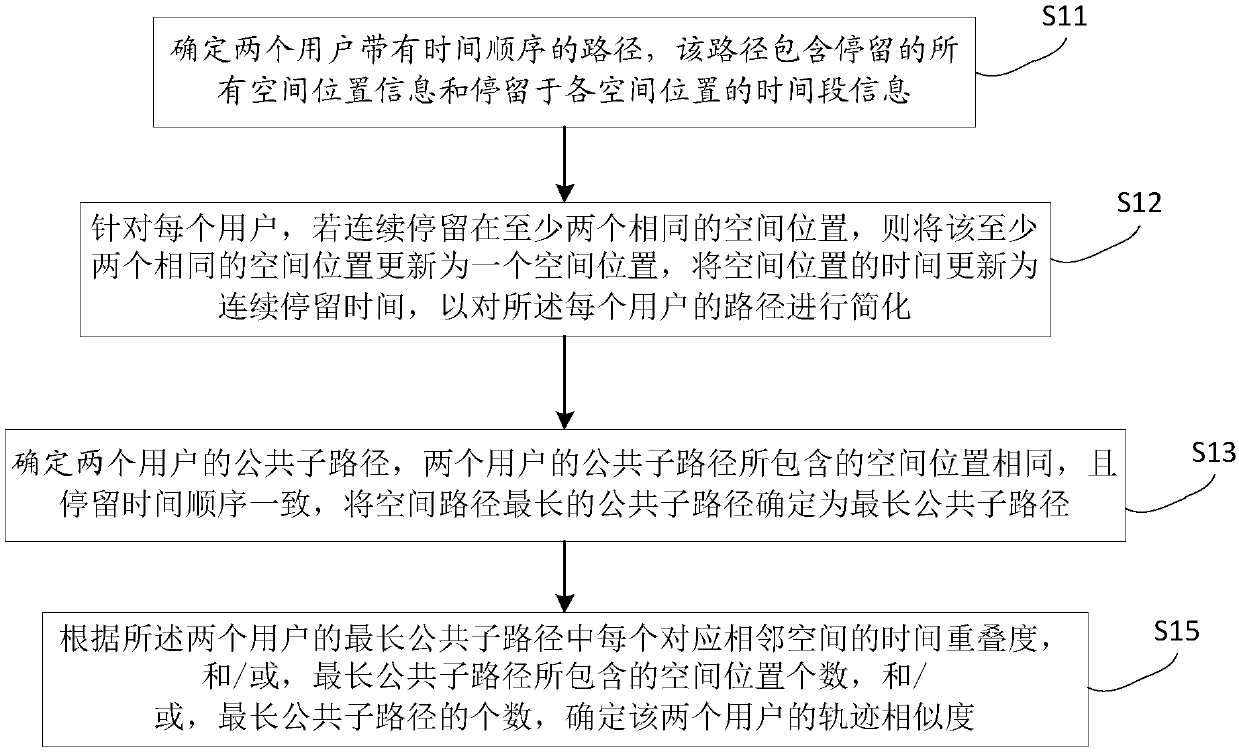
[0034] figure 1 It is a flowchart of a method for judging user trajectory similarity according to Embodiment 1 of the method of the present invention. see see figure 1 , in this embodiment, the method includes:
[0035] Step S11, determine the path of two users with time sequence, this path includes all spatial location information of staying and the time period information of staying in each spatial location;
[0036] Specifically, the spatial location information and short stay time information contained in the user's time-ordered route can be obtained through a device that directly or indirectly obtains the geographic location, for example, using an app with positioning information, or using the user to send a network request The exposed ip, or wifi or base station, etc.
[0037] Step S13, determine the common sub-paths of the two users, the common sub-paths of the two users contain the same spatial location, and the order of stay time is the same, and determine the common...
Embodiment 2
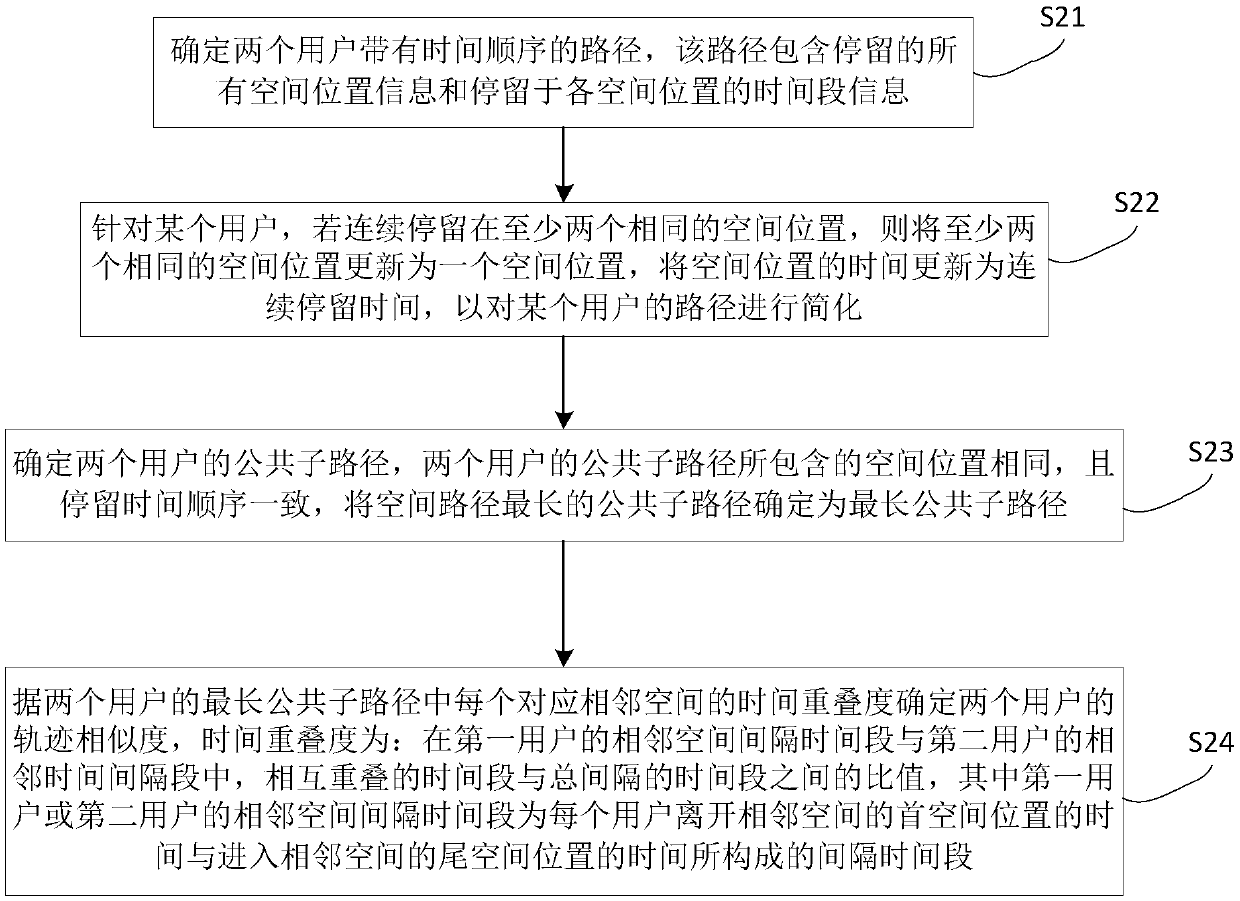
[0047] figure 2 It is a flow chart of a method for judging user trajectory similarity according to Embodiment 2 of the method of the present invention. see see figure 2 , in this embodiment, the method includes:
[0048] Step S21, determine the path of two users with time sequence, this path includes all spatial location information of stay and the time period information of staying in each spatial location;
[0049] Step S22, for a certain user, if staying in at least two identical spatial locations continuously, update at least two identical spatial locations to one spatial location, and update the time of the spatial location to the continuous stay time, so as to The user's path is simplified;
[0050] Step S23, determine the public sub-paths of the two users, the spatial positions contained in the public sub-paths of the two users are the same, and the order of stay time is consistent, and the public sub-path with the longest spatial path is determined as the longest ...
Embodiment 3
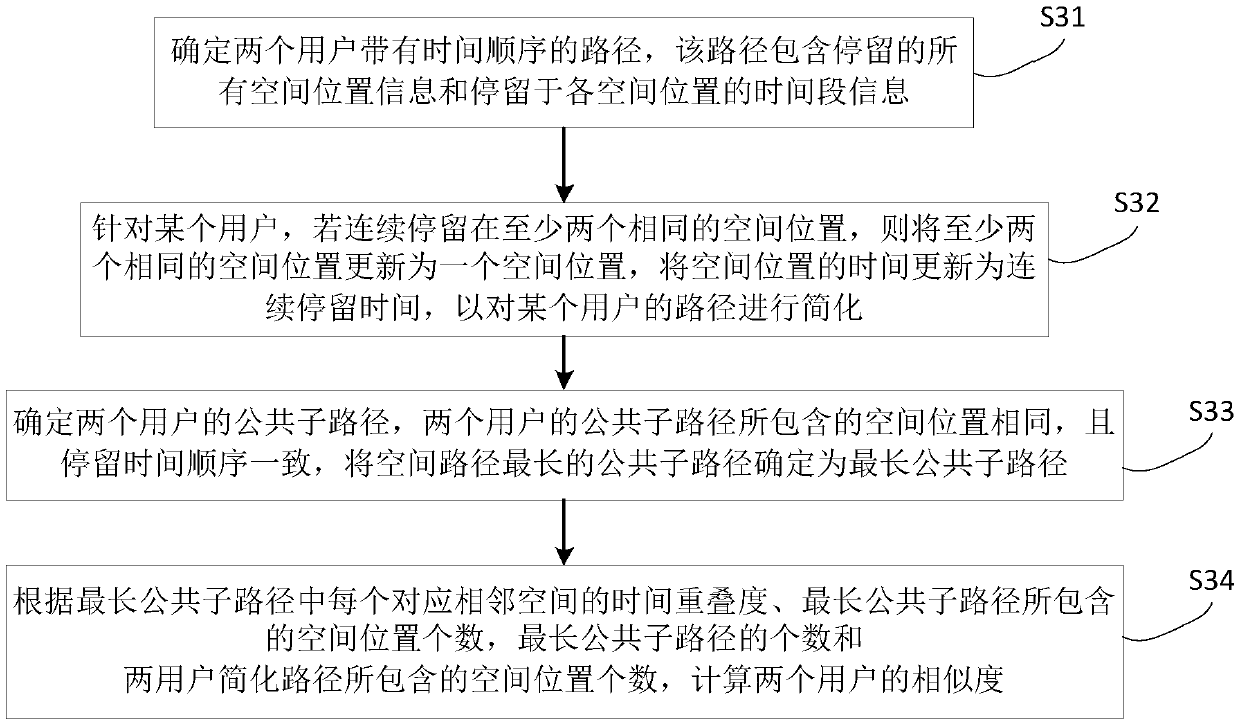
[0069] image 3 It is a flowchart of a method for judging user trajectory similarity according to Embodiment 3 of the method of the present invention. see see image 3 , in this embodiment, the method includes:
[0070] Step S31, determine the path of two users with time sequence, this path includes all spatial location information of staying and the time period information of staying in each spatial location;
[0071] Step S32, for a certain user, if staying in at least two identical spatial locations continuously, then update at least two identical spatial locations as one spatial location, and update the time of the spatial location as the continuous stay time, so as to The user's path is simplified;
[0072] Step S33, determine the public sub-paths of the two users, the spatial positions contained in the public sub-paths of the two users are the same, and the order of stay time is consistent, and the public sub-path with the longest spatial path is determined as the longe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com