Access control method and user equipment
A technology of access control and user equipment, applied in access restriction, connection management, wireless communication, etc., can solve problems such as meaninglessness and non-belonging, and achieve the effect of improving utilization efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
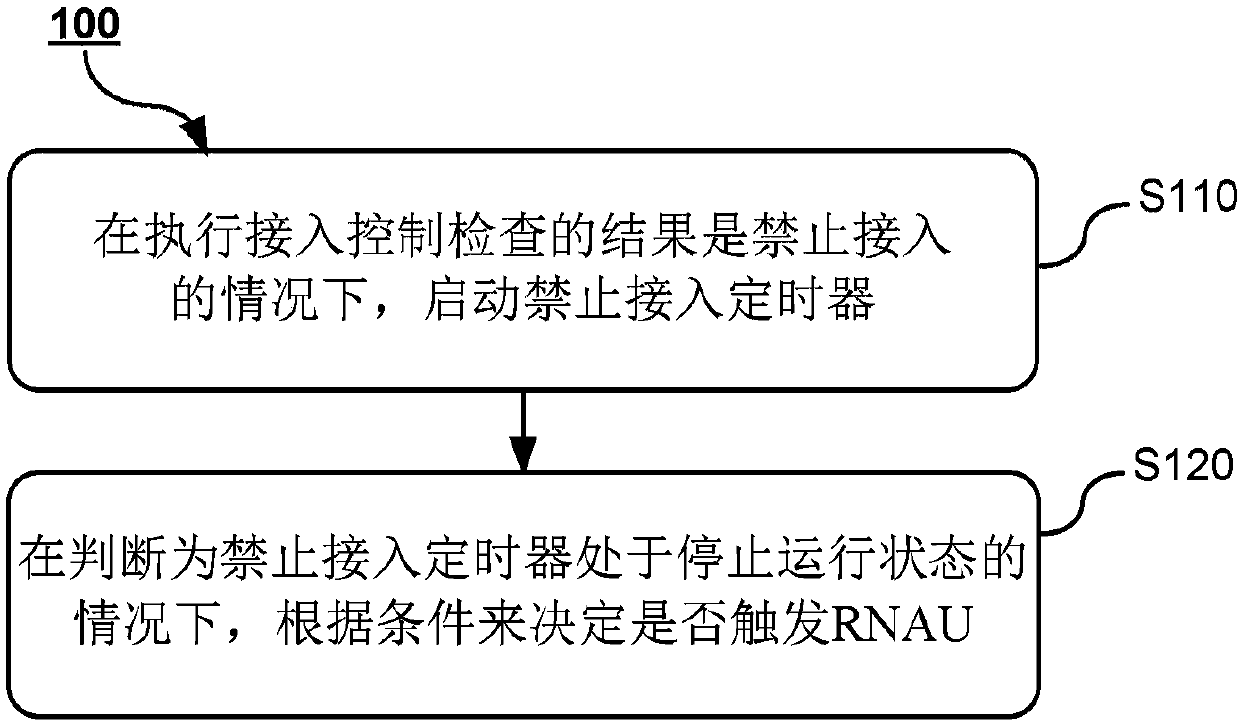
[0057] When the barring timer stops running, determine whether the UE is in the INACTIVE state,
[0058] - If the UE is not in the INACTIVE state or the UE is in the connected state, the UE does not trigger RNAU;
[0059] - If the UE is in the INACTIVE state, further determine whether the T380 is in the running state;
[0060] - Trigger RNAU if T380 is not running;
[0061] - If T380 is running, further determine whether the cell where the UE is currently camping belongs to the RNA area;
[0062] - If the cell where the UE is currently camping does not belong to the RNA area, trigger RNAU;
[0063] -If the cell where the UE is currently camping on belongs to the RNA area, RNAU is not triggered.
[0064] Wherein, the barring timer refers to a timer related to barring, which can be understood as a timer started when an access check result of a certain access category (access category) is barring access. The stopping of the barring timer can be caused by the timeout of the ba...
Embodiment 2
[0087] The difference from Embodiment 1 is that a corresponding operation is triggered through an intermediate indication process.
[0088] When the barring timer stops running, indicate to the RRC layer or generate an indication to the UE: the access barring of the access category (access category) corresponding to the barring timer is released.
[0089] Based on or considering the indication, the RRC layer further performs the following operations:
[0090] - If the UE is not in the INACTIVE state or the UE is in the connected state, RNAU is not triggered;
[0091] - If the UE is in the INACTIVE state, further determine whether the T380 is in the running state;
[0092] - Trigger RNAU if T380 is not running;
[0093] - If T380 is running, further determine whether the cell where the UE is currently camping belongs to the RNA area;
[0094] - If the cell where the UE is currently camping does not belong to the RNA area, trigger RNAU;
[0095] -If the cell where the UE is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com