Remote operation and maintenance and data exchange method for equipment industrial control security
A data exchange and industrial control technology, applied in the field of information security, can solve the problems of data being easily intercepted, targeted malicious code, failure to detect equipment in time, abnormal data changes, etc., to reduce the probability of intercepting running data packets and control data packets, The effect of wide coverage and improved safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
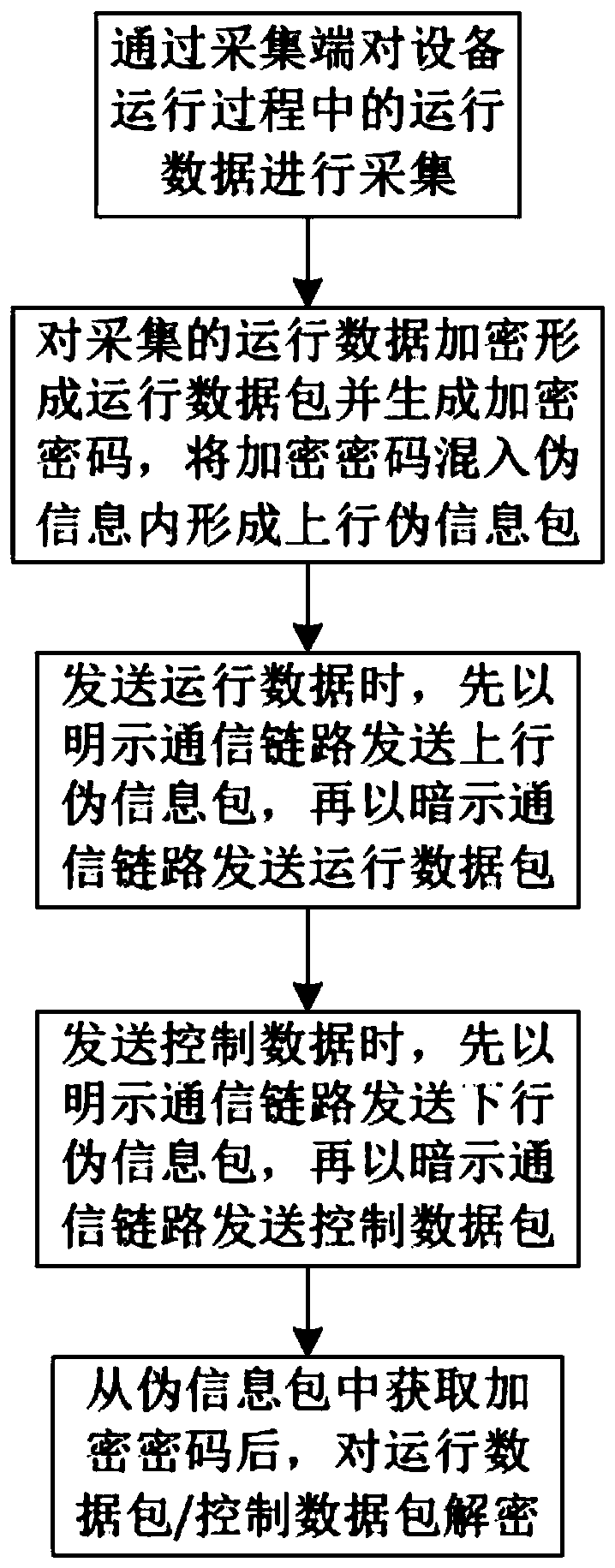
[0035] Remote operation and maintenance and data exchange methods for equipment industrial control security, such as figure 1 Shown: Include the following steps:
[0036] S100, collecting the operation data during the operation of the equipment through the collection terminal;
[0037] S200, encrypting the operation data at the acquisition end and generating an encryption password, forming an operation data packet after encrypting the operation data, generating pseudo information in the same format as the operation data transmission at the acquisition end, and mixing the encrypted password into the pseudo information to form an uplink pseudo information packet , the acquisition end backs up and stores the encrypted running data packet and the pseudo-information packet carrying the encrypted password;
[0038] S300, when exchanging data, first send an uplink dummy information packet added with an encrypted password, the uplink dummy information packet is sent through an explic...
Embodiment 2
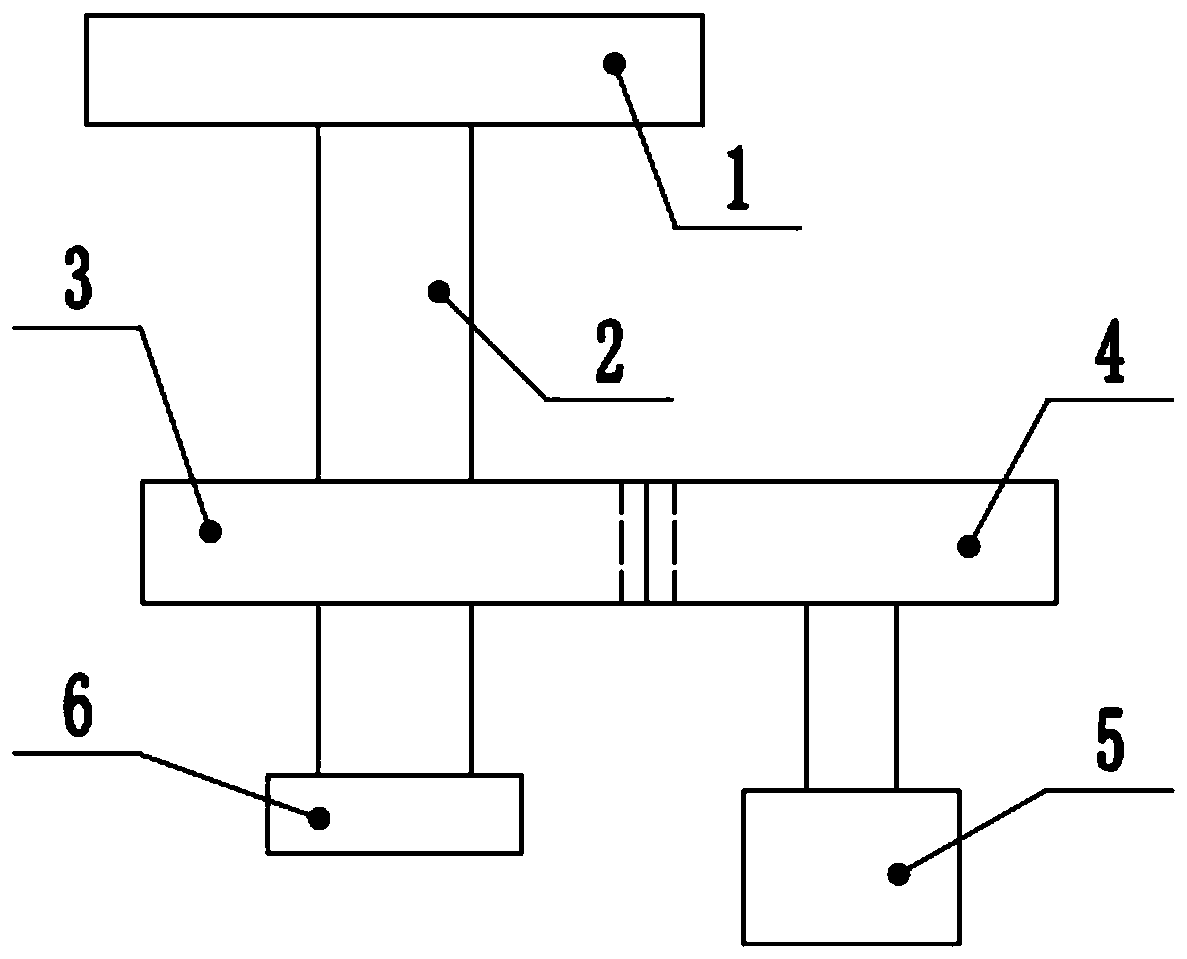
[0045] The difference with Embodiment 1 is that, if figure 2As shown, in the process of industrial control, the workpiece produced is turned and scanned through the steering mechanism. The steering mechanism includes a support plate 1, and the workpiece is placed on the support plate 1 for scanning. The bottom of the support plate 1 is welded with the shaft 2, and the middle of the shaft 2 is keyed. There is a driven gear 3, and the end of the rotating shaft 2 is key-connected with a rotating bearing 6. The rotating bearing 6 can be installed on other support frames. The driven gear 3 is meshed with a driving gear 4. The diameter of the driving gear 4 is smaller than that of the driven gear 3. The rotation of the plate 1 is decelerated, the driving gear 4 is connected to the support shaft, and the motor 5 is installed at the bottom of the support shaft. The motor 5 can be an existing SM130-100-15LFB servo motor, and also includes a scanning module. The position of the scanning...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com