Web honeypot system based on intelligent questions and answers
An intelligent question answering and honeypot technology, applied in transmission systems, special data processing applications, instruments, etc., can solve the problems of complex deployment configuration, lack of policy level, deception, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
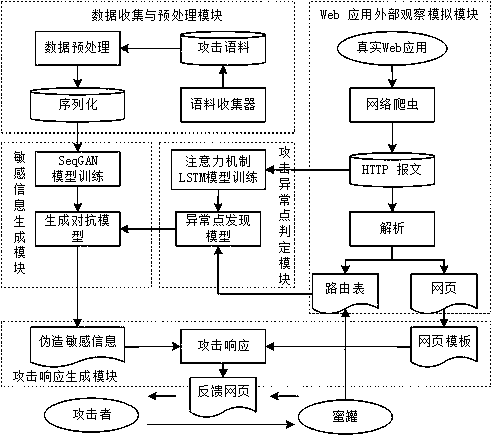
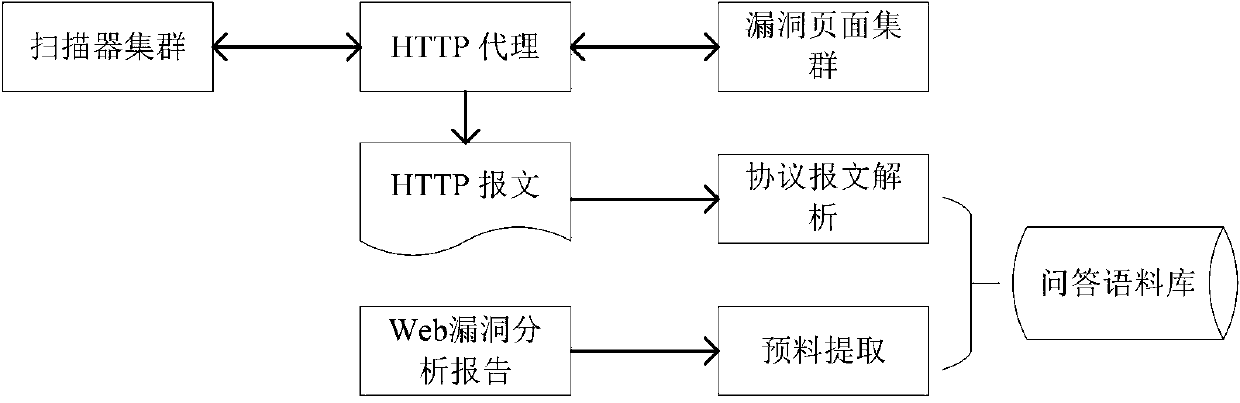
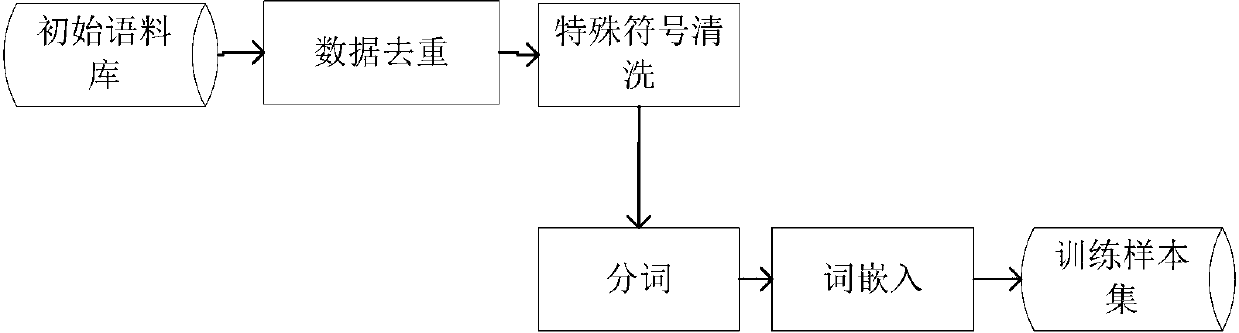
[0045] The present invention consists of the following five modules which jointly constitute a honeypot system. The technical solutions in the embodiments of the present application will be clearly and completely described below in conjunction with the drawings in the embodiments of the present application.
[0046] The honeypot and the network deception technology derived from it are tools to change the asymmetry of attack and defense. Semantic-based intelligent Q&A Web honeypots use contextual semantics to replace traditional single attack vector recognition, which can more correctly and semantically feed back the malicious behavior of attackers, and can improve the performance of Web honeypot systems in dynamic feedback, adaptive configuration, visual deception and The reliability and success rate of attack trapping. The specific technical scheme is as follows.
[0047] Such as Figure 1 Shown is a schematic diagram of the overall framework of the model of the present inv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com