Two-party authentication and session key exchange method based on bst-puf
A technology of session key and key exchange, which is applied in the field of communication technology and information security to achieve the effect of high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
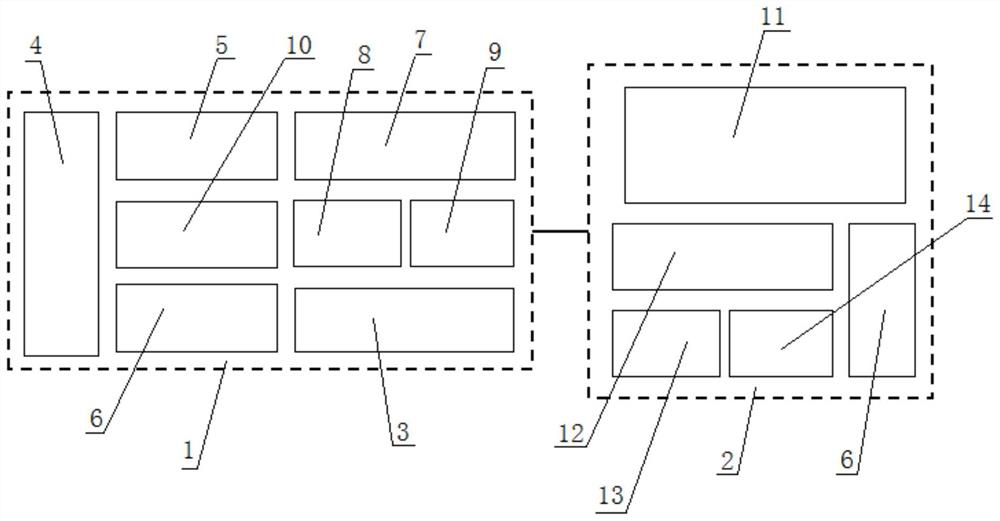
[0054] like figure 1 As shown, the two-party authentication and session key exchange method based on BST-PUF of the present invention, the device based on it includes a device end 1 and a server end 2, and the device end 1 includes a non-volatile memory module 3, and also includes:
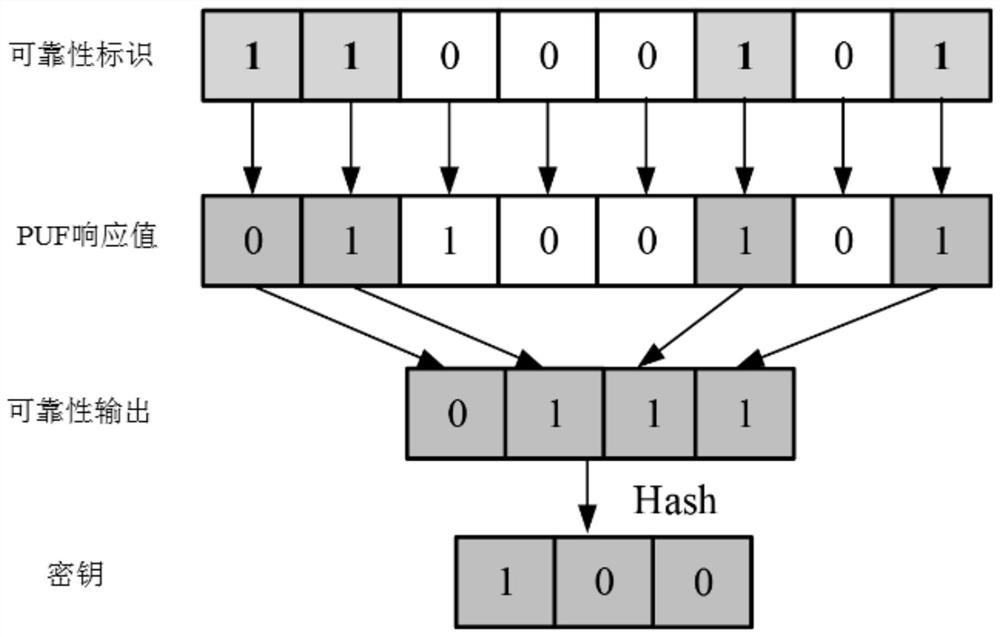
[0055] BST-PUF module 4: Input an incentive information with a length of L bits, L is a positive integer, output a PUF response value of L bits and a reliability identification value of L bits, wherein the i-th bit in the reliability identification value The value identifies the reliability of the i-th bit output in the corresponding response. When the i-th bit value in the reliability identification value is 1, it proves that the i-th bit output in the response value is reliable, otherwise it is unreliable;
[0056] Key extraction module 5: input the L...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com