Wireless medical sensor network user identity authentication protocol based on biological characteristic information
A biometric information, user identity authentication technology, applied in decryption and confidential fields, can solve problems such as damage to patient privacy, wrong diagnosis results, medical malpractice, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
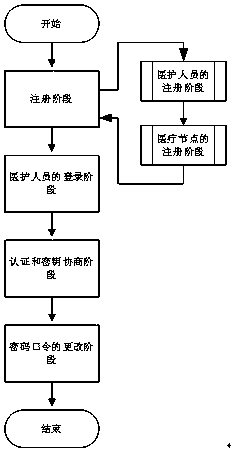
[0019] The following will refer to the attached figure 1 , to describe the identity authentication protocol of the present invention in detail.
[0020] (1) Registration stage:
[0021] (a) Phase of registration of healthcare personnel:
[0022] To become a legitimate user, medical staff must register with a reliable hospital registration center. The specific steps are as follows:
[0023] Step 1: User U i First choose your own ID i and password PW i , and collect biometric information template B on the corresponding human biometric information scanning device i . Then, U i Use B i and by fuzzy extraction function i , P i >=Gen(B i ) to obtain the biometric key BPW i =h(R i ). In addition, U i Calculate RBPW i =h(ID i ||PW i ||BPW i ). Finally, U i Pass the information {ID i ,RBPW i} Send gateway GW.
[0024] Step 2: After receiving U i The registration request information {ID i ,RBPW i}, GW randomly generates a random value r g , and calculate X GW...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com