Active defense method for power industry network security
A technology of active defense and network security, applied in the field of information security, it can solve the problem that network administrators have no way of knowing, and achieve the effect of diversifying protection methods, improving protection capabilities, and reducing false negatives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
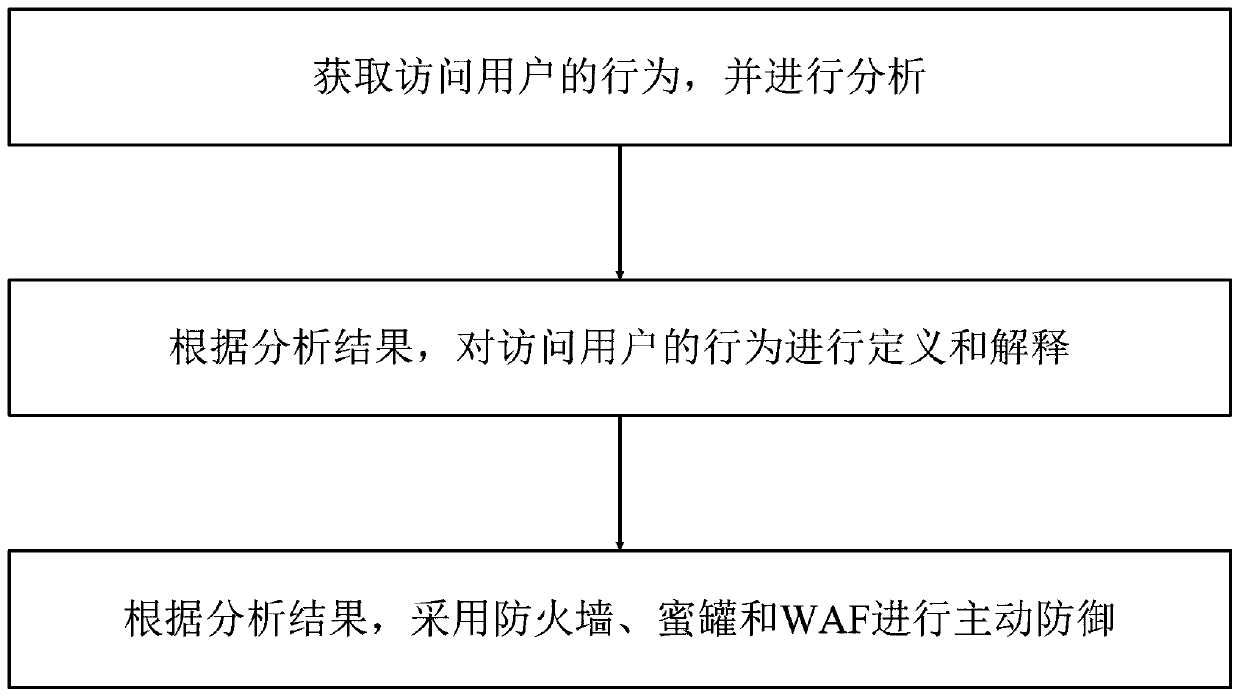
[0036] The active defense method of the electric power industry network security provided by the present invention comprises the following steps:
[0037] S1. Acquiring and analyzing the accessing behavior of the user; specifically, acquiring the accessing behavior of the user and analyzing it: if the user’s accessing behavior is a normal accessing behavior, no processing will be done and the access will be released; if the user’s accessing behavior is an attacking behavior, then Carry out subsequent active defense steps;
[0038] S2. According to the analysis results of step S1, define and explain the behavior of the accessing user; specifically, to obtain the attacking behavior of the user, and compare it with the data in the pre-established knowledge base: if the comparison is successful, the knowledge will be directly triggered The execution behavior in the library, and execute the corresponding defense strategy;
[0039] S3. According to the analysis result of step S1, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com