Log collector configuration method, device and system
A configuration method and collector technology, applied in the Internet field, can solve problems such as server security accidents, achieve the effects of ensuring security, preventing server password leakage, and avoiding direct login to the server
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0027] According to an embodiment of the present application, a method for configuring a log collector is provided.
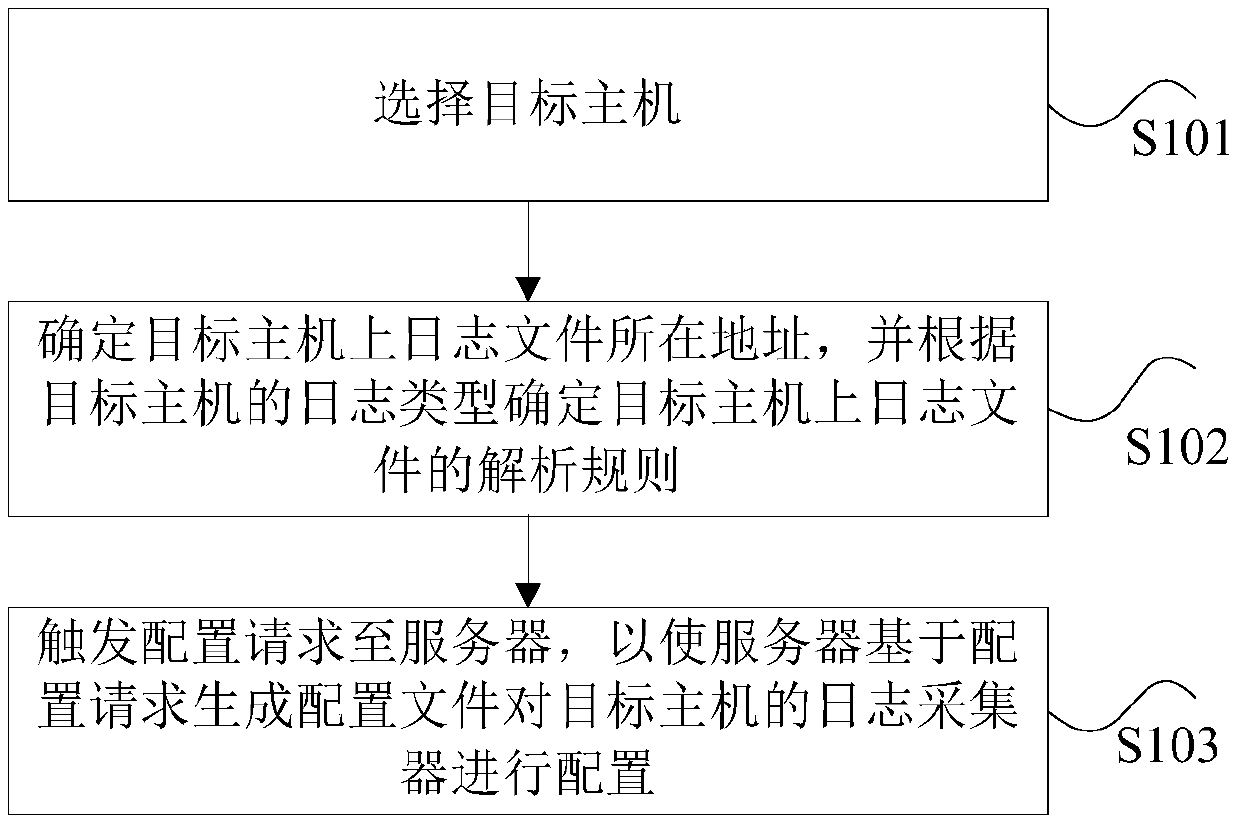
[0028] figure 1 is a flow chart of a log collector configuration method according to Embodiment 1 of the present application. Such as figure 1 As shown, the method includes the following steps:
[0029] Step S101, selecting a target host, where the target host is a host for which a log collector needs to be configured.
[0030] The above-mentioned target host can be one or more. For example, if there are 100 servers, you need to configure log collectors to select 50 of them.
[0031] Step S102, determine the location of the log file on the target host, and determine the parsing rules for the log file on the target host according to the log type of the target host.
[0032]The above address of the log file on the target host may be input by the user, and the addresses of the log files of different target hosts may be different. For example, the log file ad...
Embodiment 2
[0041] figure 2 It is a flowchart of a log collector configuration method according to Embodiment 2 of the present application. Such as figure 2 As shown, the method includes the following steps:
[0042] Step S201, receiving the configuration request sent by the client, wherein the configuration request carries the information of the target host, the address information of the log file on the target host, and the information of the parsing rules of the log file on the target host, and the target host needs to be configured The host of the log collector.
[0043] Step S202, acquiring a target template corresponding to the configuration request.
[0044] On the server side, through some pre-defined templates, the target template is selected based on the configuration request. It should be noted that different configuration requests will match different templates on the server side.
[0045] Step S203, rendering the target template based on the configuration request to ge...
Embodiment 3
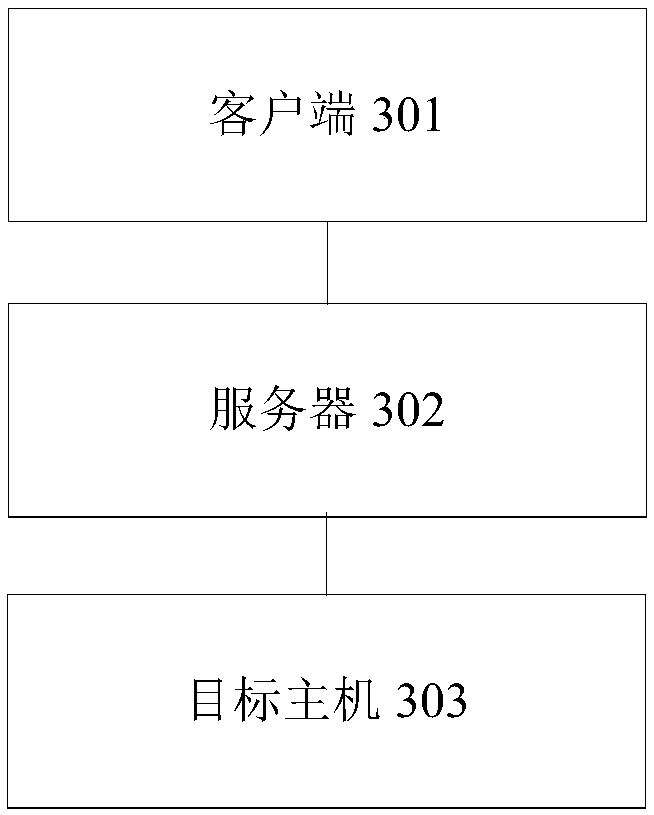
[0053] According to an embodiment of the present invention, there is also provided a system for implementing the log collector configuration method of the first and second embodiments above, such as image 3 As shown, the system includes: a client 301 , a server 302 and a target host 303 .
[0054] Specifically, the client 301 is used to select the target host, determine the address of the log file on the target host, and determine the parsing rules of the log file on the target host according to the log type of the target host, and trigger a configuration request to the server, wherein the target host is The host that needs to configure the log collector, the configuration request carries the information of the target host, the address information of the log file on the target host, and the information of the parsing rules of the log file on the target host;
[0055] The server 302 is configured to receive the configuration request sent by the client, render the target templa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com