Top-k disease matching method for protecting privacy in electronic medical system
A privacy-protecting, electronic medical technology, applied in the field of electronic medical and data matching, to achieve the effect of excellent feasibility, privacy and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
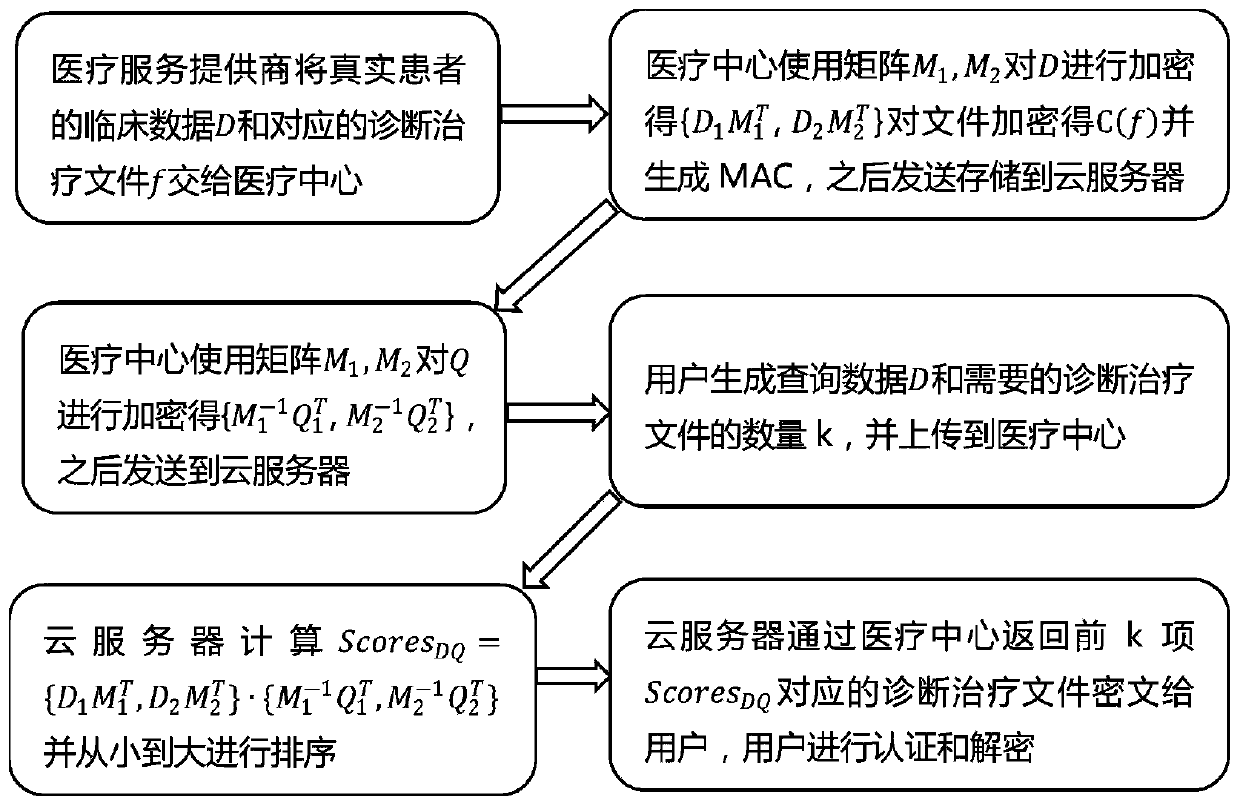
[0055] This embodiment elaborates in detail the specific implementation of data encryption, data storage and data query using the secure k-nearest neighbor technology to realize the privacy-protected Top-k disease matching method in the present invention.
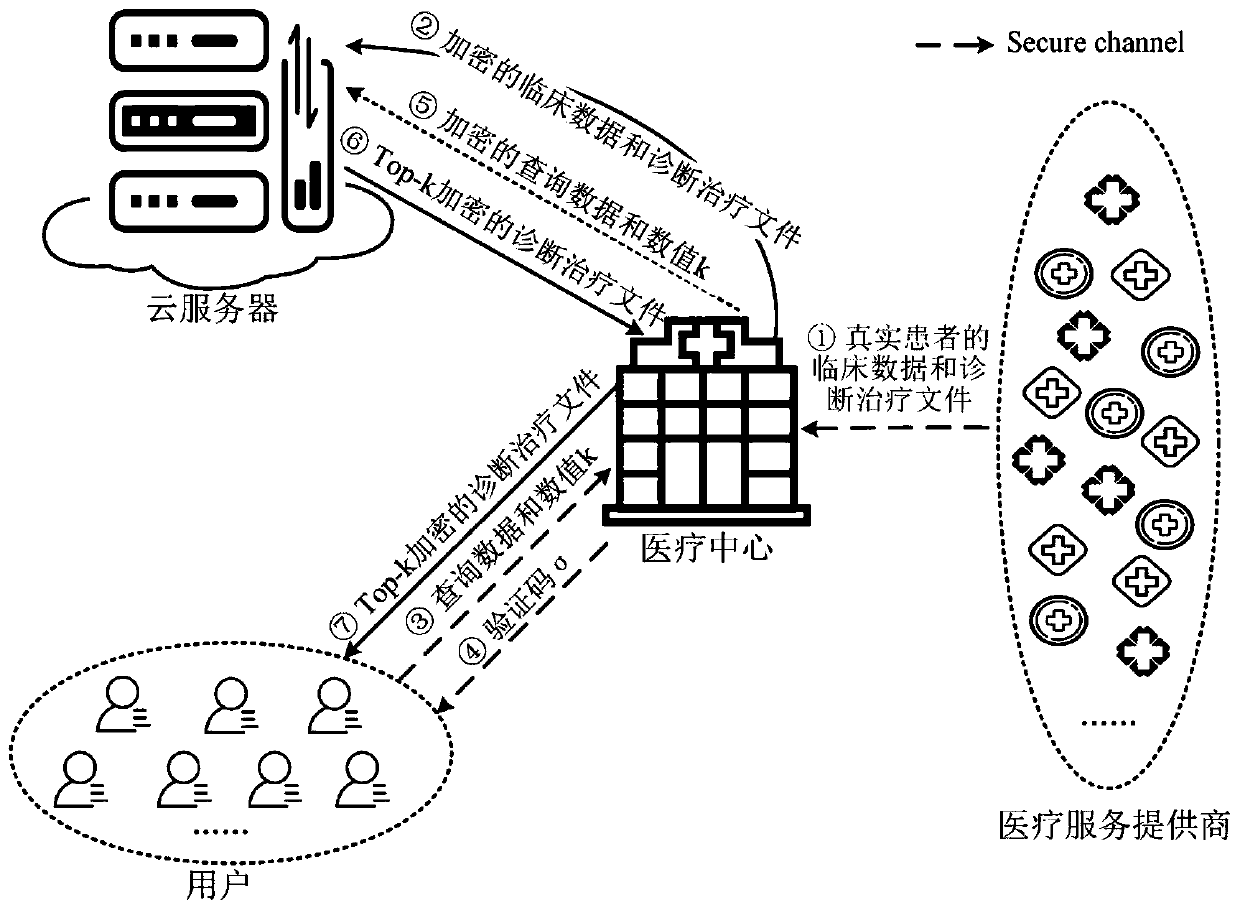
[0056] The overall model of a privacy-preserving Top-k disease matching method in the electronic medical system is as follows: figure 1 shown. The system mainly includes four entities: medical service providers, medical centers, cloud servers and users. In order to realize the digitalization of the medical system and shorten the time and spatial distance of users' visits, medical service providers will issue corresponding diagnosis and treatment documents based on the clinical data of real patients, and combine the clinical data of these real patients with the corresponding diagnosis and treatment documents. The file is uploaded to the cloud server. The user obtains his own physical signs through the wearable device to ge...
Embodiment 2
[0063] This example elaborates our experiments on a privacy-preserving Top-k disease matching method in an electronic medical system. We mainly experiment with the method under four scenarios.
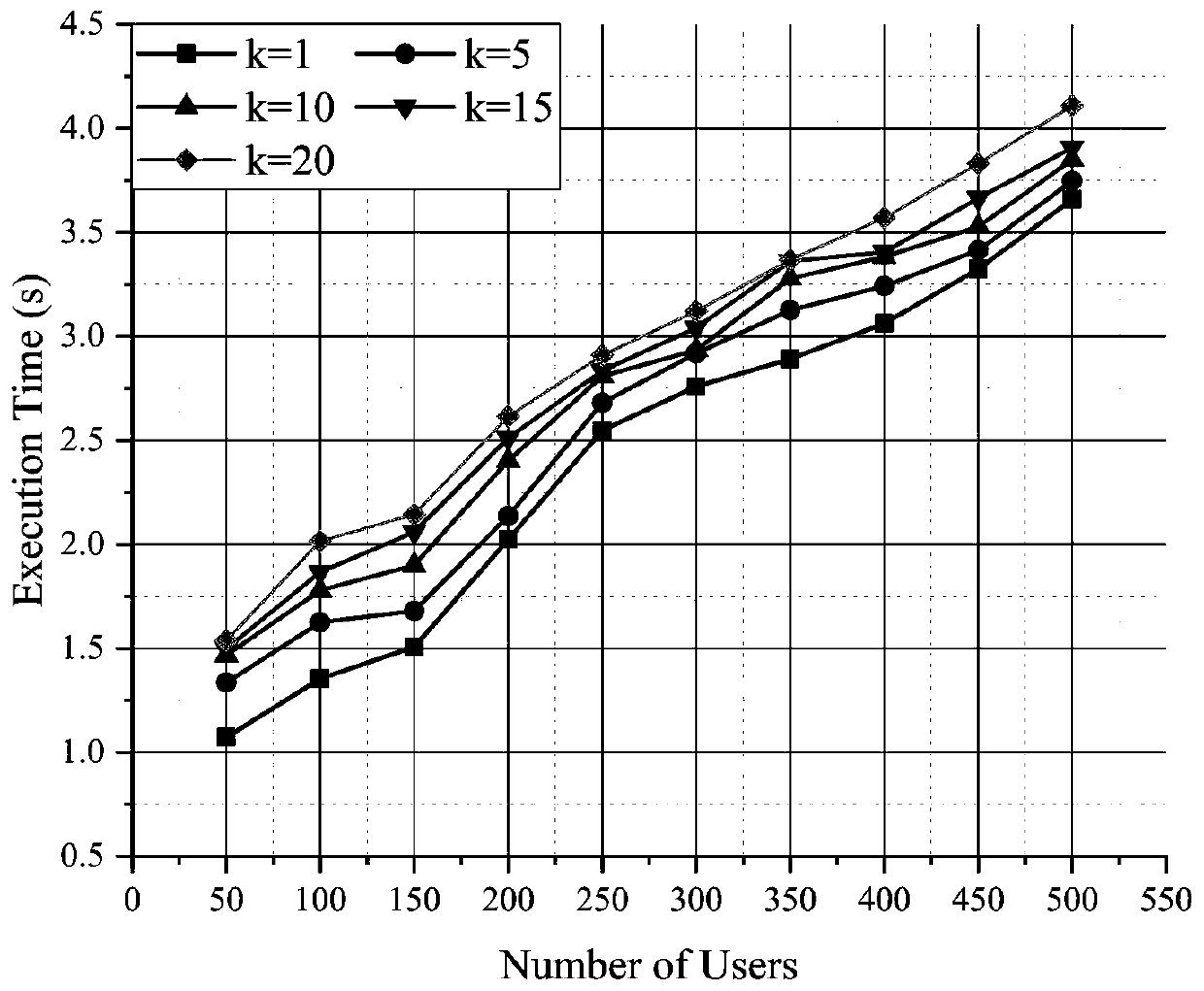
[0064] First of all, for the experiment conducted under the scenario of different numbers of users in the electronic medical system and the number of different diagnosis and treatment files returned (that is, the value of k), we conducted a simulation experiment of matching diagnosis and treatment files in this scenario, and the experimental results Such as image 3 As shown, the x-axis represents the number of users, and the y-axis represents the execution time. This experiment is mainly carried out on the case where the user value is from 50 to 500 and the k value is 1, 5, 10, 15, 20. As the number of users increases, the time required will become longer. But when the number of users is constant, k has little effect on the execution time. One of the main reasons is that the value r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com