Method and system for privacy-preserving social media advertising
A sum and ciphertext technology, applied in the field of information security, can solve problems such as personal data leakage, misuse of personal data, and seller influence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
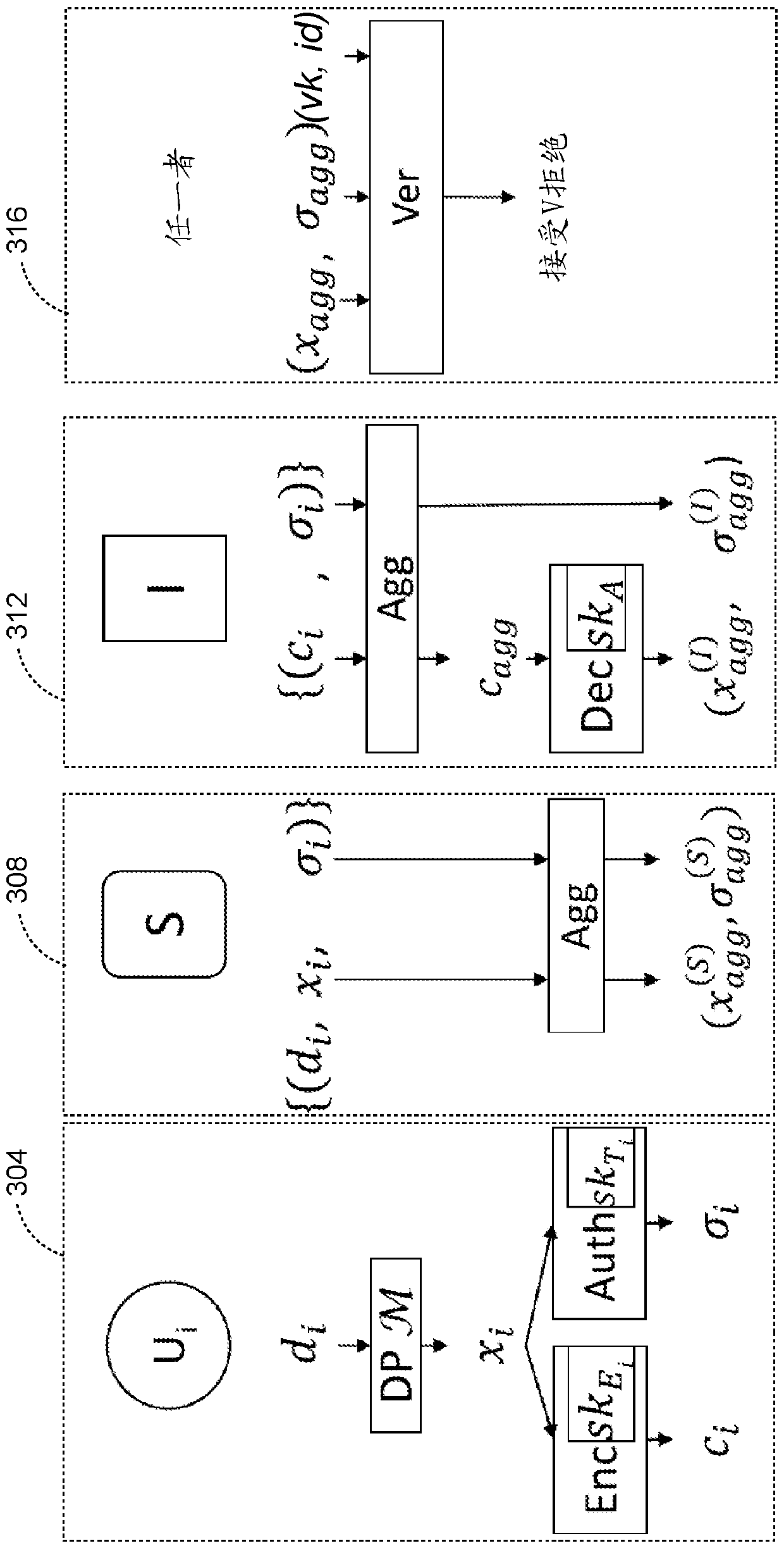
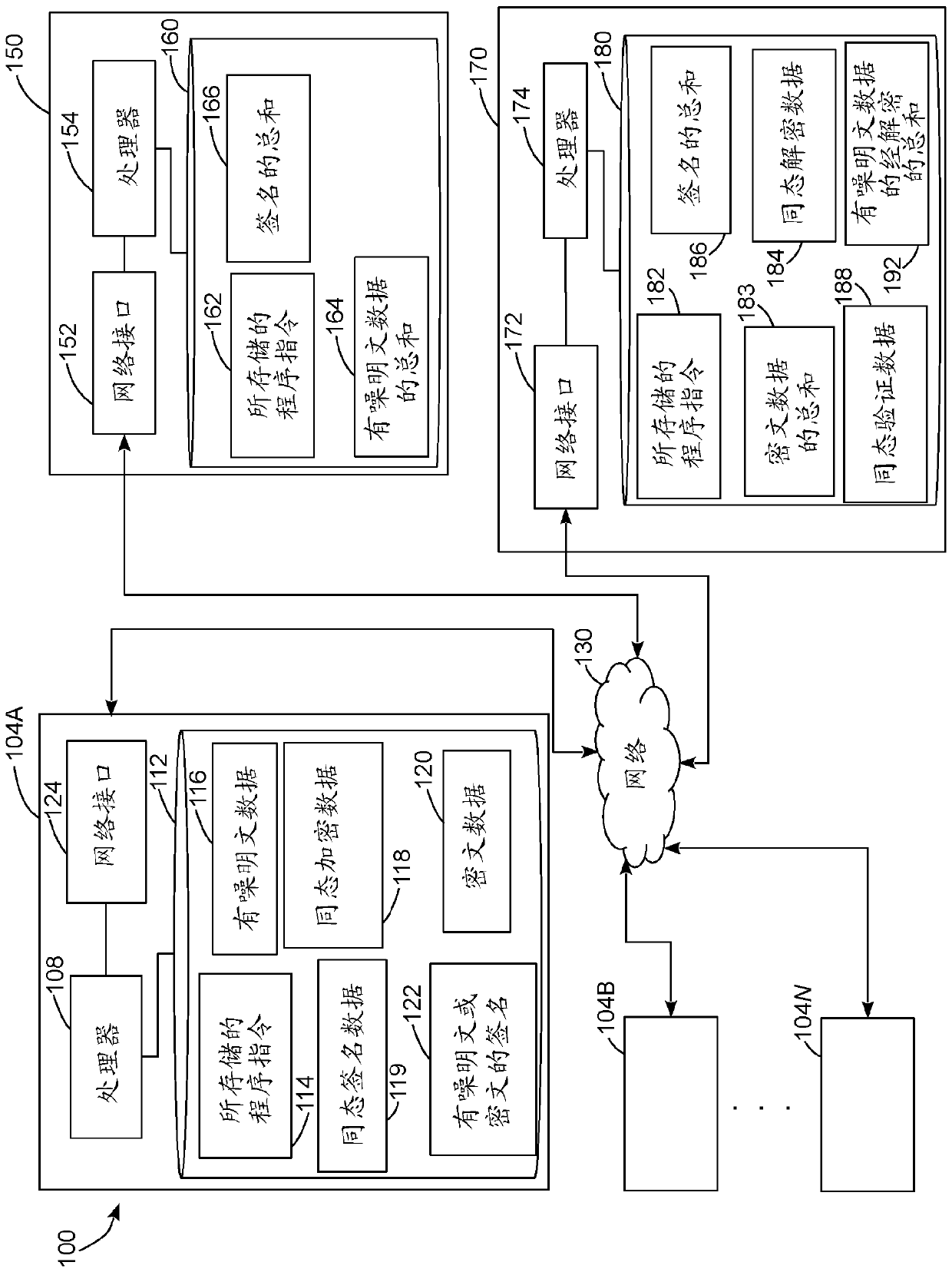
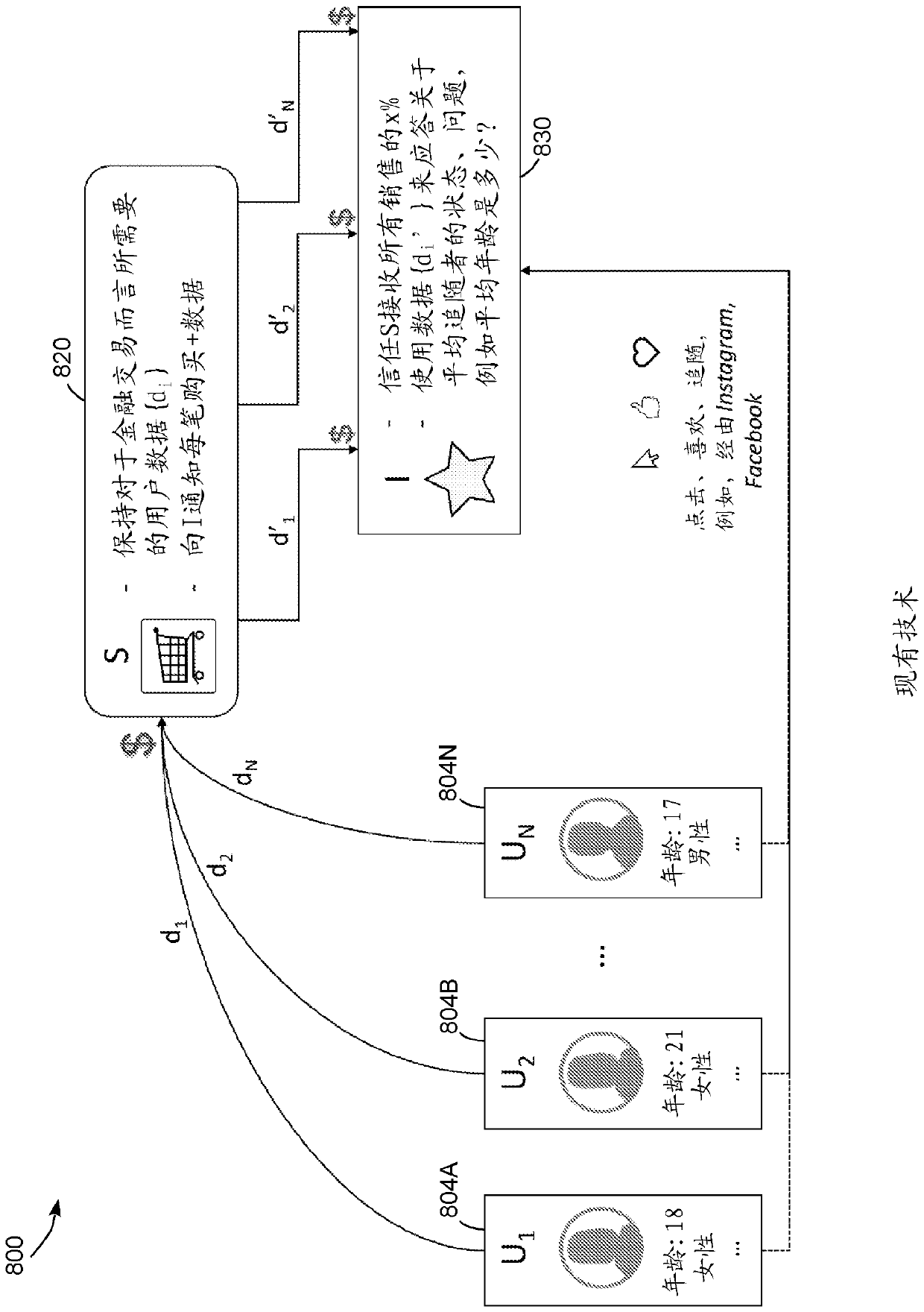
[0039] For the purpose of promoting an understanding of the principles of the embodiments described herein, reference is now made to the drawings and description in the following written specification. No limitation on the scope of subject matter is intended by reference. This patent also covers any alterations and modifications of the illustrated embodiments, and further applications of the principles of the described embodiments as would normally occur to one skilled in the art to which this document pertains.
[0040] As used herein, the terms "isomorphic" and "homomorphic" refer to properties of some cryptographic systems that enable a computerized system to perform operations by using encrypted ciphertext data that The data, after decryption, produces a plaintext result that matches the result of the same operation if applied to the plaintext data. For example, in this paper we describe cryptosystems that provide additive isomorphisms, which enable a computer to combine ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com