Terminal tracing method based on traffic learning
A terminal and traffic technology, applied in the field of terminal traceability based on traffic learning, can solve problems such as the difficulty of active traceability, the inability to trace criminal individuals through active traceability, and the non-existence of information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
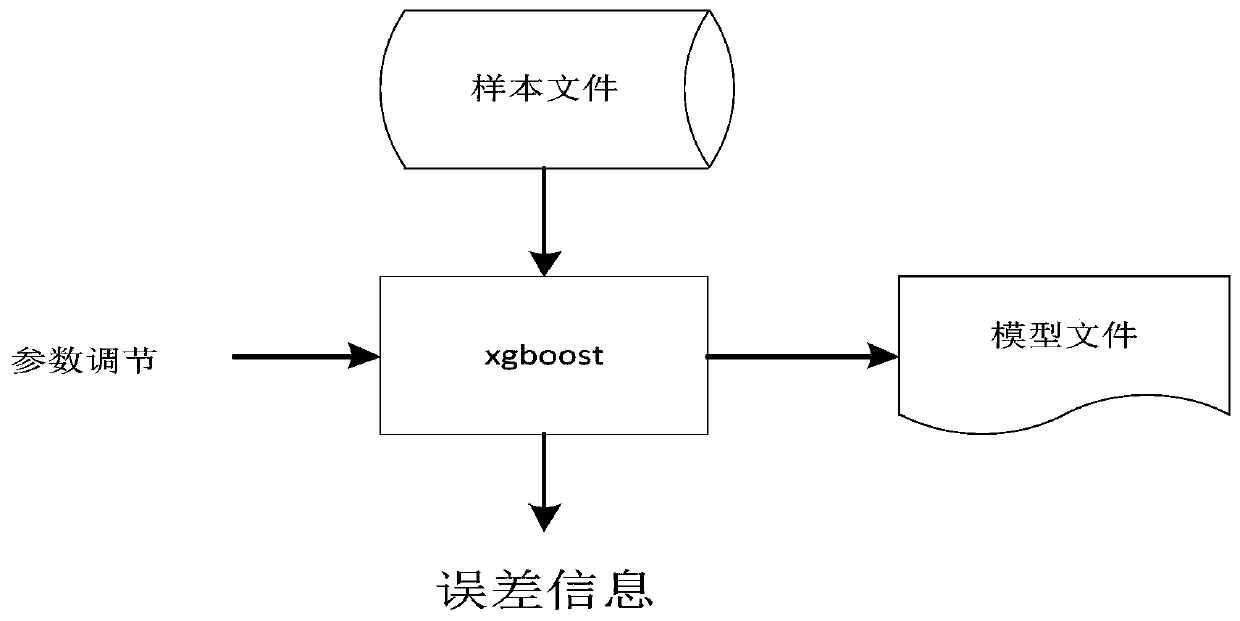
[0068] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
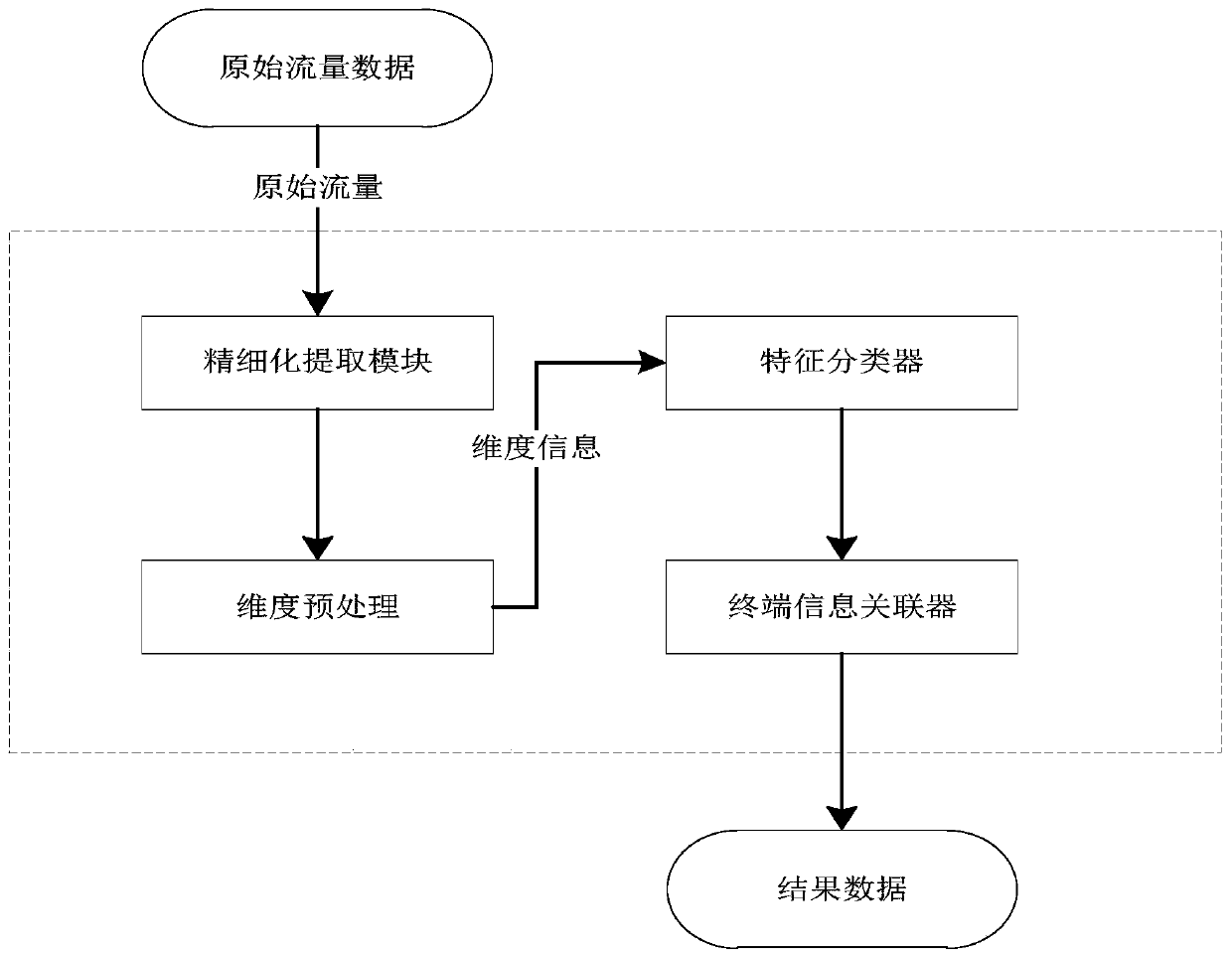
[0069] 1. Refined extraction module
[0070] The refined extraction module mainly adopts DFI (Deep / Dynamic Flow Inspection) and DPI (DeepPacket Inspection) technical means to extract terminal information (only part of the data contains) in network traffic for traceability and dimension information for forming machine learning .
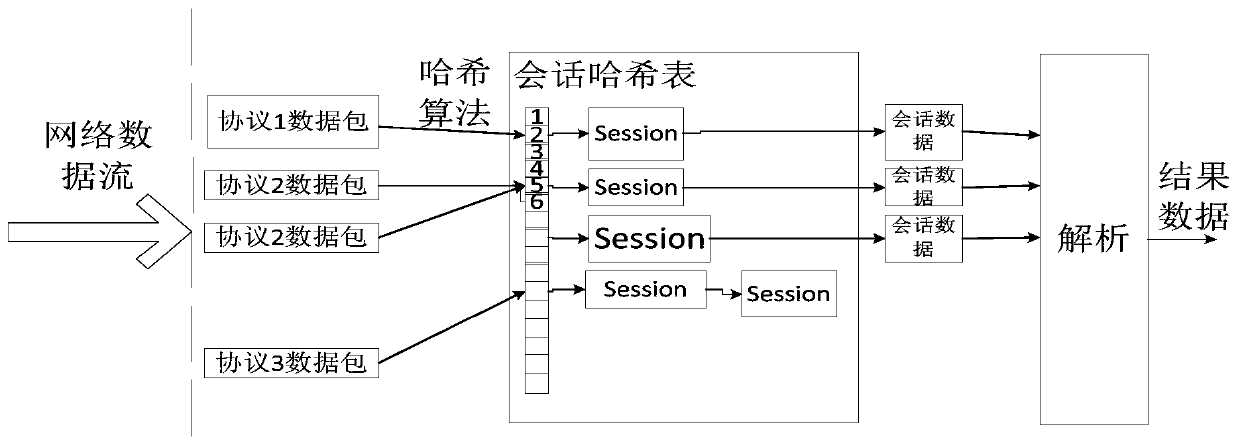
[0071] (1) Packet reassembly
[0072] Transmission Control Protocol TCP (Transmission Control Protocol, RFC 793, RFC 1122, RFC813, RFC 816, RFC 879, RFC 896, RFC 889, RFC 964) is a protocol that provides host-to-host high-reliability communication in the network, according to RFC793 Regulation. The sequence number (Sequence Number) in the TCP header is used to specify the position of the data packet in the entire session, and the sequence number is the key to TCP session reassembly.
[0073] Session: The data flow of a sock...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com