Key updating method and device and storage medium
A key update and device technology, applied in the blockchain field, can solve problems such as error-prone, long update cycle, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
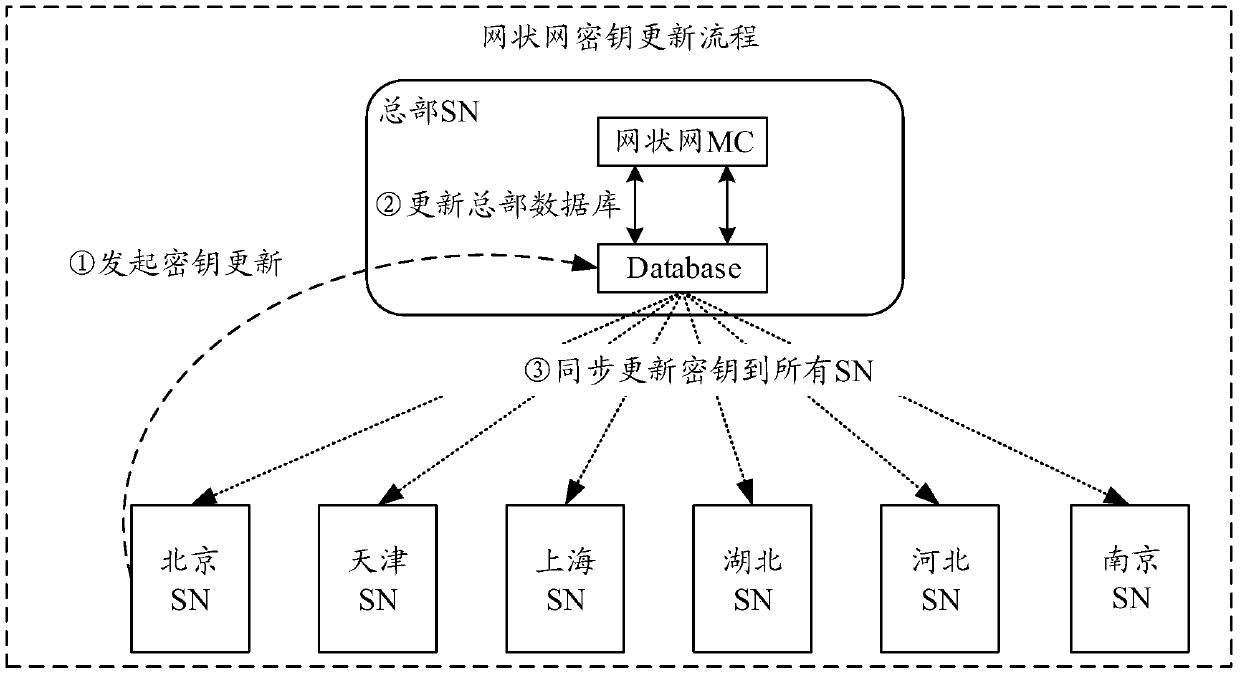
[0057] The first key update method is given here, applied to the first device, such as figure 2 As shown, key update methods include:
[0058] Step 201: Obtain the key update request of the service node corresponding to the first device, and generate corresponding key update information for the key update request; wherein, the key update information includes at least service node information and a new key;
[0059] Step 202: Send key update information to at least one second device, so that at least one second device can verify the validity of the key update information to obtain a verification result;
[0060] Step 203: receiving a verification result of at least one second device, and generating a corresponding block for the new key based on the verification result of at least one second device;
[0061] Step 204: Send the block to at least one second device, so that the at least one second device adds the block to the local blockchain to generate a new blockchain.
[006...
Embodiment 2
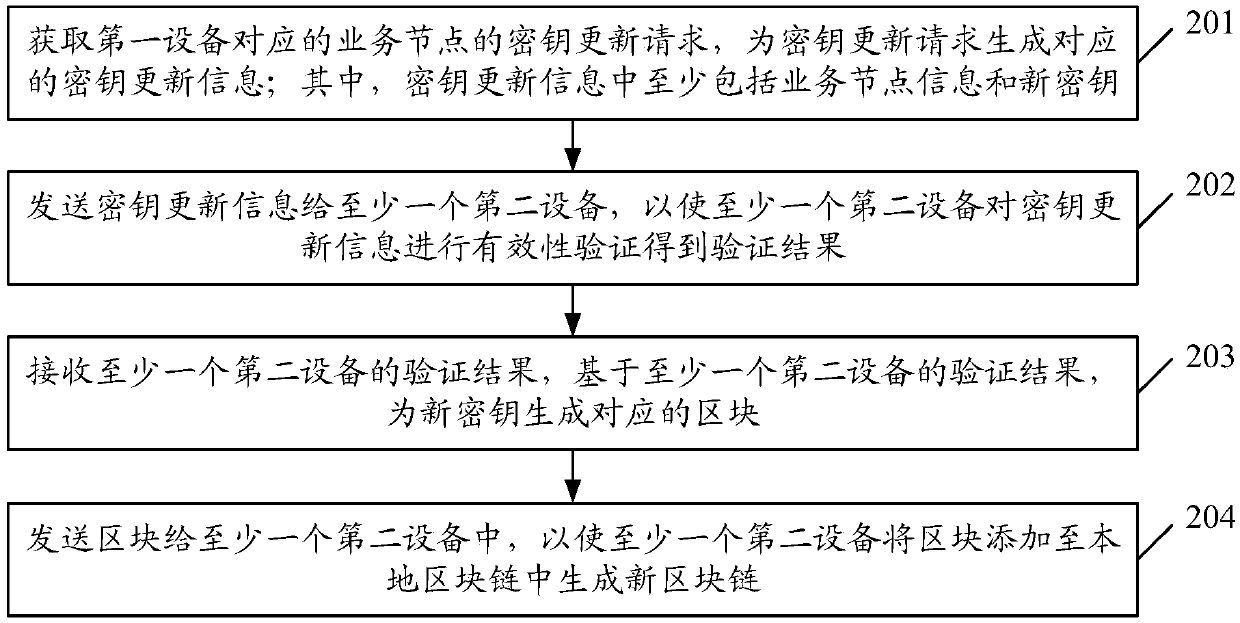
[0074] In order to better reflect the purpose of the present invention, on the basis of Embodiment 1 of the present invention, further illustrations are made, such as image 3 As shown, the key update method specifically includes:
[0075] Step 301: Obtain the key update request of the service node corresponding to the first device, and generate corresponding key update information for the key update request; wherein, the key update information includes at least service node information and a new key;
[0076] Step 302: Send key update information to at least one second device, so that at least one second device can verify the validity of the key update information to obtain a verification result;
[0077] Step 303: When the verification results of at least N second devices in at least one second device are valid, determine that the key update information is valid; generate a corresponding block for the new key;
[0078] Step 304: Send the block to at least one second device,...
Embodiment 3
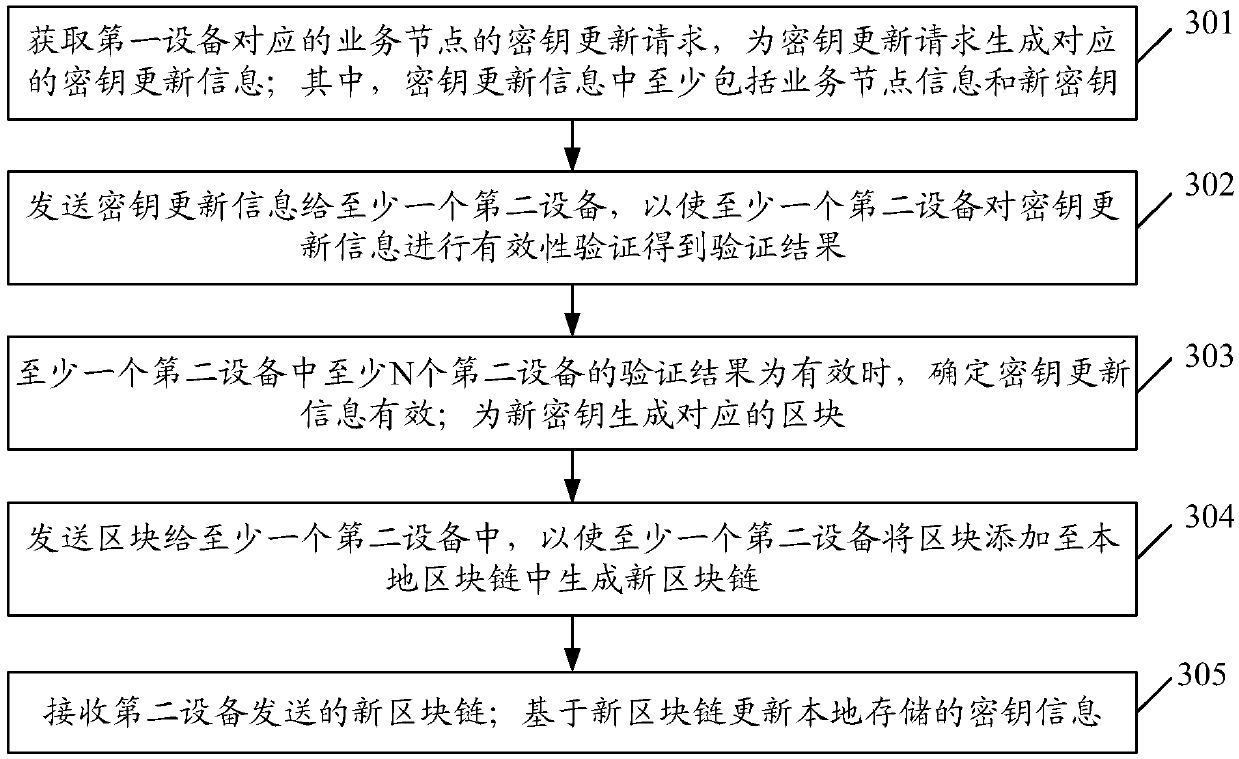
[0093] In order to better reflect the purpose of the present invention, on the basis of Embodiment 1 of the present invention, further illustrations are made, such as Figure 4 As shown, the key update method specifically includes:
[0094] Step 401: Obtain the key update request of the service node corresponding to the first device, and generate corresponding key update information for the key update request; wherein, the key update information includes at least service node information and a new key;
[0095] Step 402: Send key update information to at least one second device, so that at least one second device performs validity verification on the key update information to obtain a verification result;
[0096] Step 403: receiving a verification result of at least one second device, and generating a corresponding block for the new key based on the verification result of at least one second device;
[0097] Step 404: Send the block to at least one second device, so that at ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com