Private data distribution method based on proxy re-encryption
A technology for proxy re-encryption and private data, applied in the field of data processing in the blockchain, it can solve the problem that the public key encryption system cannot outsource the private data distribution business to a third party for operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
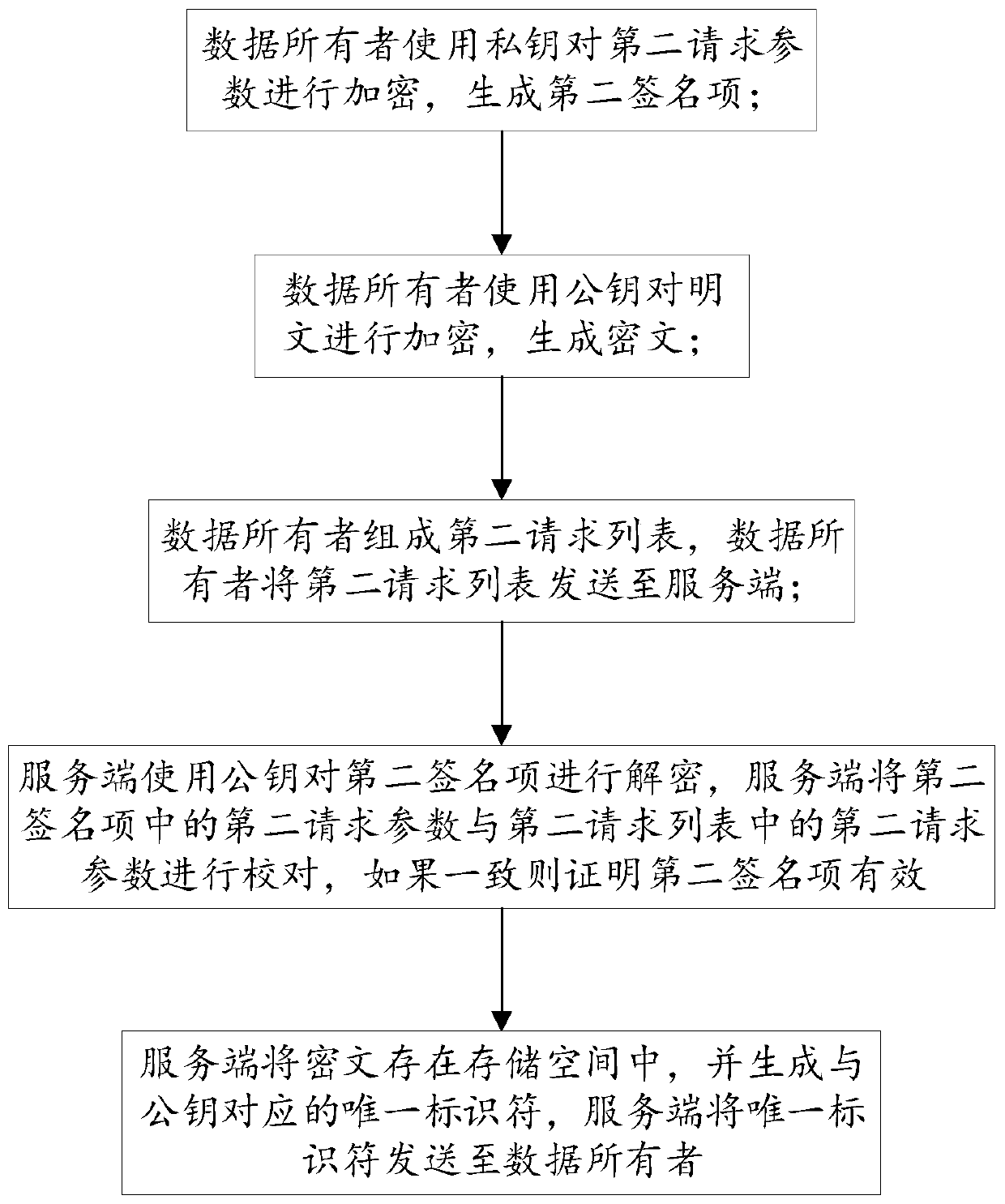
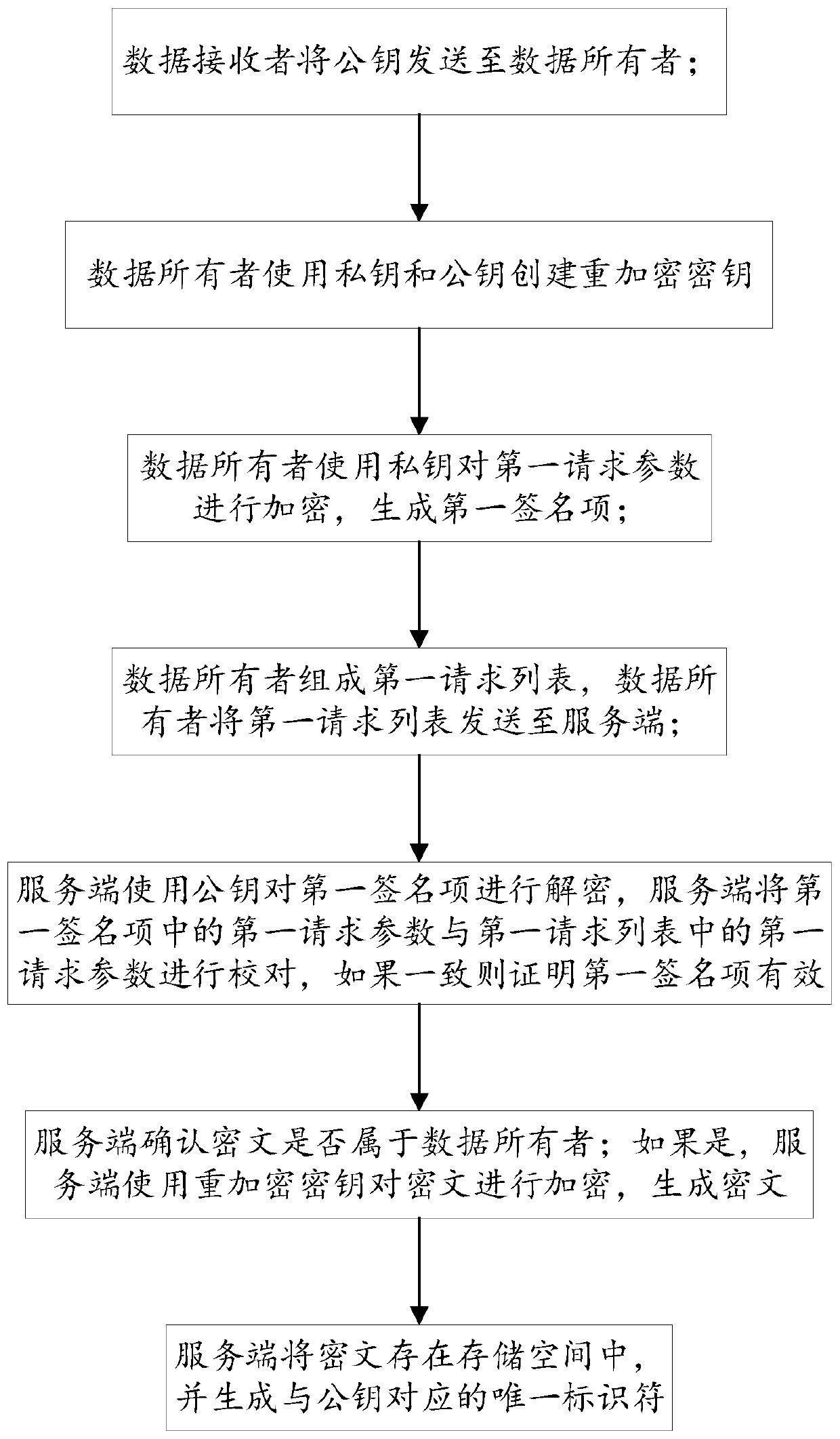
[0086] The data owner establishes the structural content of the private data in the second request list, and the structural content includes a special identifier and description content;
[0087] Special identifiers are used to identify the structure properties of the structure content;
[0088] The description includes: the data format of the plaintext m, the encryption algorithm type of the plaintext m, and the ciphertext c A and public key pk A ;The structure content is expressed as the first byte array, and the structure properties of the structure content are:
[0089] In the first byte array, the first 2 bytes represent a special identifier, the data format of the plaintext m is represented as 2 bytes, the encryption algorithm type of the plaintext m is represented as 2 bytes, and the ciphertext c A Represented as the second byte array, the public key pk A represented as a third byte array;
[0090] The data owner performs a hash operation on the structure content to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com