Malicious scanning ip detection method, system, device, equipment and storage medium
A detection method and malicious technology, applied in the computer field, to achieve the effect of accurate and fast detection of malicious scanning IP
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
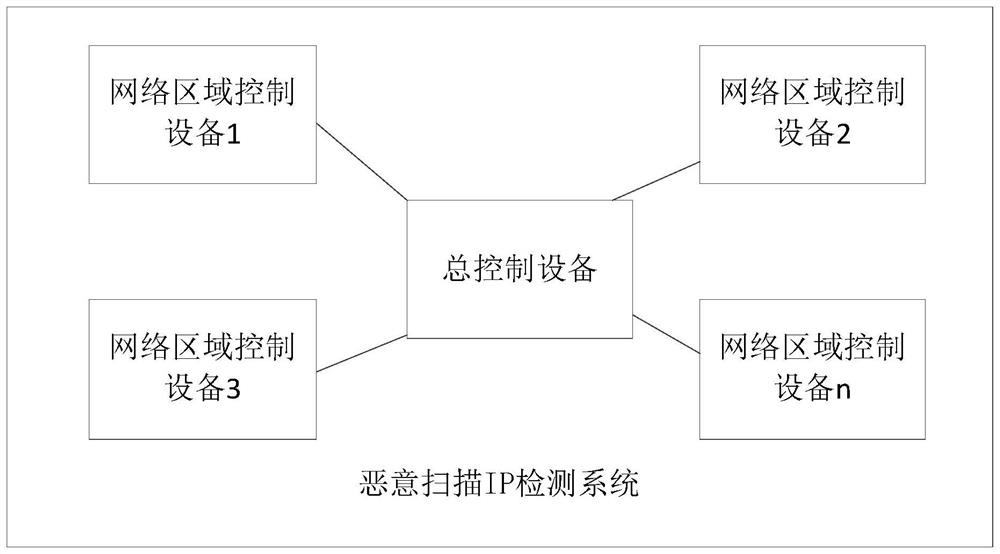
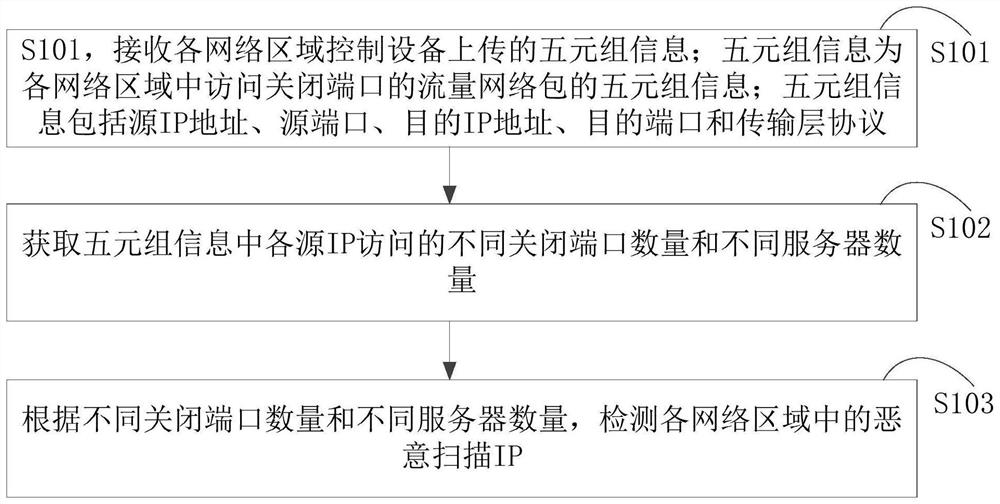
[0085] Optionally, as in Figure 6 As shown, in the S303 step, a possible implementation manner of obtaining the quintuple information of the traffic network packet accessing the closed port includes:
[0086] S401. According to the destination IP in each quintuple information, search for the open port information list reported by the server corresponding to each traffic network packet.
[0087] Specifically, each network area control device obtains the destination IP in each traffic network packet, and then also obtains a list of open port information reported by the server to which each traffic network packet belongs. That is, each network area control device determines the corresponding server according to the destination IP, and then obtains the list of open port information reported by the corresponding server.
[0088] S402. If the destination port in the quintuple information of the corresponding traffic network packet does not exist in the open port information list r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com