Block chain private transaction method and device and electronic equipment
A transaction method, block chain technology, applied in the field of devices and electronic equipment, block chain privacy transaction method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
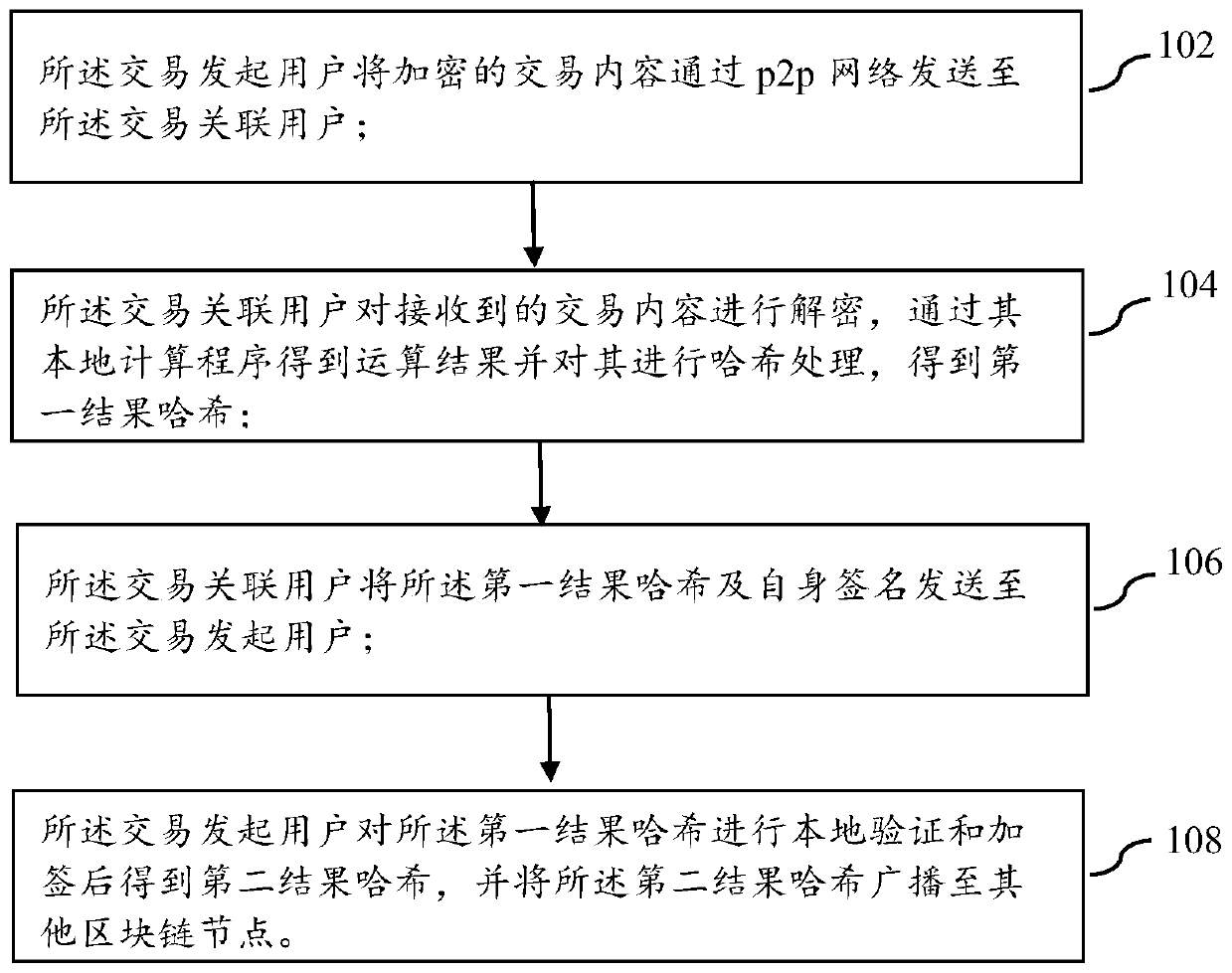
[0028] refer to figure 1 As shown, it is a schematic diagram of the steps of a blockchain private transaction method provided by the embodiment of this specification, wherein the members of the private transaction include the transaction initiator user and the transaction associated user on the blockchain node; the method may include the following steps:
[0029] Step 102: the transaction initiating user sends the encrypted transaction content to the transaction associated user through the p2p network;
[0030] Step 104: The transaction-associated user decrypts the received transaction content, obtains the calculation result through its local calculation program, and performs hash processing on it to obtain the first result hash;
[0031] Step 106: The transaction-associated user sends the first result hash and its own signature to the transaction initiating user;
[0032] Step 108: The transaction initiating user obtains a second result hash after locally verifying and signi...
Embodiment 2
[0053] This embodiment specifically provides a blockchain private transaction device, wherein members of the private transaction include transaction initiators and transaction associated users on blockchain nodes; the device includes:
[0054] The first sending module 202: used for the transaction initiation user to send the encrypted transaction content to the transaction associated user through the p2p network;
[0055] The first processing module 204: used for the transaction associated user to decrypt the received transaction content, obtain the operation result through its local calculation program and perform hash processing on it, and obtain the first result hash;
[0056] The second sending module 206: used for the transaction-associated user to send the first result hash and his own signature to the transaction initiation user;
[0057] The second processing module 208: used for obtaining the second result hash after the transaction initiation user performs local veri...
Embodiment 3
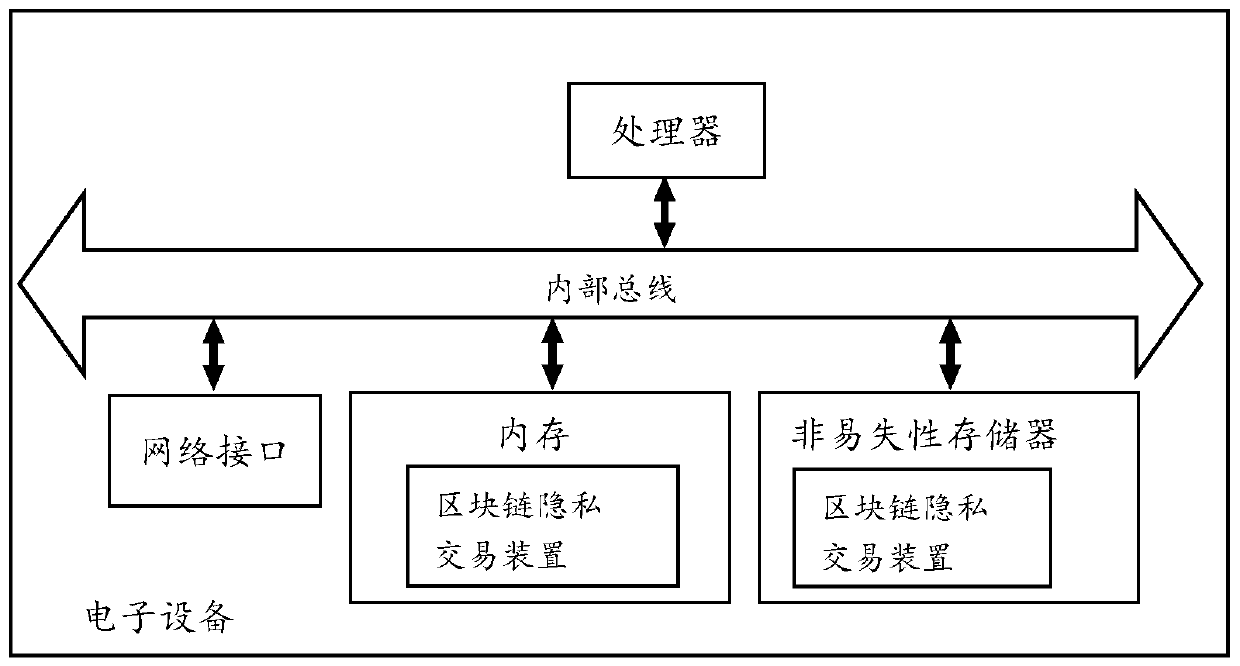
[0068] Refer below figure 2 The electronic equipment of the embodiment of this specification is introduced in detail. Please refer to figure 2 , at the hardware level, the electronic device includes one or more processors and memory. Optionally also include internal bus and network interface. Wherein, the memory may include a memory, such as a high-speed random-access memory (Random-Access Memory, RAM), and may also include a non-volatile memory (Non-Volatile Memory), such as at least one disk memory. Of course, the electronic device may also include hardware required by other services.
[0069] The processor, network interface, and memory may be interconnected via an internal bus, which may be an Industry Standard Architecture (ISA) bus, a Peripheral Component Interconnect (PCI) bus, or an extended industry standard Structure (Extended Industry Standard Architecture, EISA) bus, etc. The bus can be divided into address bus, data bus, control bus and so on. For convenie...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com