Android environment secret key segmentation processing method and device
A processing method and key technology, which is applied in key distribution, can solve the problems of high development cost, limited security application, inability to adapt to mobile phones at the same time, and achieve the effect of increasing security and facilitating promotion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
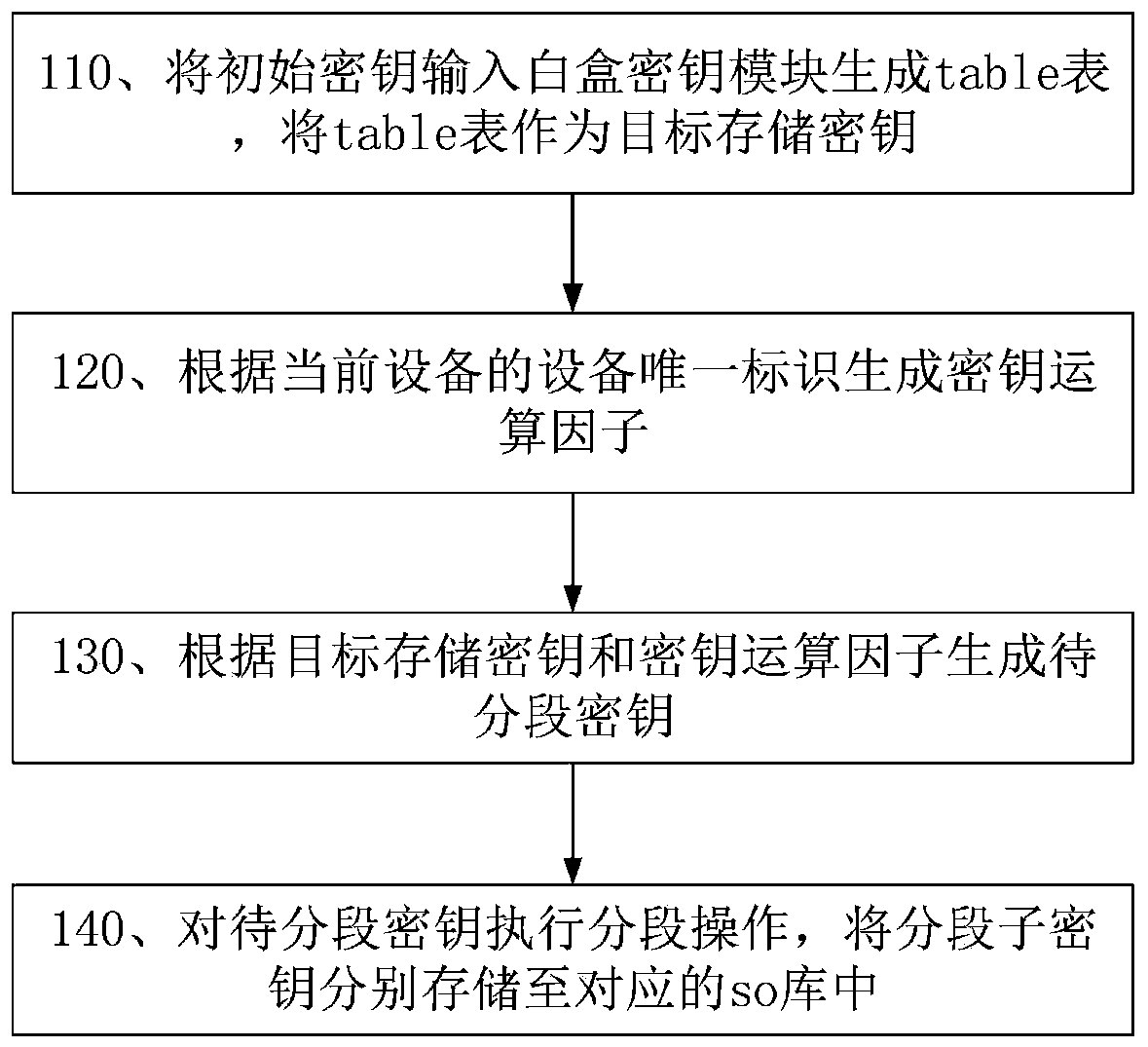
[0040] Embodiment 1 of the present application provides a method for segmented storage of keys in an Android environment, such as figure 1 shown, including:
[0041] Step 110, input the initial key into the white box key module to generate a table table, and use the table table as the target storage key;
[0042] In the embodiment of this application, the white-box key module uses white-box encryption calculation to encrypt the input initial key pkey to generate a table table, and this table is used as the target storage key key;
[0043] Since the white-box encryption and decryption algorithm cannot decrypt the correct initial key according to the encryption and decryption key, this application uses white-box encryption and decryption calculation as a more secure encryption and decryption algorithm to increase the security of key storage.
[0044] Step 120, generating a key calculation factor according to the unique device identifier of the current device;
[0045] Since ea...
Embodiment 2
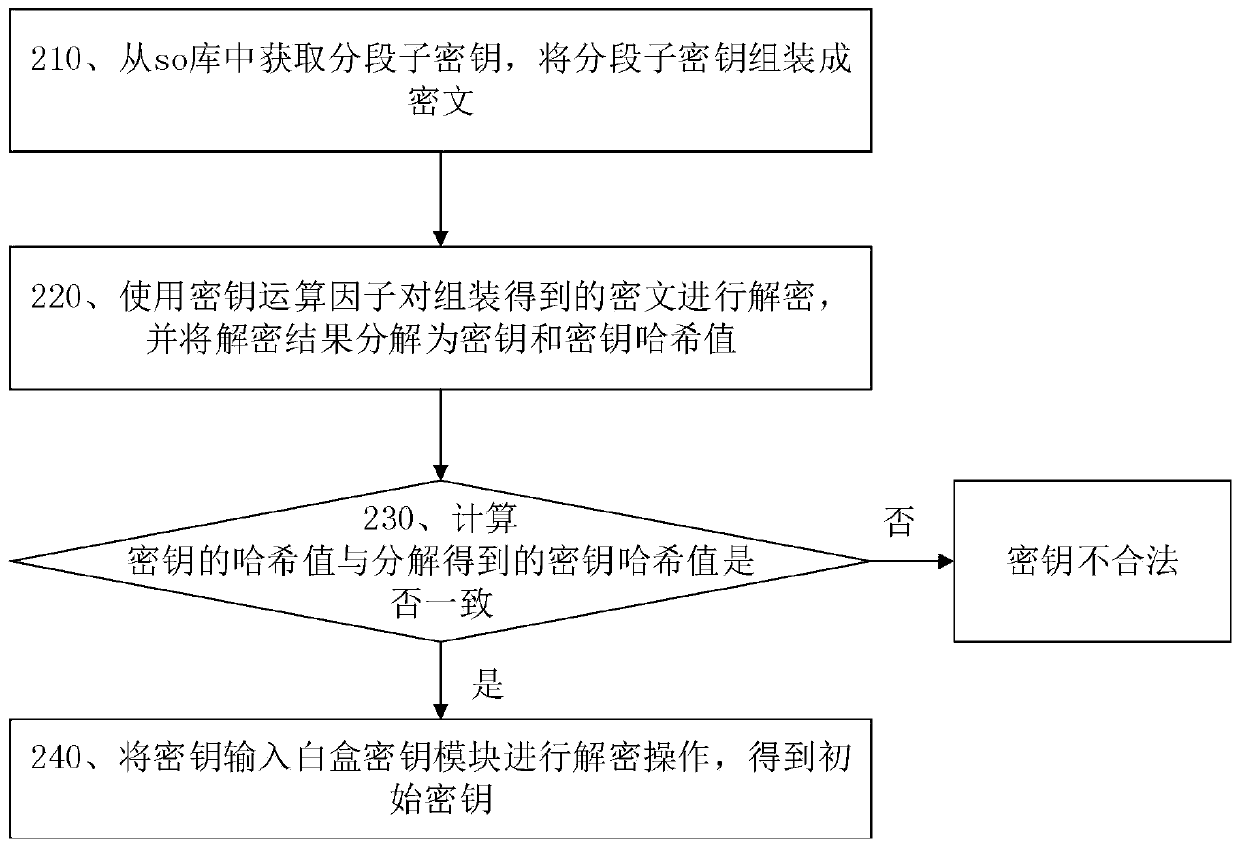
[0064] Embodiment 2 of the present application provides an Android environment key segment extraction method, such as figure 2 shown, including:
[0065] Step 210, obtain segmented subkeys from the so library, and assemble the segmented subkeys into ciphertext;
[0066] Specifically, when key extraction is required, in response to receiving the key extraction instruction, the call interface sends a key extraction instruction to the function so library, and the function so library extracts the corresponding storage from the segmented key storage so library. For example, after the libmainFunc.so library receives the key extraction instruction from the Android device, it extracts the corresponding stored segment subkeys from the libsecurity1.so library, libsecurity2.so library, and libsecurity3.so library respectively. Then determine the order of assembly according to the segment identification (ie the first byte of the data storage format) of each segment subkey, and then asse...
Embodiment 3
[0075] Embodiment 3 of the present application provides an Android environment key segmentation processing device, including:
[0076] Key segmentation storage module, executes the Android environment key segmentation storage method as described in embodiment one;
[0077] The key segmentation extraction module executes the Android environment key segmentation extraction method as described in Embodiment 2.
[0078] Adopting the technical scheme of the present application can achieve the following effects:
[0079] 1. Save development costs, do not distinguish between mobile phone manufacturers and chip models used, and the pure Android environment key segment storage scheme can be used universally on all Android system mobile phones, which is conducive to the promotion of security-related applications;
[0080] 2. There is no need for a TEE environment. On the basis of relatively ensuring data security, keys can be used to process sensitive data on low-end mobile phones, whi...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap