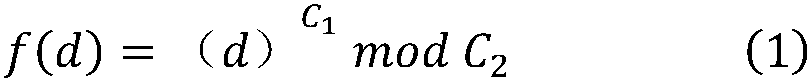Mobile malicious user identification method and system based on communication behavior rule
A malicious user, identification method technology, applied in wireless communication, security devices, electrical components, etc., can solve the problem that the identification method cannot be used directly
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
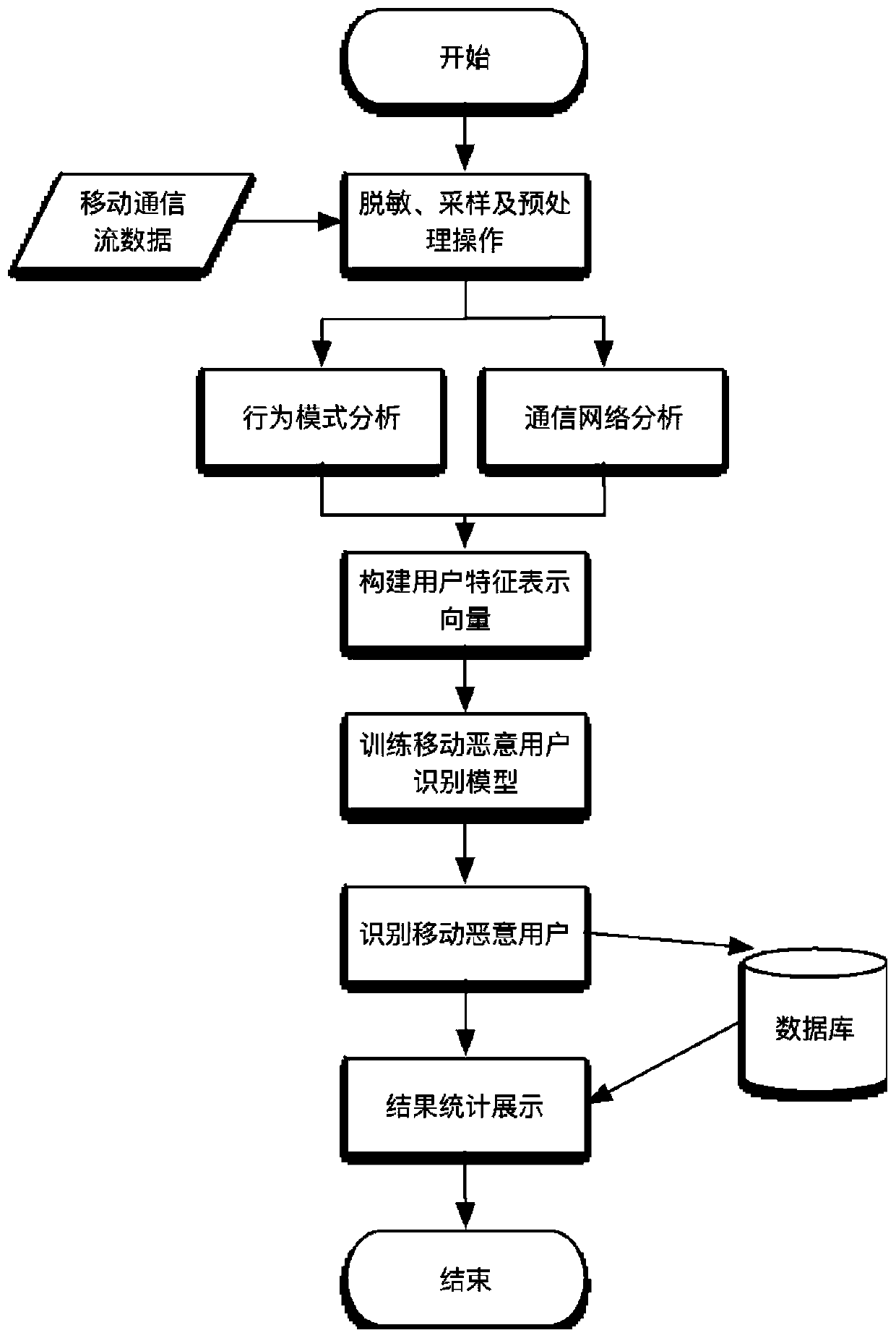
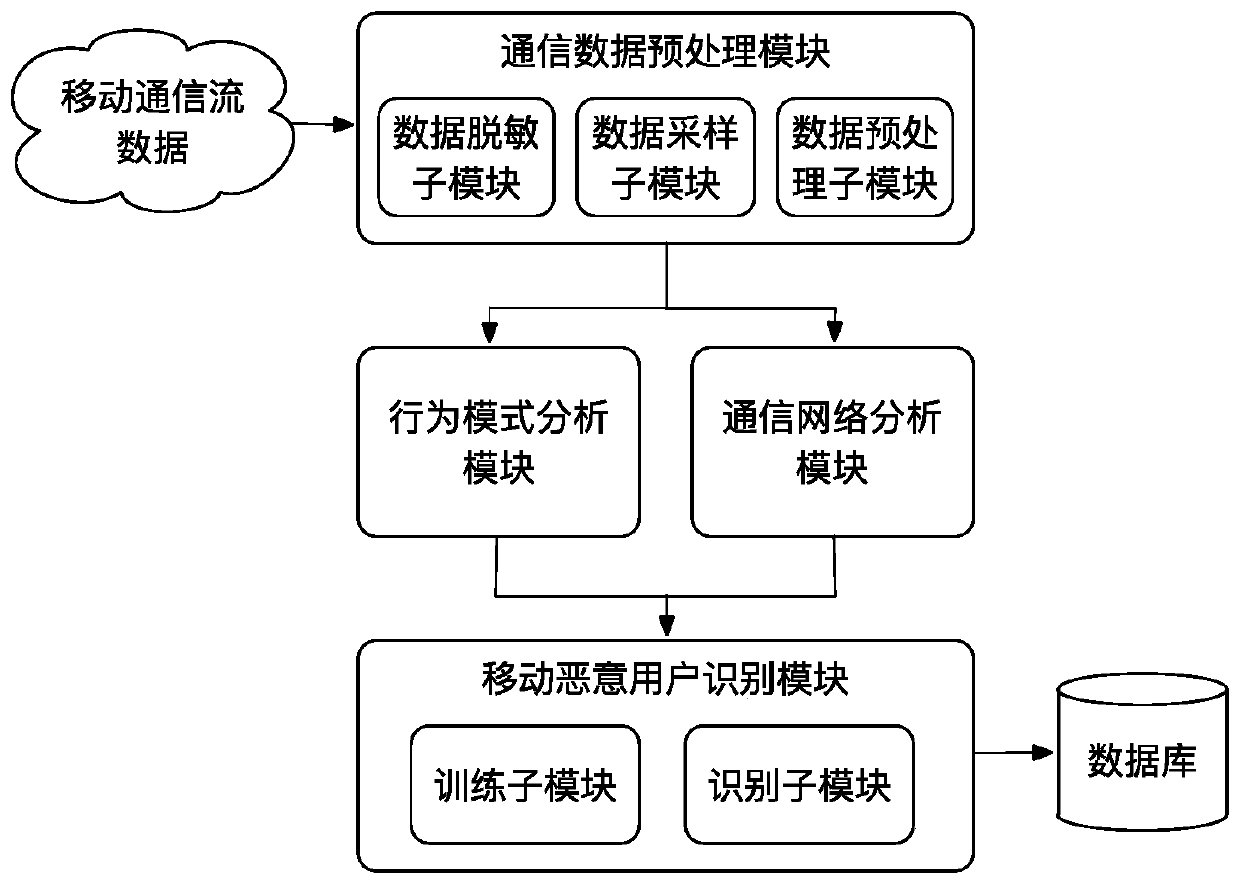
[0057] Such as figure 1 As shown, a mobile malicious user identification method based on communication behavior rules of the present invention includes as follows:
[0058] Step 1: Collect data based on the non-uniform sampling method in the desensitized mobile communication flow data, and perform preprocessing operations.
[0059] Firstly, the desensitization operation is performed on the mobile communication flow data. Because the mobile phone number segment represents different meanings (2-digit country code, 3-digit mobile access code, 4-digit HLR identification code, 4-digit mobile subscriber number, and 11-digit mobile phone number is composed of the last three items), the mobile phone number is divided into The segment hash method; for the call record, only the start time and end time of the call are saved, and for the SMS record, only the co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com