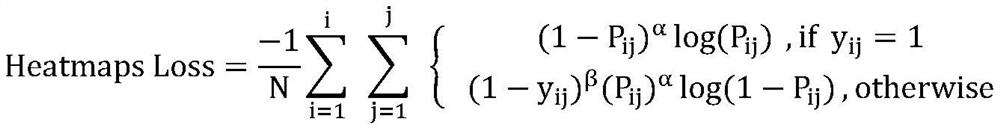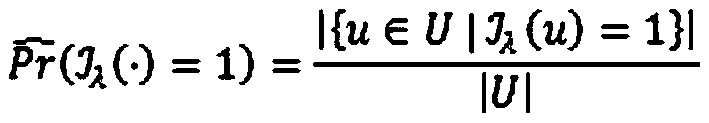Patents
Literature
30results about How to "No privacy involved" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
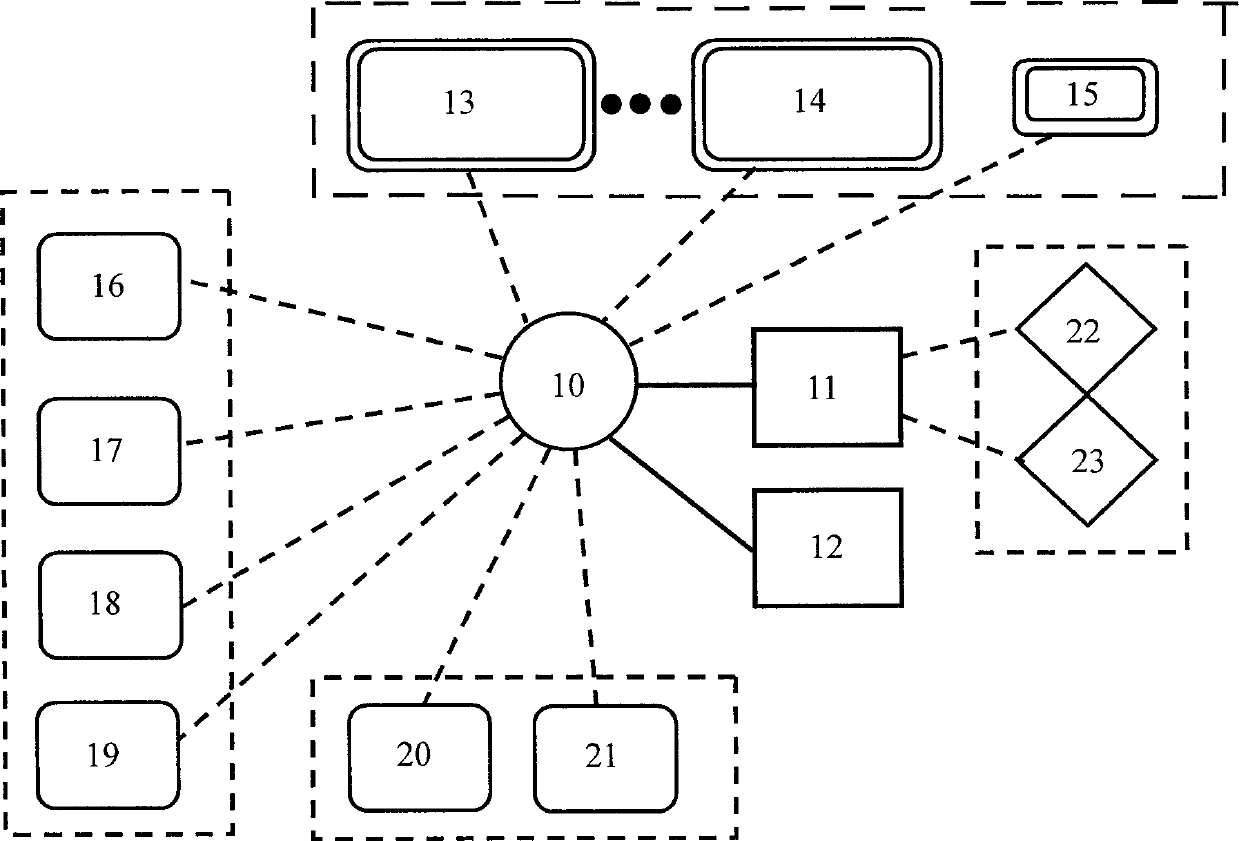
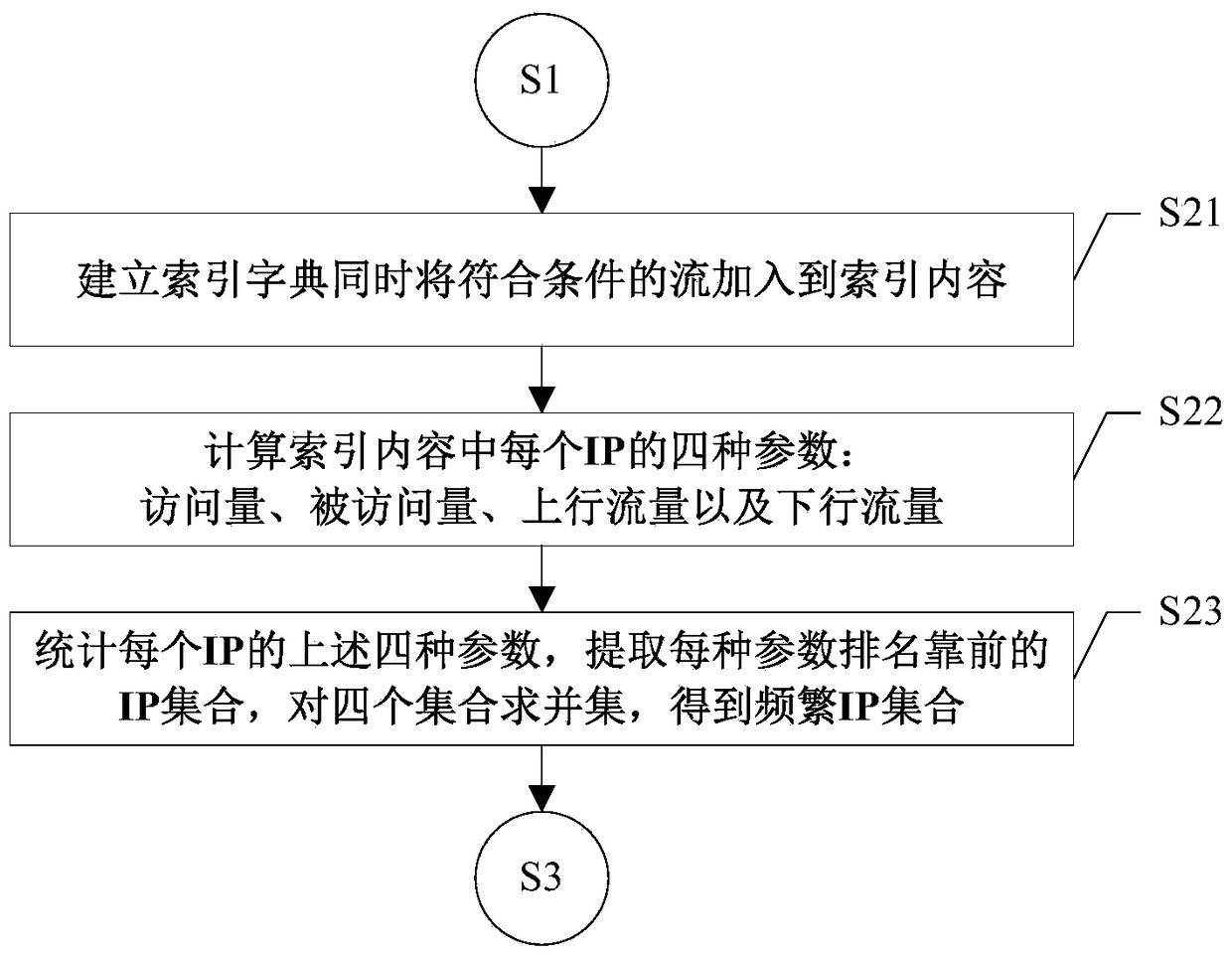
Traffic classification method and device based on transport layer characteristics
InactiveCN102271090AImplement classificationTraffic Classification ImplementationData switching networksData streamTransport layer
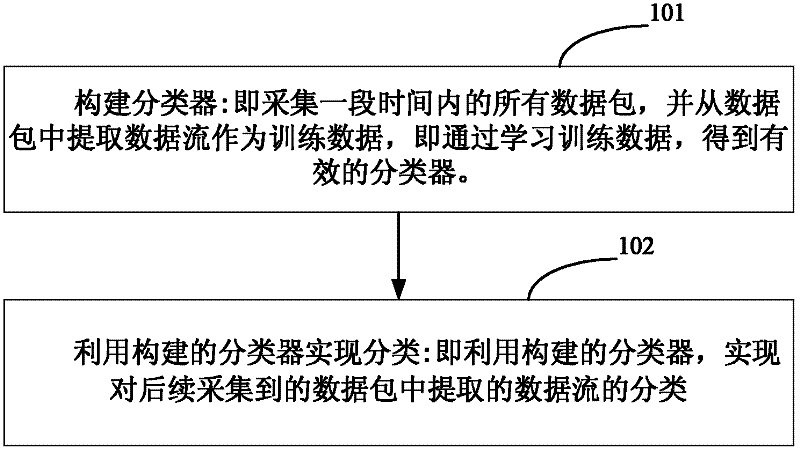
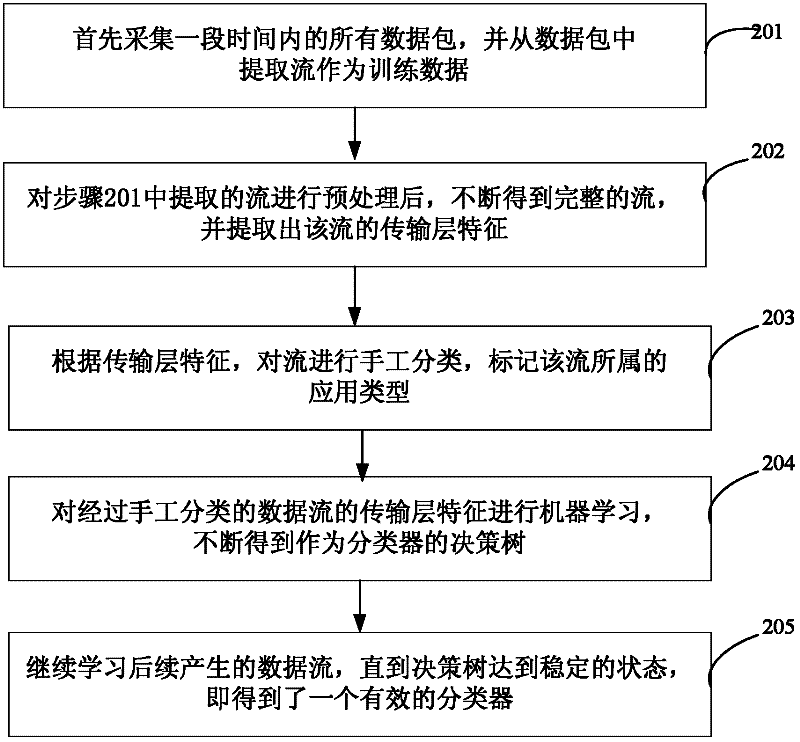
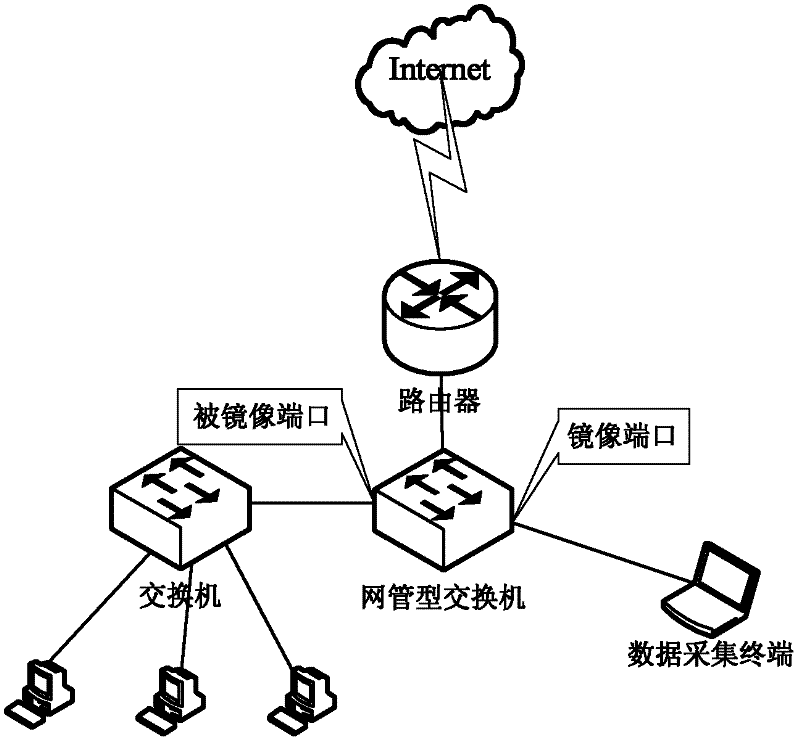
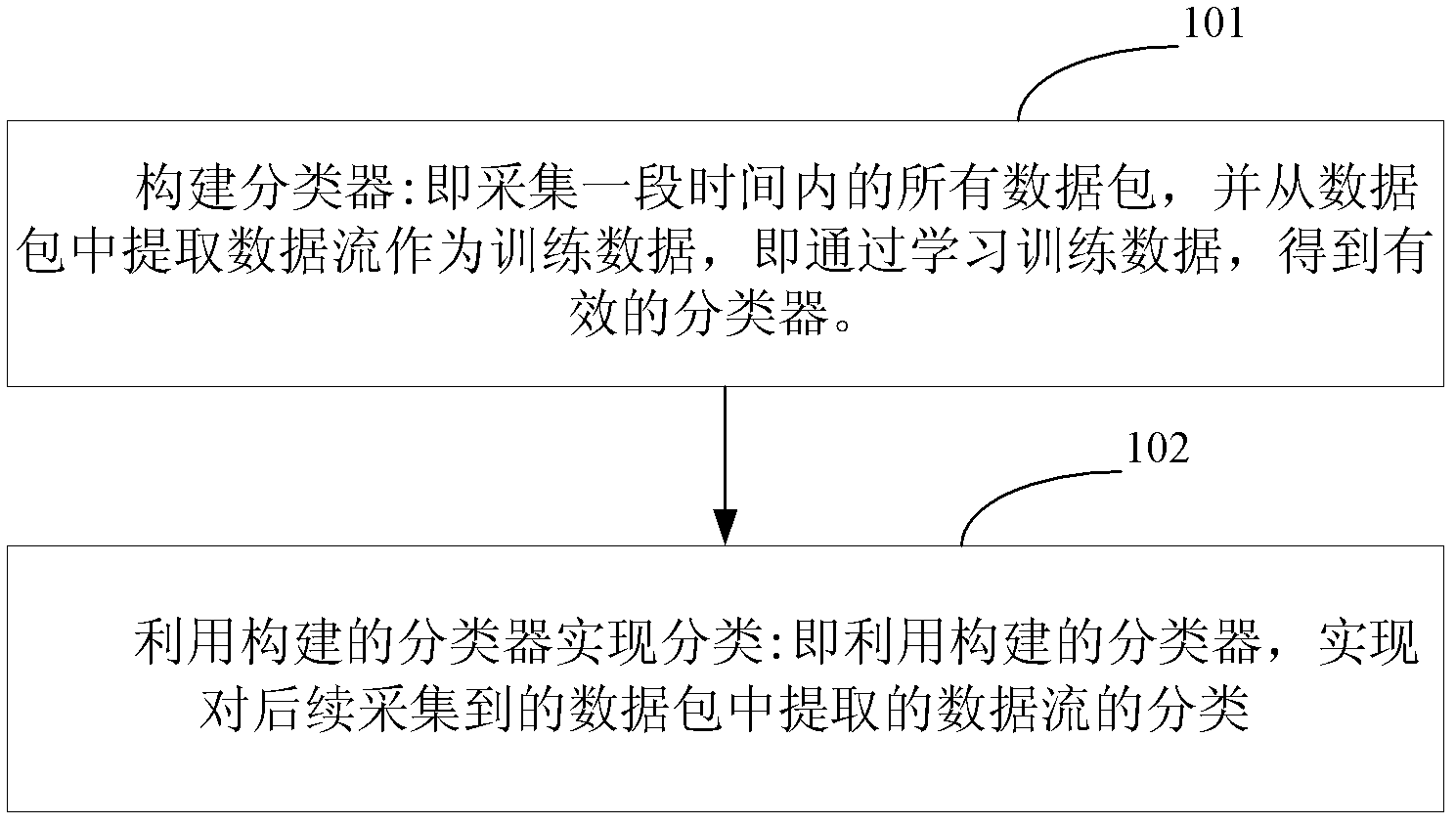
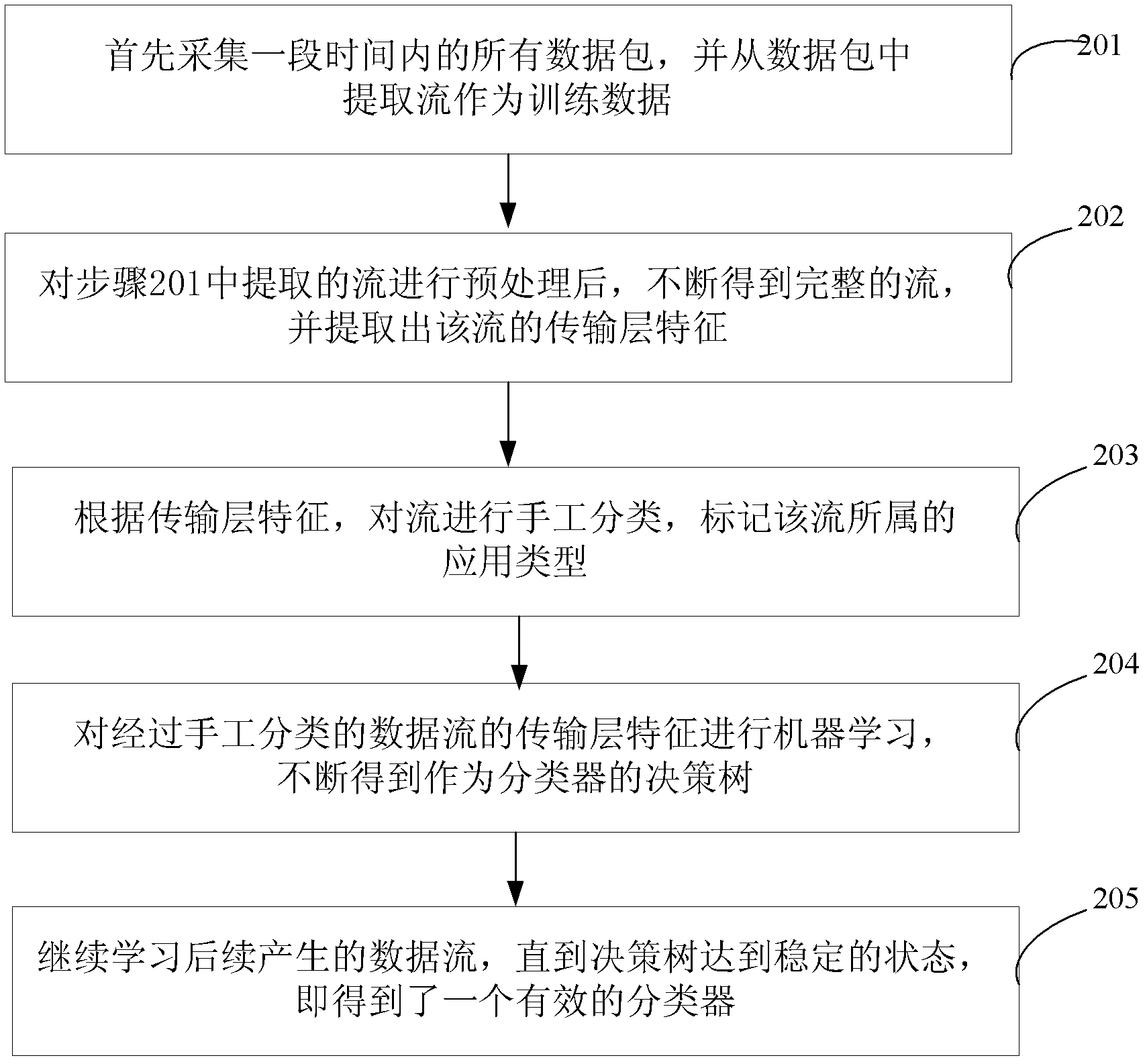
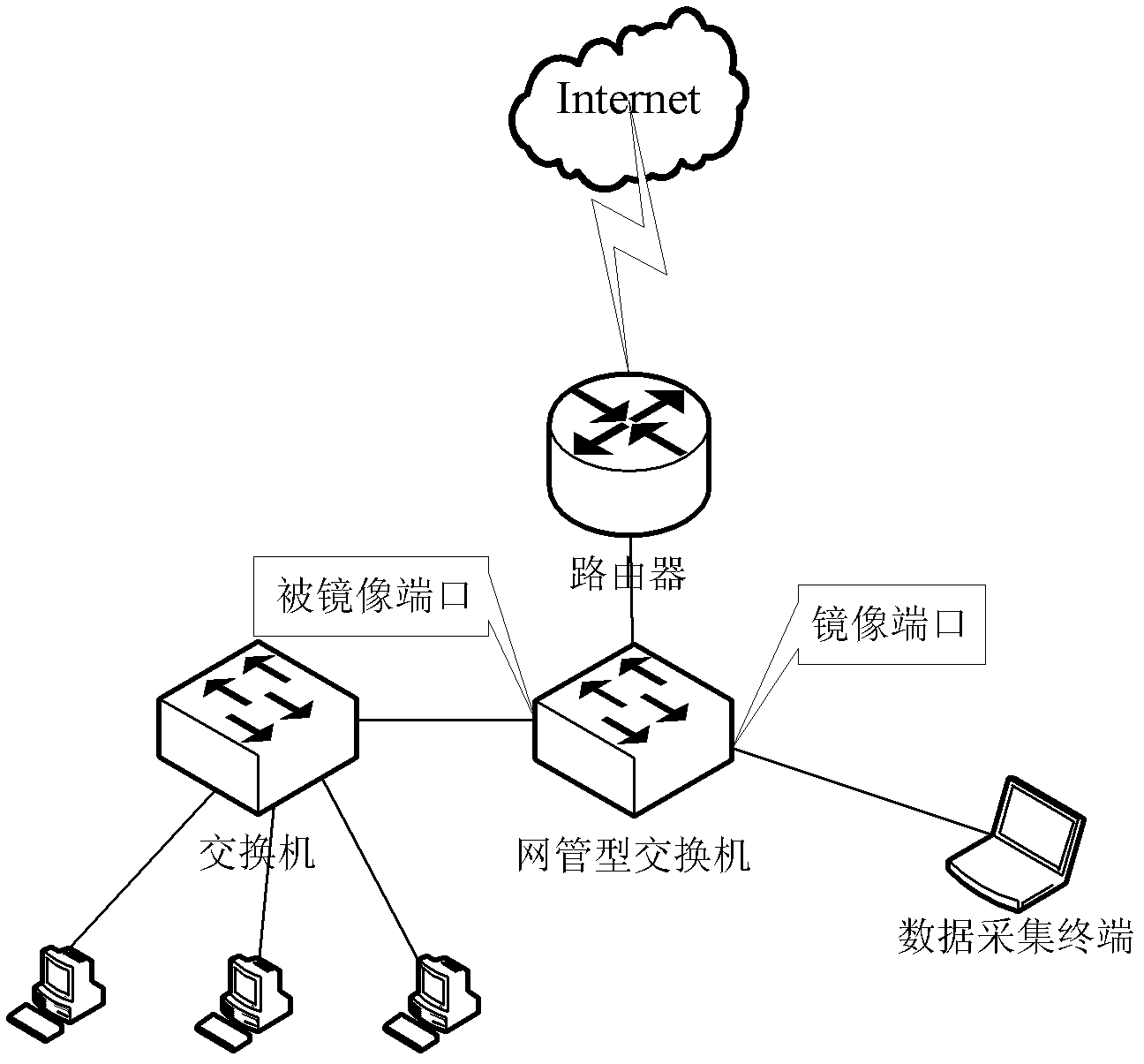
The invention relates to the technical field of Internet application, in particular to a transport-layer-characteristic-based traffic classification method for the Internet application. The method comprises the following steps of: acquiring a data packet which serves as training data, and constructing a classifier by utilizing transport layer characteristics of a data stream extracted from the data packet; and classifying the data stream extracted from a subsequently acquired data packet by utilizing the constructed classifier. The application type of the stream can be identified only by extracting the transport layer characteristics of the stream without knowing load contents such as a port number, a characteristic field and the like of the data packet. The privacy of a user is uninvolved, and a dynamic-port-number-based or encrypted stream can be identified by the technology. Moreover, the method is highly accurate and integral, novel application can be identified and the user can be prompted to check suspected virus attack streams.
Owner:四川智联科创科技有限公司
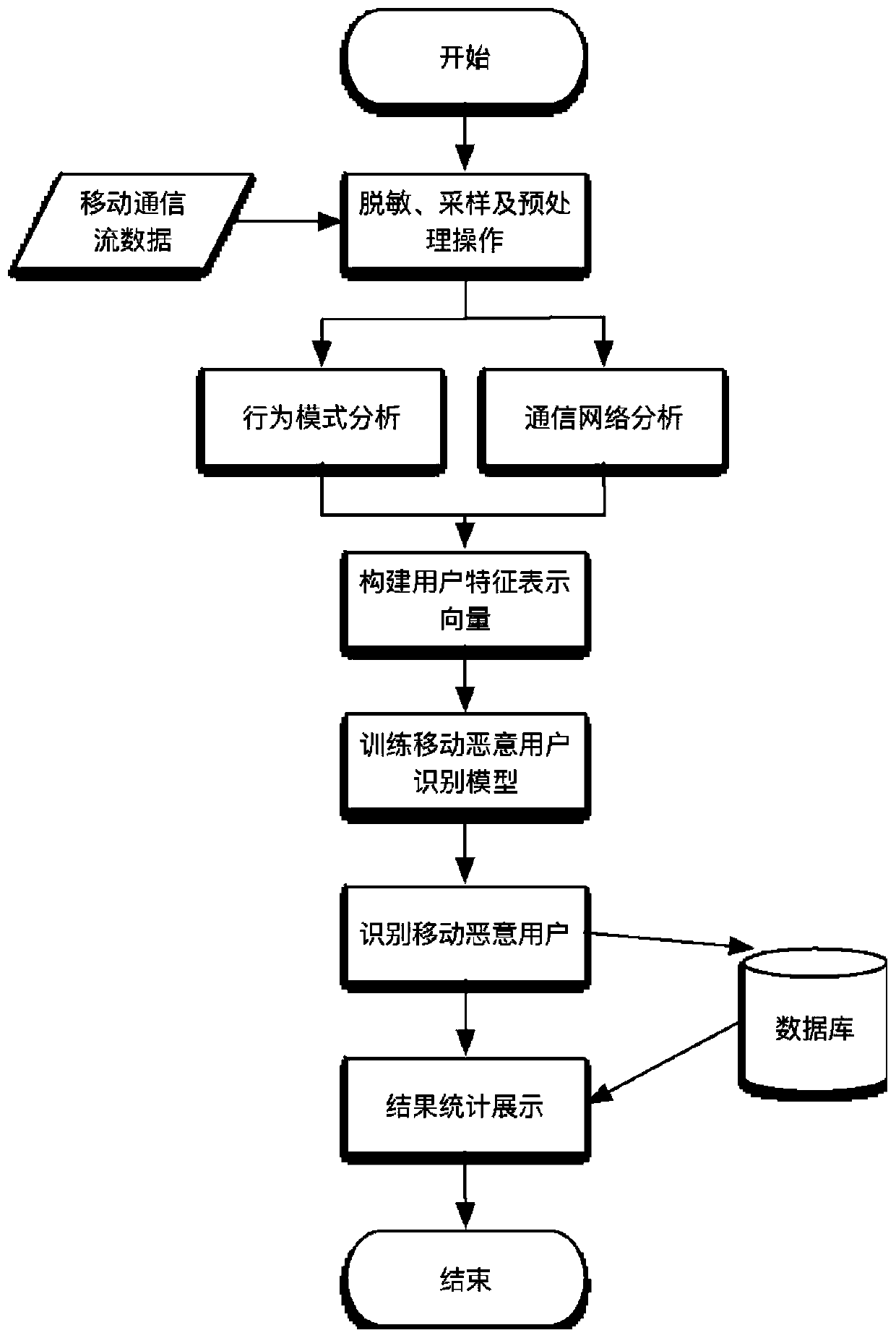
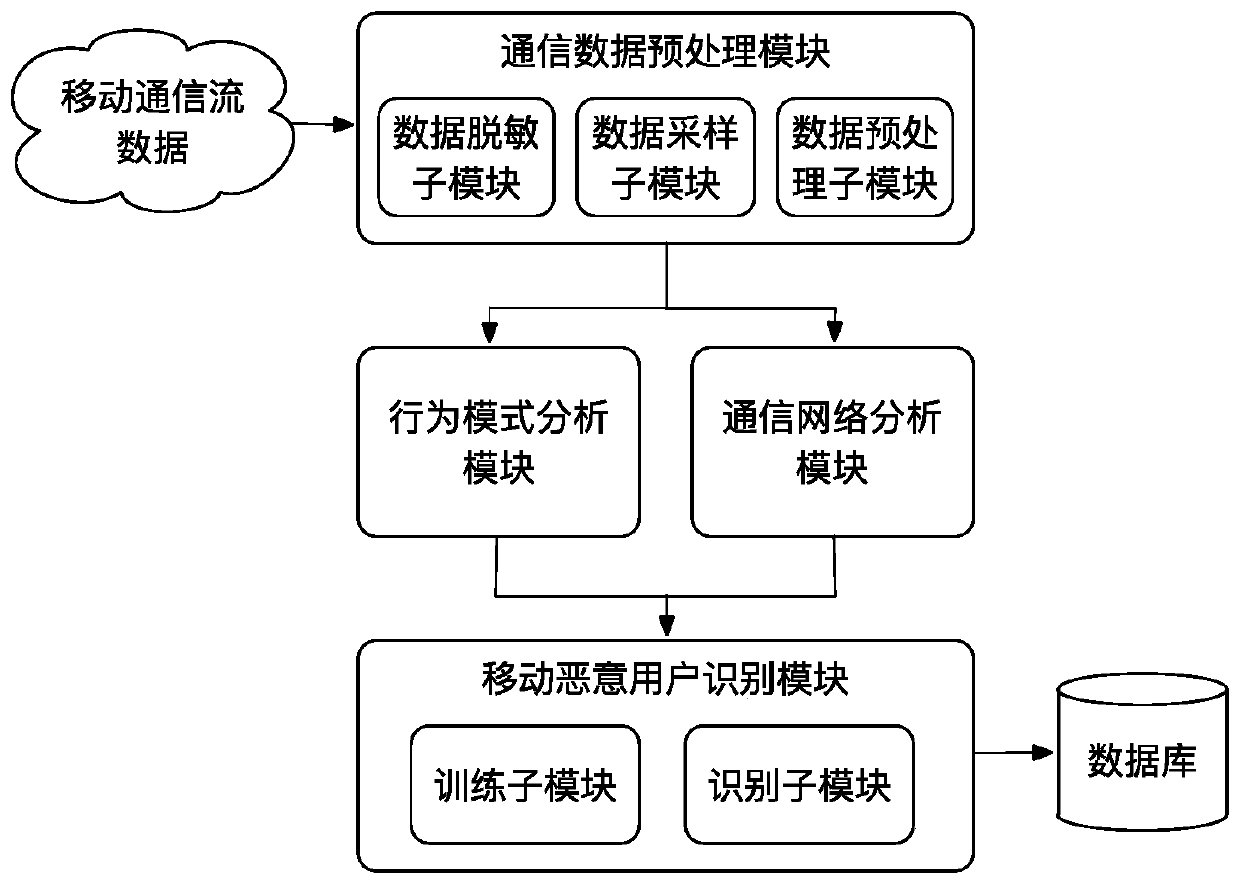
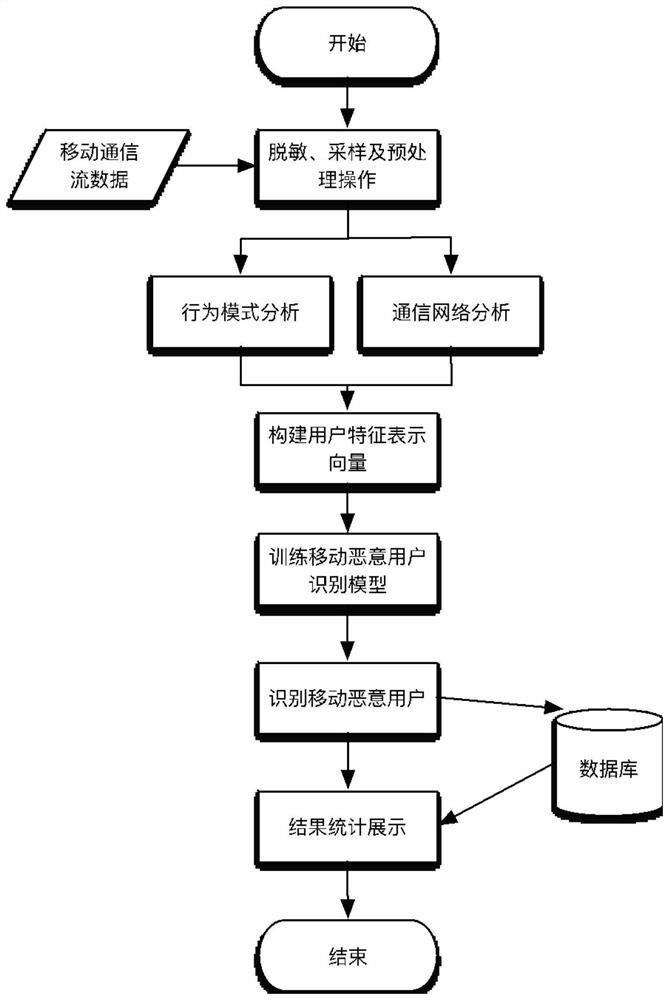
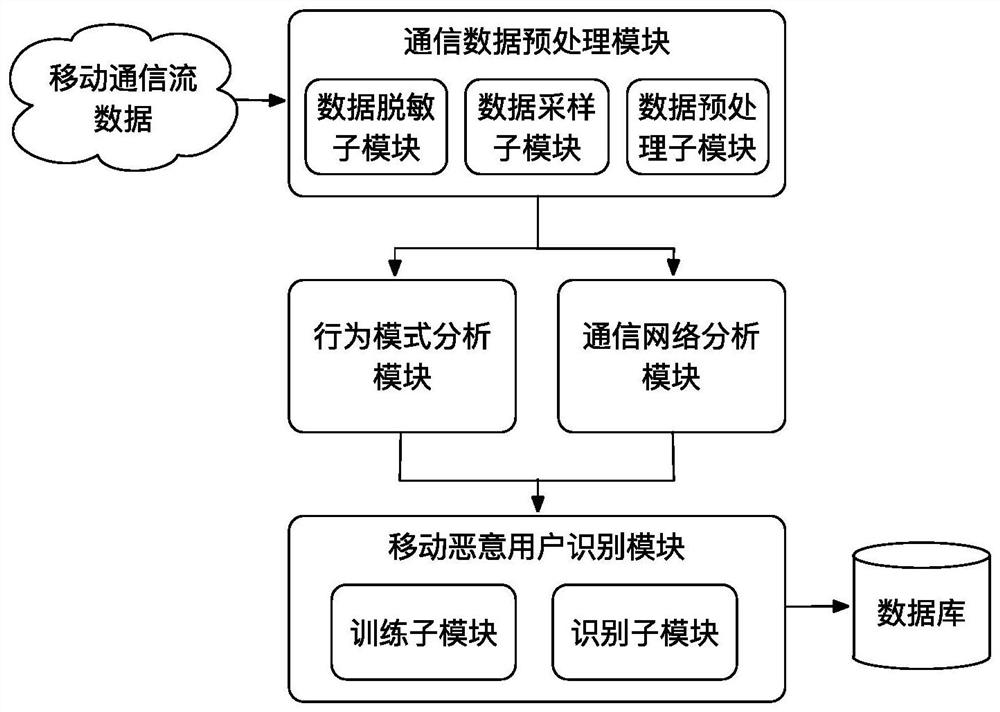
Mobile malicious user identification method and system based on communication behavior rule
The invention relates to a mobile malicious user identification method and system based on a communication behavior rule, and the method comprises the steps: collecting data in desensitized mobile communication flow data based on a non-uniform sampling method, and carrying out preprocessing; analyzing and extracting call behavior characteristics, short message behavior characteristics and time distribution characteristics of the user by utilizing a behavior mode in a mobile communication behavior analysis model based on the preprocessed mobile communication sampling data; based on the preprocessed mobile communication sampling data, analyzing and extracting social attribute characteristics of the user by utilizing a communication network in a mobile communication behavior analysis model; and constructing a mobile malicious user identification model based on the extracted user behavior mode characteristics and the extracted user social attribute characteristics. The behavior rule of theuser can be analyzed based on the desensitization data, whether the user is a mobile malicious user or not is recognized, timeliness is achieved, and the mobile malicious user can be recognized withhigh accuracy under the condition that personal privacy of the user is not involved.
Owner:INST OF INFORMATION ENG CAS
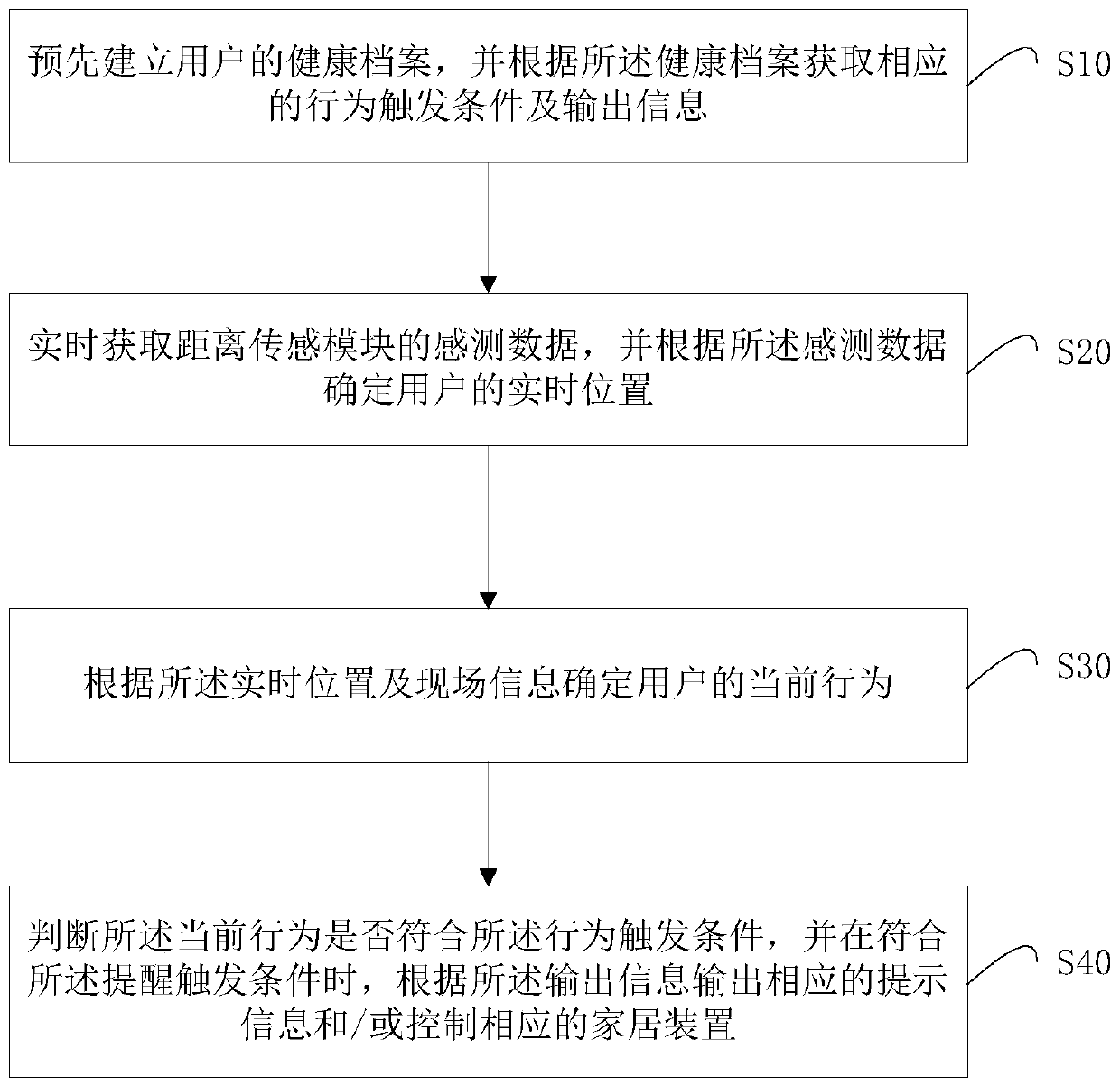
Smart home health and old-age care realization method and smartintelligent device
InactiveCN110264388AAccurate Care ServiceImprove experienceData processing applicationsMeasurement devicesSensing dataUser privacy
The invention relates to a smart home health and old-age care realization method and a smart device, and the method comprises the steps: pre-establishing a health file of a user, and obtaining a corresponding behavior trigger condition and output information according to the health file; acquiring sensing data of a distance sensing module in real time, and determining a real-time position of a user according to the sensing data; determining the current behavior of the user according to the real-time position and the field information; and judging whether the current behavior conforms to the behavior triggering condition or not, and outputting corresponding prompt information and / or controlling a corresponding home device according to the output information when the current behavior conforms to the behavior triggering condition. According to the technical scheme, the accurate care service is actively provided for the user, convenient, intelligent and comfortable user experience is brought to the user, and due to the fact that the distance sensing module does not involve user privacy, the distance sensing module is not limited in family application.
Owner:SHENZHEN HUI ANKANG TECH CO LTD
Time, geographic location, and network-based social networking system and method
InactiveCN104184779ARealize online paymentFacilitate tax auditWireless commuication servicesTransmissionTransaction serviceGeolocation
The invention relates to a time, geographic location, and network-based social networking system and method, thereby realizing functions of vehicle location, social activity organization, advertisement publishing, news information releasing, offline and online transaction services and information inquiring reservation. Especially, the system includes a novel mobile IC card reader and a method. According to the invention, a new concept based on location and time based service (LATBS) is put forward based on a location based service (LBS)-based concept; and a beneficial social life network is established by the system and method. Therefore, information transmitting becomes efficient; the traffic situation is improved; the positive social contact orientation is guided; the transaction becomes simple, convenient and rapid; and the life style of the human being is improved. And thus the great social benefits are generated.
Owner:牛帅
Transport-layer-characteristic-based traffic classification method and device
InactiveCN102271090BNo privacy involvedImprove accuracyData switching networksTransport layerData stream
Owner:四川智联科创科技有限公司
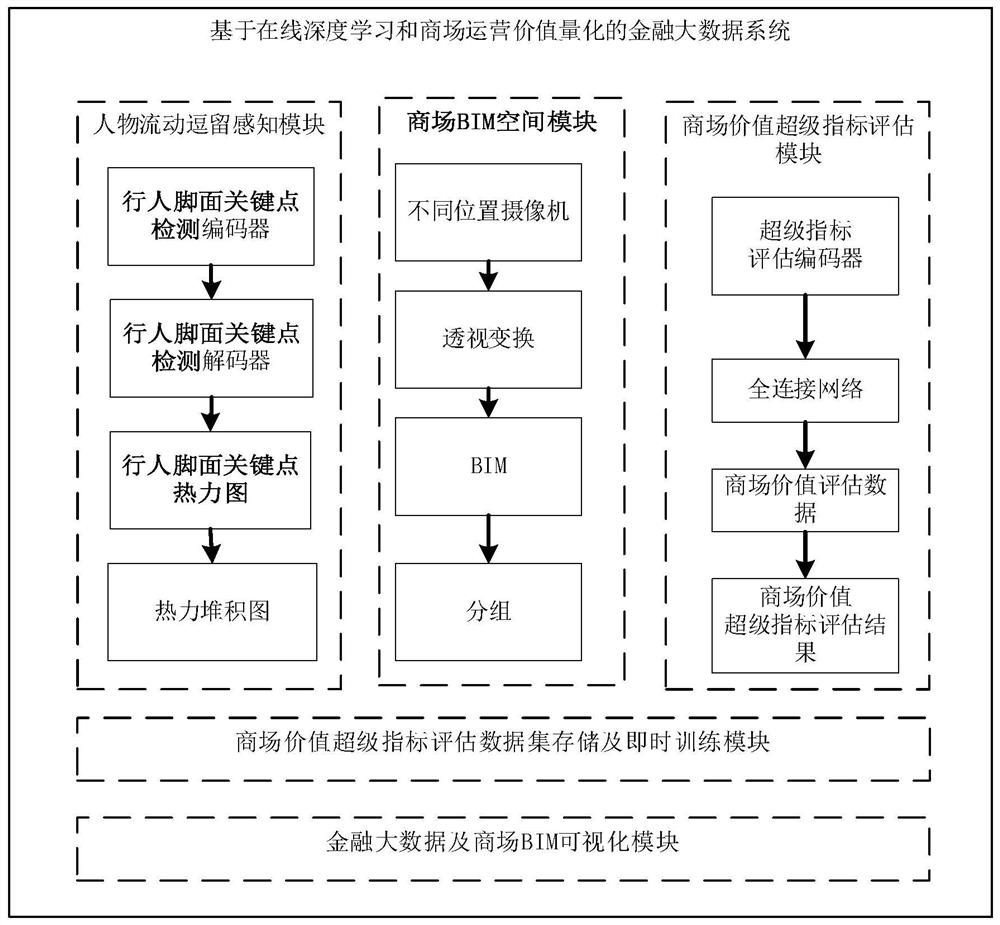
Financial big data system based on online deep learning and market operation value quantification
InactiveCN111783678AReflect fairnessAchieve desensitizationBiometric pattern recognitionNeural architecturesPersonalizationNerve network
The invention discloses a financial big data system based on online deep learning and market operation value quantification. The system includes a person flow stay perception module, a shopping mall BIM space module, a shopping mall value super index evaluation module, a shopping mall value super index evaluation data set storage and instant training module, and a financial big data and shopping mall BIM visualization module. A subjective operation value quantized value is fitted through passenger flow data and business volume personalized data, an optimized convolutional neural network is trained in real time for processing a large amount of data sampled during operation, and real-time quantification of the operation value of a shopping mall is realized. According to the invention, fairness from objective data to subjective rating is ensured, data desensitization is realized, network training is convenient, and real-time monitoring and evaluation of managers are facilitated.
Owner:郑州智利信信息技术有限公司
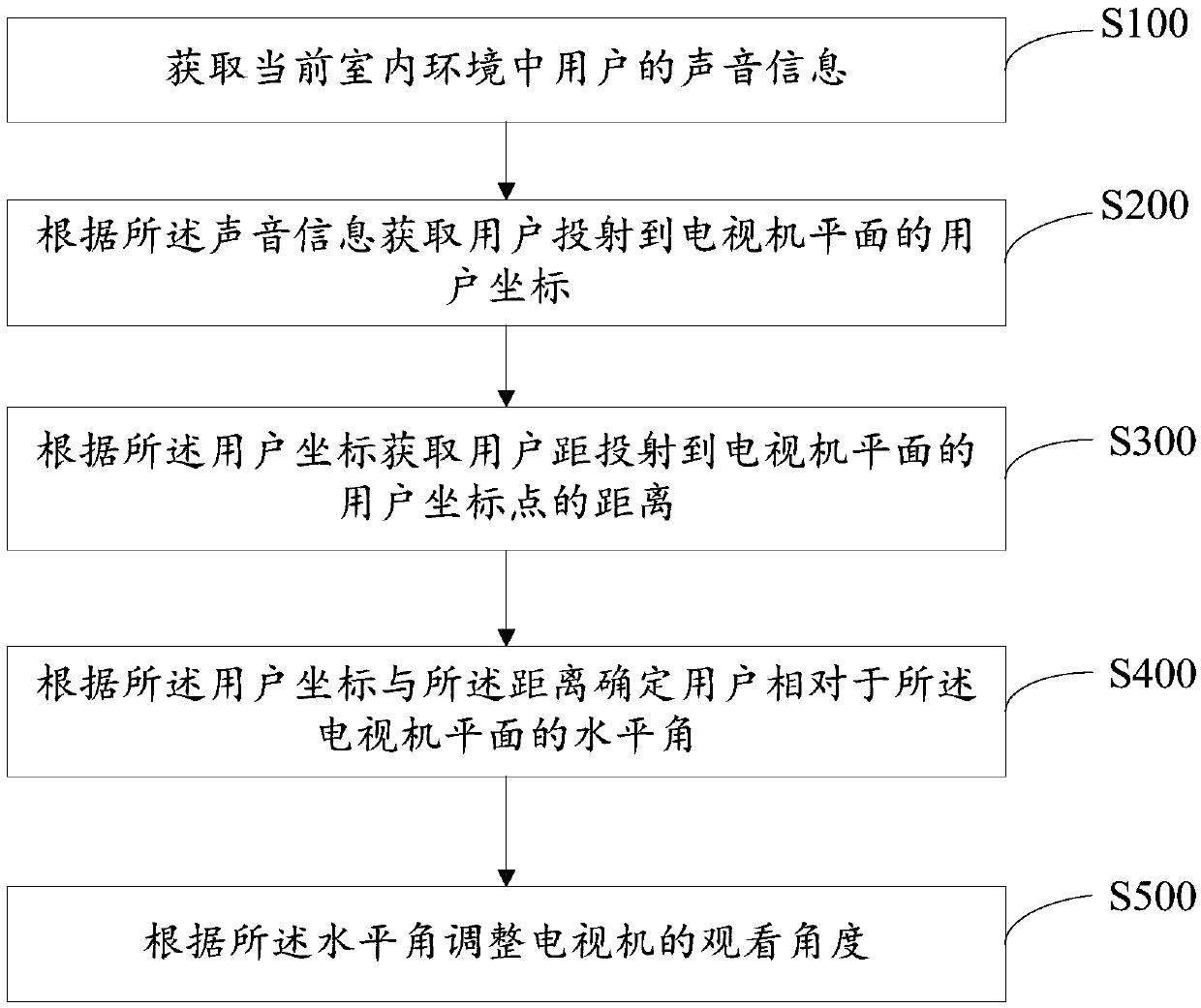
Method for adjusting angle of television set, television set, and computer-readable storage medium
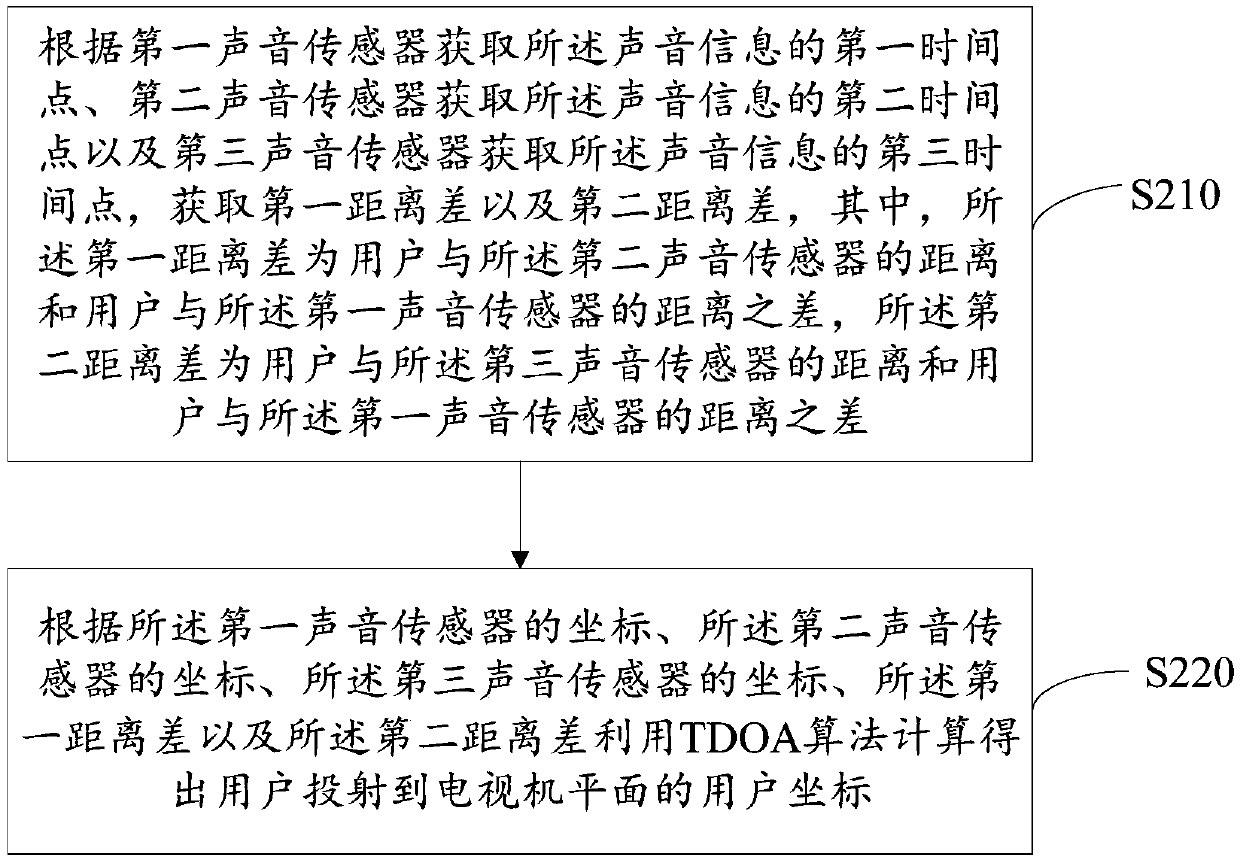
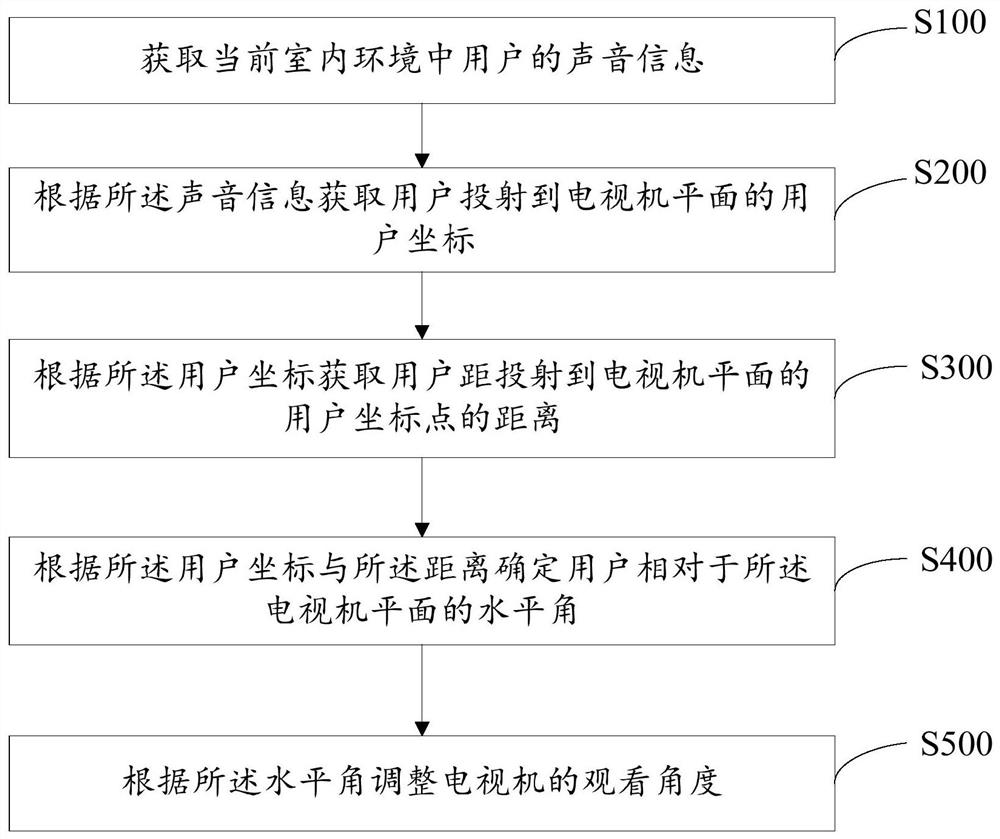
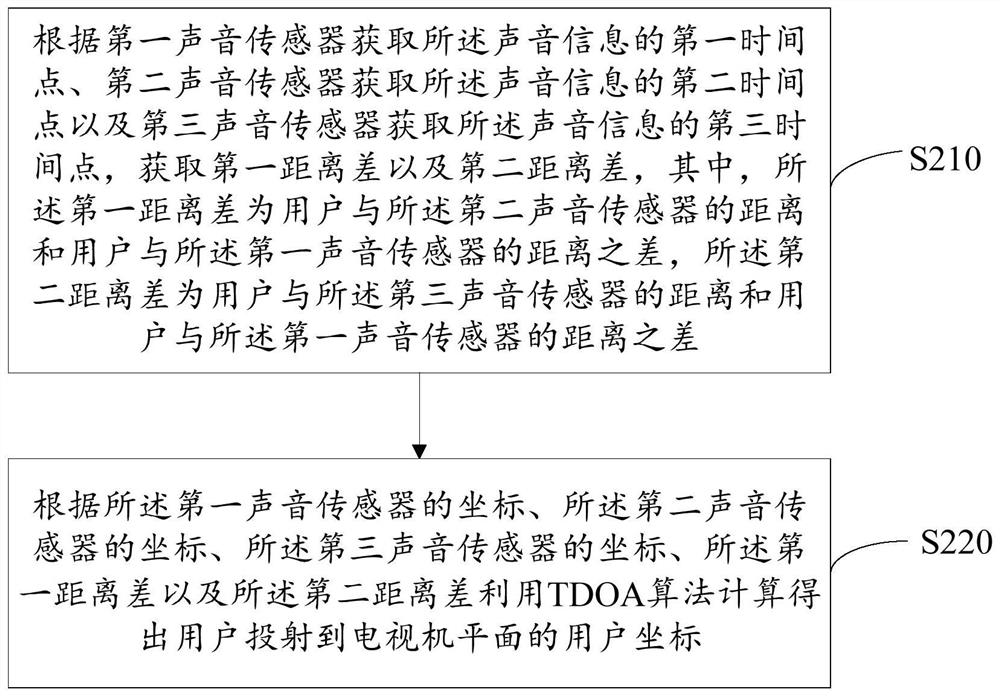
ActiveCN109557951AEasy to watchImprove viewing effectControl using feedbackComputer scienceTelevision set
The invention discloses a method for adjusting the angle of a television set. The method comprises: acquiring a user coordinate projected onto a plane of a television set according to sound information of the user in a current indoor environment; acquiring a distance between the user and a user coordinate point of projection onto the plane of the television set based on the user coordinate; according to the user coordinate and the distance, determining a horizontal angle of the user relative to the plane of the television set; and adjusting the viewing angle of the television set based on thehorizontal angle. In addition, the invention also provides a television set and a computer-readable storage medium. According to the invention, the coordinate, projection on the plane of the television set, of the user is located based on the sound information of the user and the screen of the television set is adjusted automatically to face the angle of the user, so that the user can carry out watching comfortably and thus the best watching effect of the user is obtained. Therefore, the watching experience of the user is improved.
Owner:SHENZHEN TCL DIGITAL TECH CO LTD
Intelligent payment method based on different merchants
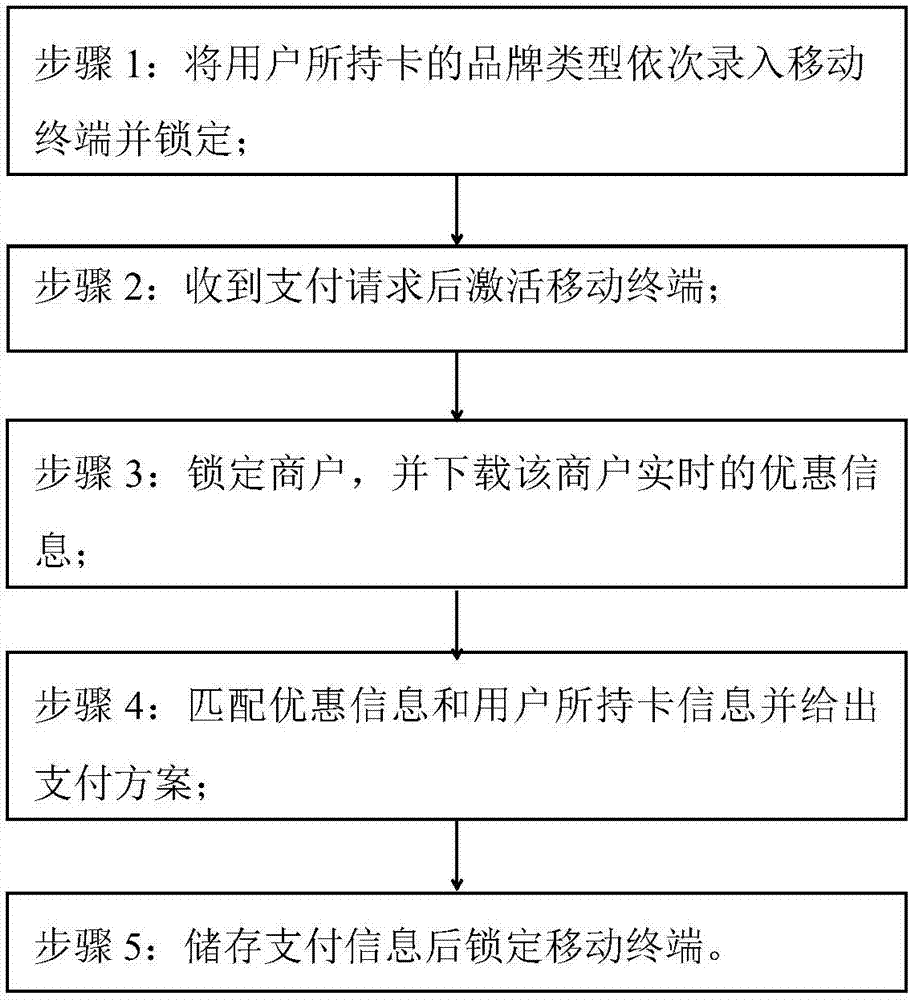
InactiveCN107424005ANo privacy involvedImprove confidentialityDiscounts/incentivesPayment architecturePaymentComputer terminal
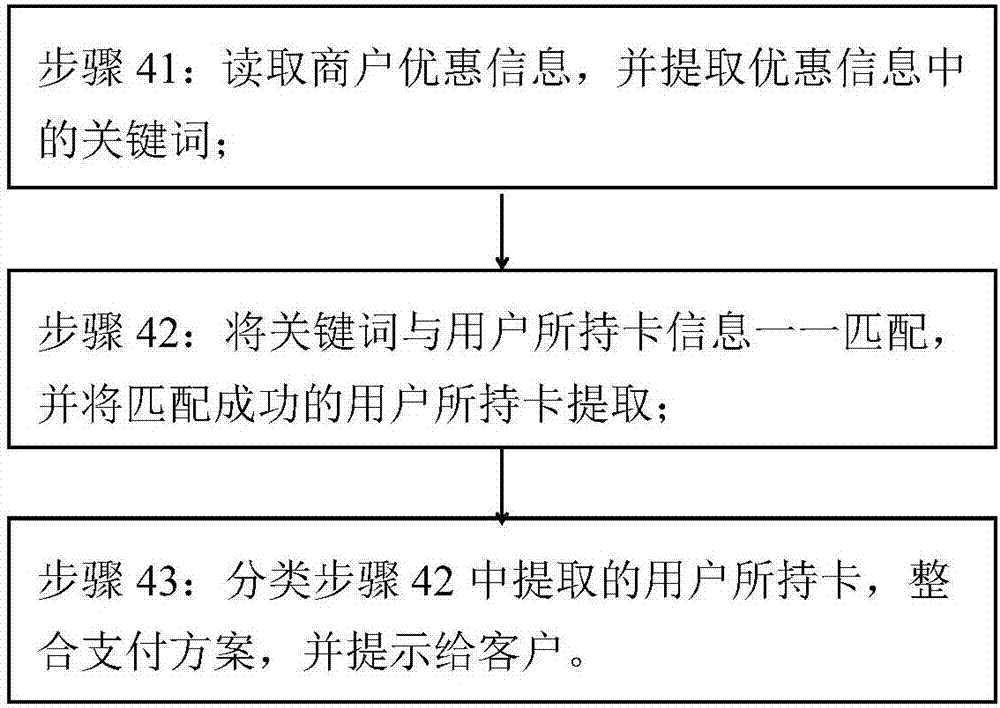
The invention discloses an intelligent payment method based on different merchants. The method comprises the steps of (1) orderly inputting brand types of cards held by a user into a mobile terminal and carrying out locking, (2) activating the mobile terminal after receiving a payment request, (3) locking a merchant and downloading real-time discount information of the merchant, (4) matching the discount information and information of the cards held by the user and giving a payment scheme, and (5) storing payment information and locking the mobile terminal. According to different merchants, combined with the cards held by the user, the optimal payment is carried out, thus the user can enjoy a most preferential consumption mode, the management and monitoring of the cards held by the user are facilitated, and the convenience of user consumption is greatly improved.
Owner:佛山杰致信息科技有限公司
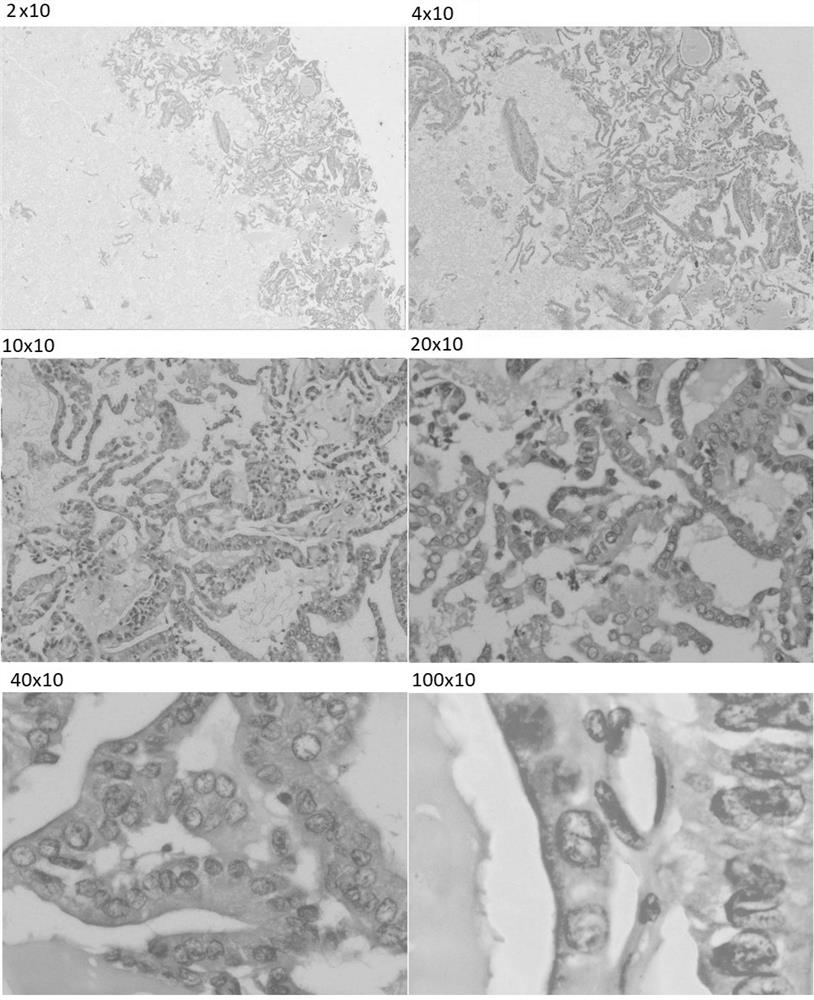
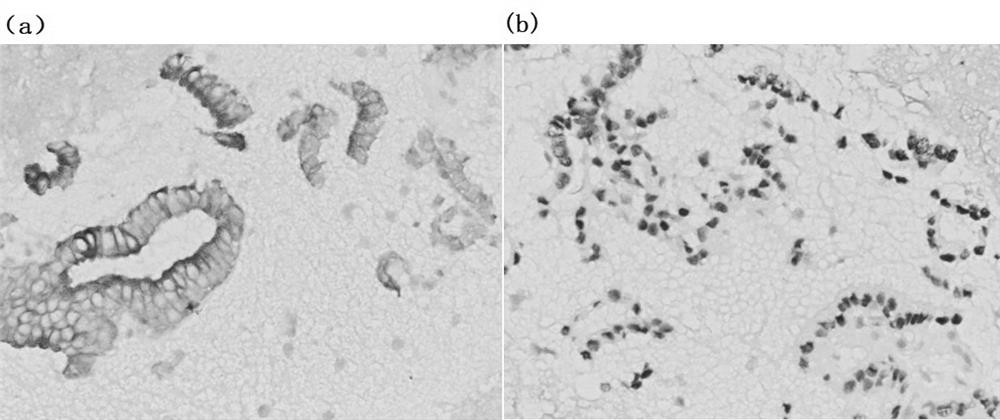
Preparation method for thyroid and mammary fine needle aspiration cell tissue blocks
ActiveCN109975090ASimple structureNo privacy involvedPreparing sample for investigationHydrothoraxThyroid
The invention provides a preparation method for thyroid and mammary fine needle aspiration cell tissue blocks. The method includes the following steps: a, performing centrifugation on hydrothorax or ascites in advance, and obtaining hydrothorax or ascites supernatant; b, taking the hydrothorax or ascites supernatant to inject into a centrifuge tube; c, injecting a fine needle punctured thyroid andmammary specimen into the centrifuge tube, and then immediately taking 95% of ethanol to inject into the centrifuge tube; and d, performing centrifugation on the centrifuge tube and abandoning the supernatant so that cell sediment can be obtained, adding 4% of neutral buffer formaldehyde fixative, and adopting a paraffin tissue specimen processing program to perform conventional embedding after the cell sediment in the centrifuge tube is solidified. The preparation method can guarantee that tissue fragments and free-floating single cells are not lost; and cytoplasm is good in form and structure preservation, can be sliced continuously or for many times, and is suitable for a plurality of dyeing, and therefore, diagnosis efficacy can be enhanced.
Owner:马晓丽
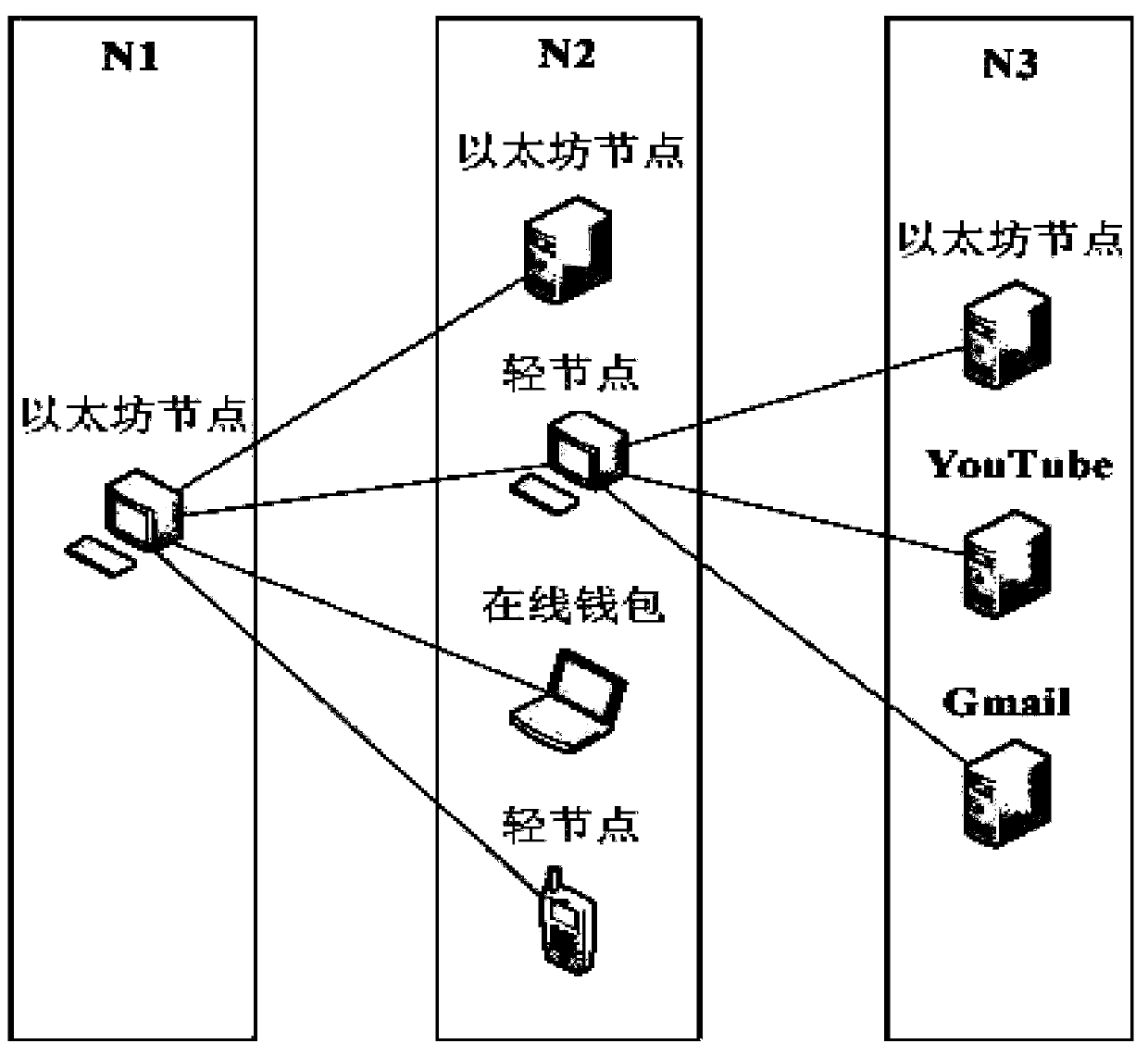
Ethereum network behavior analysis method, corresponding storage medium and electronic device
InactiveCN111082995ANo privacy involvedImprove accuracyMachine learningData switching networksData packData set
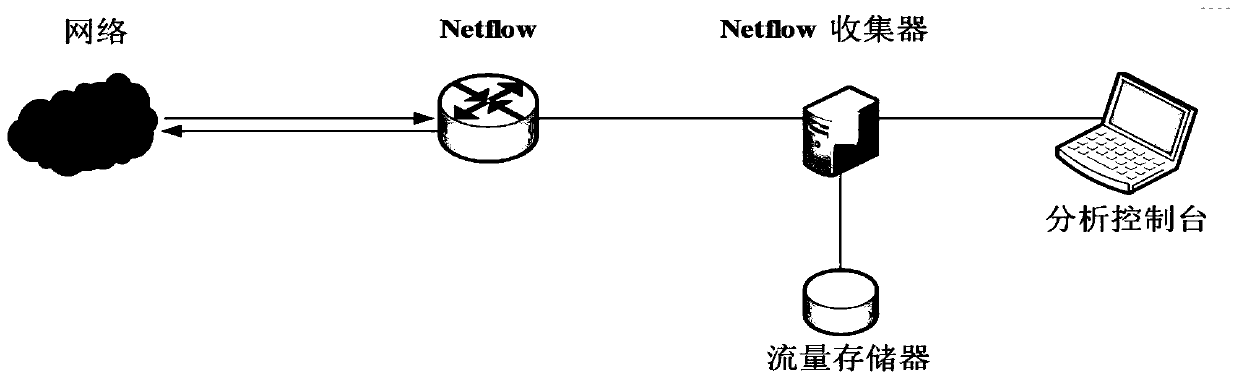
The invention discloses an Ethereum network behavior analysis method, a corresponding storage medium and an electronic device. The method comprises the following steps: detecting Ethereum nodes in network traffic data by using a passive association method to obtain an Ethereum node set, and obtaining an Ethereum iterative node set according to an iterative association relation among the nodes in the Ethereum node set; converging the Ethereum iterative node set through a machine learning classifier to obtain an Ethereum convergence node set; monitoring the Ethereum node set and the Ethereum convergence node set to obtain a communication relationship data set, and analyzing the communication relation data set to obtain an Ethereum network attribute analysis result. According to the invention, the real backbone network NetFlow flow is used to detect the Ethereum nodes, the NetFlow data is used to summarize and count the data packet information, the important information reflecting the flow characteristics is retained, and the privacy of the user is not involved.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
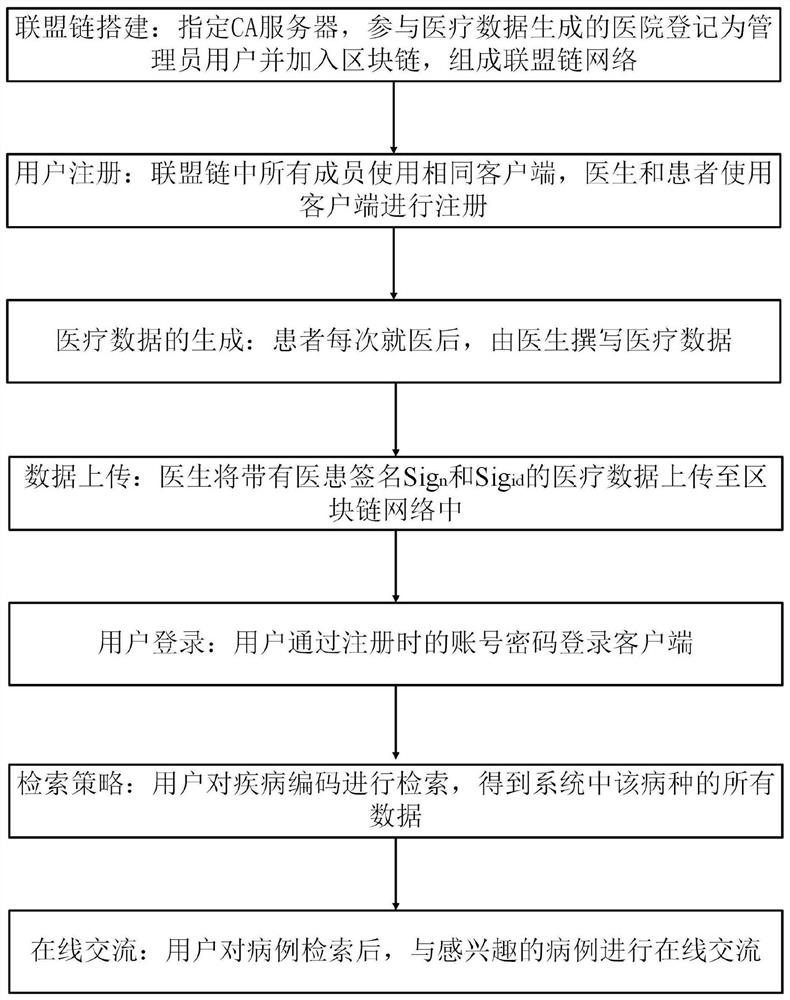
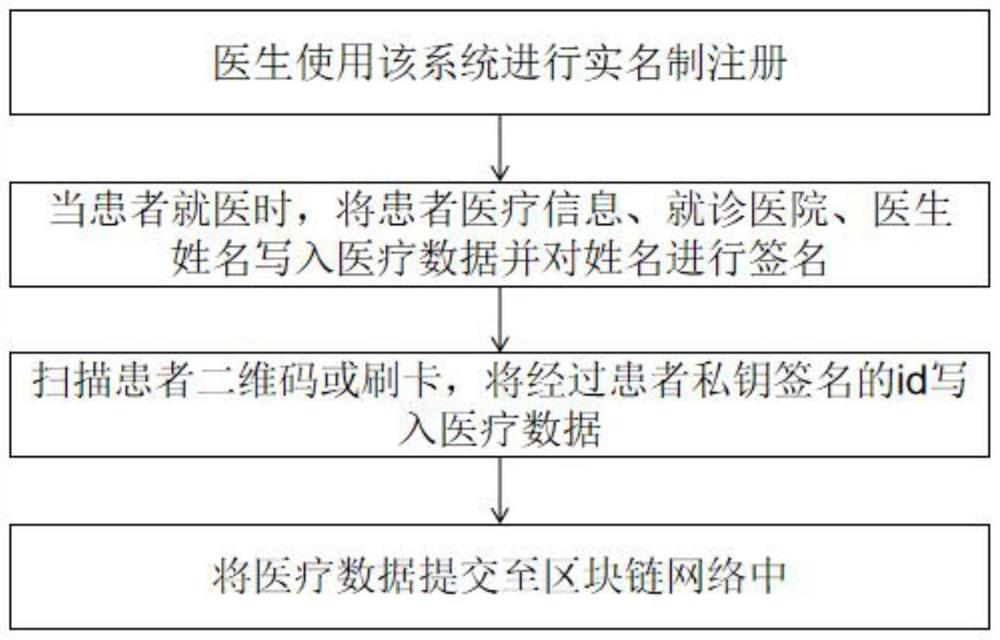
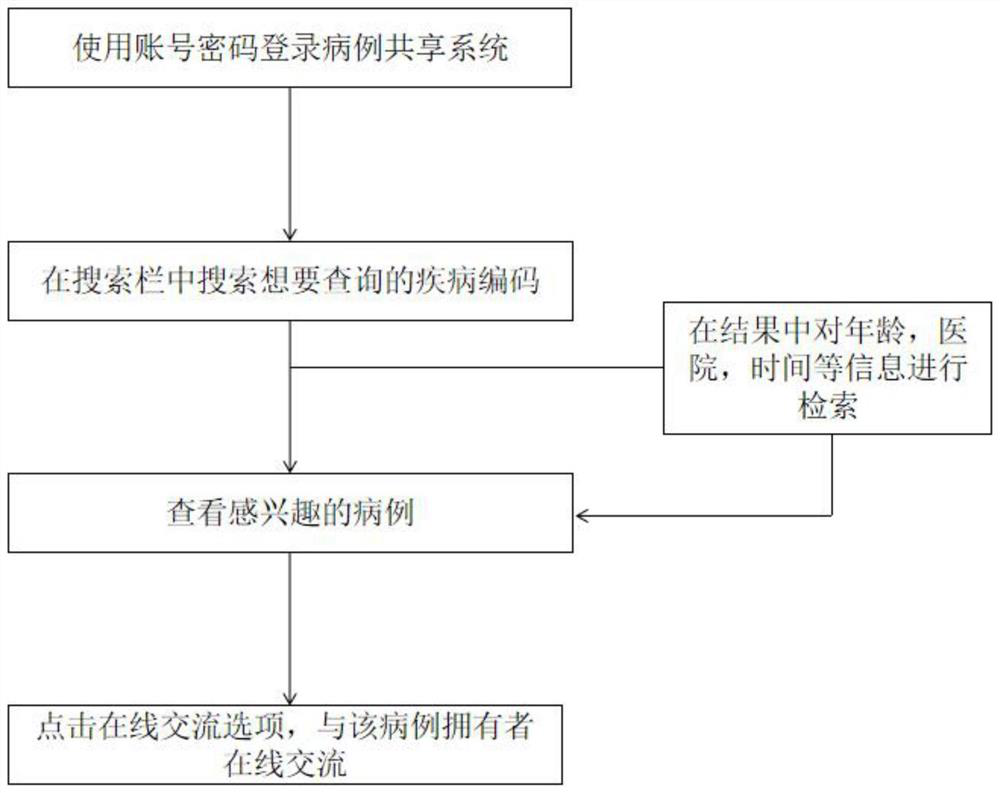
Case sharing method and system based on block chain and private key storage medium
PendingCN112733164ANo privacy involvedKey distribution for secure communicationDigital data protectionEngineeringChain network
The invention discloses a case sharing method based on a block chain, and the method comprises the steps: S1, building an alliance chain: registering hospitals participating in the generation of medical data as administrator users, adding the administrator users to the block chain, and forming an alliance chain network; S2, performing user registration: all members in the alliance chain use the same client; S3, generating medical data: writing the medical data by a doctor after the patient seeks a doctor every time; S4, performing data uploading: the doctor uploads the medical data with the doctor-patient signatures Sigdoc and Sigid to a block chain network; S5, logging in by the user; S6, making a retrieval strategy: retrieving the disease code by the user to obtain all data of the disease type in the system; S7, performing online communication: the user performs online communication with interested cases after retrieving the cases. According to the invention, the data meeting the conditions is uploaded by running the smart contract, is spread to each node to form a block, and is spread to the whole network, so that a patient can anonymously obtain a real, reliable and already-generated treatment scheme, and communicates with other patients or doctors.
Owner:CENT SOUTH UNIV
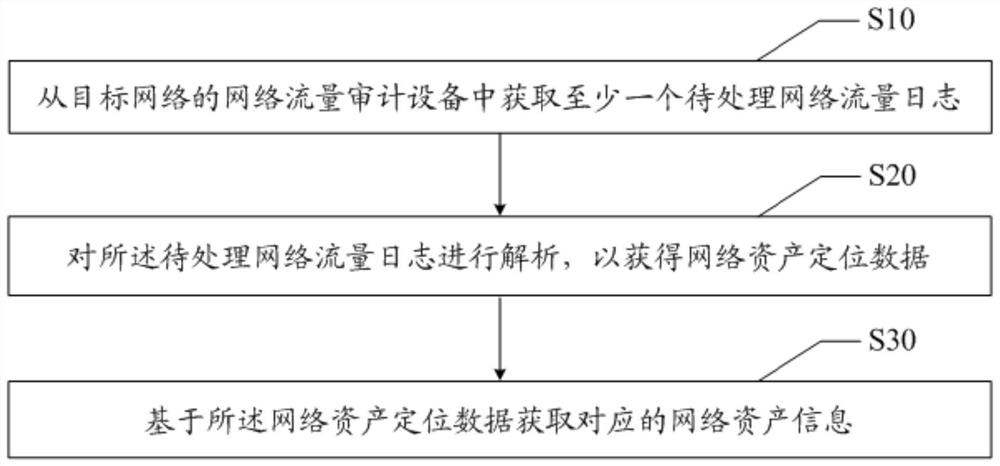
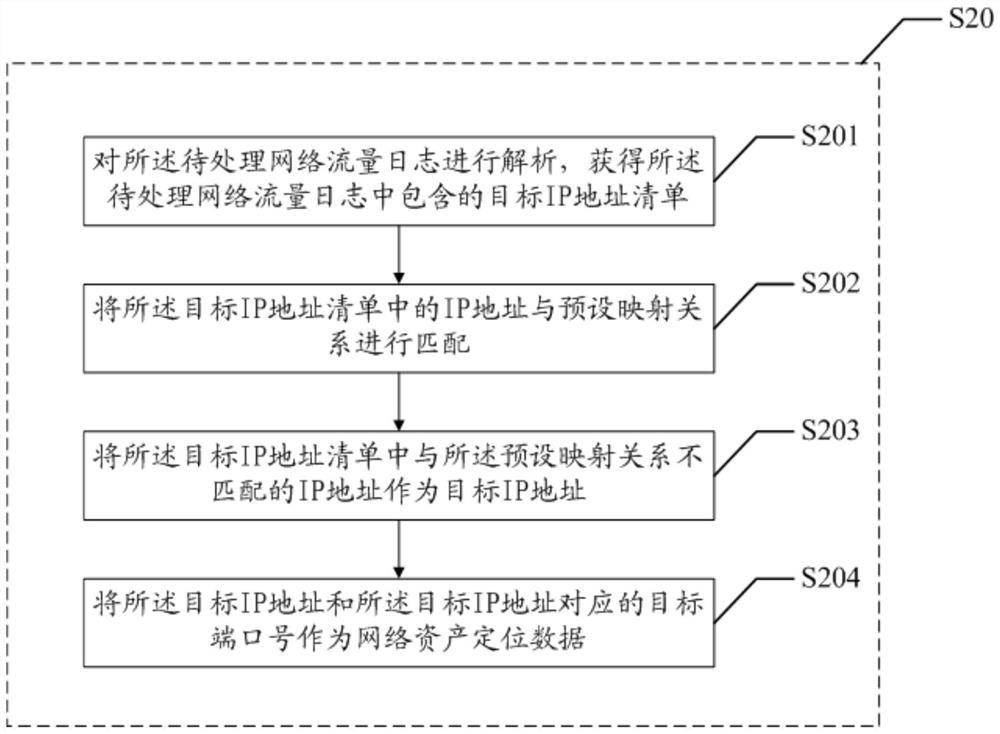
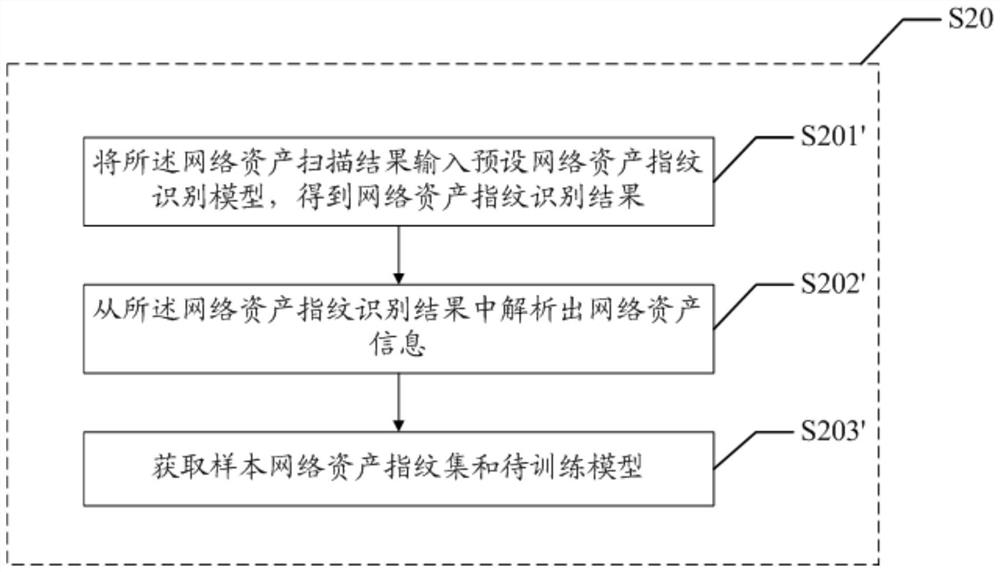
Network asset information acquisition method and device, and readable storage medium
ActiveCN112688810AEnsure comprehensivenessExpand the detection rangeData switching networksHigh level techniquesComputer networkInternet traffic
The invention discloses a network asset information obtaining method and device and a readable storage medium. The method comprises: obtaining at least one to-be-processed network flow log from a network flow auditing device of a target network; analyzing the to-be-processed network flow log to obtain network asset positioning data; and obtaining corresponding network asset information based on the network asset positioning data. According to the invention, the detection range of network asset detection is expanded, and the information security of network asset detection is improved.
Owner:苏州三六零智能安全科技有限公司
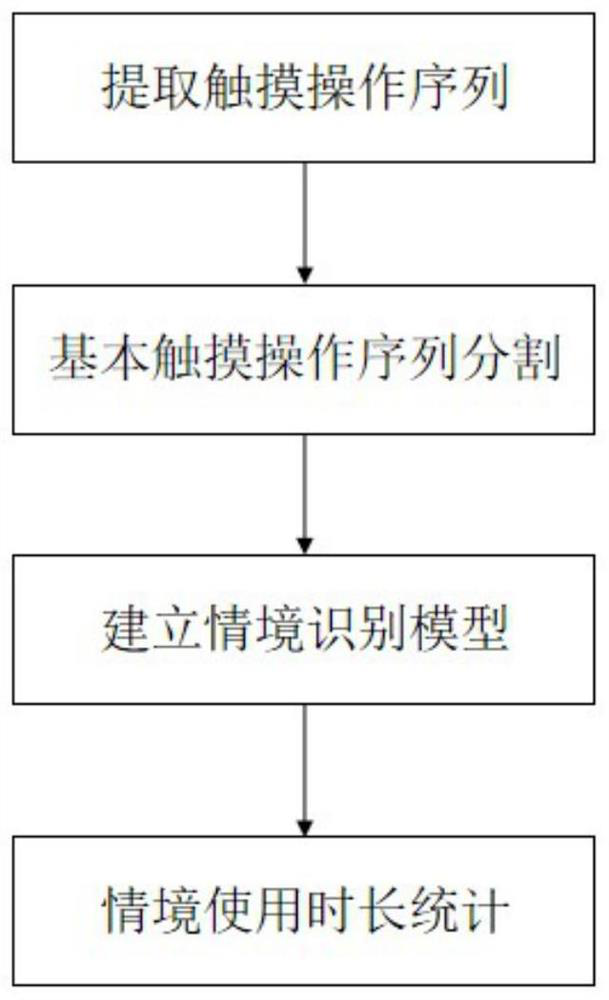
Smart phone use situation recognition method based on touch behavior sequence
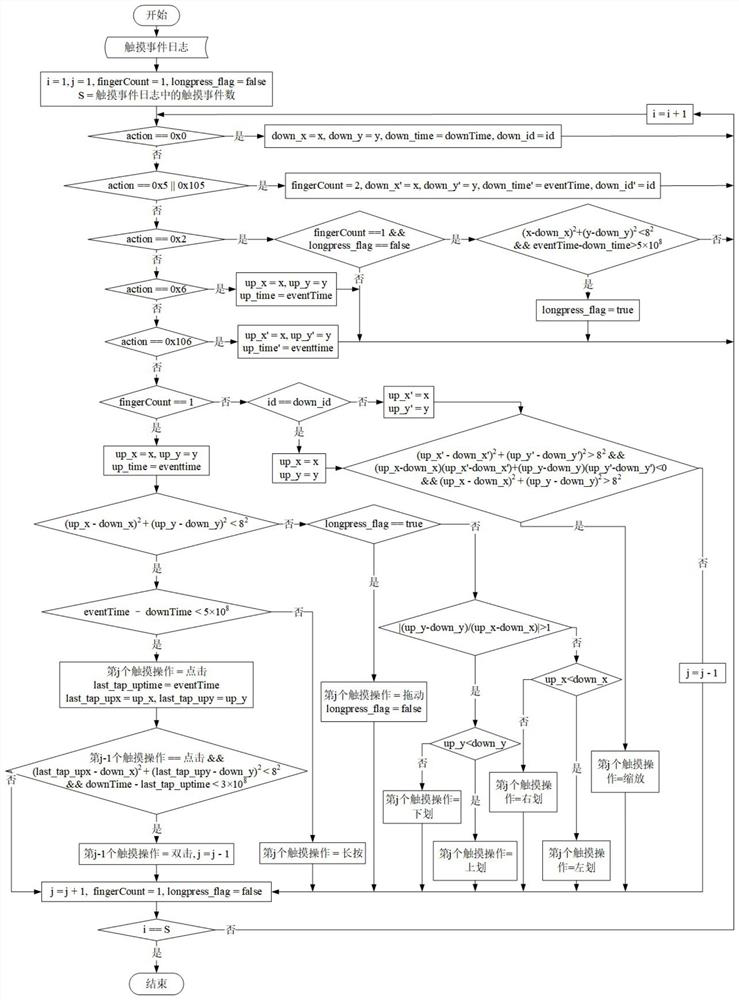
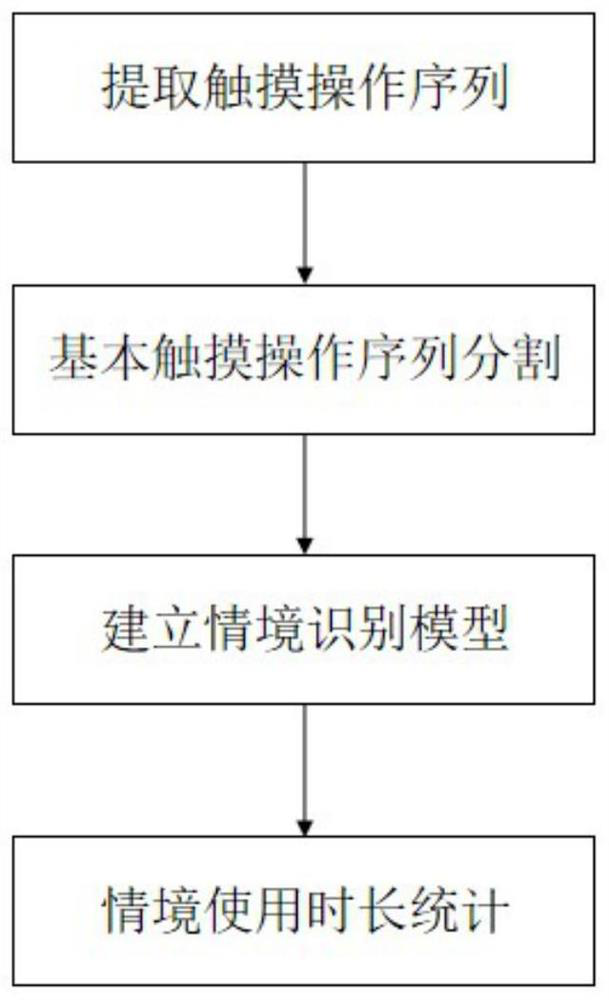
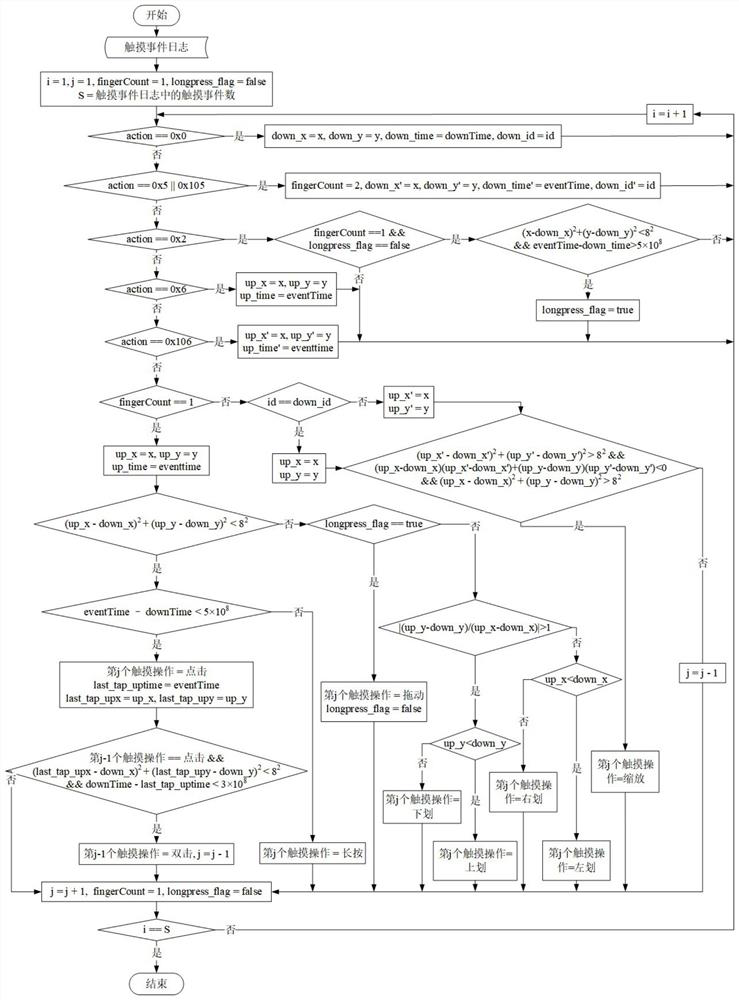
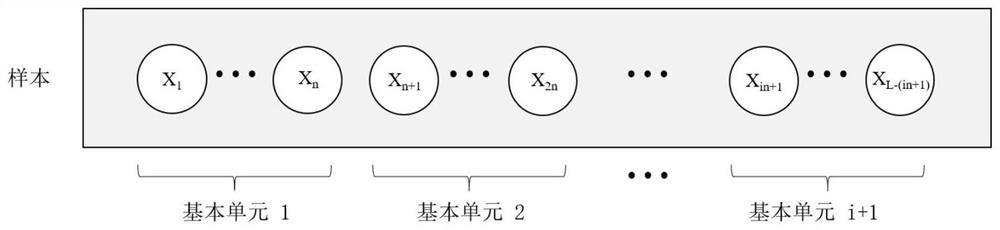
ActiveCN112073582AEasy to use habitsNo privacy involvedDevices with sensorCharacter and pattern recognitionStart timeEngineering
A smartphone use situation recognition method based on a touch behavior sequence defines nine touch operations. Nine touch operation attributes (touch starting time, touch ending time and the like) are extracted to form one touch operation by analyzing a log of a smartphone operation system, a touch operation sequence is obtained, and 32 continuous operations serve as a basic touch interaction sequence; and modeling is carried out by using a long-short-term memory network and an attention mechanism, so that judgment and statistics of the situation duration of using the mobile phone by the userare realized. According to the invention, the basic touch interaction sequence is input into the bidirectional long-short-term memory network model of the superimposed attention mechanism to carry out situation identification, so that the judgment of the situation of using the mobile phone by the user, such as shopping, social contact, browsing, learning, short videos, games and the like, is realized, and various situation subdivisions in the application of using the intelligent mobile phone by the user can be realized; and the use duration of each situation in a certain period of time is counted, so that a direct basis is provided for the user to know the use duration of each situation of a smart phone.
Owner:OCEAN UNIV OF CHINA
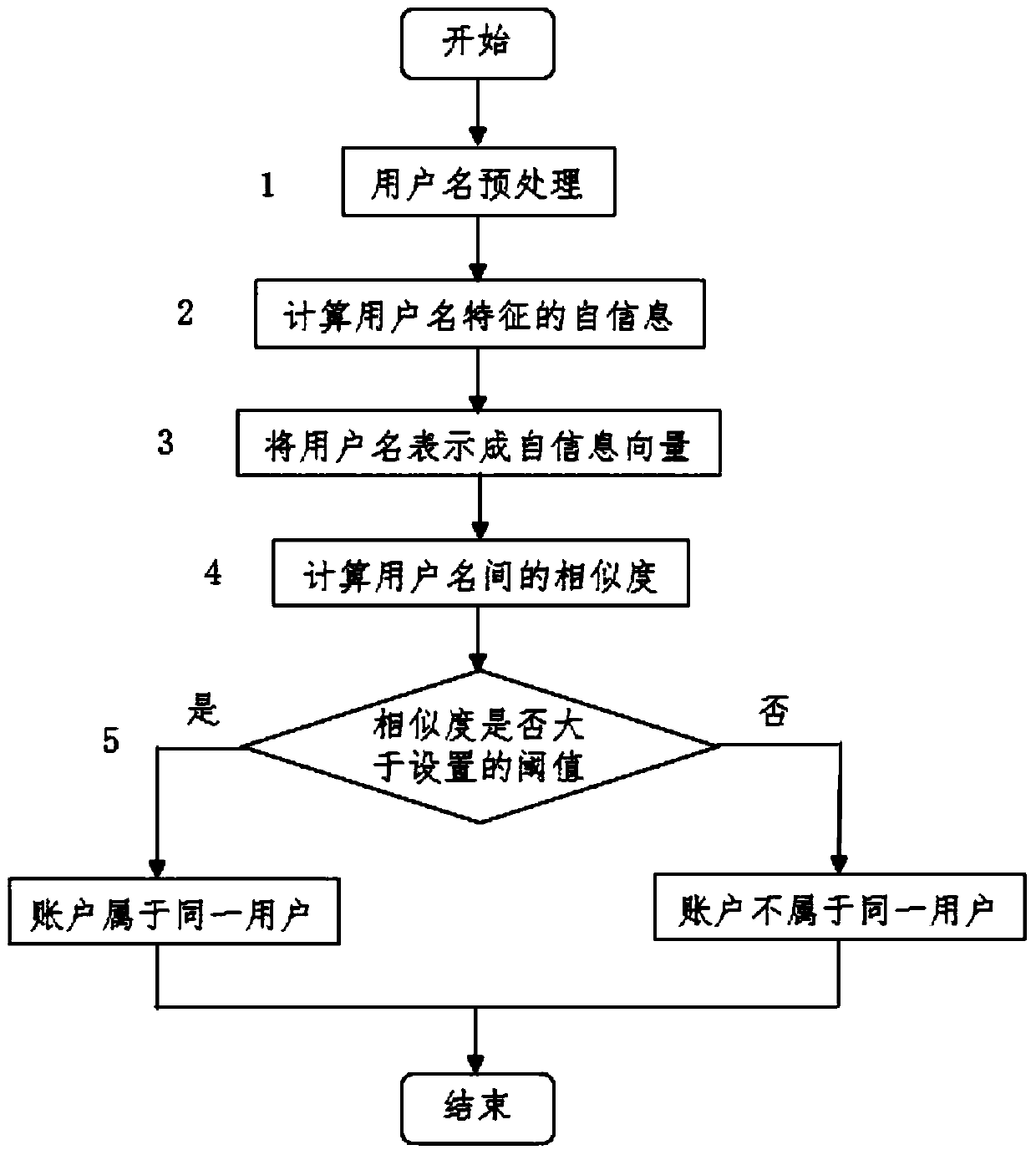
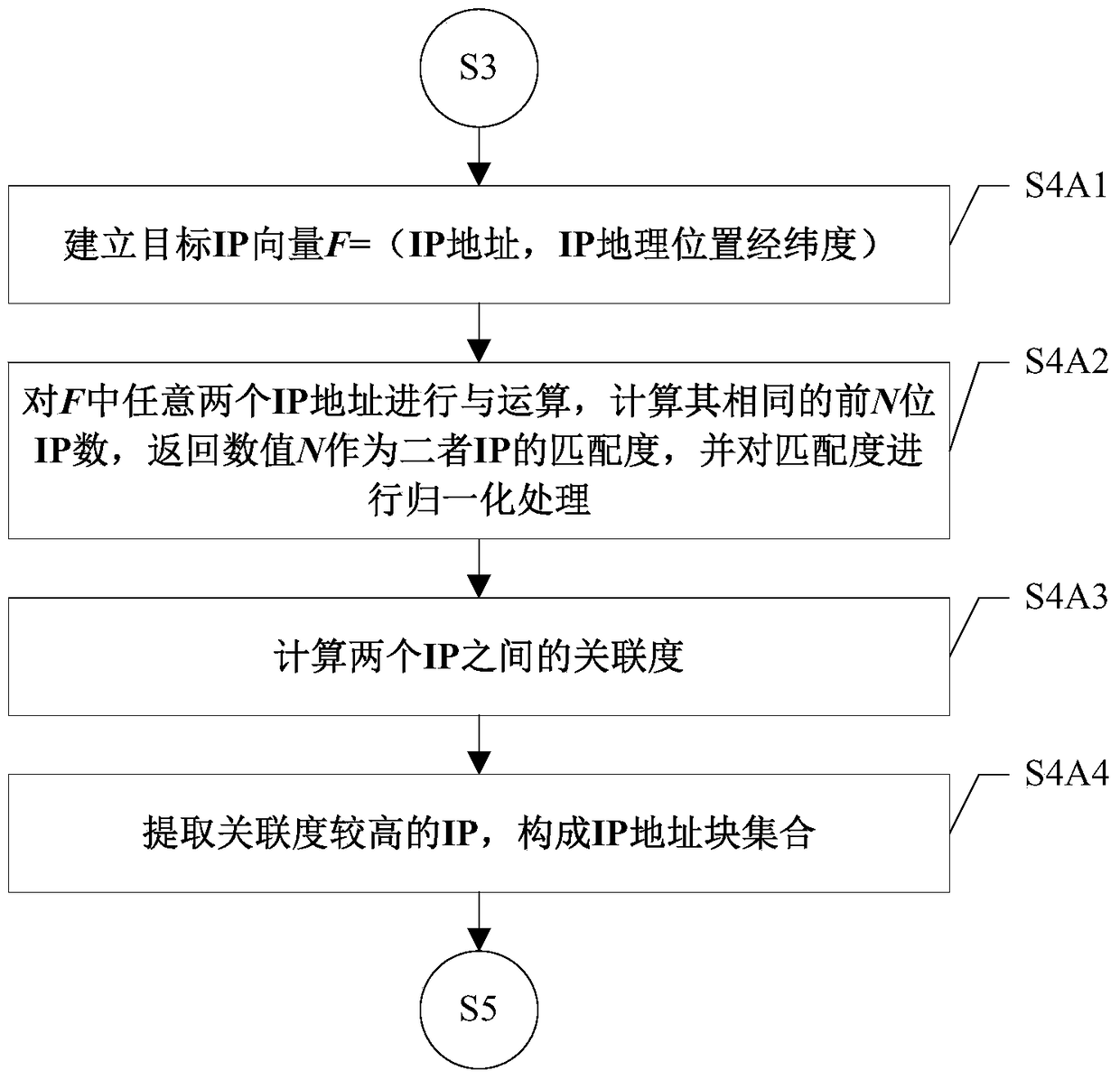
A cross-site user association method based on user name similarity
ActiveCN106126654BEasy accessUnrestricted integrityData processing applicationsWeb data indexingPattern recognitionComputer science
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
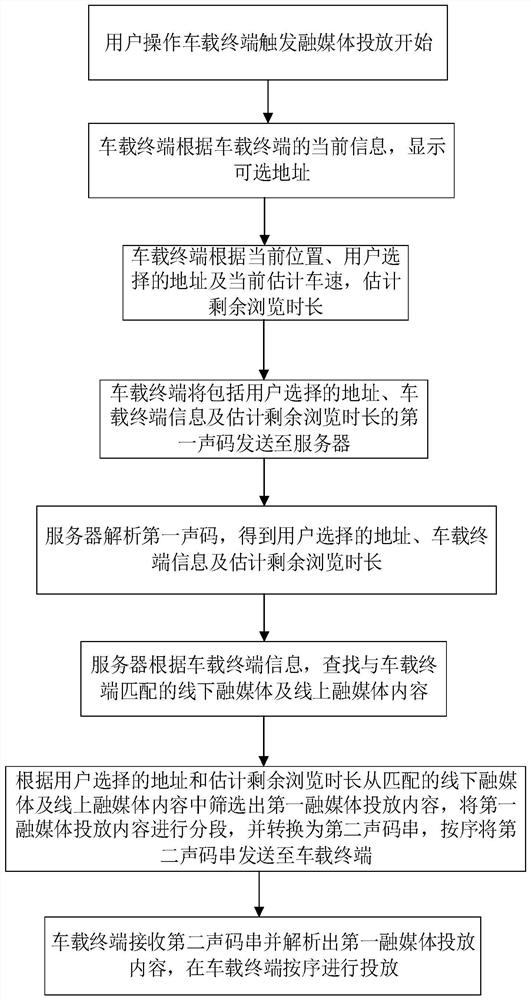
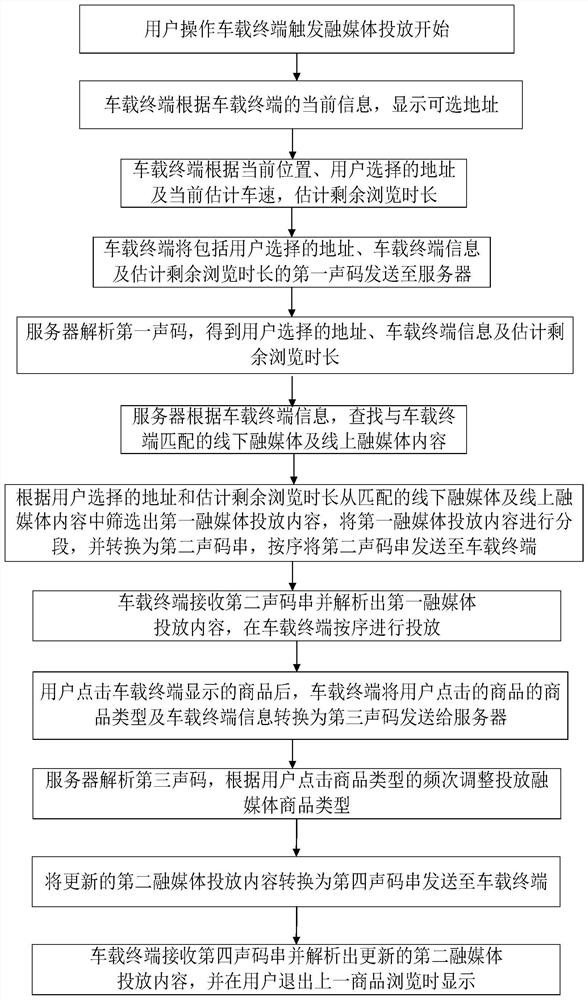
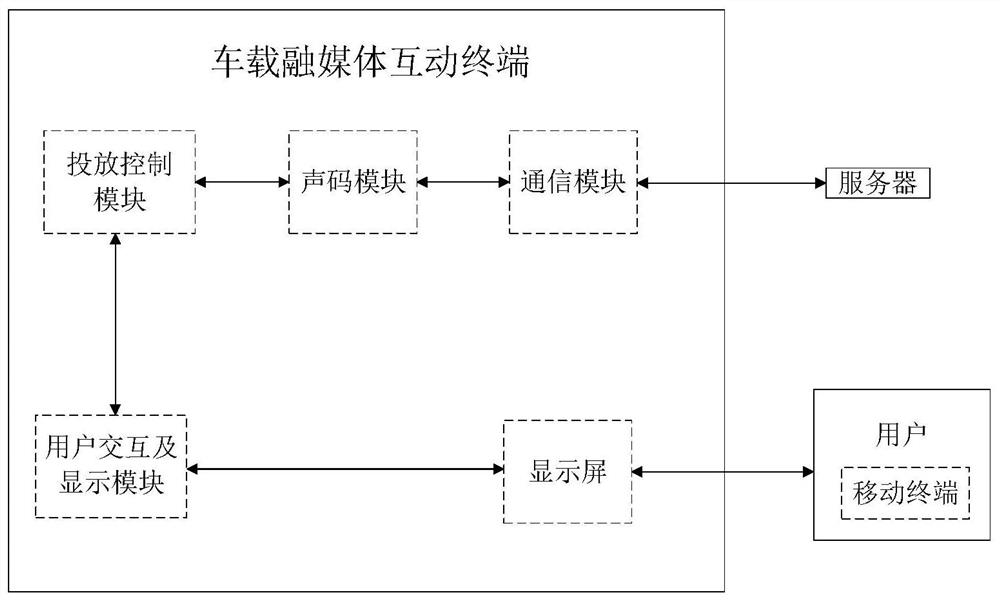
Vehicle-mounted terminal convergence media delivery method and vehicle-mounted convergence media interaction terminal
ActiveCN114025175APrecise deliveryAvoid interferenceSelective content distributionUser privacyIn vehicle
The invention provides a vehicle-mounted terminal convergence media delivery method and a vehicle-mounted convergence media interaction terminal, and belongs to the technical field of convergence media delivery. According to the method, fusion media delivery is triggered through user operation, after a user selects an address, the remaining browsing duration is estimated, and the remaining browsing duration, the selected address and vehicle-mounted terminal information are sent to a server in a sound code mode; a server searches for matched offline and online convergence media, screens out convergence media delivery content, segments the convergence media delivery content, converts the convergence media delivery content into acoustic code strings, and sends the acoustic code strings to the vehicle-mounted terminal; and the vehicle-mounted terminal analyzes the converged media delivery content and delivers the converged media delivery content in sequence. And the server performs convergence media content adjustment according to the frequency of the commodity types clicked by the user, and performs arrival reminding according to the address selected by the user. The converged media delivery is triggered by the user, accurate delivery of online shopping groups and old people is realized, and excessive user privacy is not involved.
Owner:上海声态圈物联网科技有限公司
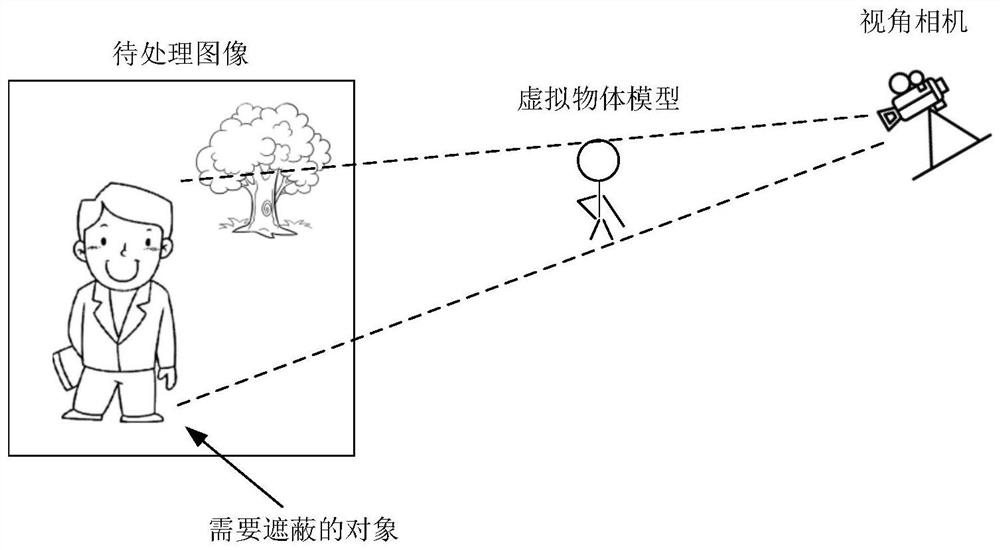
Image shielding method and device, equipment and storage medium
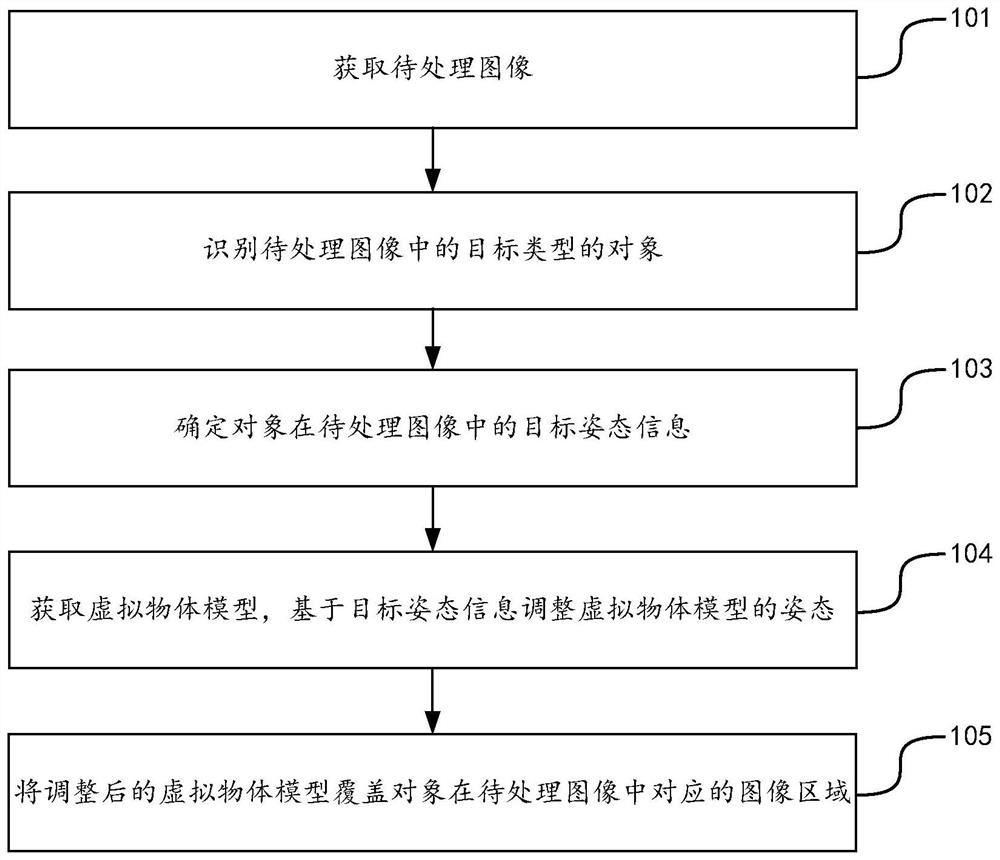
PendingCN114723854ANo privacy involvedImage enhancementImage analysisComputer graphics (images)Engineering
The embodiment of the invention provides an image shielding method and device, equipment and a storage medium. The method comprises the following steps: acquiring a to-be-processed image; identifying an object of a target type in the to-be-processed image; determining target attitude information of the object in the to-be-processed image; obtaining a virtual object model, and adjusting the attitude of the virtual object model based on the target attitude information; and covering an image area corresponding to the object in the to-be-processed image with the adjusted virtual object model. According to the method, the real image of the object is shielded, and meanwhile, a part of available information which does not involve privacy and can be exposed to the outside can be reserved by enabling the virtual object model to simulate the posture of the object and the like.
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
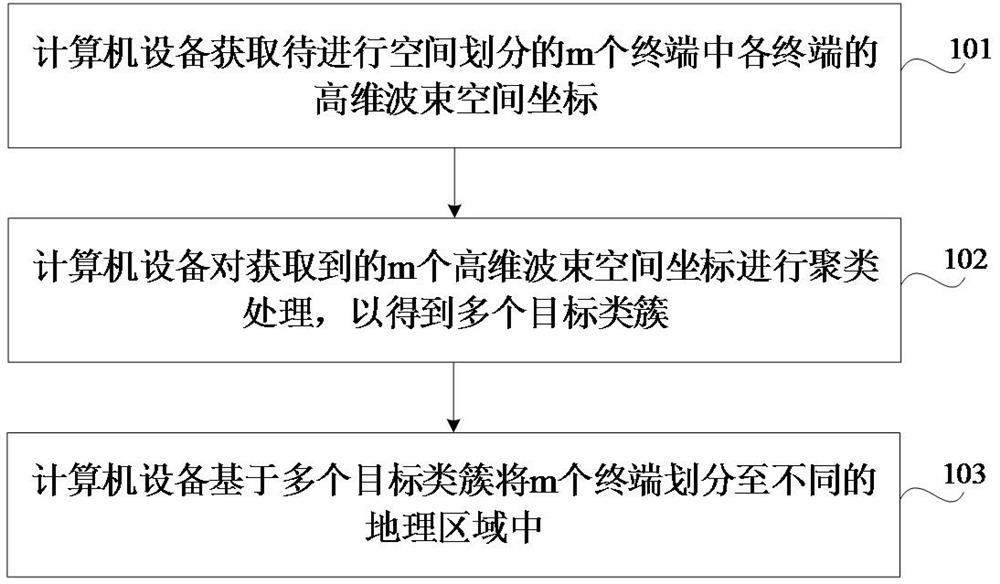
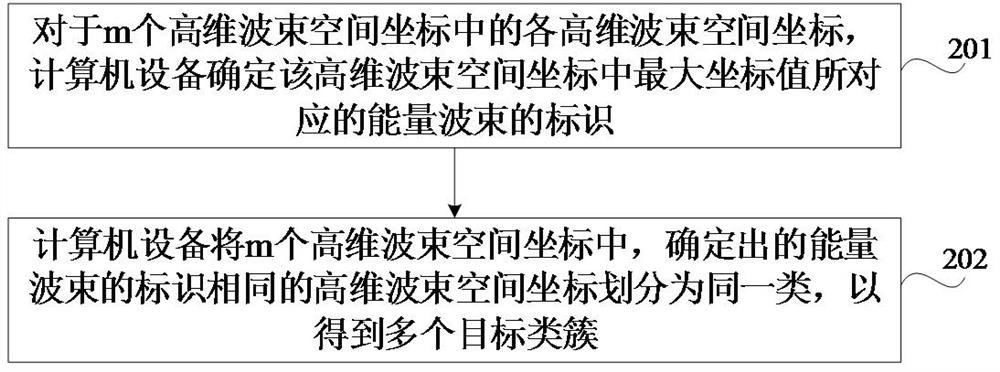
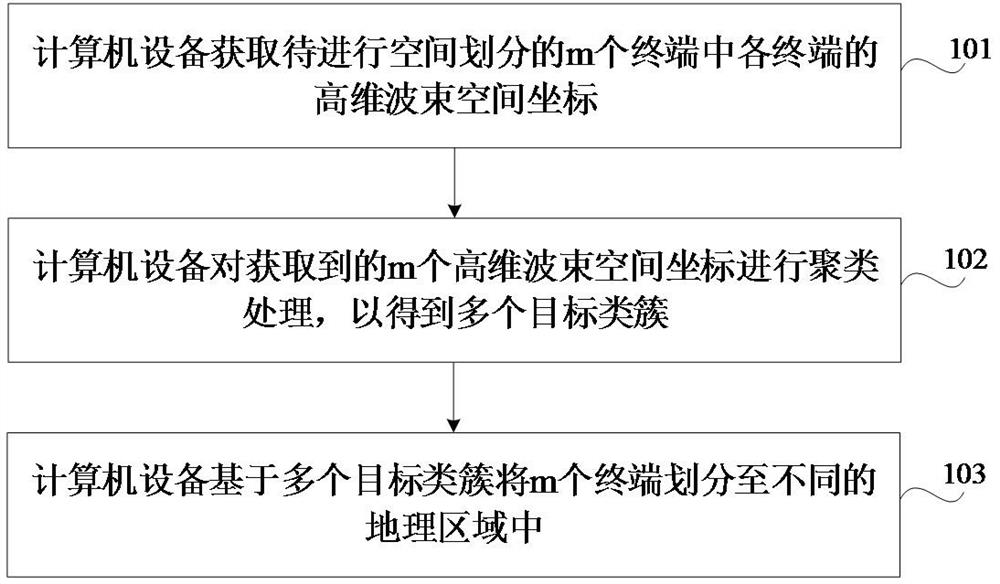
Spatial division method, apparatus, device, medium and program product
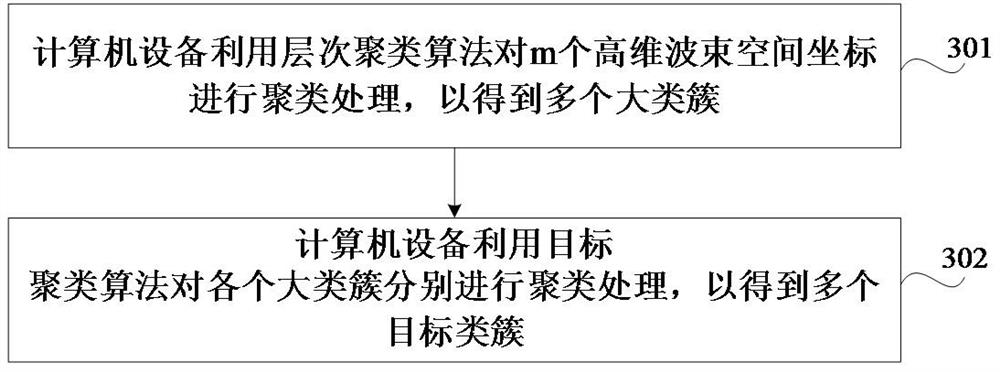
ActiveCN114430530BDivision successNo privacy involvedCharacter and pattern recognitionLocation information based serviceSpatial partitionSignal strength
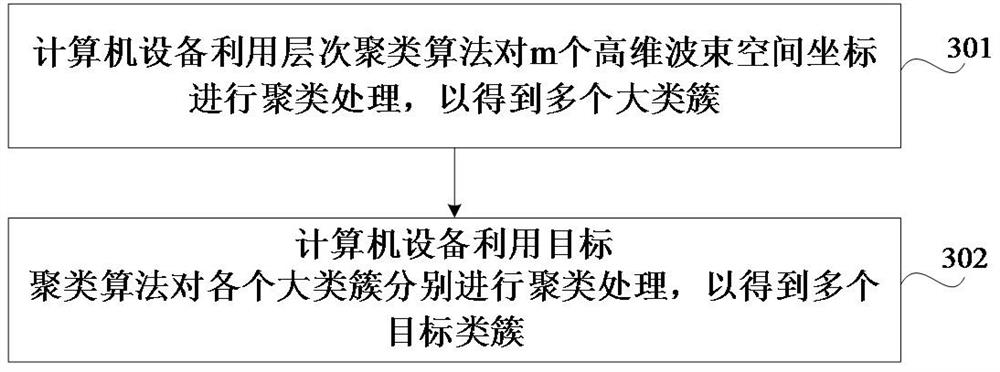
The present application relates to a space division method, device, device, medium and program product, and relates to the technical field of wireless communication. The method includes: obtaining the high-dimensional beam space coordinates of each of the m terminals to be space-divided, the high-dimensional beam space coordinates include n coordinate values, and the n coordinate values are equal to the n energy beams in the multi-antenna system One-to-one correspondence, each coordinate value is the received signal strength RSS of the corresponding energy beam; the acquired m high-dimensional beam space coordinates are clustered to obtain multiple target clusters; based on multiple target clusters, m Terminals are divided into different geographical regions. Adopting the method can ensure that the terminals can be successfully space-divided, thereby ensuring the successful prediction of the wireless network traffic.
Owner:THE CHINESE UNIV OF HONG KONG SHENZHEN +2
Smartphone usage context recognition method based on touch behavior sequence
ActiveCN112073582BEasy to use habitsNo privacy involvedDevices with sensorCharacter and pattern recognitionContext recognitionEngineering
Smartphone usage context recognition method based on touch behavior sequence, which defines 9 kinds of touch operations, extracts 9 kinds of touch operation attributes (touch start and end time, etc.) , taking 32 continuous operations as a basic touch interaction sequence; then use the long short-term memory network and attention mechanism to model, to realize the judgment and statistics of the user's use of the mobile phone situation. In the present invention, the basic touch interaction sequence is input into the two-way long-short-term memory network model of the superimposed attention mechanism for situation recognition, and realizes the judgment of the user's mobile phone situation including shopping, social interaction, browsing, learning, short video, game, etc. Realize the subdivision of multiple scenarios in the user's smartphone application, and count the usage time of each scenario within a certain period of time, so as to provide a direct basis for users to know the usage duration of their smartphones in various scenarios.
Owner:OCEAN UNIV OF CHINA
A mobile Internet voiceprint access control system and its implementation method
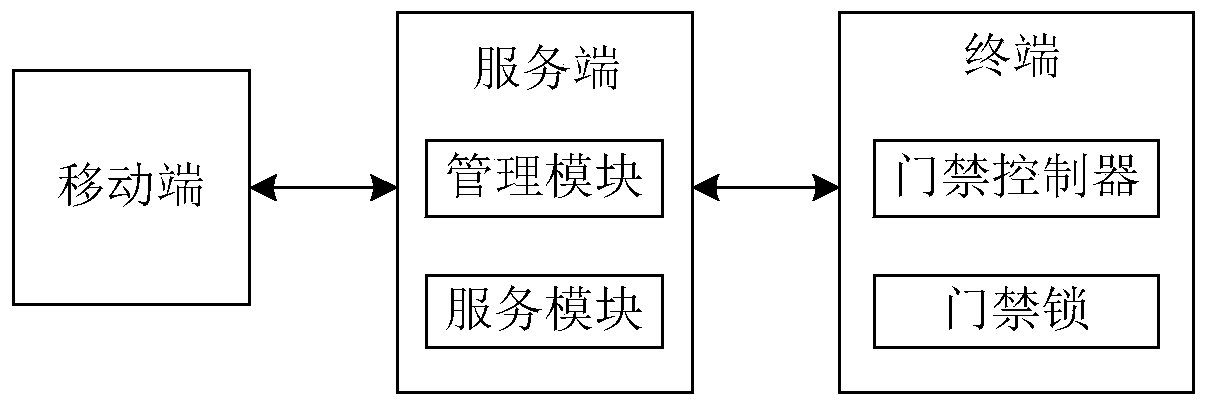
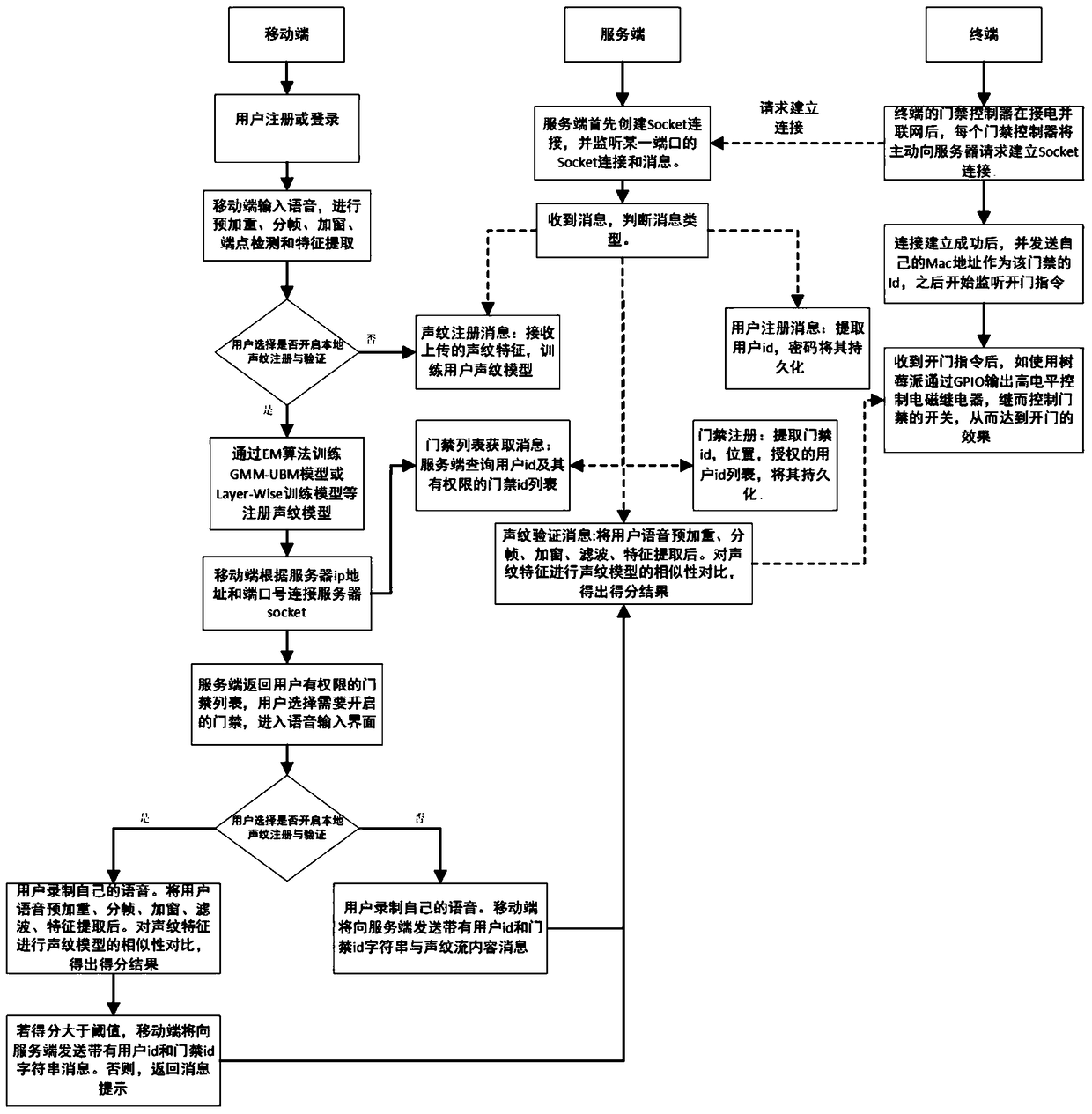
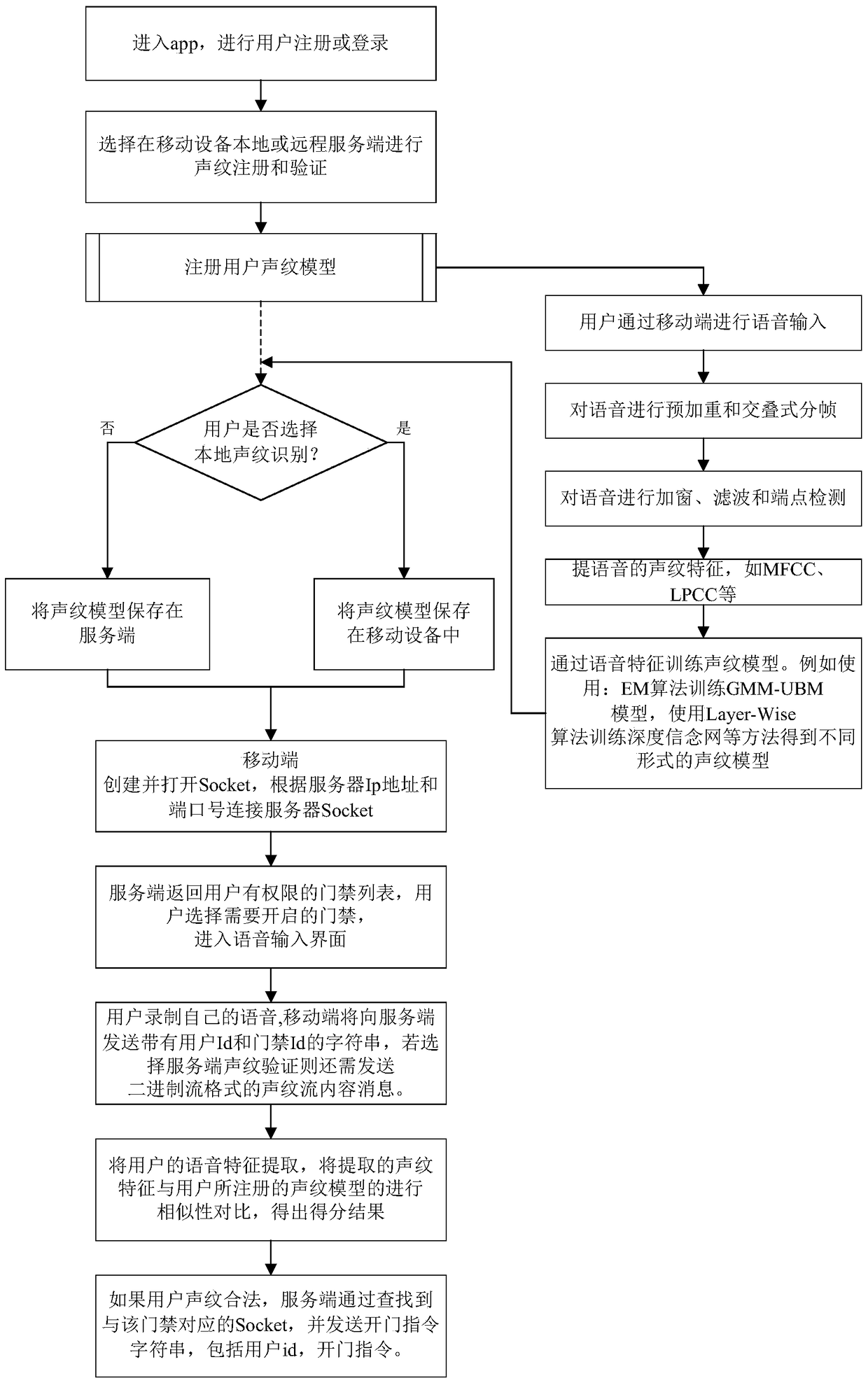
ActiveCN105069874BIncrease the difficulty of counterfeitingCannot be stolenIndividual entry/exit registersComputer terminalMobile device
The invention proposes a mobile Internet voiceprint access control system and an implementation method thereof, belonging to the technical field of identity authentication. The system of the present invention is divided into a mobile terminal, a server terminal and a terminal. The mobile terminal displays the access control list that the user has permission, receives voiceprint input and generates and verifies the local voiceprint model, establishes a Socket connection between the mobile device and the server; the server manages users, access control and door opening records, and remotely registers and verifies the voiceprint Pattern model; the terminal includes the access controller and the access lock, and the access controller actively requests the server to establish a Socket connection after networking, and listens for the door opening command. The invention can enable users to perform local or remote door opening operations through mobile devices and voice, and has the advantages of high difficulty in counterfeiting, impossibility of stealing, no privacy involved, low cost, easy remote verification and the like.
Owner:BEIHANG UNIV
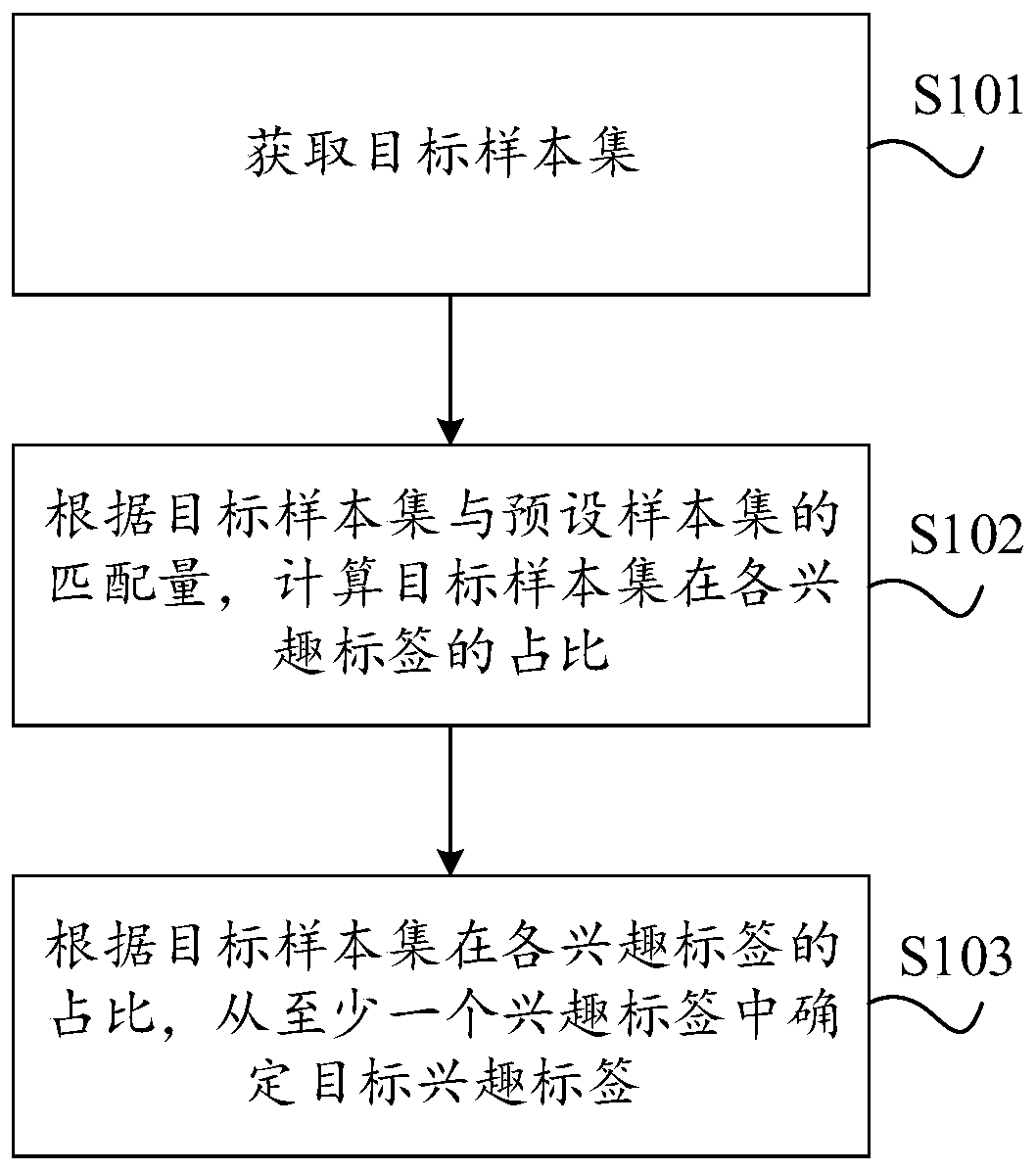
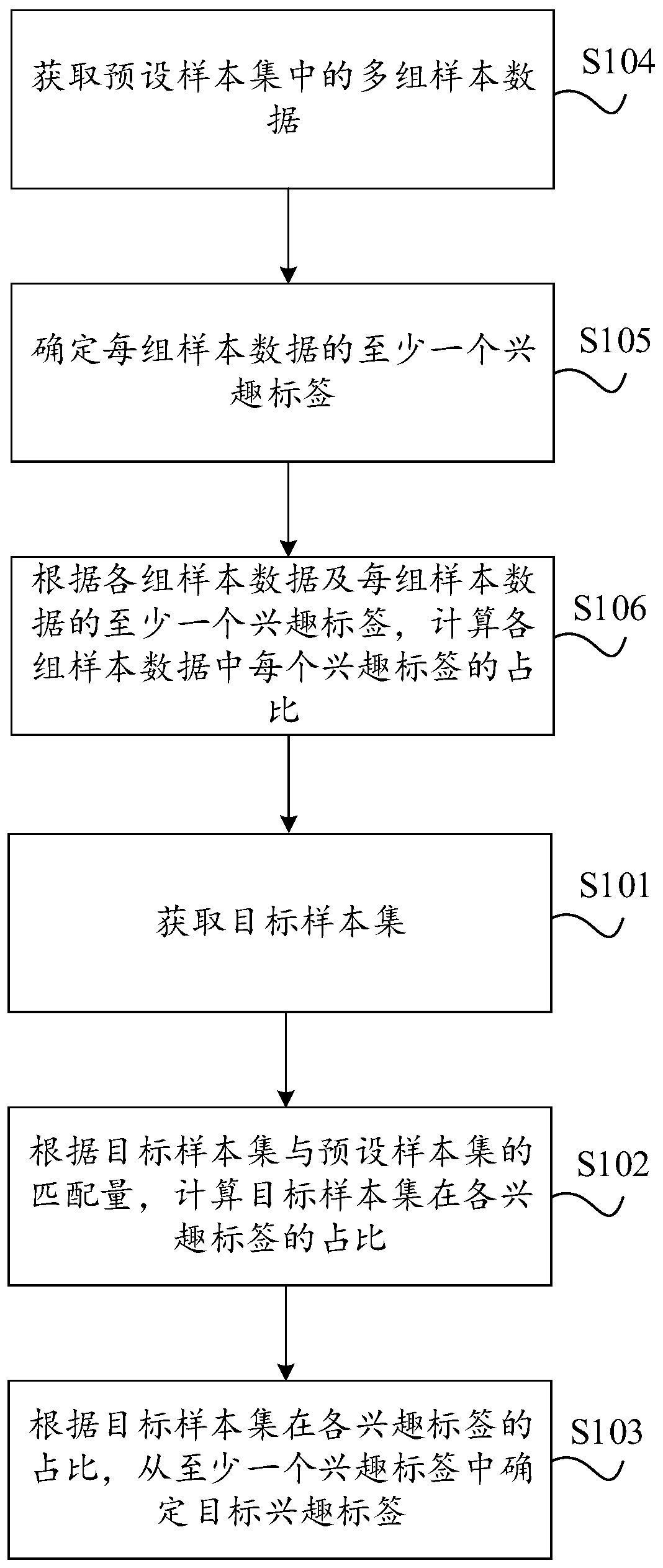
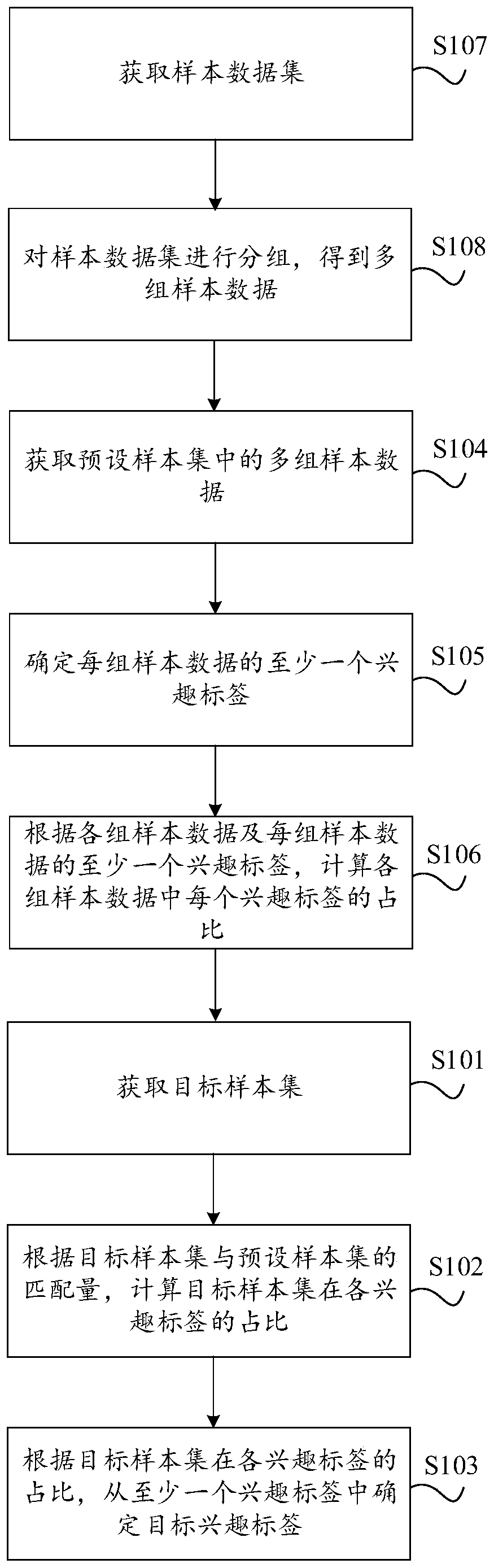
Target audience interest analysis method and device, equipment and storage medium
The invention provides a target audience interest analysis method and device, equipment and a storage medium, and relates to the technical field of data analysis. The method comprises the steps of obtaining a target sample set; calculating the proportion of the target sample set in each interest label according to the matching amount of the target sample set and a preset sample set; wherein the preset sample set comprises multiple groups of sample data and at least one interest label; and determining a target interest label from at least one interest label according to the proportion of the target sample set in each interest label. Compared with the prior art, the problem that cost is high due to the fact that interest of sample data is analyzed through a large amount of investigated individual-level data is avoided.
Owner:MIAOZHEN INFORMATION TECH CO LTD
Adjustment method of TV angle, TV set, and computer-readable storage medium
ActiveCN109557951BEasy to watchImprove viewing effectControl using feedbackComputer graphics (images)Television set
The invention discloses a method for adjusting the angle of a TV set, which includes: obtaining user coordinates projected to a TV plane according to voice information of a user in a current indoor environment; distance; determine the horizontal angle of the user relative to the TV plane according to the user coordinates and distance; adjust the viewing angle of the TV according to the horizontal angle. The present invention also provides a television and a computer-readable storage medium. The solution provided by the present invention locates the coordinates projected by the user to the TV plane according to the user's voice information, automatically adjusts the screen of the TV to the angle facing the user, is suitable for the user to watch, and enables the user to obtain the best viewing effect, thereby improving the User viewing experience.
Owner:SHENZHEN TCL DIGITAL TECH CO LTD
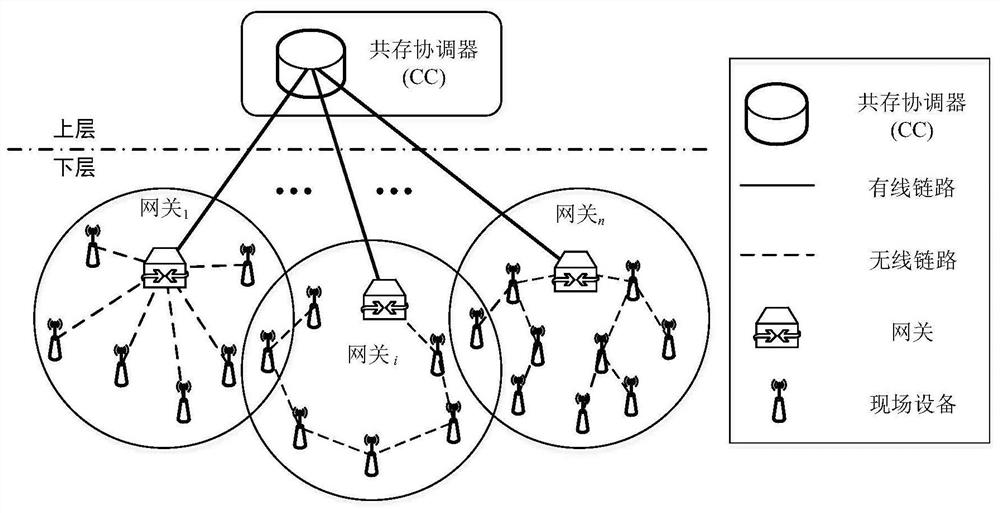
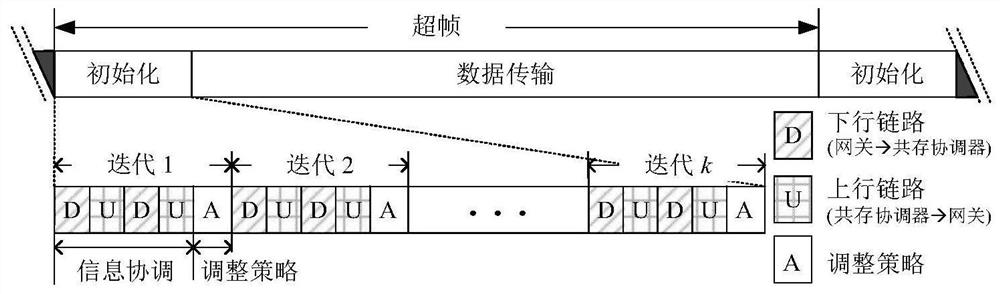
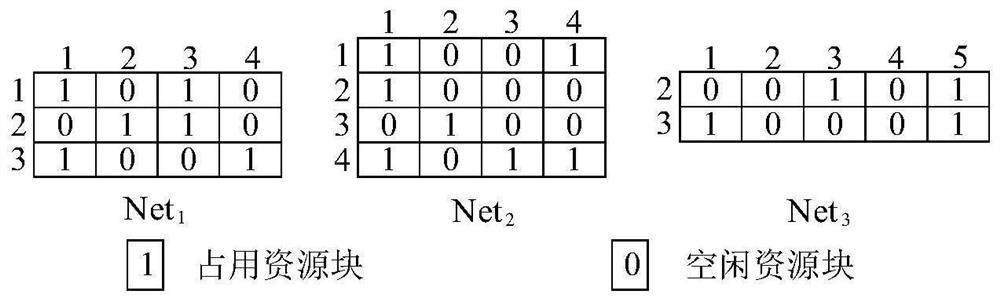
Industrial wireless network non-centralized coexistence management method based on information coordination
ActiveCN114095455ANo limitNo limit on network sizeTransmissionHigh level techniquesResource coordinationPrivacy protection
The invention relates to an industrial wireless network coexistence management method, in particular to an industrial wireless network non-centralized coexistence management method based on information coordination. Aiming at the coexistence problem caused by mutual interference of a plurality of industrial wireless networks, the invention provides the non-centralized coexistence management method applied to industrial wireless networks for the first time, and the non-centralized coexistence management method specifically comprises two parts of incomplete information interaction and non-centralized resource coordination. For the incomplete information used for coordination, on the premise of considering privacy protection, the content of the incomplete information is definitely defined, and guidance is provided for non-centralized resource coordination; and aiming at the aspect of non-centralized resource coordination, the requirement of network transmission data packet deadline is considered, a network utility function is designed, based on coordinated incomplete information, the network utility function is designed, and a network occupied resource strategy is independently adjusted. The network gain is maximized, the time required for convergence of the algorithm is reduced, and the interference between coexisting networks is minimized.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
A k-anonymous incentive method based on local reputation storage
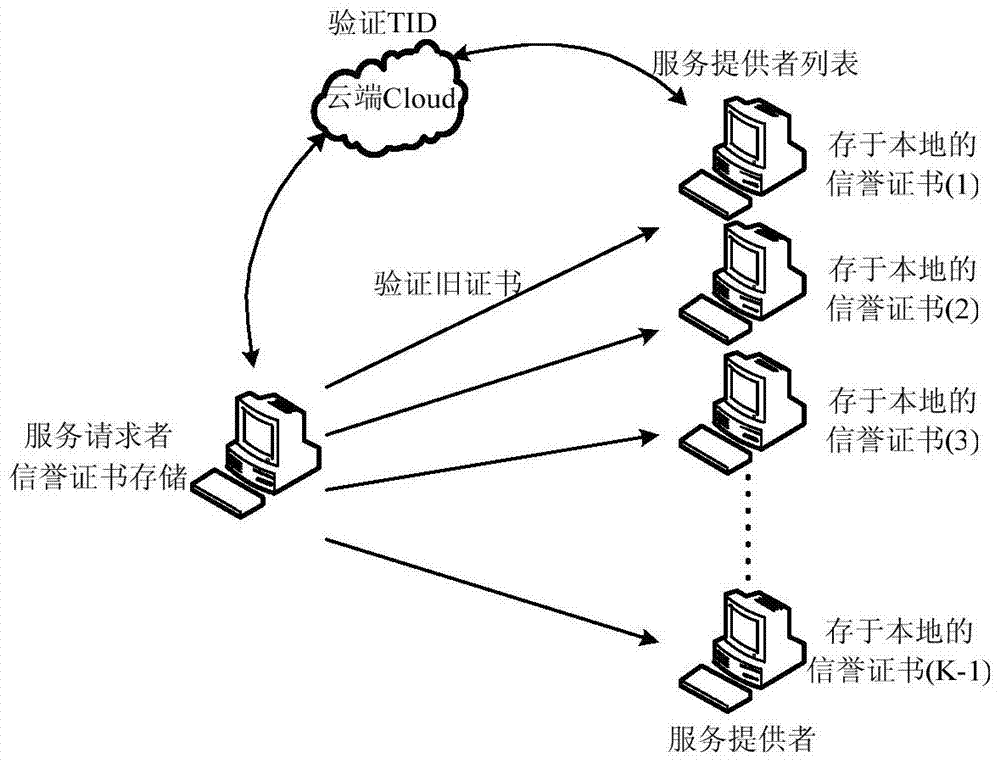
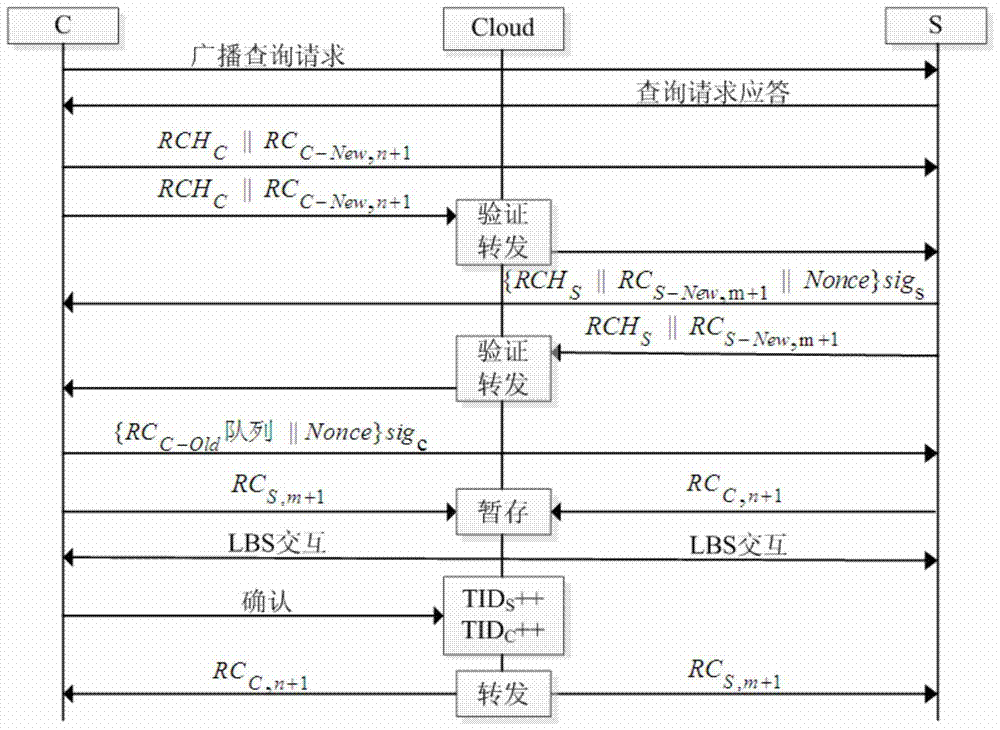
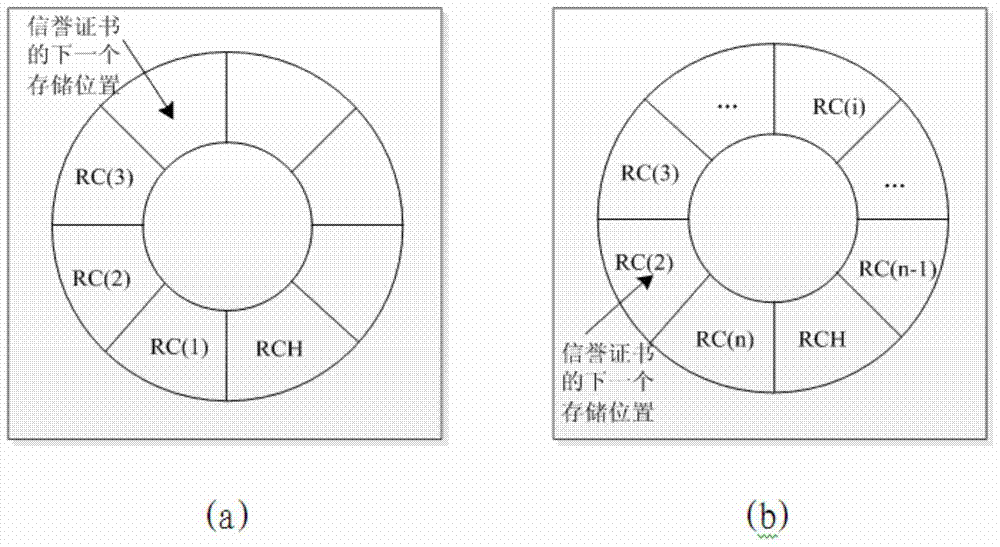
ActiveCN104168563BIncrease motivationTo achieve the effect of continuous motivationLocation information based serviceSecurity arrangementThird partyK-anonymity
Owner:XIDIAN UNIV
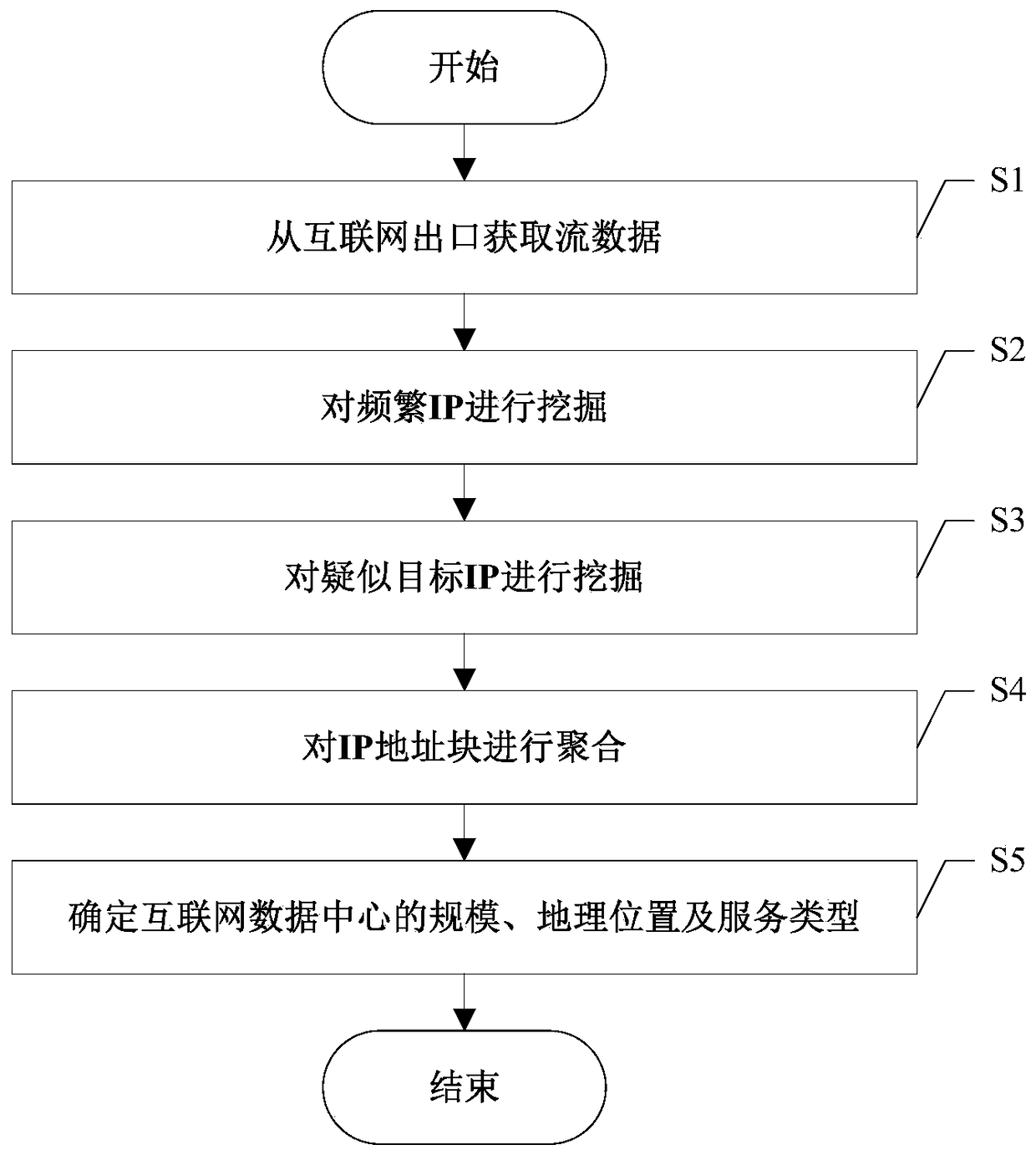
A search method for Internet data center ip address based on traffic behavior
ActiveCN105430109BNo privacy involvedResource optimizationData switching networksData streamIp address
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
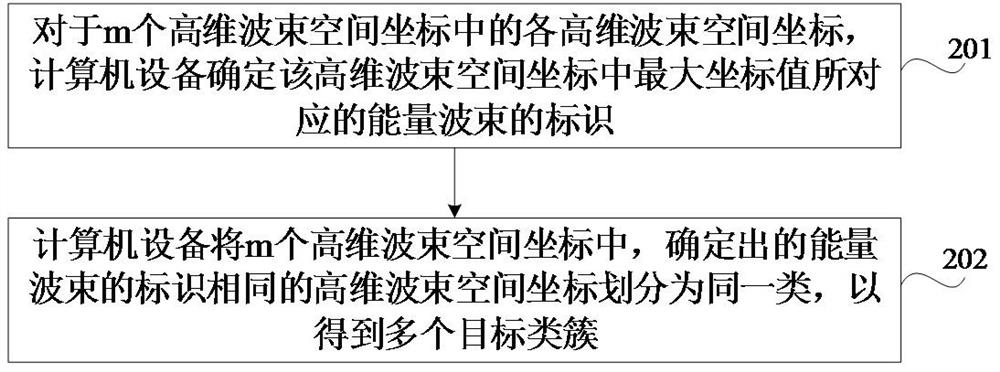
Space division method and device, equipment, medium and program product
ActiveCN114430530ADivision successNo privacy involvedCharacter and pattern recognitionTransmissionComputer hardwareSpatial partition
The invention relates to a space division method and device, equipment, a medium and a program product, and relates to the technical field of wireless communication. The method comprises the steps that high-dimensional beam space coordinates of each terminal in m terminals to be spatially divided are acquired, the high-dimensional beam space coordinates comprise n coordinate values, the n coordinate values are in one-to-one correspondence with n energy beams in the multi-antenna system, and each coordinate value is received signal strength (RSS) of the corresponding energy beam; performing clustering processing on the obtained m high-dimensional beam space coordinates to obtain a plurality of target class clusters; and dividing the m terminals into different geographic areas based on the plurality of target class clusters. By adopting the method, it can be ensured that the terminal can be divided in space successfully, so that successful implementation of wireless network traffic prediction is ensured.
Owner:THE CHINESE UNIV OF HONG KONG SHENZHEN +2
Coding-based entity ID creation method and system
PendingCN111597345AUniqueness guaranteedNo privacy involvedCharacter and pattern recognitionNatural language data processingData securityEngineering
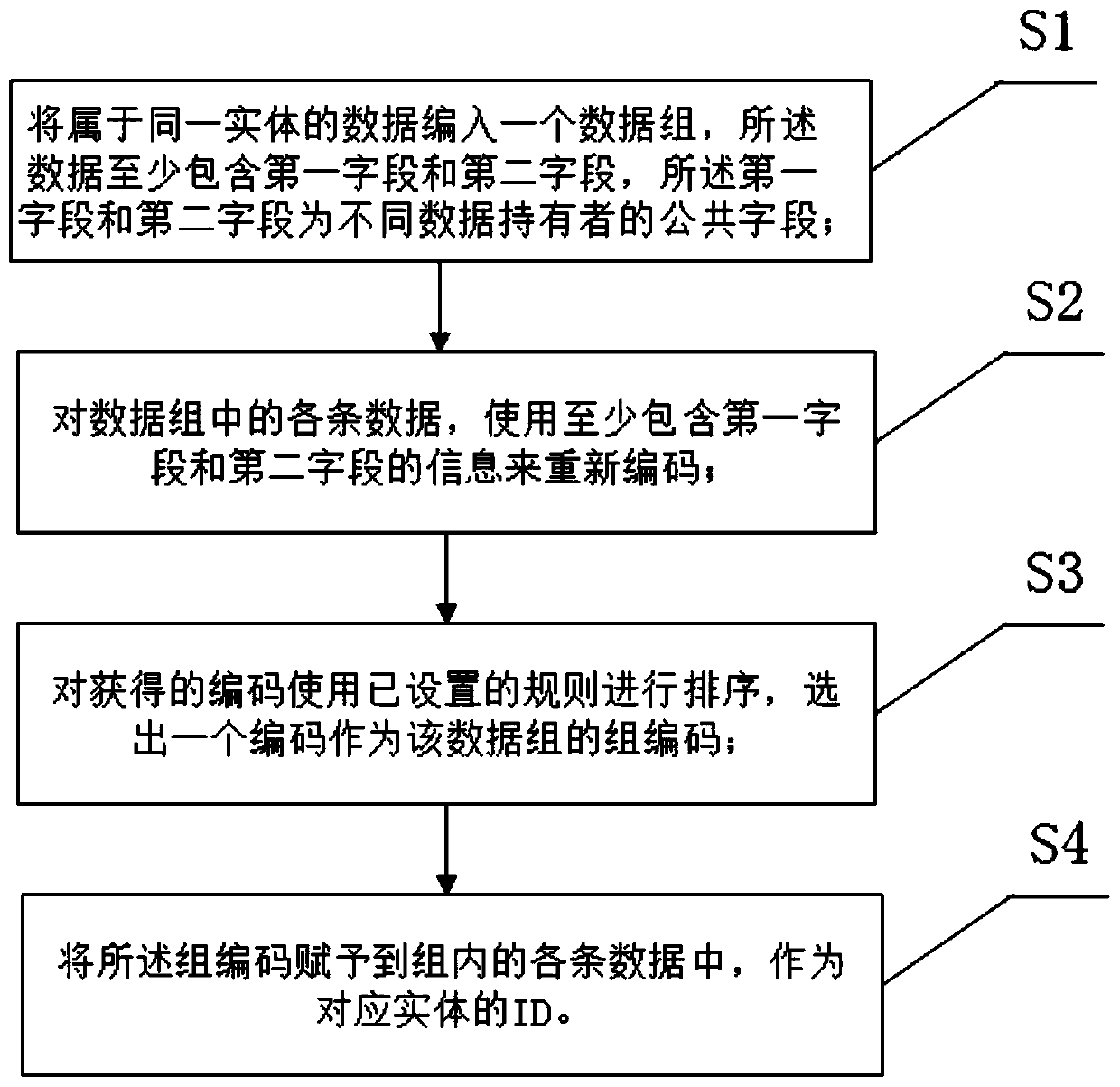
The invention relates to a coding-based entity ID creation method and system. According to the invention, the entities are coded by using the common fields of different data holders, the constructed codes are sorted by using the set rules, and the codes conforming to a certain data rule are selected as the common IDs of the same entities, so that accurate and non-redundant construction of knowledge graph construction is realized. And support is provided for data fusion of different data holders. The ID constructed through the method has uniqueness, privacy or sensitive information is not involved, and data safety is guaranteed.
Owner:成都数联铭品科技有限公司
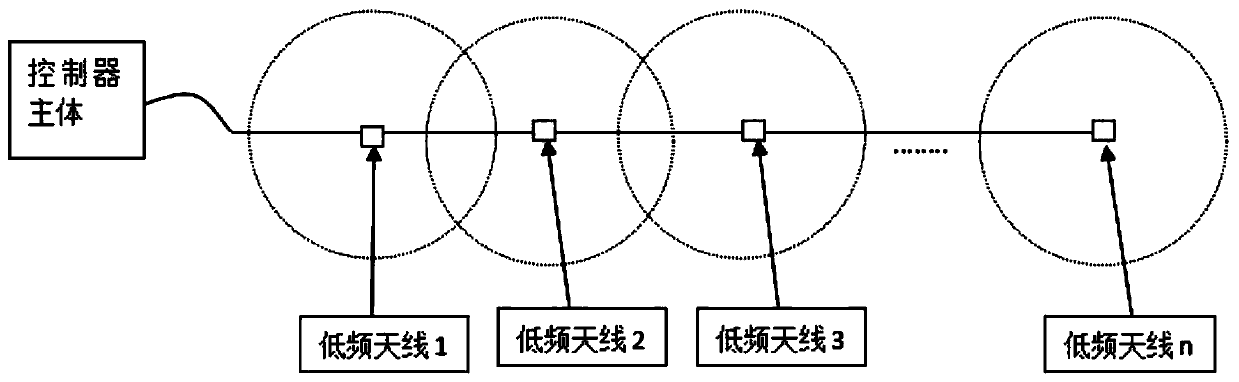
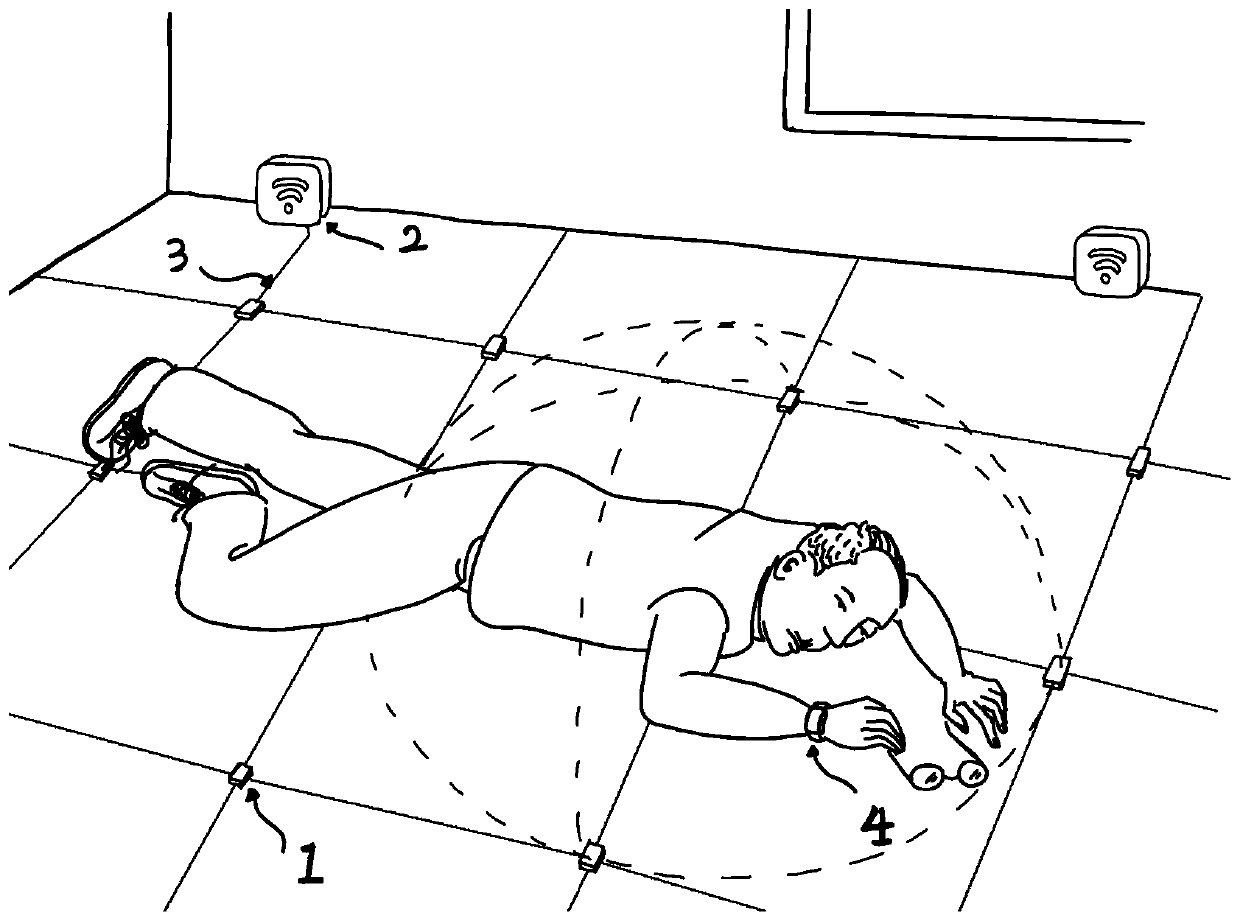
Detection device and use method thereof
PendingCN110338810ASimple installation and deploymentEasy to useSensorsAlarmsComputer moduleEngineering
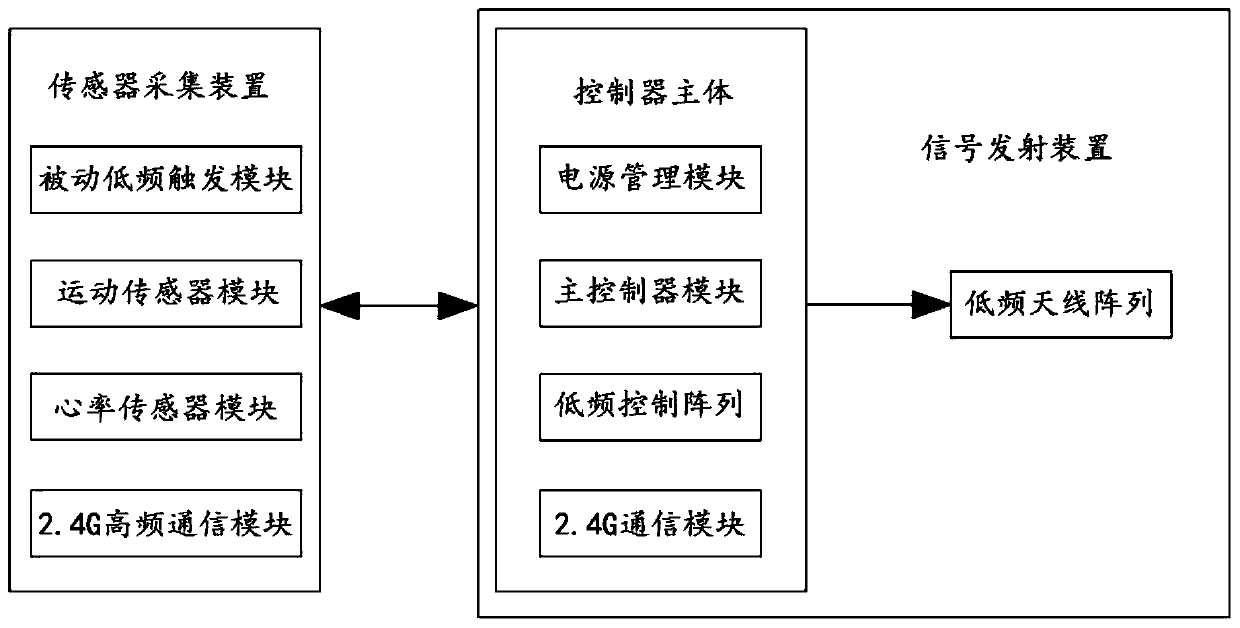
The invention provides a detection device and a use method thereof, and relates to the technical field of monitoring and detection equipment. The detection device comprises a sensor acquisition deviceand a signal emission device, wherein the sensor acquisition device comprises a passive low-frequency trigger module, a motion sensor module, a heart rate sensor module and a 2.4 G high-frequency communication module, the signal emission device comprises a controller body and a low-frequency antenna array, and the controller body comprises a power management module, a master controller module, alow-frequency controller array and a 2.4 G communication module. The detection device and the use method thereof have the advantages that the installation and deployment are simple, the installation position is not restricted, the reliability is high, and the implementation and running cost of the device is low.
Owner:杭州米越科技有限公司
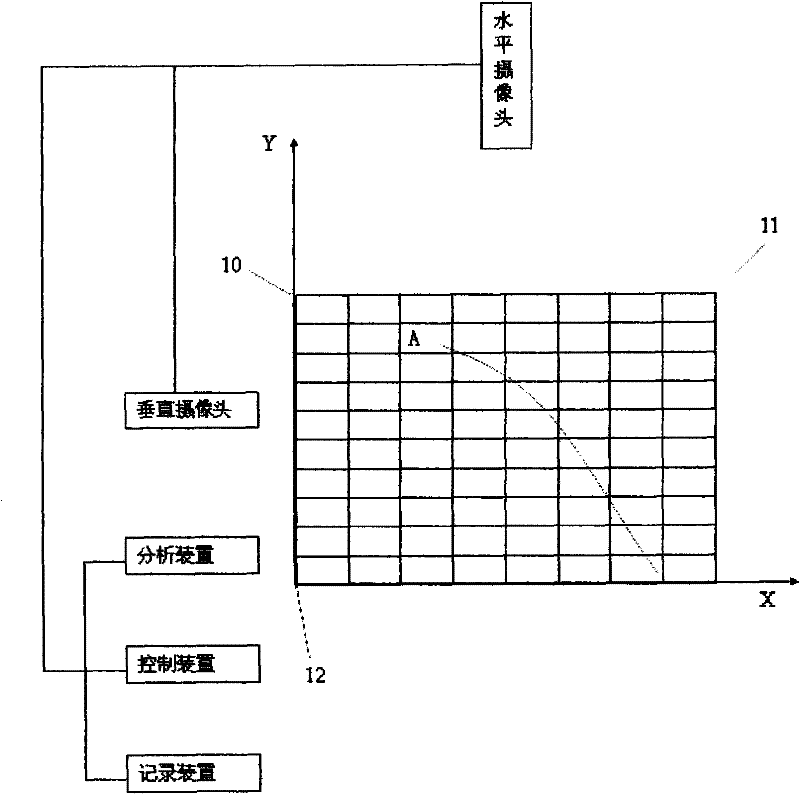
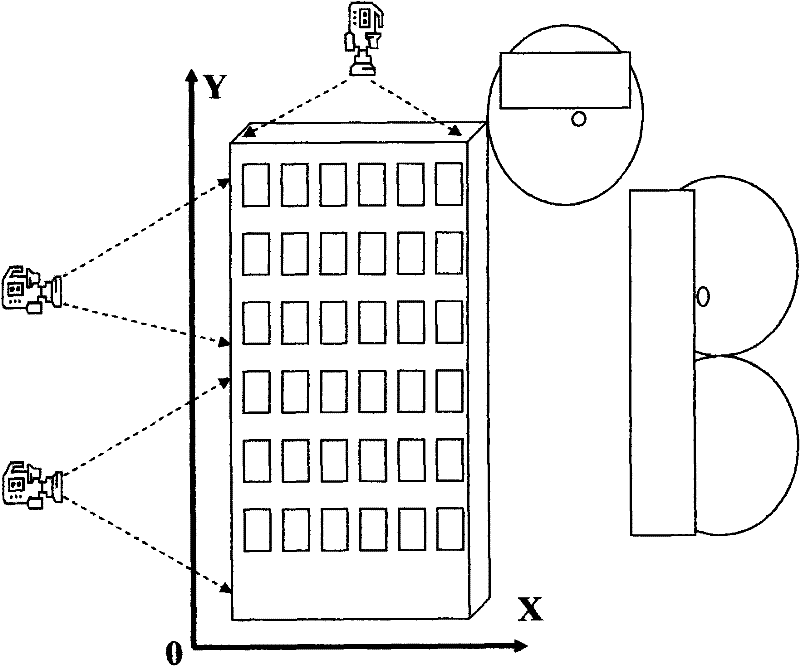
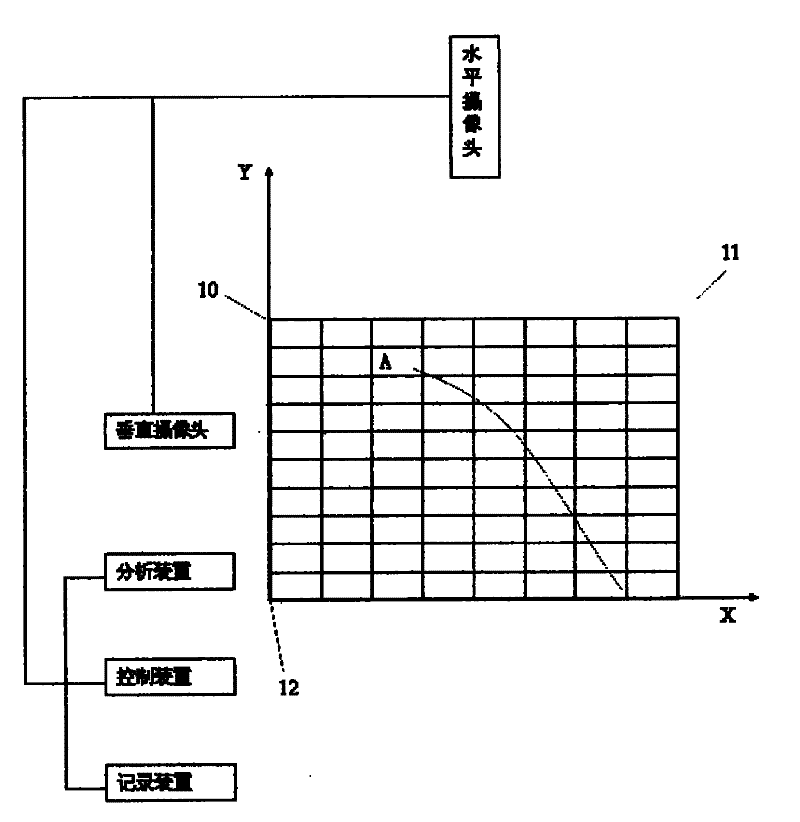
Automatic position system of multiple cameras
InactiveCN101646072BAccurate detectionNo privacy involvedClosed circuit television systemsPanoramic photographyVisual field lossSky
The invention provides an automatic position system of multiple cameras, which is applied to monitor residential housing. The invention is characterized in that the system at least comprises a horizontal camera for transverse scan and shooting, a vertical camera for vertical scan and shooting, a control device for connecting the horizontal camera and the vertical camera, an analysis device and a recording device, wherein the control device is used for controlling the scanning periods of the horizontal camera and the vertical camera and controlling the record operation of the recording device.The invention can accurately detect an object threw in high sky, and has hard evidence to cause a shooter to be unable to quibble; in addition, the shooting visual field of a camera all aims at nonactive areas of residents, thus relating to no privacy.
Owner:融创天下(上海)科技发展有限公司
A mobile malicious user identification method and system based on communication behavior rules
The present invention relates to a method and system for identifying mobile malicious users based on communication behavior rules. Sampling data, using the behavior pattern analysis in the mobile communication behavior analysis model to extract the user's call behavior characteristics, short message behavior characteristics and time distribution characteristics; based on the preprocessed mobile communication sampling data, using the communication network analysis in the mobile communication behavior analysis model Extract the user's social attribute features; based on the extracted user behavior pattern features and the extracted user social attribute features, build a mobile malicious user identification model; the present invention can analyze the user's behavior rules based on the desensitized data, and identify whether the user is a mobile malicious user The user has good timeliness and can identify mobile malicious users with high accuracy without involving the user's personal privacy.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
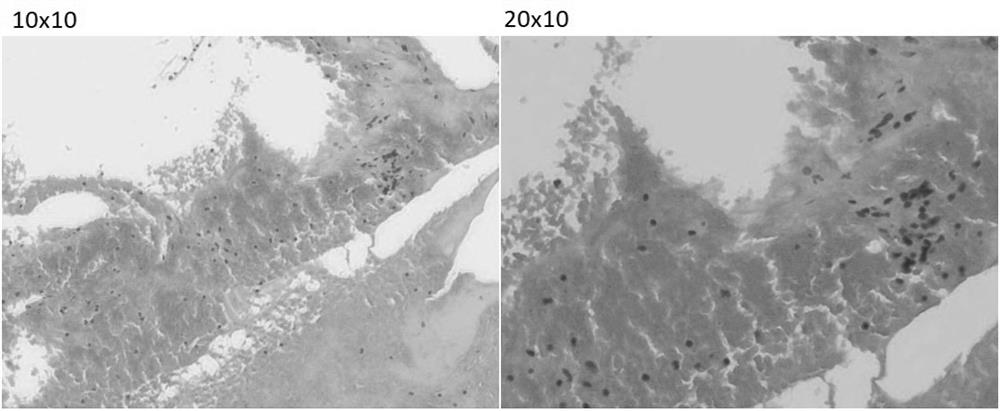
A method for preparing thyroid and breast fine-needle aspiration cell tissue block
ActiveCN109975090BSimple structureNo privacy involvedPreparing sample for investigationStainingMammary gland structure
The invention provides a method for preparing thyroid and mammary gland fine needle aspiration cell tissue block. It includes the following steps: a. Centrifuge non-infectious pleural effusion or ascites in advance to obtain pleural effusion or ascites supernatant; b. Take pleural effusion or ascites supernatant and inject it into a centrifuge tube; c. Thyroid or mammary gland punctured with a fine needle Inject the sample into the centrifuge tube, then immediately take 95% ethanol and inject it into the centrifuge tube; d, centrifuge the centrifuge tube and discard the supernatant to obtain the cell sediment, then add 4% neutral buffered formaldehyde fixative solution, and the cells in the centrifuge tube After the precipitate had solidified, routine embedding was performed using paraffin tissue specimen processing procedures. The preparation method of the invention can ensure no loss of tissue fragments and free-floating single cells, and the shape and structure of the cytoplasm are well preserved.
Owner:马晓丽
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com