Method and device for determining same service data based on privacy protection
A technology of business data and the same business, applied in the computer field, can solve the problems of multiple interactions and low comparison efficiency, and achieve the effects of improving comparison efficiency, improving efficiency, and reducing the amount of calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The following describes the solutions provided in this specification with reference to the drawings.
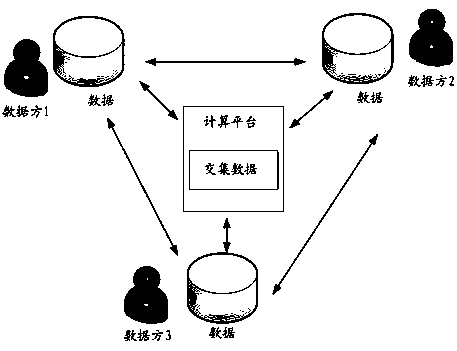
[0034] First, combine figure 1 A specific implementation scenario is shown for description. Such as figure 1 As shown, in this implementation scenario, multiple data parties have their own business data, and multiple data parties may also be referred to as multiple business parties. These data parties can communicate with each other, such as joint security data operations. That is, in the case where each data party does not obtain the data of the other party from each other, data calculation is performed. The data operations here are, for example, addition, multiplication, logical operations (and, or, not) and so on. It is understandable that subtraction and addition can be transformed into each other, and multiplication and division can be transformed into each other. As a means of data operation, the specific scenarios can be determined according to actual business n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com