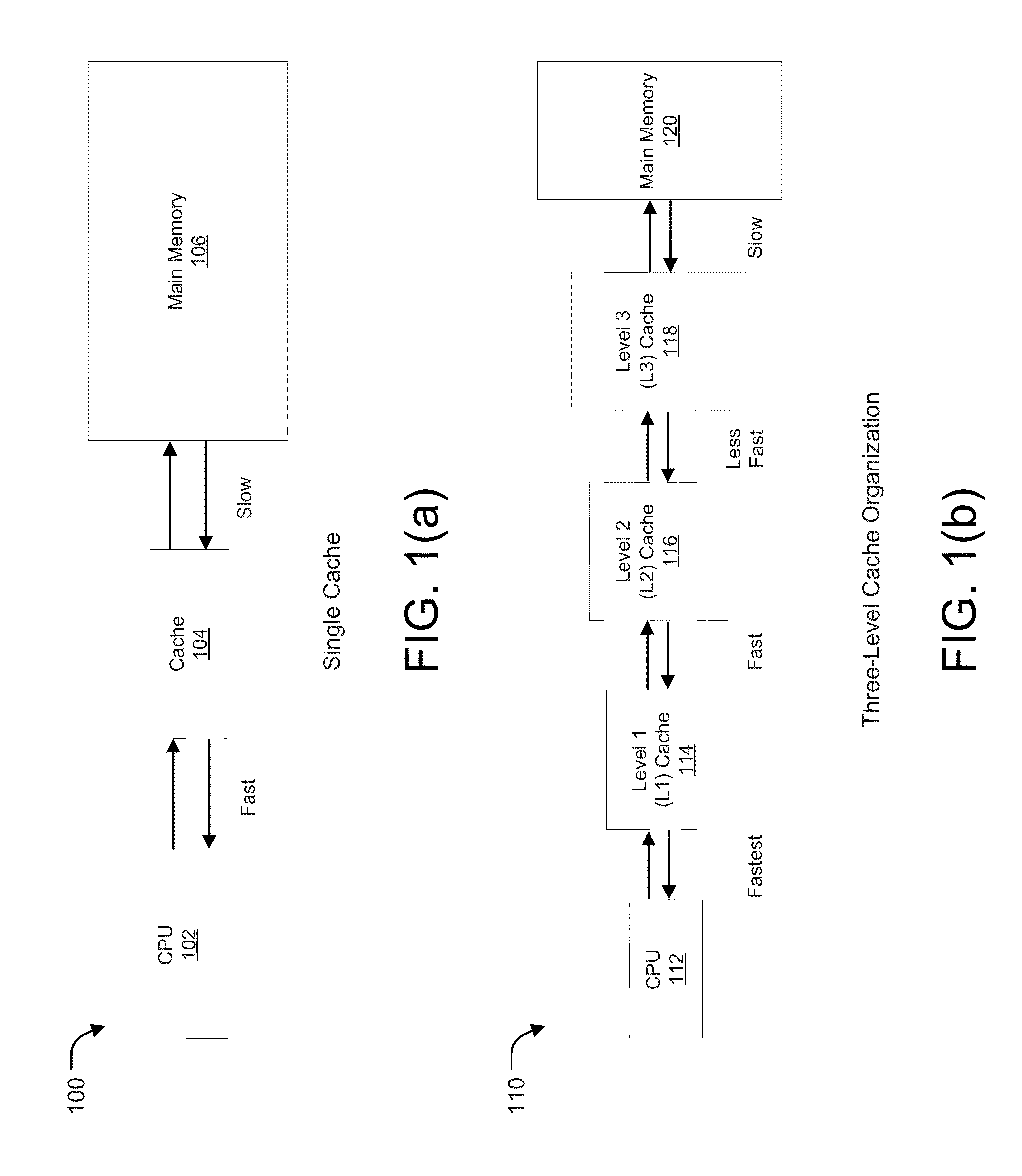
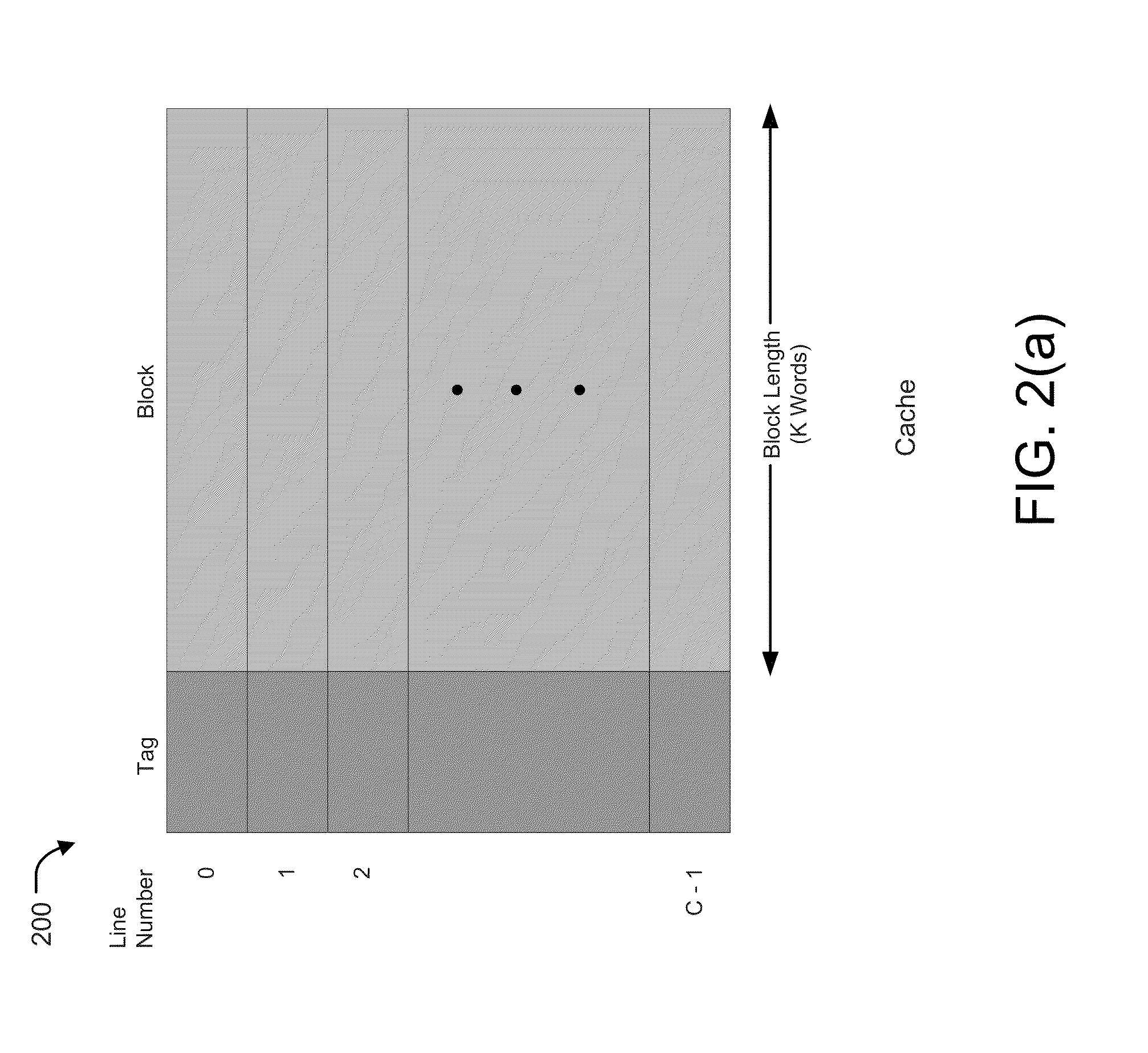
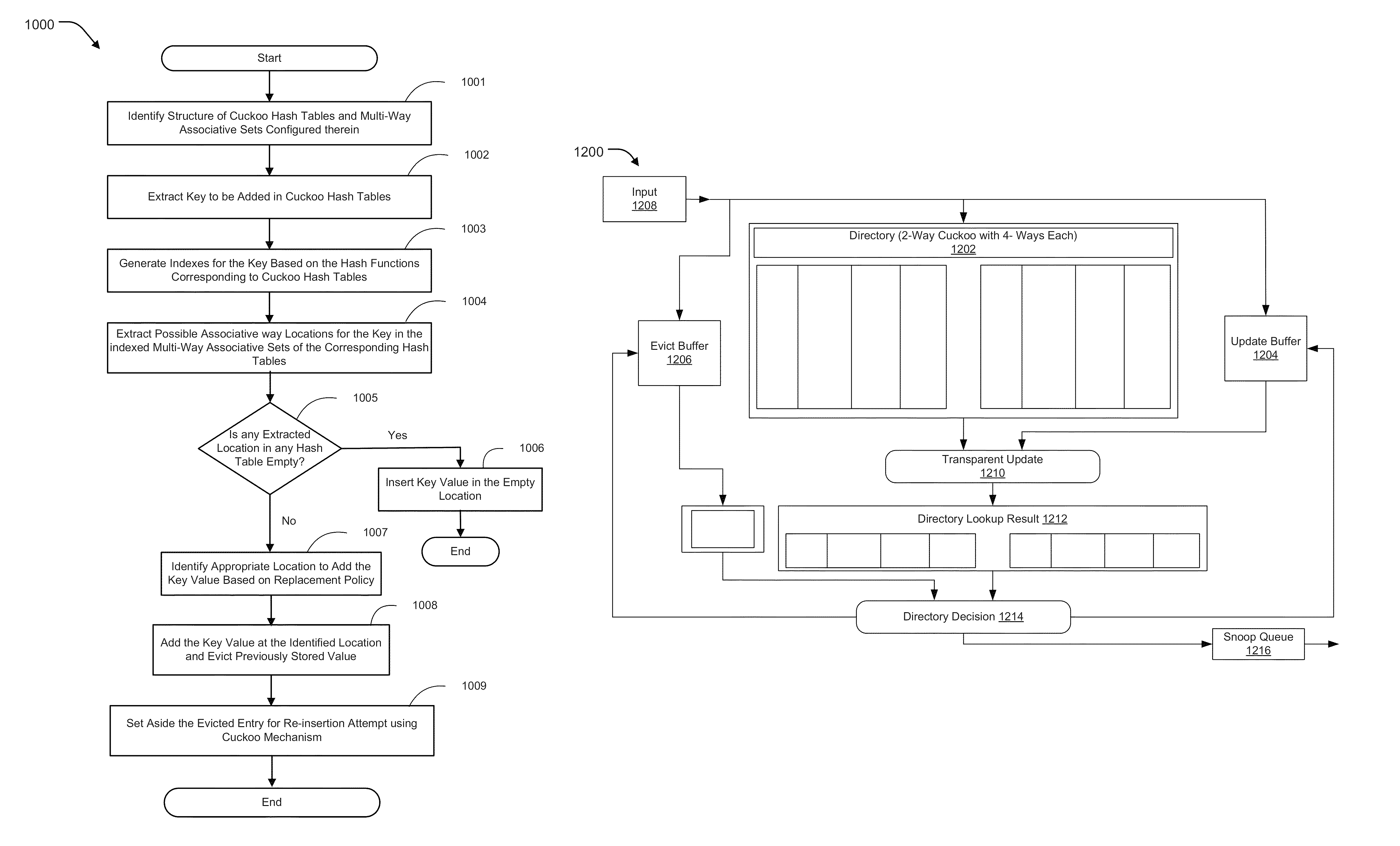
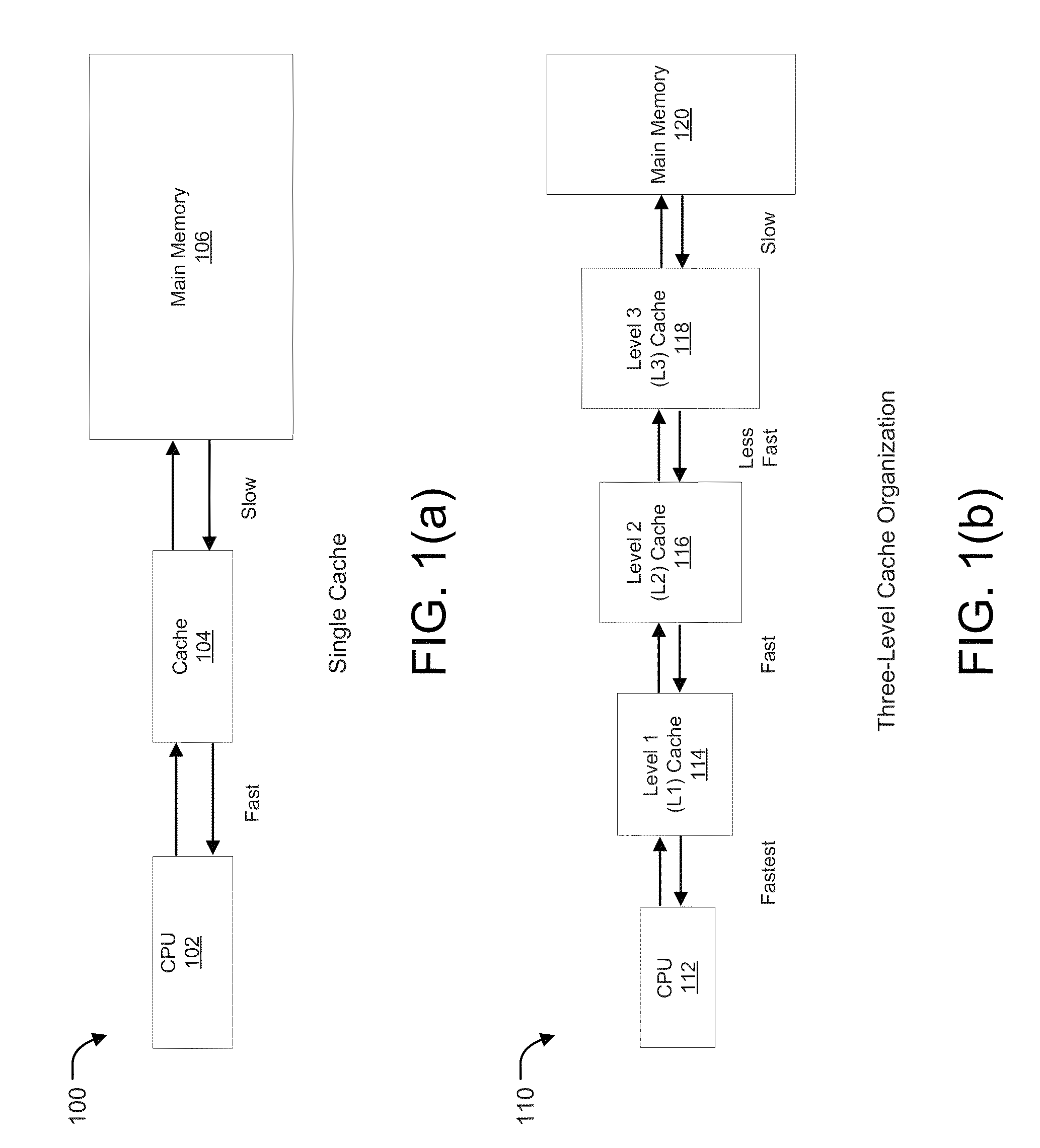
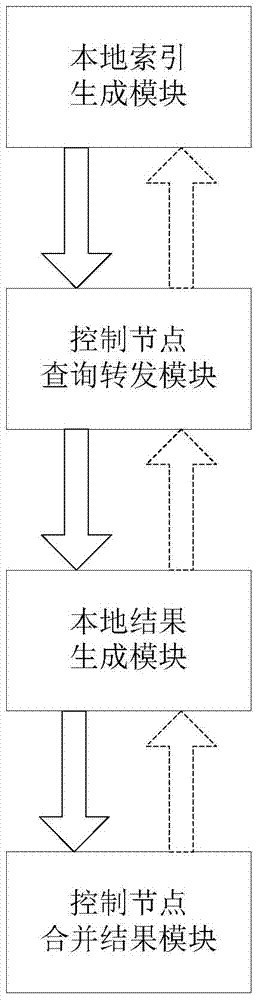
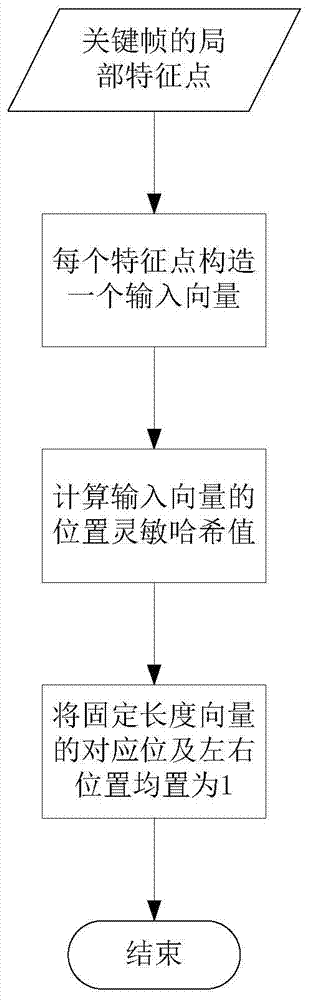
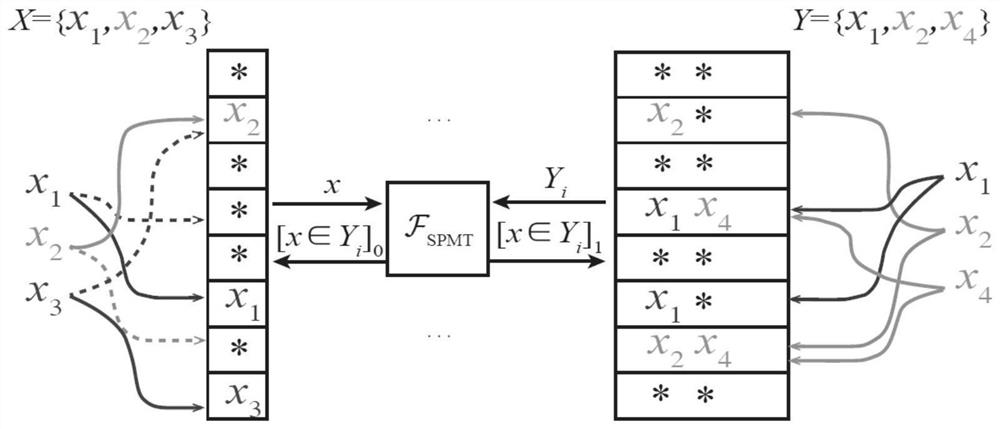
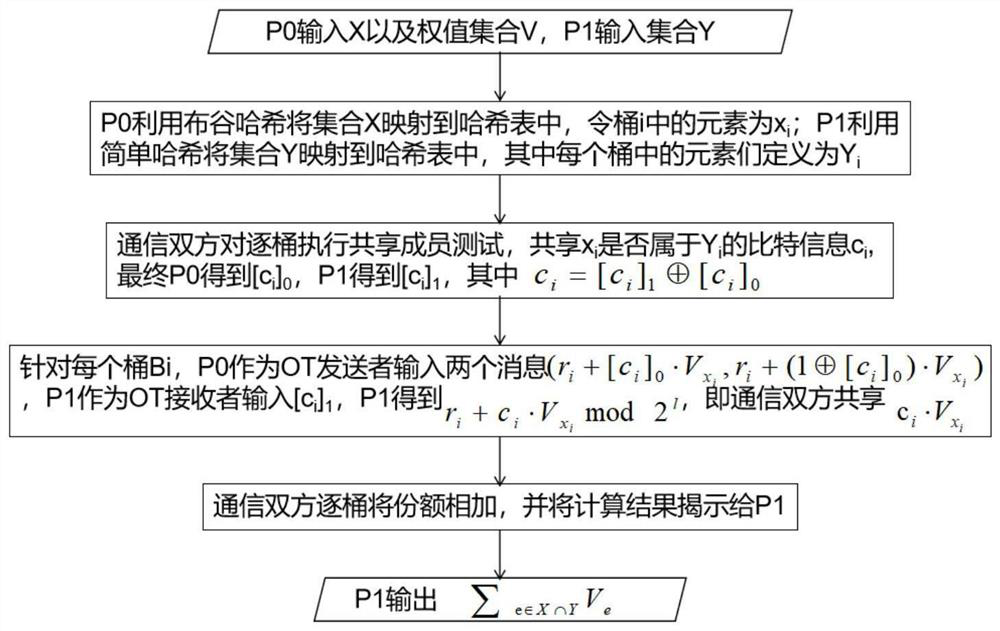
Patents
Literature
40 results about "Cuckoo hashing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
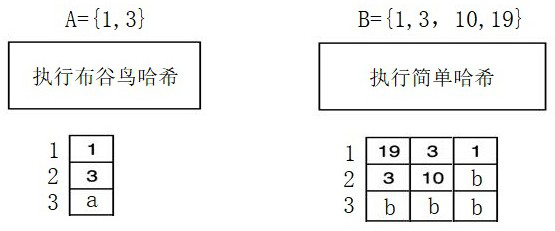
Cuckoo hashing is a scheme in computer programming for resolving hash collisions of values of hash functions in a table, with worst-case constant lookup time. The name derives from the behavior of some species of cuckoo, where the cuckoo chick pushes the other eggs or young out of the nest when it hatches; analogously, inserting a new key into a cuckoo hashing table may push an older key to a different location in the table.
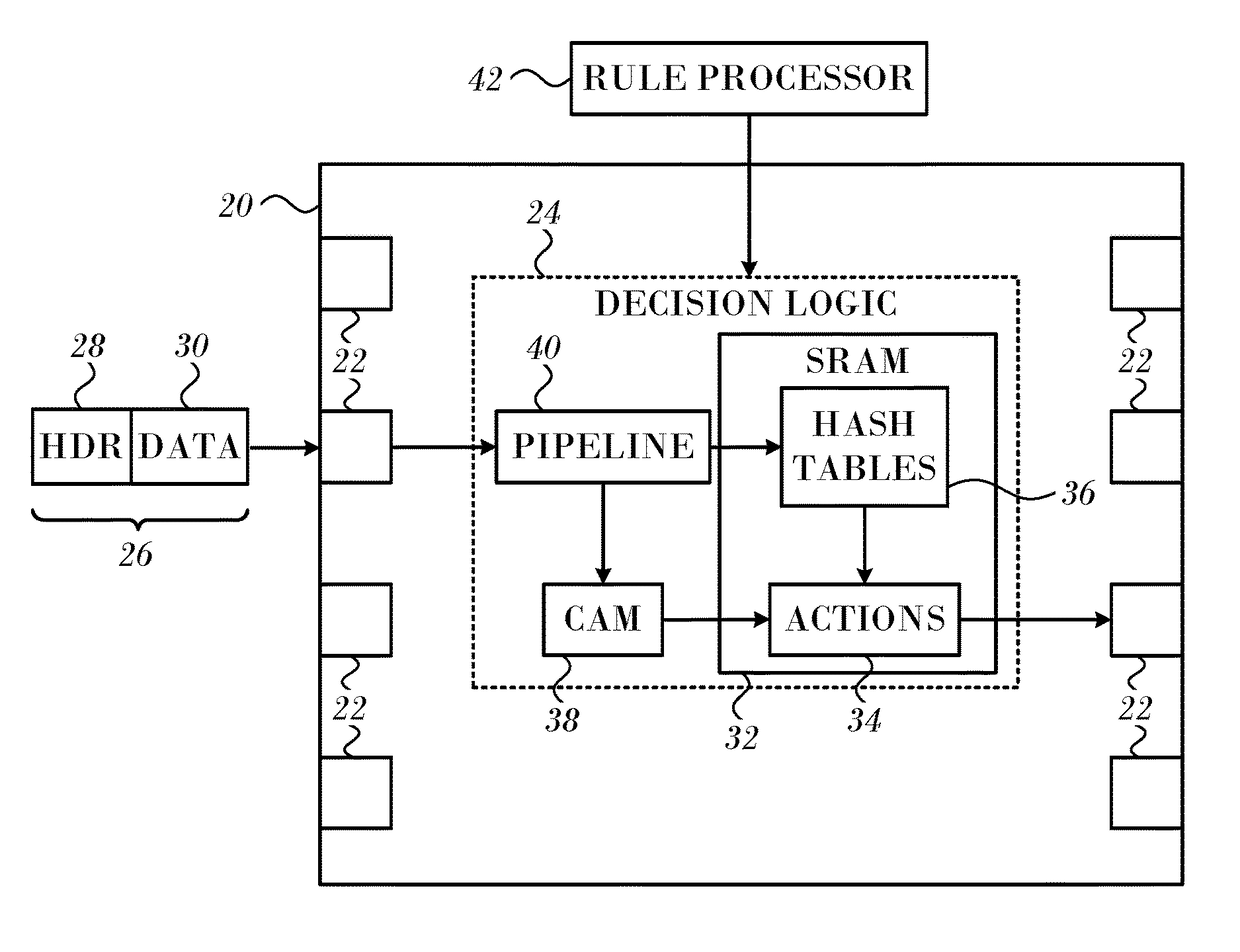
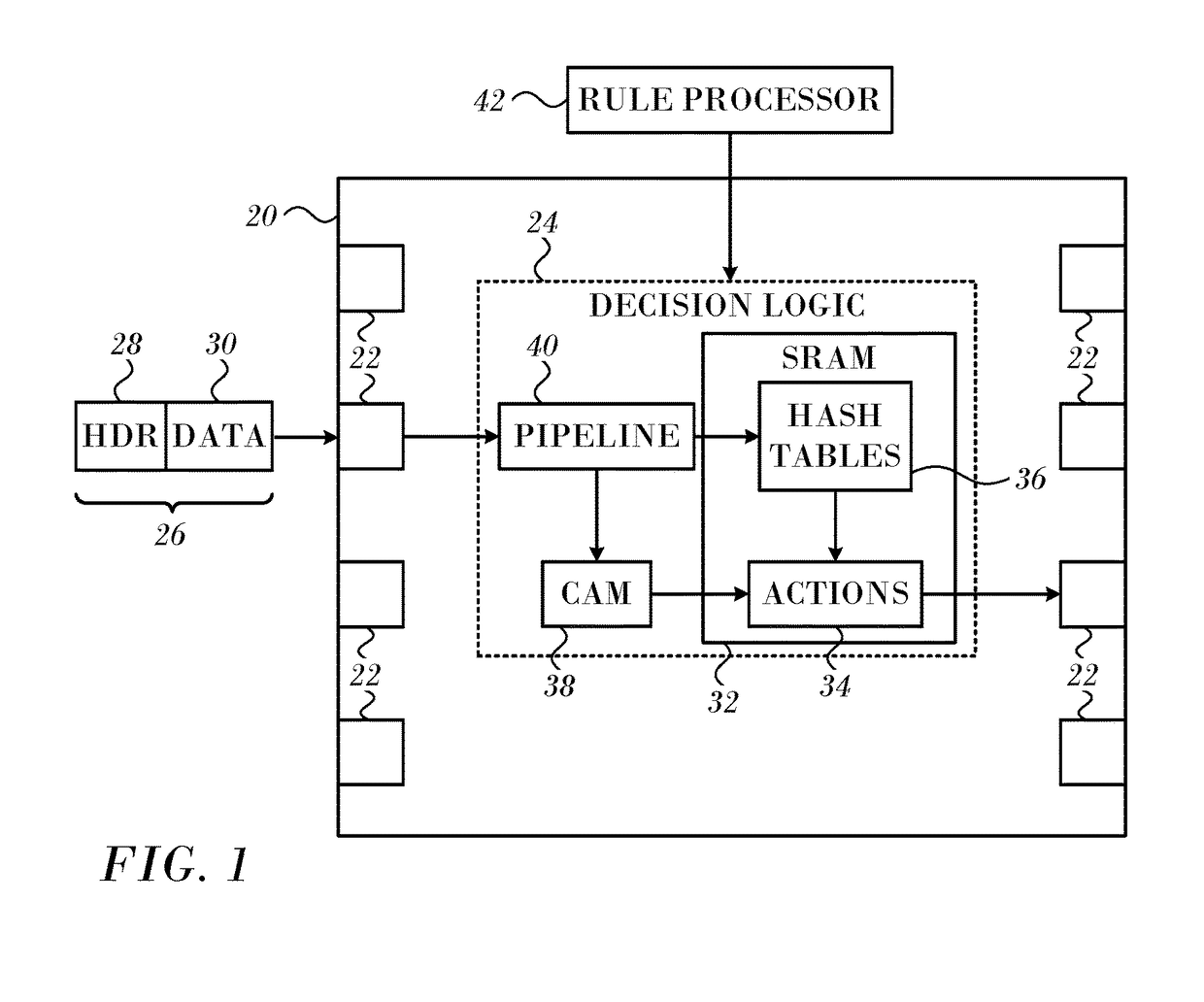
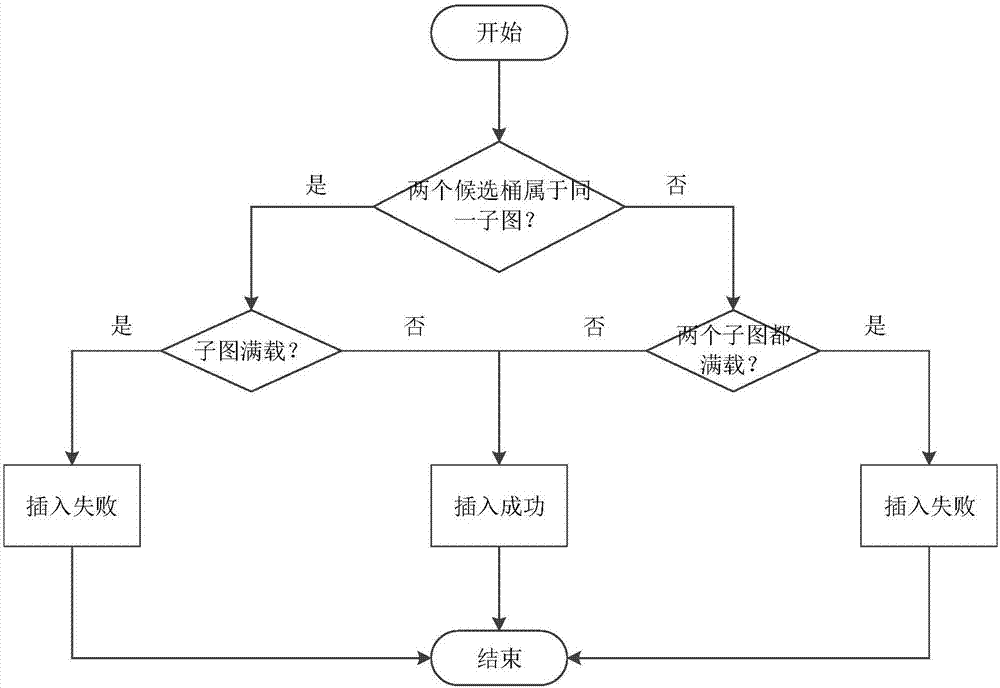
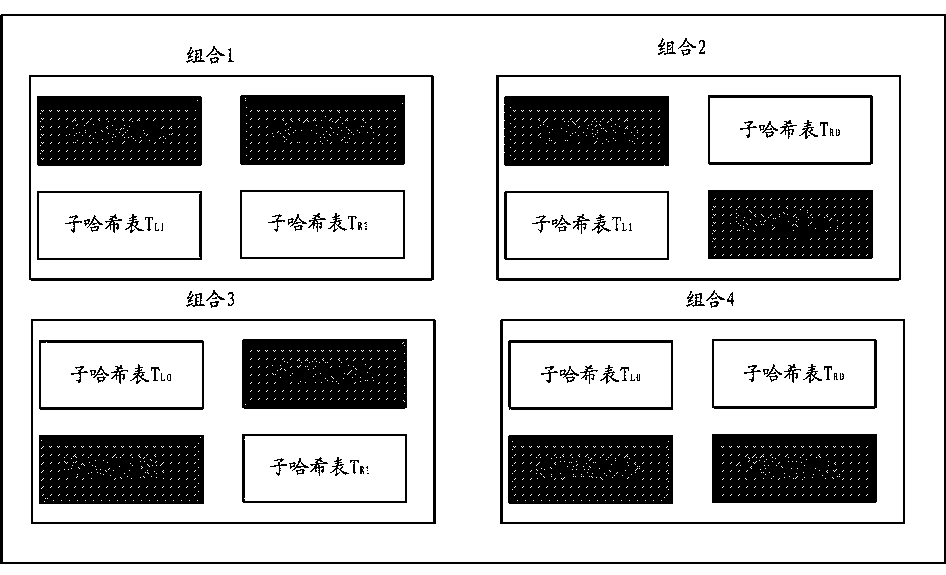
Set-associative hash table organization for efficient storage and retrieval of data in a storage system
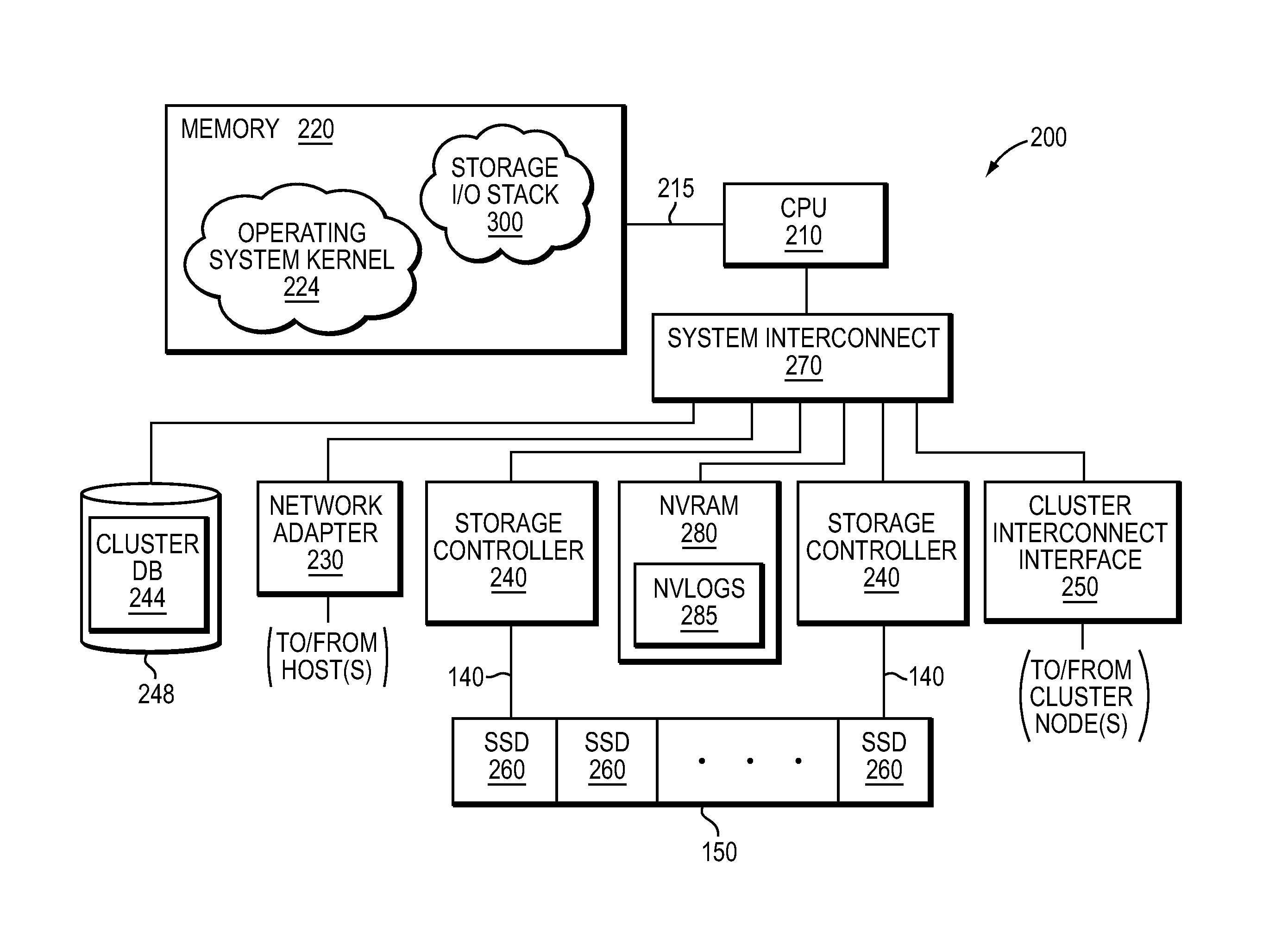
ActiveUS8874842B1Memory architecture accessing/allocationInput/output to record carriersFile systemSolid-state drive
In one embodiment, use of hashing in a file system metadata arrangement reduces an amount of metadata stored in a memory of a node in a cluster and reduces the amount of metadata needed to process an input / output (I / O) request at the node. Illustratively, cuckoo hashing may be modified and applied to construct the file system metadata arrangement. The file system metadata arrangement may be illustratively configured as a key-value extent store embodied as a data structure, e.g., a cuckoo hash table, wherein a value, such as a hash table index, may be configured as an index and applied to the cuckoo hash table to obtain a key, such as an extent key, configured to reference a location of an extent on one or more storage devices, such as solid state drives.
Owner:NETWORK APPLIANCE INC
Combining associativity and cuckoo hashing
ActiveUS20150052309A1Improve performanceEfficient designMemory adressing/allocation/relocationParallel computingConsistency control
Addition, search, and performance of other allied activities relating to keys are performed in a hardware hash table. Further, high performance and efficient design may be provided for a hash table applicable to CPU caches and cache coherence directories. Set-associative tables and cuckoo hashing are combined for construction of a directory table of a directory based cache coherence controller. A method may allow configuration of C cuckoo ways, where C is an integer greater than or equal to 2, wherein each cuckoo way Ci is a set-associative table with N sets, where each set has an associativity of A, where A is an integer greater than or equal to 2.
Owner:INTEL CORP
Combining associativity and cuckoo hashing
ActiveUS9223711B2Improve performanceEfficient designMemory adressing/allocation/relocationParallel computingConsistency control
Addition, search, and performance of other allied activities relating to keys are performed in a hardware hash table. Further, high performance and efficient design may be provided for a hash table applicable to CPU caches and cache coherence directories. Set-associative tables and cuckoo hashing are combined for construction of a directory table of a directory based cache coherence controller. A method may allow configuration of C cuckoo ways, where C is an integer greater than or equal to 2, wherein each cuckoo way Ci is a set-associative table with N sets, where each set has an associativity of A, where A is an integer greater than or equal to 2.
Owner:INTEL CORP
Mechanism to support multiple-writer/multiple-reader concurrency for software flow/packet classification on general purpose multi-core systems
Owner:INTEL CORP
Composite index method and device
ActiveCN104536958AReduce space overheadAvoid calculationRelational databasesSpecial data processing applicationsData streamAlgorithm
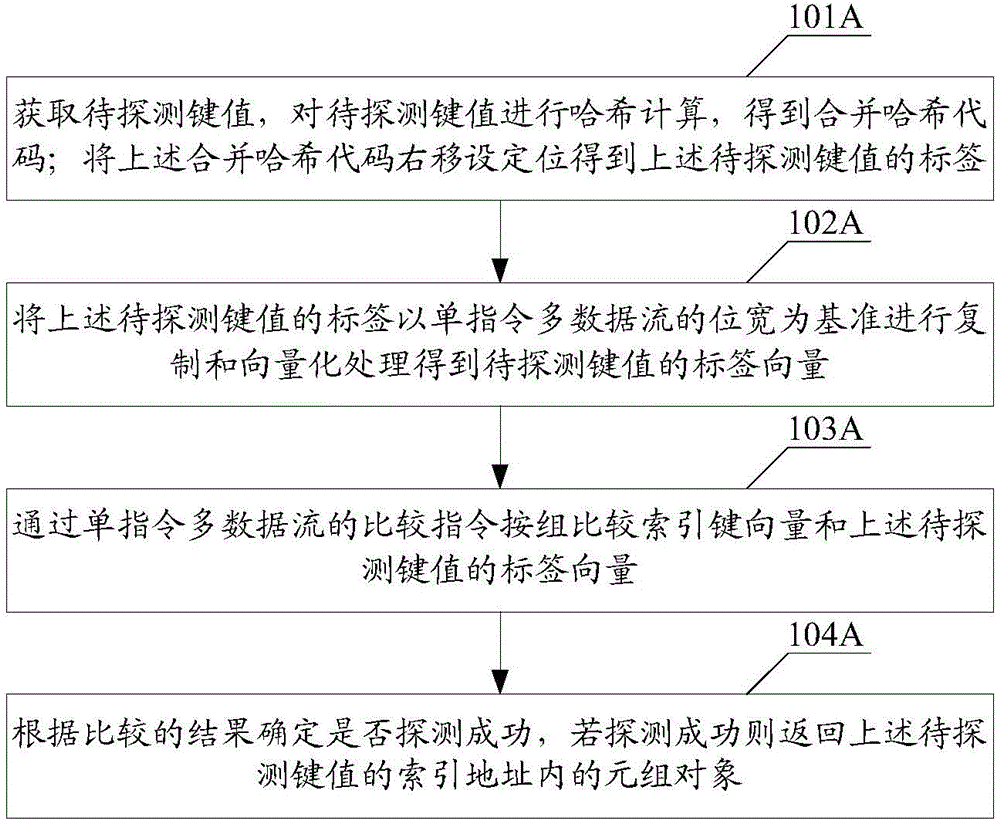
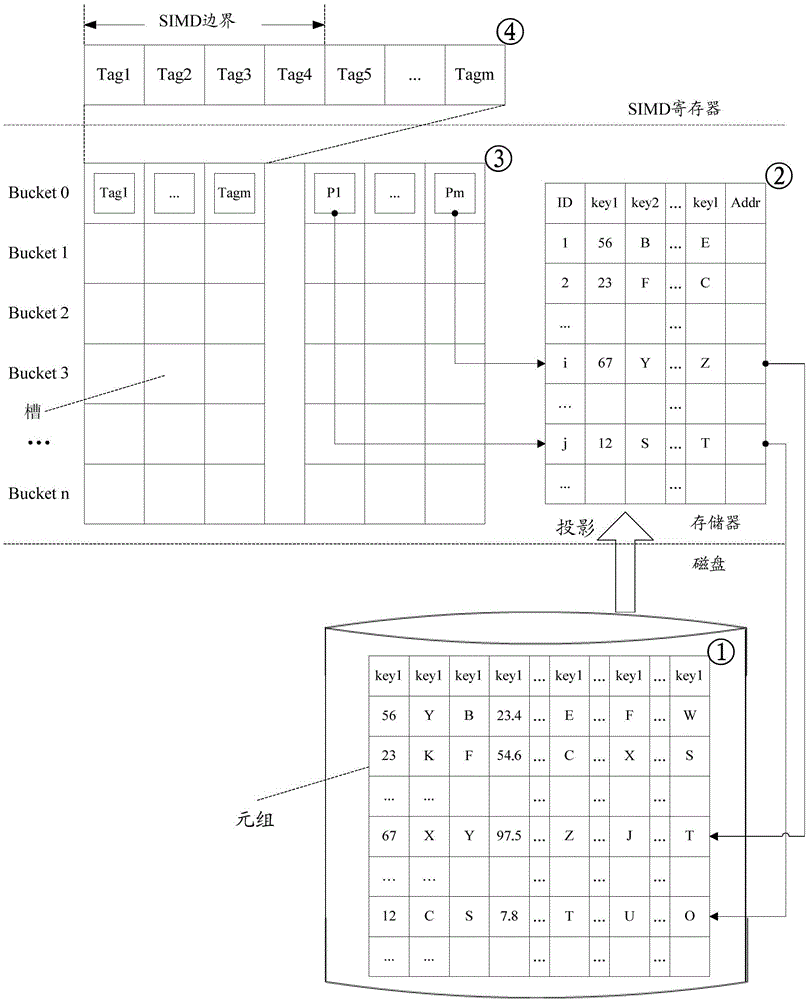
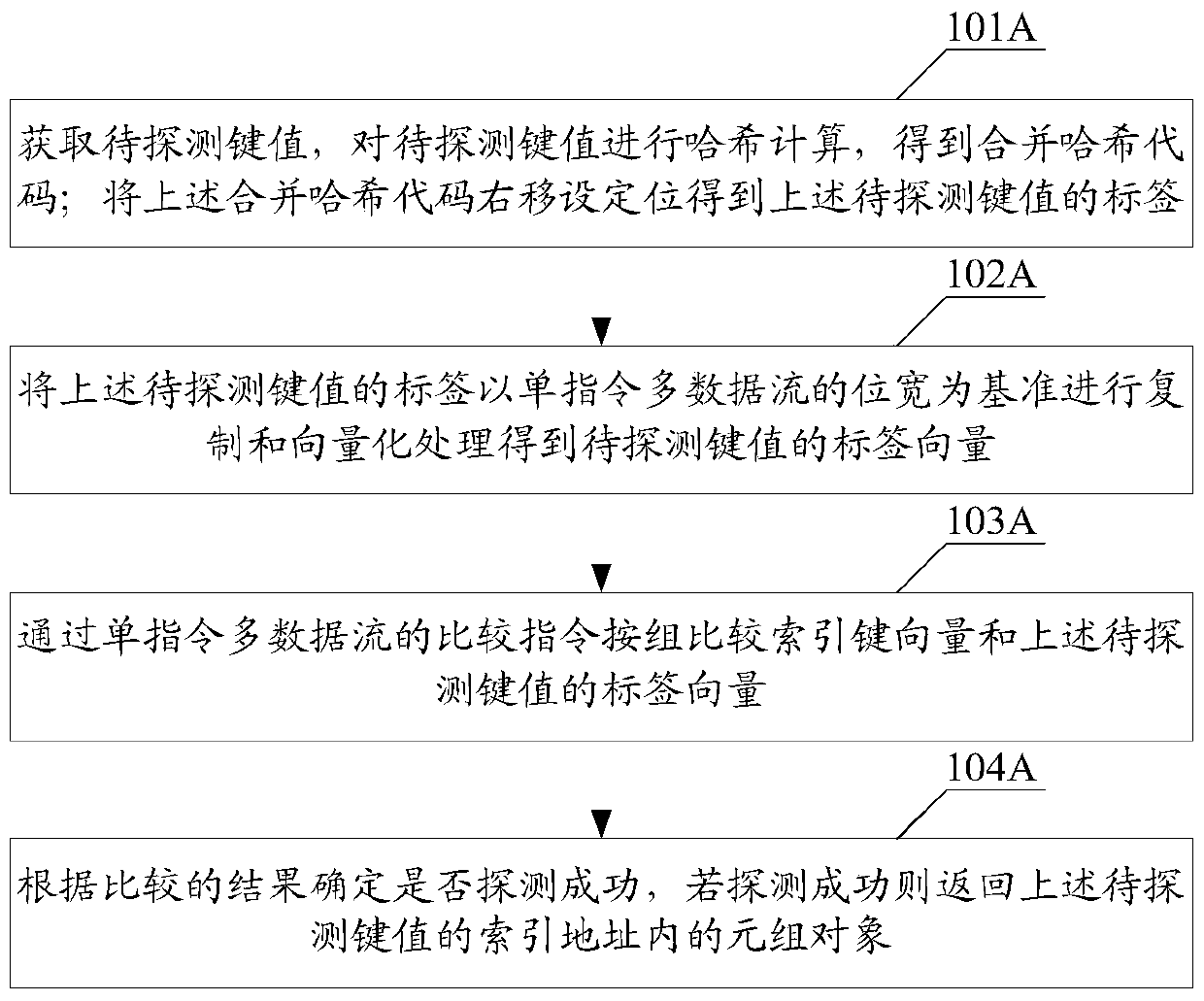
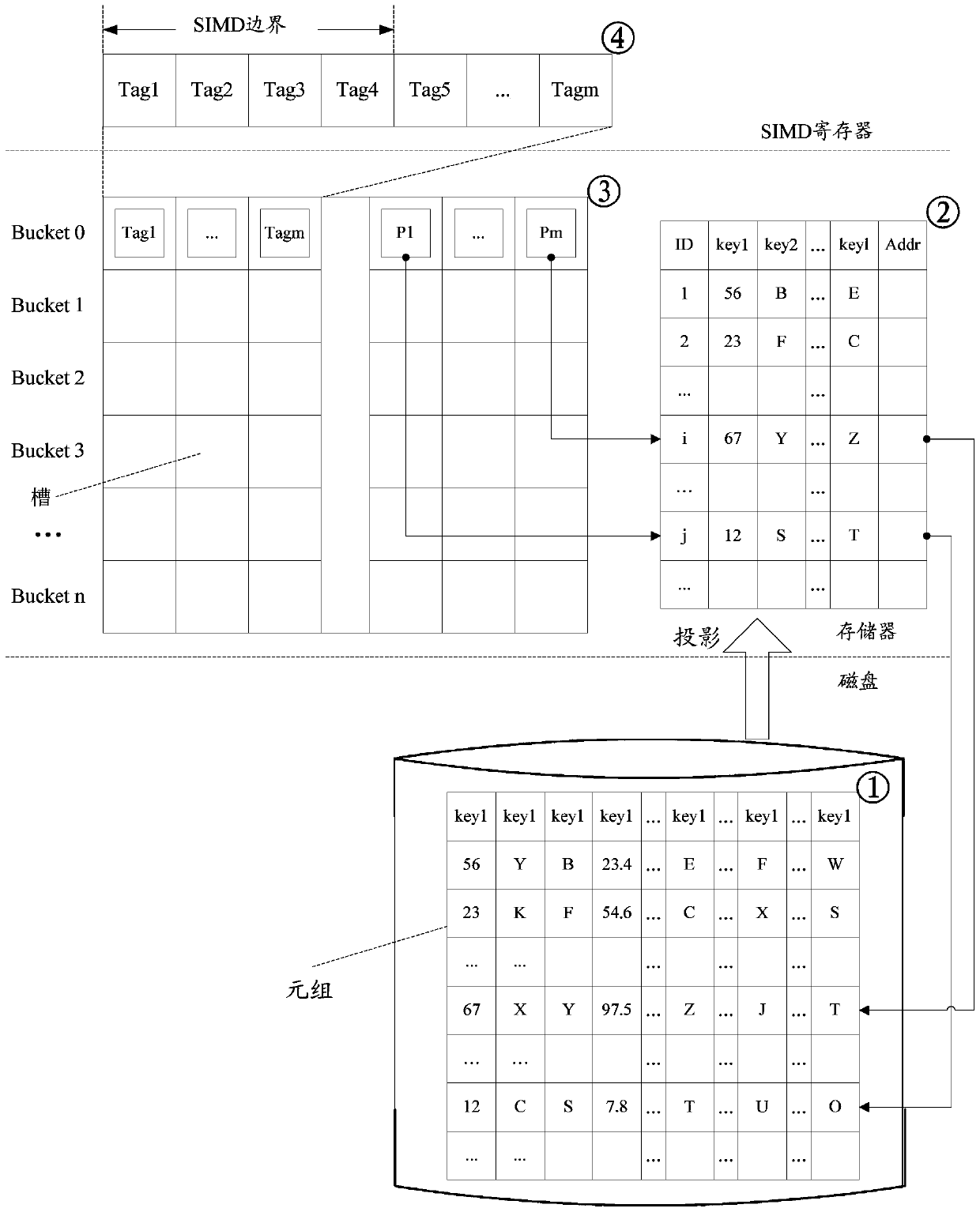
An embodiment of the invention discloses a composite index method and a device. The method is implemented by the following steps of obtaining to-be-detected keys and carrying out Hash computation on the to-be-detected keys to obtain combined Hash codes; moving the combined Hash codes a set bit to the right to obtain labels of the to-be-detected keys; carrying out copy and vectorization processing on the labels of the to-be-detected keys with a bit wide of single-instruction multiple-data stream as reference so as to obtain label vectors of the to-be-detected keys; comparing index key vectors with the label vectors of the to-be-detected keys by group through a comparison order of the single-instruction multiple-data stream; and determining whether detection is successful according to the comparison result, and returning tuple objects in index addresses of the to-be-detected keys if detection is successful. A plurality of data items can be compared at each time through parallel detection based on SIMD (Single Instruction Multiple Data), so that the performance cost brought by searching loop is reduced and multiple computations of a Hash function are avoided; the labels of the to-be-detected keys belong to Cuckoo Hashing of partial keys and can be used for reducing the space cost of a Hash table.
Owner:HUAWEI TECH CO LTD
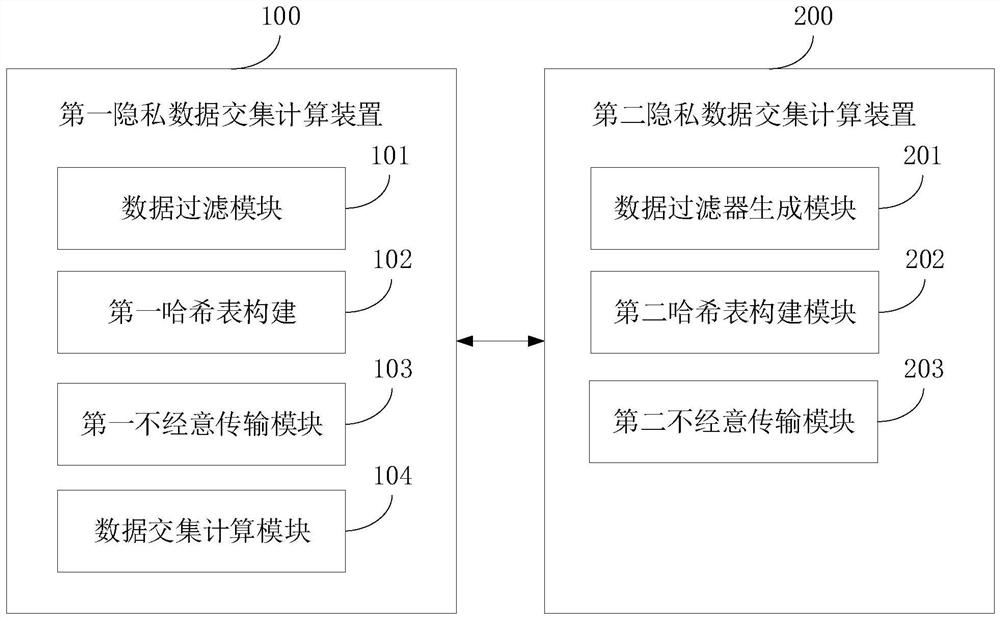
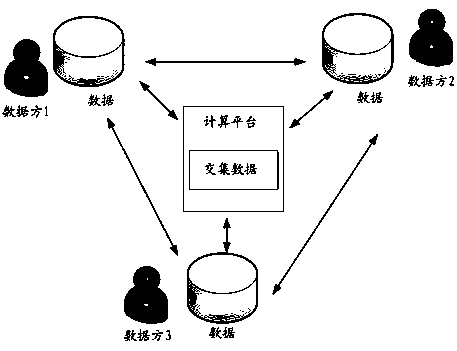
Private data intersection calculation method and device, equipment and storage medium
PendingCN113343305AReduce processingIncrease the rate of intersection calculationsDigital data protectionSpecial data processing applicationsTheoretical computer scienceEngineering
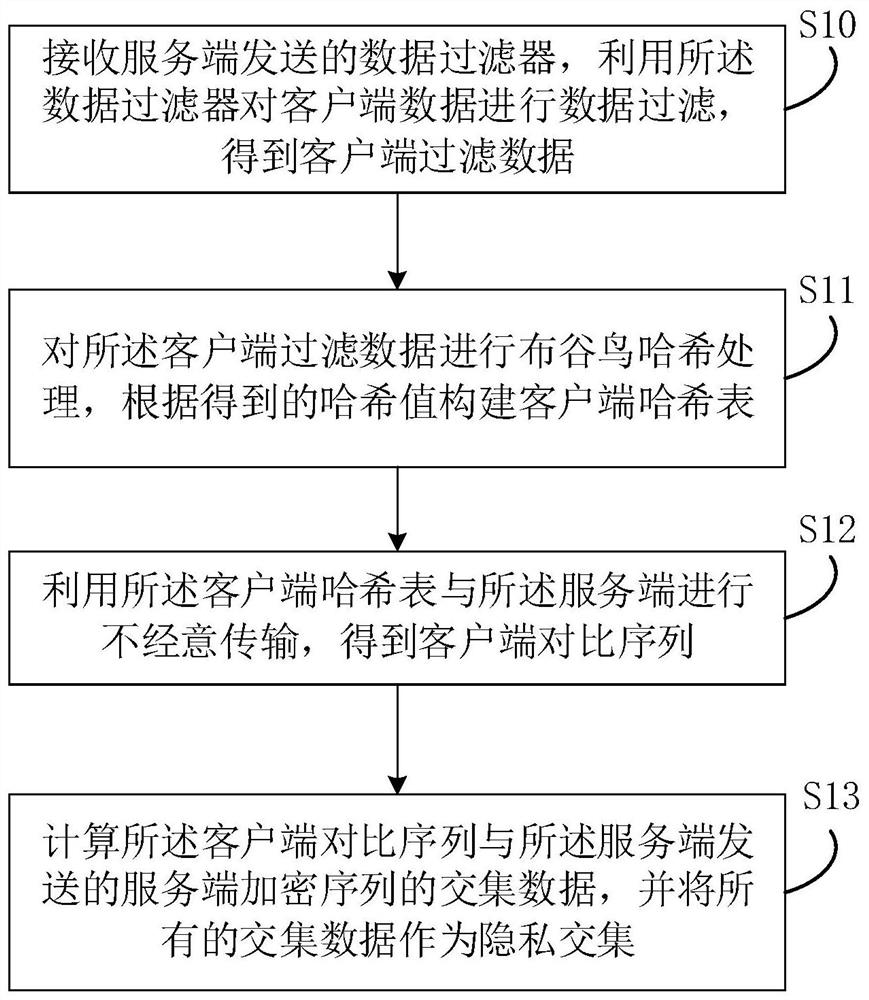
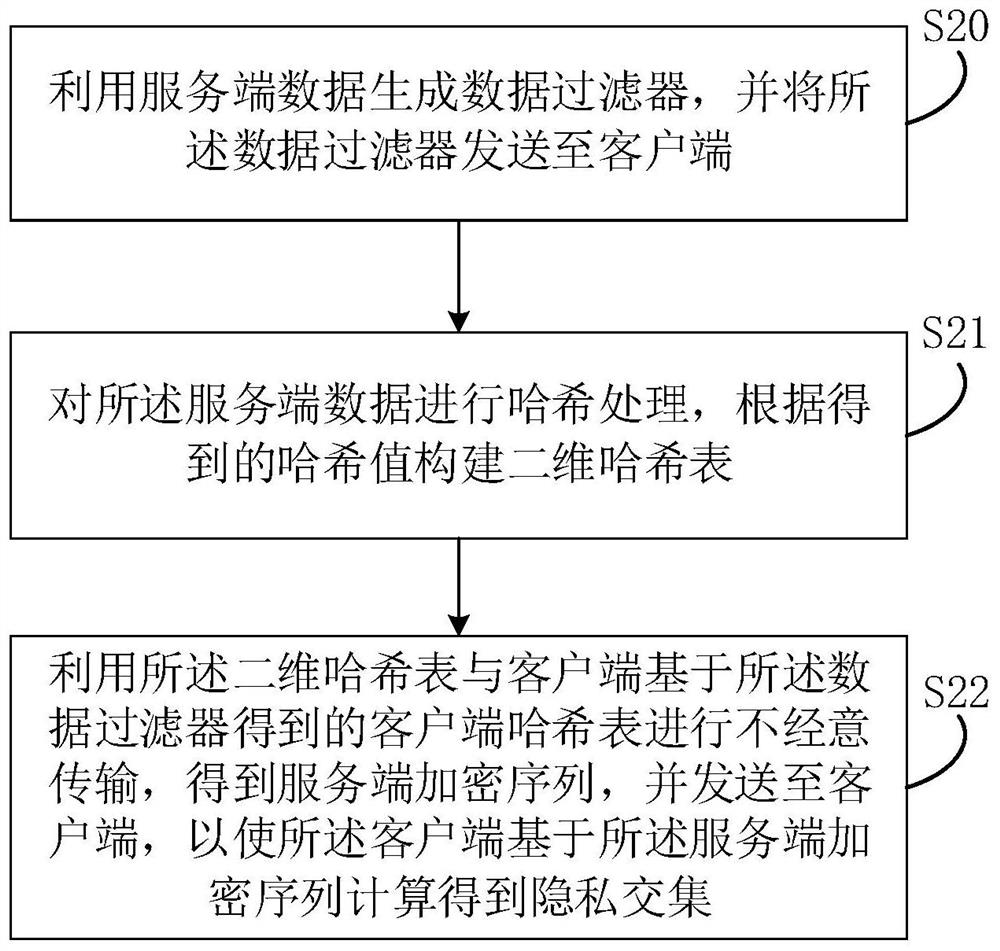
The invention relates to the technical field of security, and discloses an intersection calculation method for private data, which is applied to a client and comprises the following steps: receiving a data filter sent by a server, filtering client data by using the data filter to obtain client filtered data, performing cuckoo hash processing on the client filtered data, constructing a client hash table according to the obtained hash value, performing casual transmission with the server by using the client hash table to obtain a client comparison sequence, calculating intersection data of the client comparison sequence and a server encrypted sequence sent by the server, and taking all the intersection data as a privacy intersection. The invention further provides a private data intersection calculation device, electronic equipment and a computer readable storage medium. According to the invention, the problem of low efficiency of data intersection calculation can be solved.
Owner:招商局金融科技有限公司
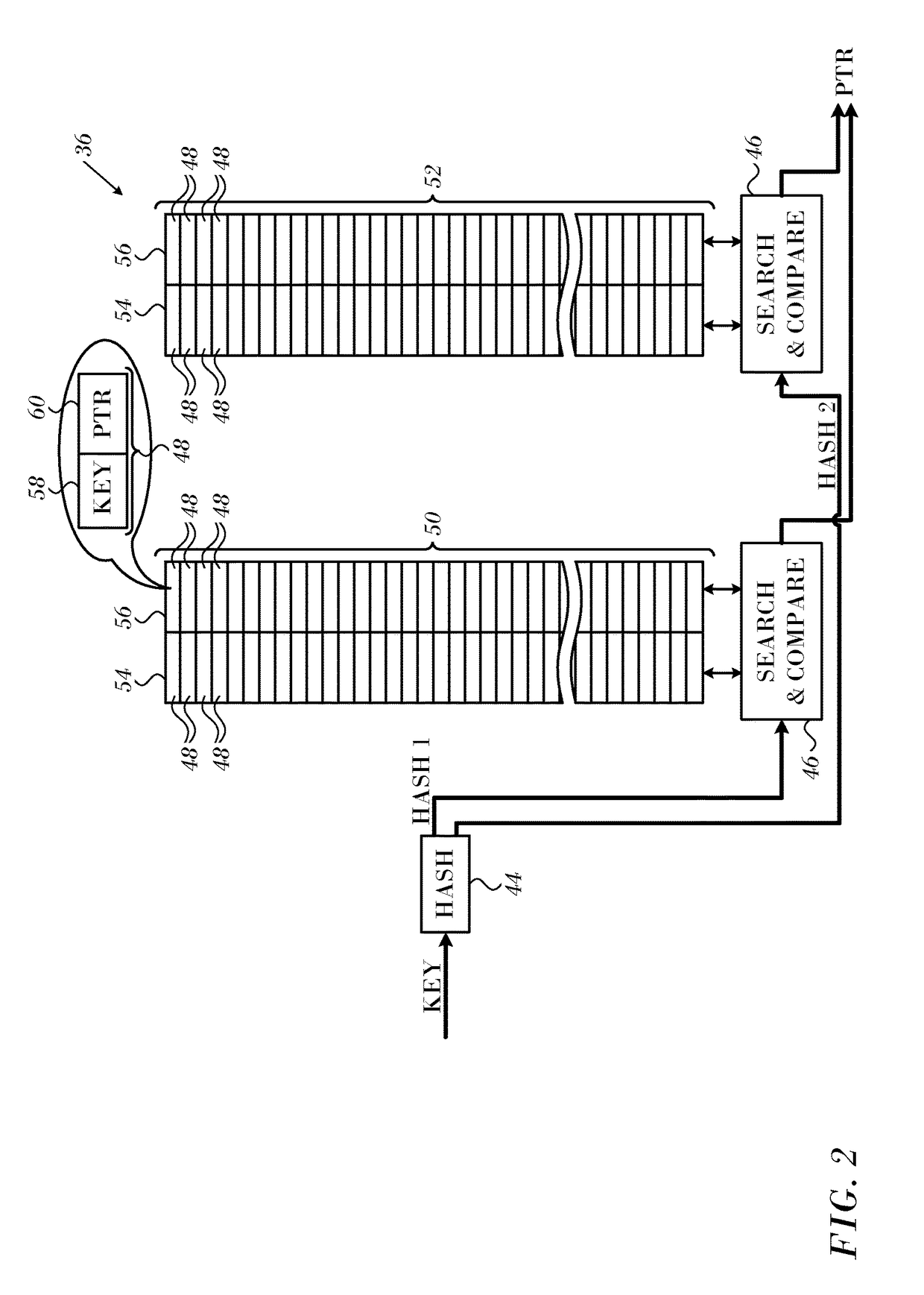
Single Double Cuckoo Hash
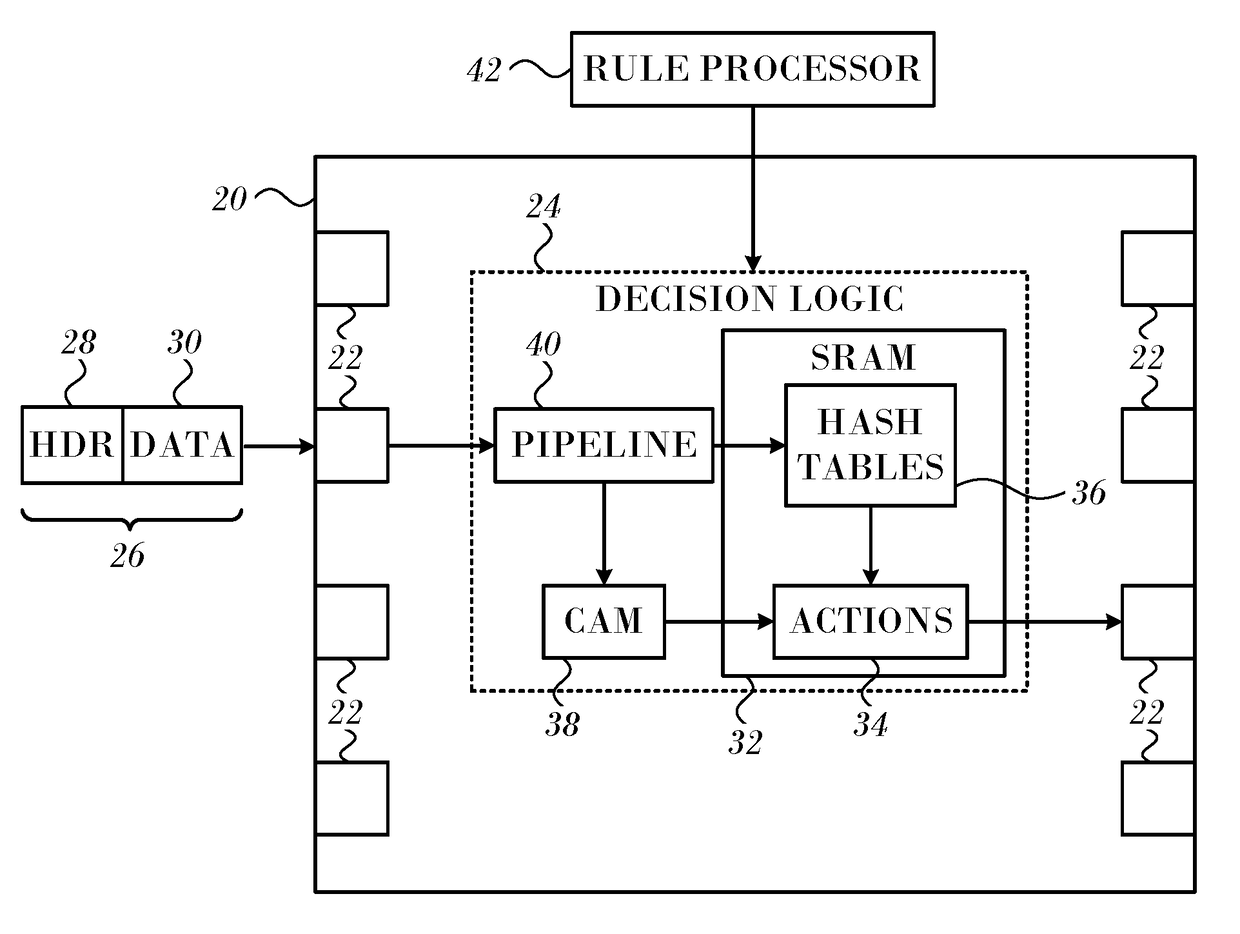
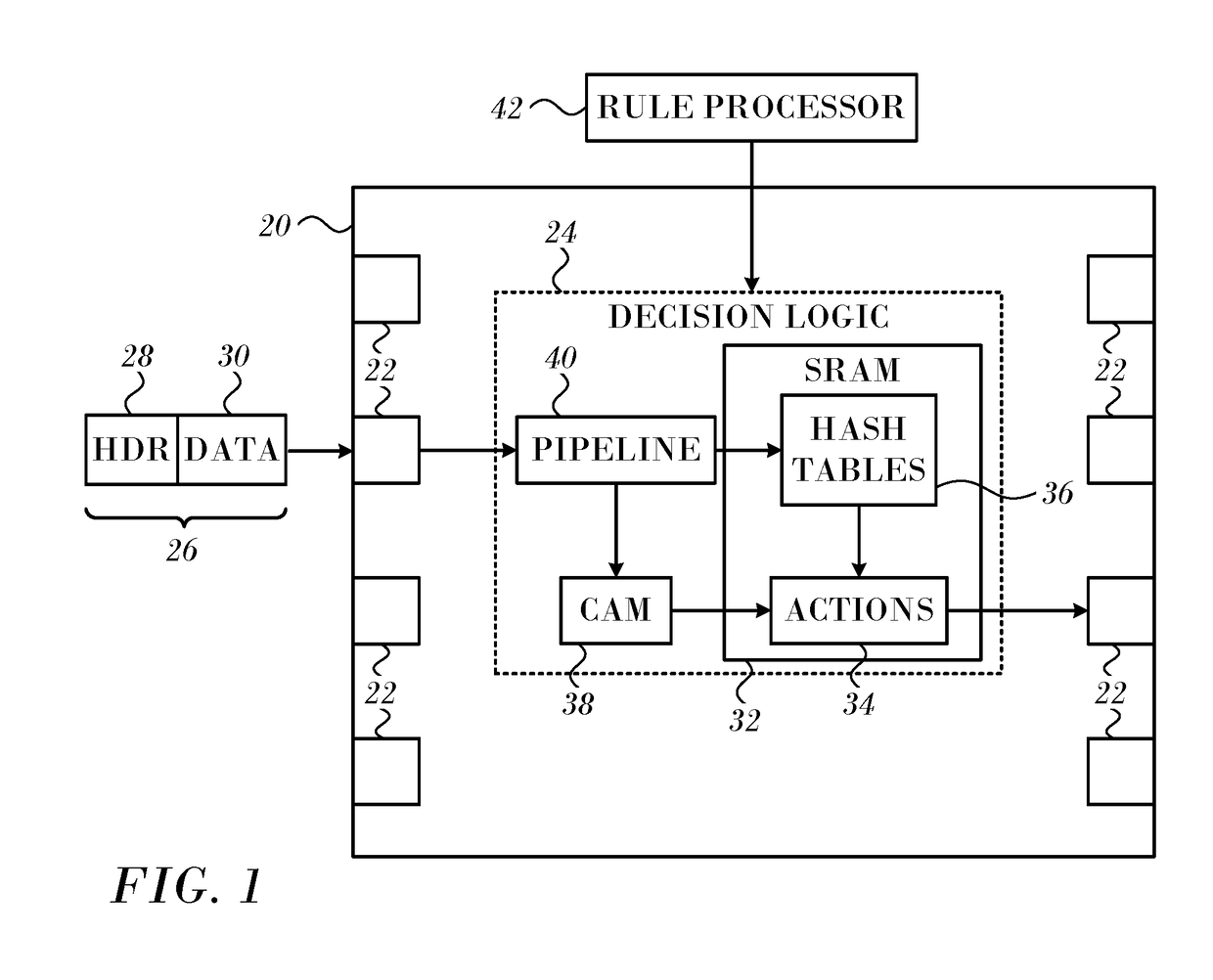
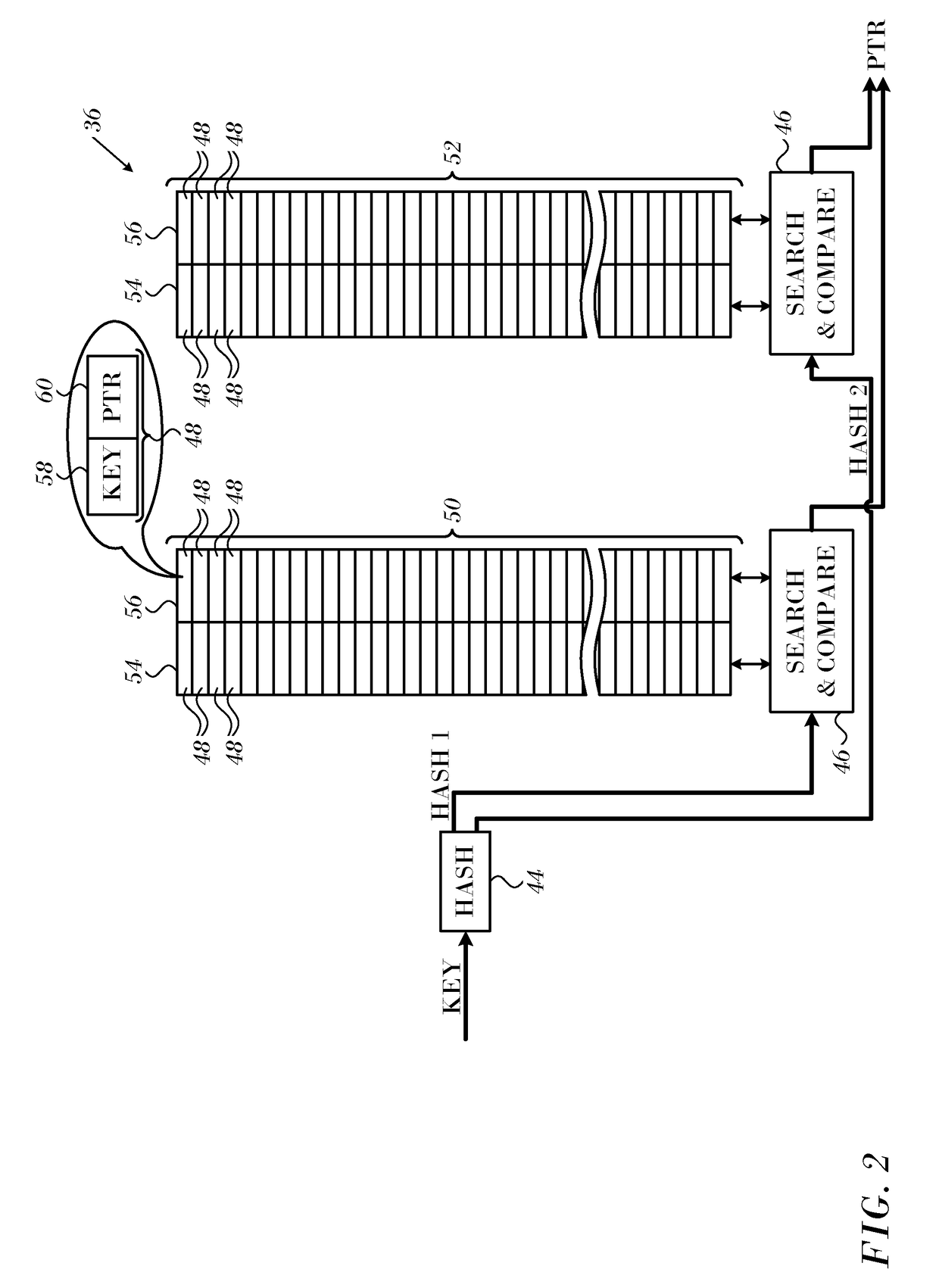
ActiveUS20170286292A1Memory architecture accessing/allocationDigital data information retrievalTheoretical computer scienceHash table
In a network element a decision apparatus has a plurality of multi-way hash tables of single size and double size associative entries. A logic pipeline extracts a search key from each of a sequence of received data items. A hash circuit applies first and second hash functions to the search key to generate first and second indices. A lookup circuit reads associative entries in the hash tables that are indicated respectively by the first and second indices, matches the search key against the associative entries in all the ways. Upon finding a match between the search key and an entry key in an indicated associative entry. A processor uses the value of the indicated associative entry to insert associative entries from a stash of associative entries into the hash tables in accordance with a single size and a double size cuckoo insertion procedure.
Owner:MELLANOX TECHNOLOGIES LTD
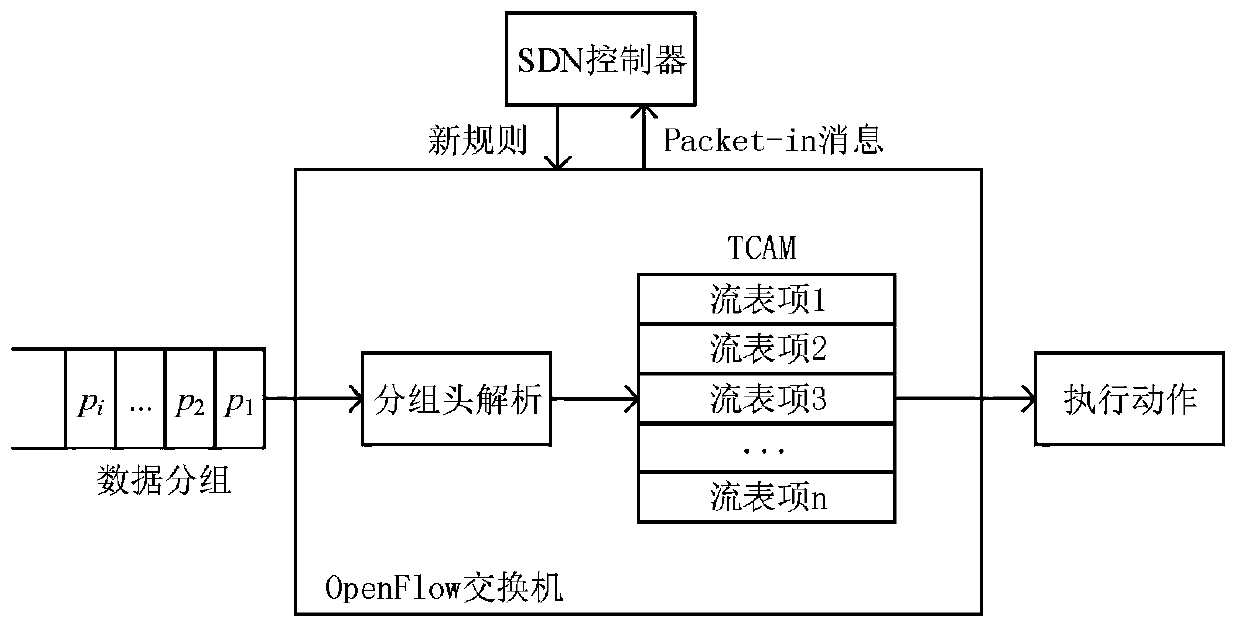
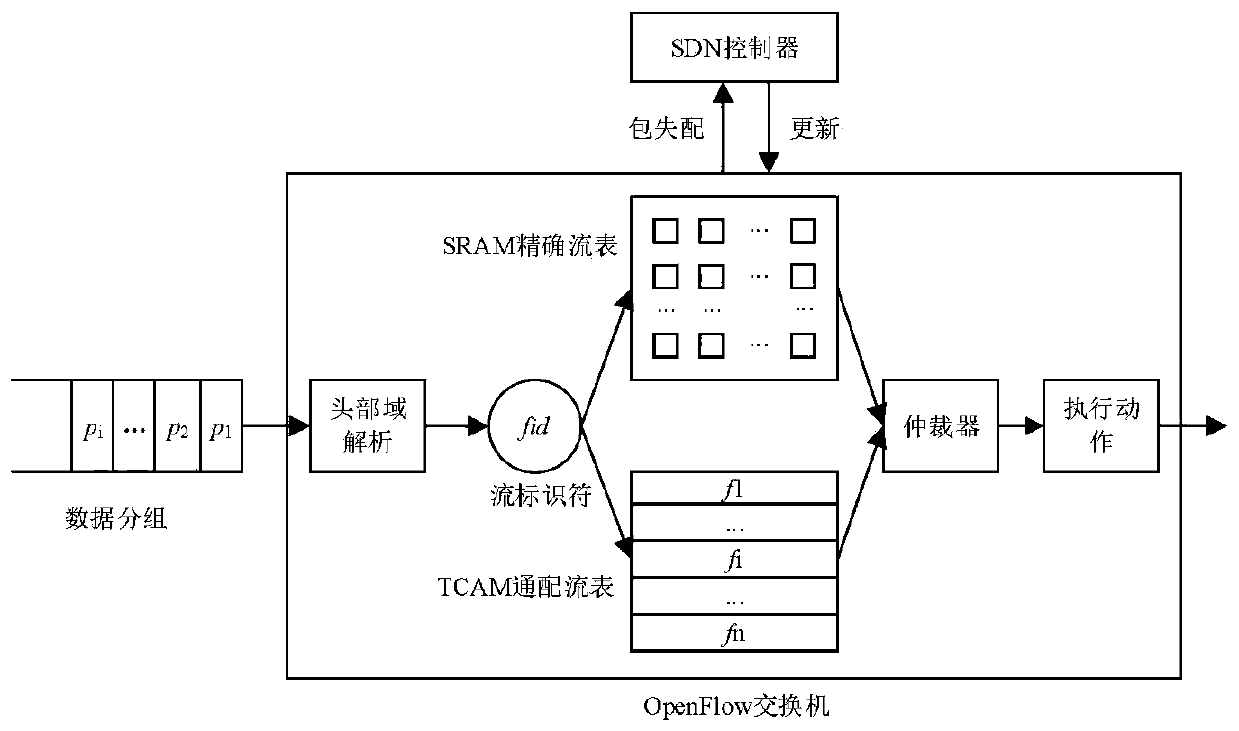
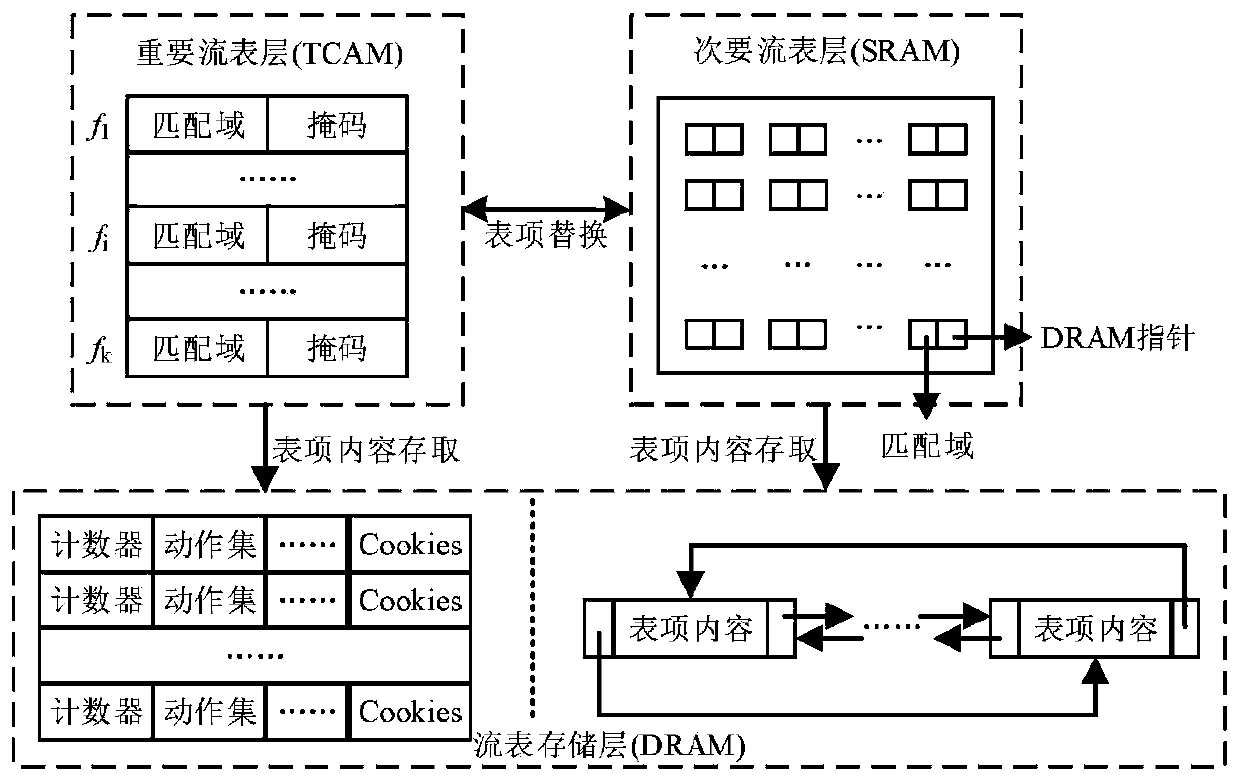
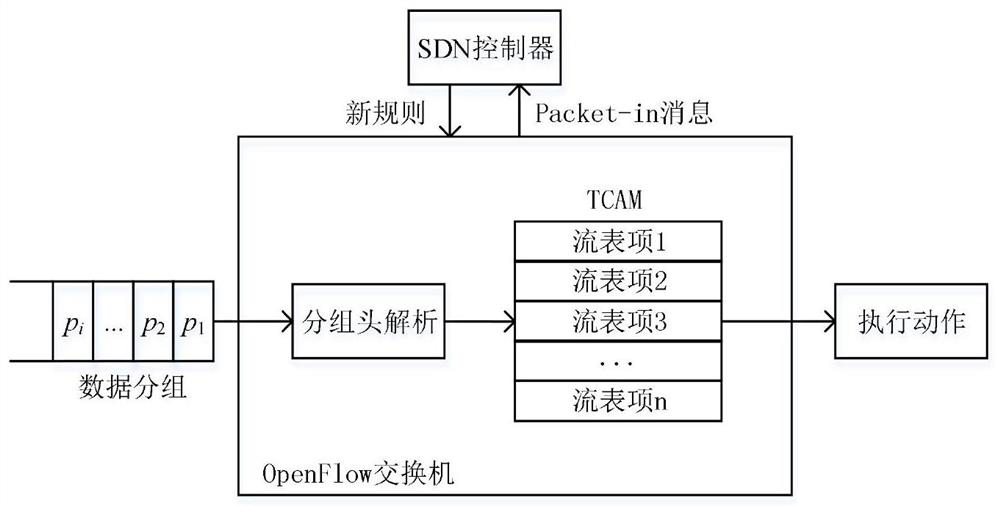
OpenFlow flow table energy-saving storage architecture supporting QoS (Quality of Service) and application thereof
ActiveCN110808910AGuaranteed service qualityGuaranteed flow table lookup performanceData switching networksQos quality of serviceEngineering
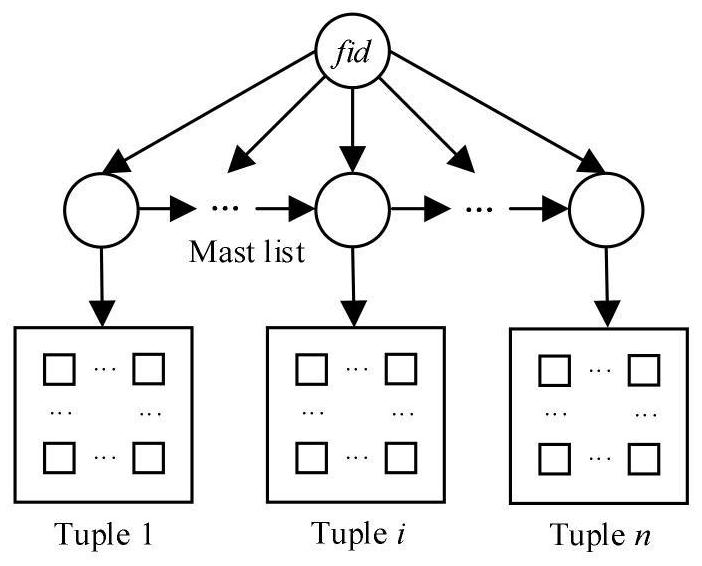
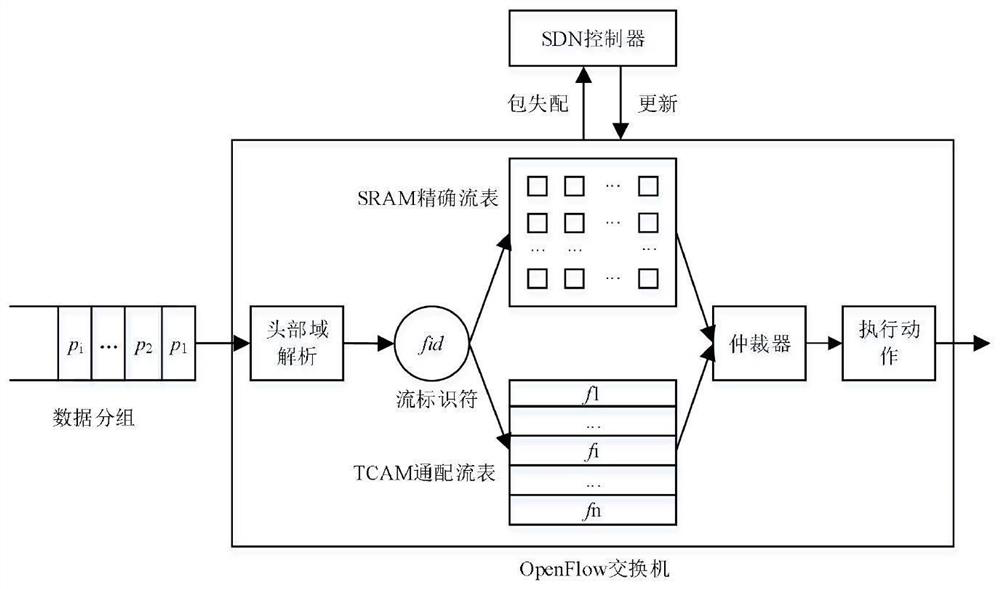
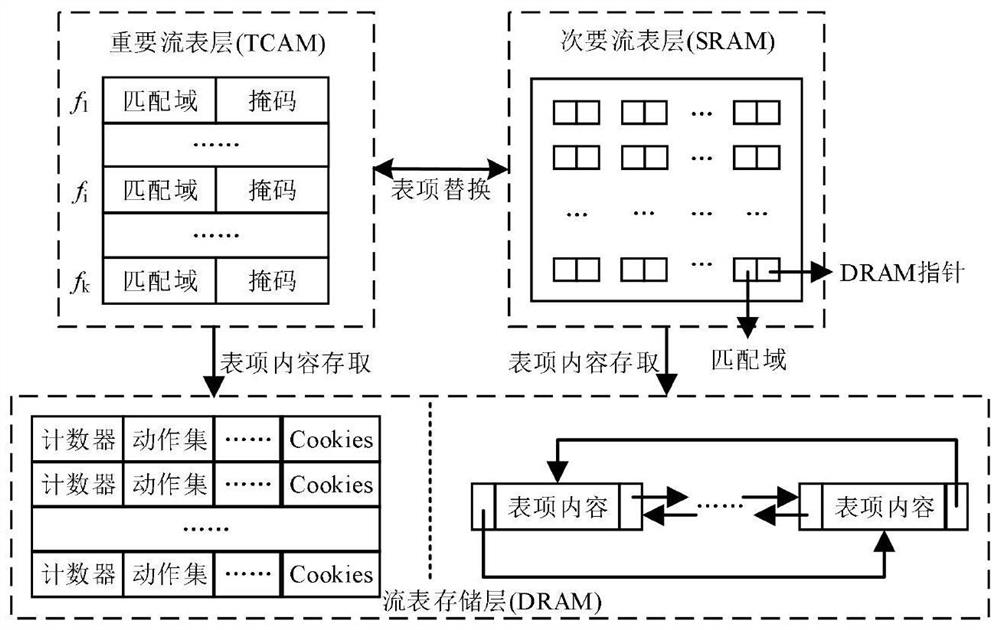
The invention provides an OpenFlow flow table energy-saving storage architecture supporting QoS (Quality of Service) and application of the OpenFlow flow table energy-saving storage architecture. Thearchitecture comprises three layers, namely a priority flow / elephant flow layer, a mouse flow layer and an active connection cache layer, wherein the priority flow / elephant flow layer adopts a TCAM and a DRAM as storage media, the mouse flow layer adopts an SRAM and a DRAM as storage media, the active connection cache layer adopts an SRAM as a storage medium, and a Cuckoo hash structure is adoptedto cache a mapping relationship between active connection and flow table entries in the TCAM. According to the architecture, the TCAM is adopted to preferentially store the identification fields of the priority flow table entries, and quick flow table lookup of priority data packets is realized, so that the network service quality is guaranteed. Meanwhile, a Cuckoo cache is designed to dynamically store the current active connection and the corresponding TCAM flow entry index value in the elephant flow; the cache is hit by most of the data packets, and the corresponding flow table item is found according to the address of the hit cache item, so that a TCAM flow table lookup process is bypassed, and the flow table lookup energy consumption overhead is greatly reduced.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
Data packet forwarding method based on software table look-up
InactiveCN105099957ALow costHigh-speed packet capabilityData switching networksComputer hardwareWire speed
The invention relates to a data packet forwarding method based on software table look-up. The method is based on Intel DPDK, and adopts hardware to extract a data packet header, rapid data transmission software to transmit data in batch efficiently, and software to look up table flexibly so as to realize a data packet forwarding function of a switch. A table look-up algorithm realizes the effects of storing enough items and improving table look-up speed by combining a cuckoo hash table and an open addressing method. Network equipment is allowed to have the following characteristics of multiport wire-speed forwarding, flexible high-capacity table look-up and low cost. The method combines the high-speed packet forming capability of the hardware, the mass data packet processing and forwarding capability of the rapid data transmission software and the high-speed flexible look-up capability of the software; compared with the conventional hardware switch, the method has better extendibility and programmability; and compared with a conventional software switch, the method can provide larger throughput rate and smaller time delay.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
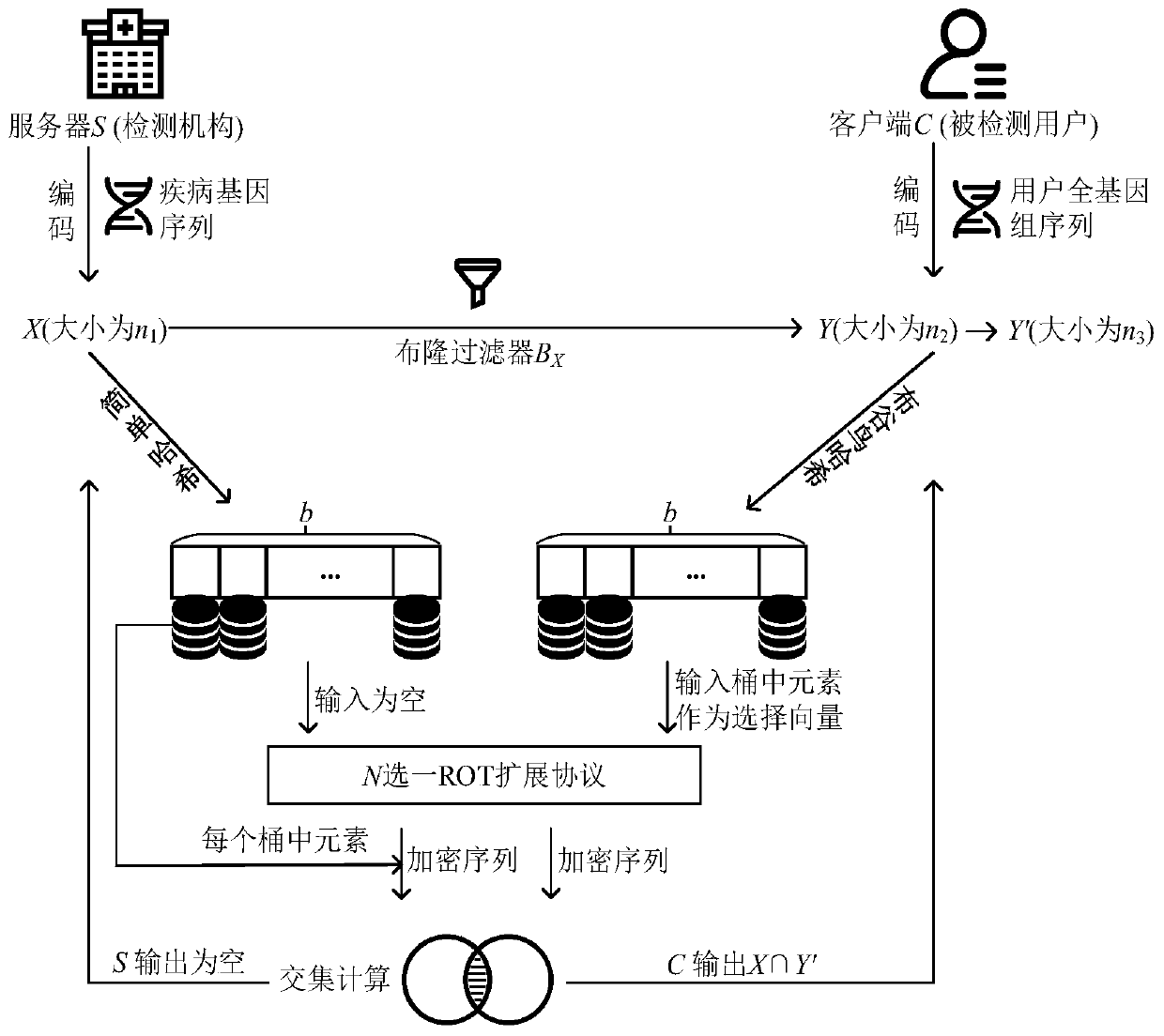
Pathogenic gene detection method based on privacy protection intersection calculation protocol
InactiveCN111125736AImprove performanceEnsure safetyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesTheoretical computer sciencePrivacy protection
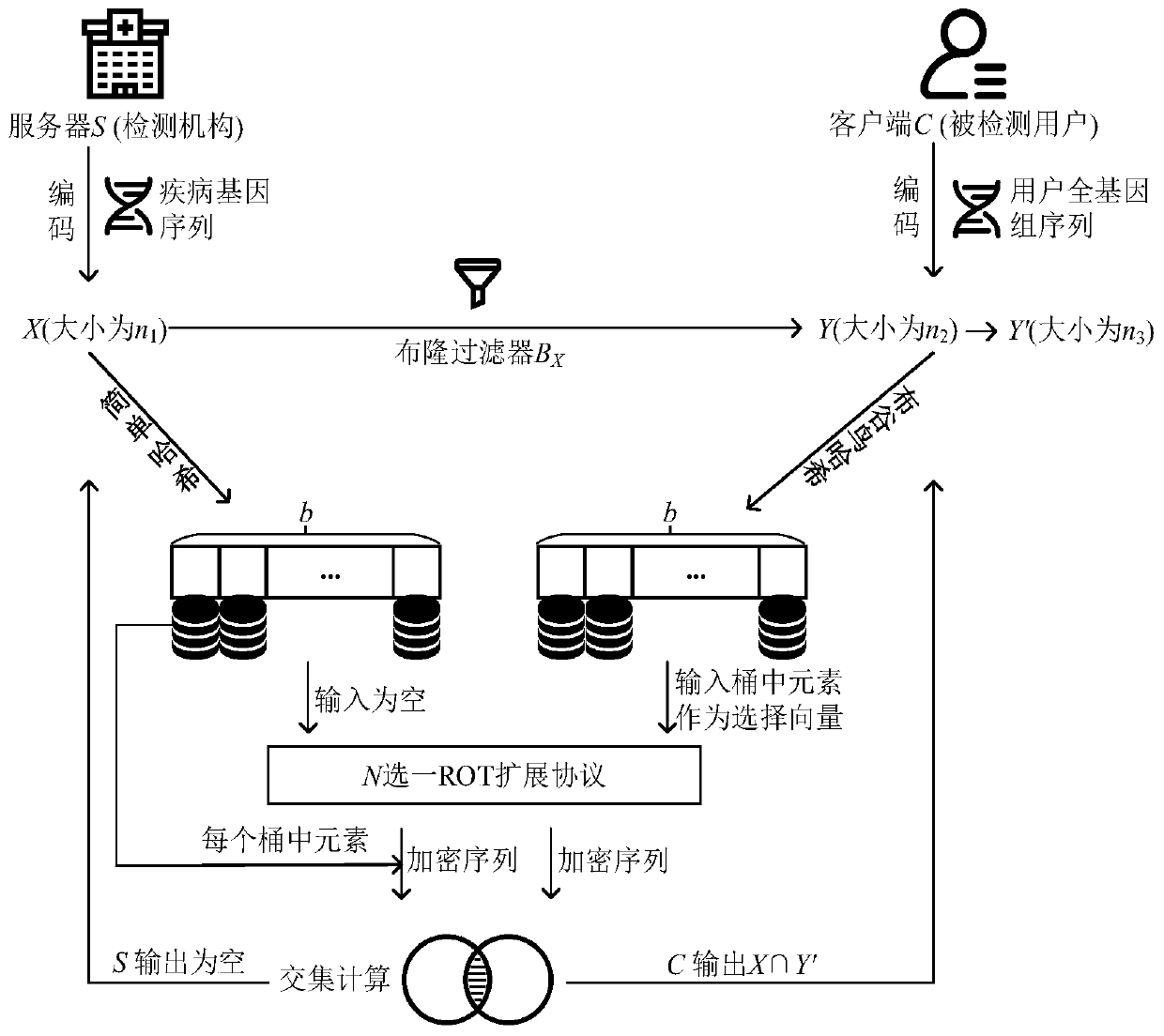
The invention discloses a pathogenic gene detection method based on a privacy protection intersection calculation protocol. According to the method, elements which do not exist in an intersection of aset held by a server and a set held by a client are filtered out by adopting a Bloom filter; the elements of the server are mapped to hash buckets through simple hash mapping, and the elements of theclient are mapped to a two-dimensional hash table through cuckoo hash mapping; a one-out-of-N ROT extension protocol is executed on the elements in each bucket; an encryption sequence generated by the server is sent to the client; intersection calculation is carried out on the output of the client and the encryption sequence of the server; the set of the client, which has been subjected to filtering and hash mapping, is compared with a calculation result; and the intersection elements of the two parties are finally obtained, the information of any party except the intersection will not leak.With the method of the invention adopted, the safety of gene detection can be ensured, and running time and communication overhead are reduced.
Owner:JINAN UNIVERSITY
Elastic Key-Value pair data storage method based on RDMA and HTM
ActiveCN110069431AAlleviate the infinite loop problemImprove throughputTransmissionSpecial data processing applicationsPaired DataPrimitive operation
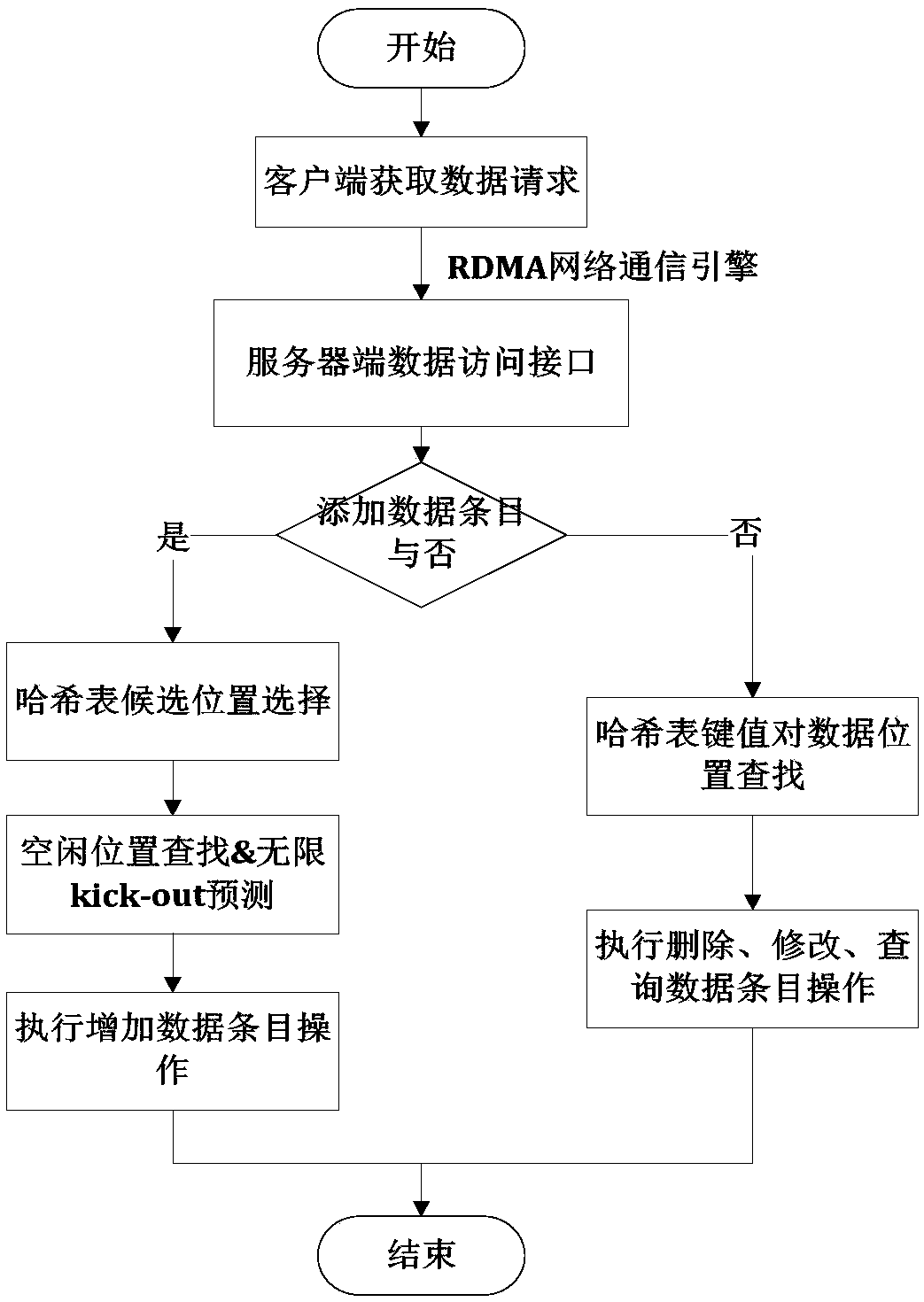
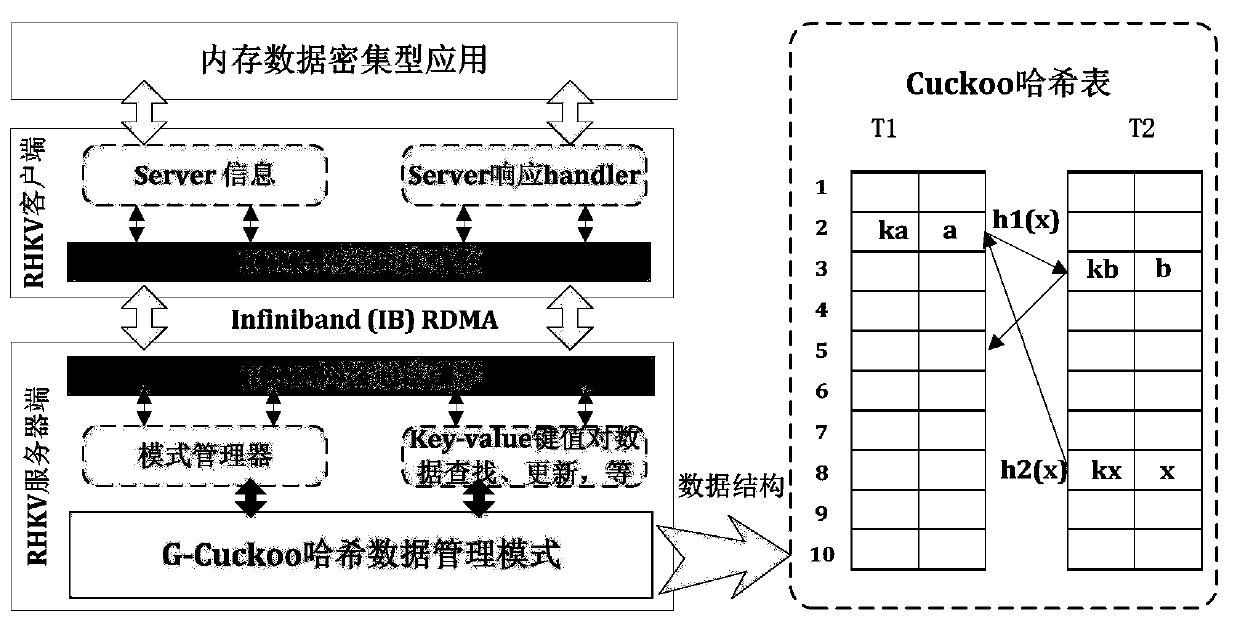
The invention provides an elastic Key-Value pair data storage method based on RDMA (Remote Direct Memory Access) and HTM (High Temperature Modulation). A server-client architecture mode is designed and followed, and the method comprises the steps that at a server side, an improved G-Cuckoo Hash data management mode is given in combination with a Hashmap; the kick-out infinite loop between Hash tables caused by searching for idle positions in the data insertion process is avoided. the bottleneck problem of key value pair storage performance caused by round response required by the traditional network message transmission between the client and the server is analyzed; an Infiniband remote direct memory access RDMA technology is used, an RDMA network communication engine is designed, a data access request is received, and a data request result is sent back; a hardware transaction memory HTM technology is utilized to realize a two-section lock protocol lock operation and ensure the atomiccharacteristics of data operation; and a key value is used for self-verifying the check code of the data to guarantee data consistency. The basic operation speed of the key value on the data can be greatly improved.
Owner:SHANGHAI JIAO TONG UNIV
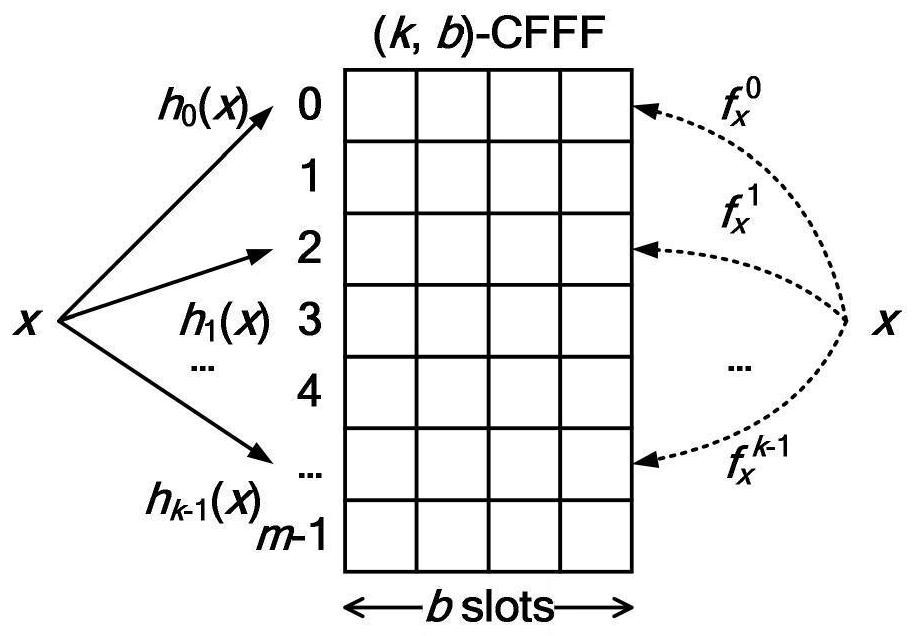
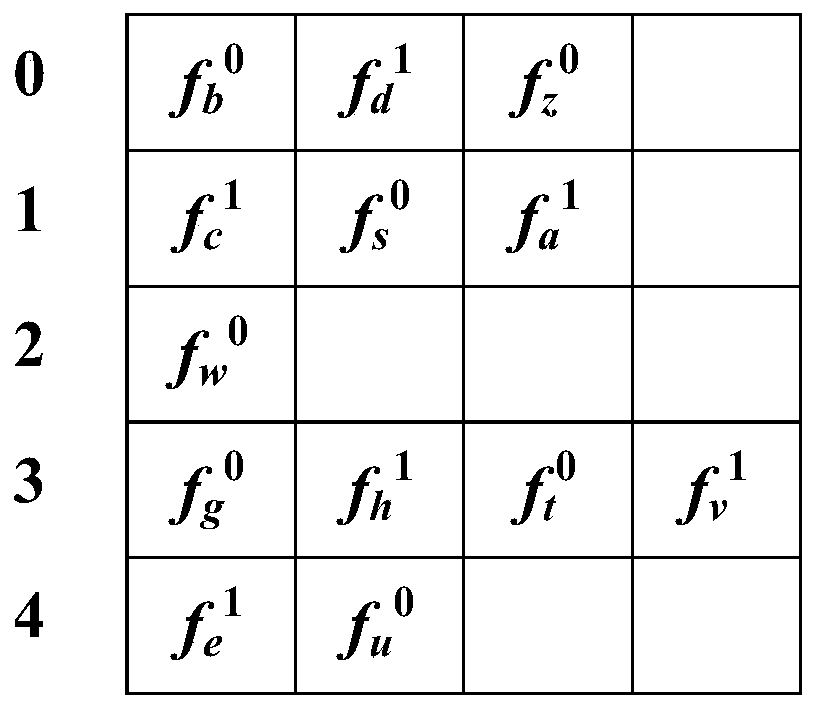
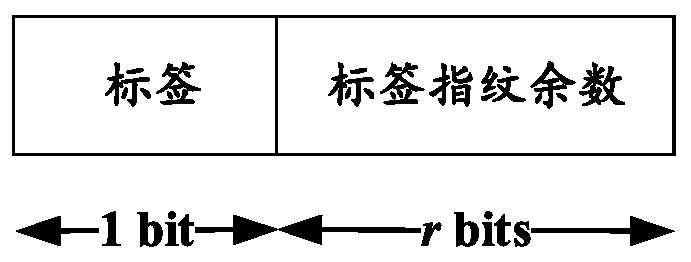
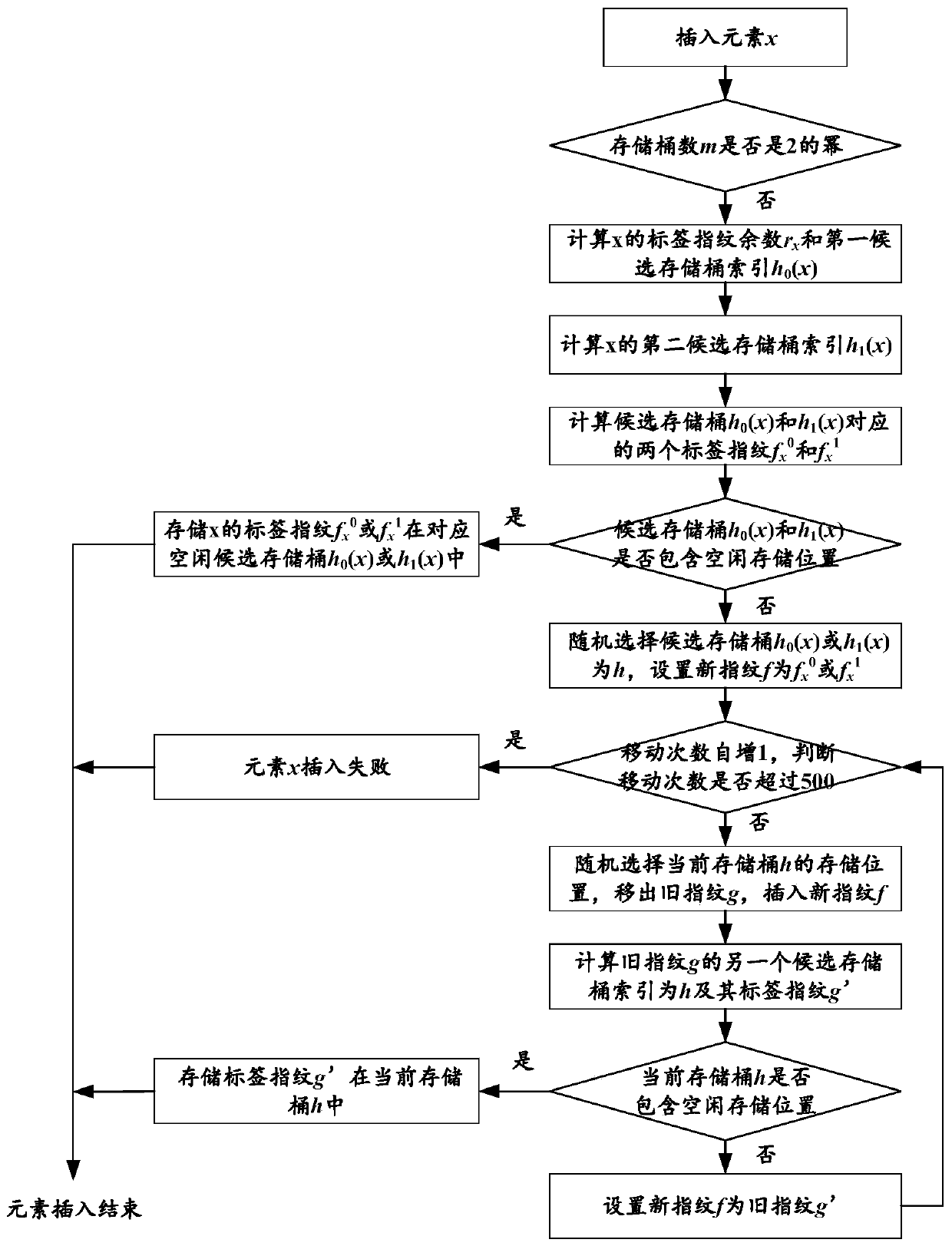
Cuckoo filter based on fingerprint family
PendingCN112148928AImprove storage space efficiencyQuick insertOther databases indexingSpecial data processing applicationsAlgorithmEngineering
The invention discloses a cuckoo filter based on a fingerprint family, the cuckoo filter based on the fingerprint family comprises a cuckoo hash table, the cuckoo hash table comprises a plurality of storage buckets, each data member corresponds to a plurality of fingerprints, and each fingerprint in the plurality of fingerprints is stored in different storage buckets; and when the cuckoo filter receives a data member management operation, a plurality of fingerprints corresponding to the data members and candidate storage buckets corresponding to the fingerprints are determined based on addition and subtraction operations, and the data member management operation is executed based on the determined fingerprints and the candidate storage buckets corresponding to the fingerprints. According to the invention, the plurality of fingerprints and the plurality of candidate storage buckets are allocated to each data member, and the number of the plurality of fingerprints can be greater than orequal to 2, so that the storage space efficiency can be improved, and quick insertion, deletion and query operations are supported.
Owner:PENG CHENG LAB +1
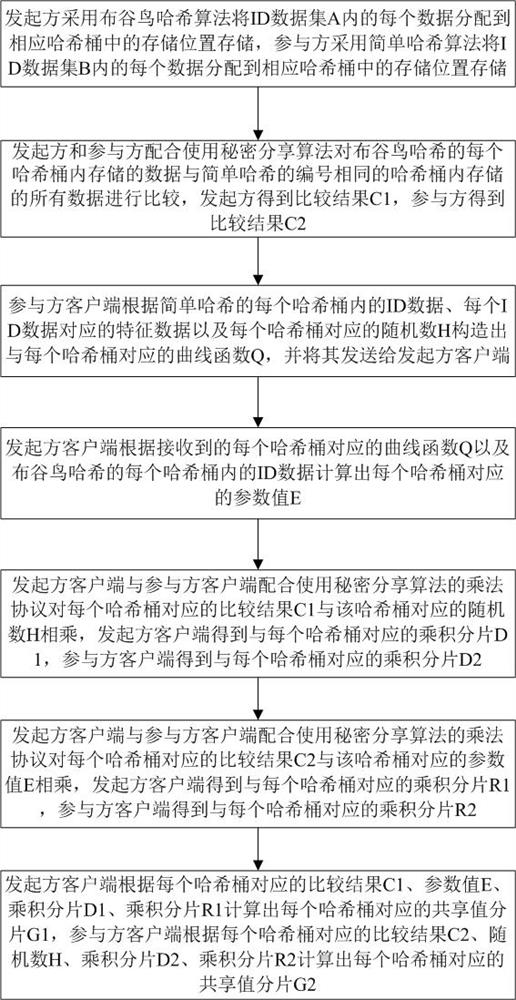
Private data hiding and sharing method
ActiveCN114661680AWon't leakPrivacy protectionDigital data information retrievalDigital data protectionComputer networkData set
The invention discloses a private data hiding and sharing method. The method comprises the following steps: an initiator distributes each data in an ID data set A to a storage position in a corresponding Hash bucket for storage by adopting a cuckoo Hash algorithm, and a participant distributes each data in an ID data set B to a storage position in a corresponding Hash bucket for storage by adopting a simple Hash algorithm; the initiator and the participant cooperatively use a secret sharing algorithm to compare data stored in each hash bucket of the cuckoo hash with all data stored in the hash bucket with the same serial number of the simple hash, and the initiator and the participant obtain comparison results respectively; the initiator calculates a shared value fragment G1 corresponding to each hash bucket, and the participant calculates a shared value fragment G2 corresponding to each hash bucket; according to the invention, the participant can share one part of the feature data corresponding to the intersection ID data of the initiator to the initiator, and the ID data of both parties are not leaked, so that the privacy and security of private data of both parties are protected.
Owner:蓝象智联(杭州)科技有限公司
QoS (Quality of Service)-aware OpenFlow flow table hierarchical storage architecture and application
ActiveCN111131084AGuaranteed packet forwarding performanceReduce the average flow table lookup timeData switching networksHigh level techniquesQuality of serviceData pack
The invention discloses a QoS (Quality of Service)-aware OpenFlow flow table hierarchical storage architecture and application, and the architecture provided by the invention stores a high-priority flow in a TCAM (Ternary Content Addressable Memory), so that the grouping search performance of the high-priority flow is ensured; a Cuckoo hash structure is adopted to design an accurate flow cache mechanism and store low-priority and non-priority active accurate flows, so that data packets in the accurate flows directly hit caches, corresponding SRAM flow table entries are quickly found, the average flow table search time is remarkably shortened, and the performance of the OpenFlow switch is improved. According to the method, corresponding flow table searching speeds are provided for network flows with different priorities, wherein network packets in a high-priority flow directly hit a TCAM flow table, and corresponding flow table entries are quickly found; a hit Cuckoo cache is searched by a network packet in the low-priority flows, and a corresponding SRAM flow table entry is directly positioned; most of the groups in the priority-free flows can directly hit the Cuckoo cache, and a tuple space search method needs to be further adopted for searching the SRAM flow table for a small part of the groups, and therefore the overall searching efficiency is high.
Owner:CHANGSHA NORMAL UNIV
Label cuckoo filter
ActiveCN111552693AReduce storage space overheadArtificial lifeEnergy efficient computingEngineeringData mining
The invention discloses a label cuckoo filter which comprises a cuckoo hash table, the cuckoo hash table comprises a plurality of storage buckets, each data member corresponds to two label fingerprints, and the two label fingerprints are respectively stored in the two storage buckets; and when the tag cuckoo filter receives a data member management operation, determining two candidate storage buckets and two tag fingerprints corresponding to a preset data member based on the exclusive-OR operation, and executing the data member management operation based on the two candidate storage buckets and the two tag fingerprints obtained through determination. According to the method, two label fingerprints and two storage buckets are configured for each data member, the candidate storage buckets corresponding to the data members are determined by adopting the exclusive-OR operation based on the label fingerprints, and the number of the storage buckets is not required to be the power of 2, so that the storage space overhead of each data member is reduced.
Owner:SOUTH UNIVERSITY OF SCIENCE AND TECHNOLOGY OF CHINA +1
Single double cuckoo hash
ActiveUS9892057B2Memory architecture accessing/allocationDigital data information retrievalCuckooTheoretical computer science
In a network element a decision apparatus has a plurality of multi-way hash tables of single size and double size associative entries. A logic pipeline extracts a search key from each of a sequence of received data items. A hash circuit applies first and second hash functions to the search key to generate first and second indices. A lookup circuit reads associative entries in the hash tables that are indicated respectively by the first and second indices, matches the search key against the associative entries in all the ways. Upon finding a match between the search key and an entry key in an indicated associative entry. A processor uses the value of the indicated associative entry to insert associative entries from a stash of associative entries into the hash tables in accordance with a single size and a double size cuckoo insertion procedure.
Owner:MELLANOX TECHNOLOGIES LTD
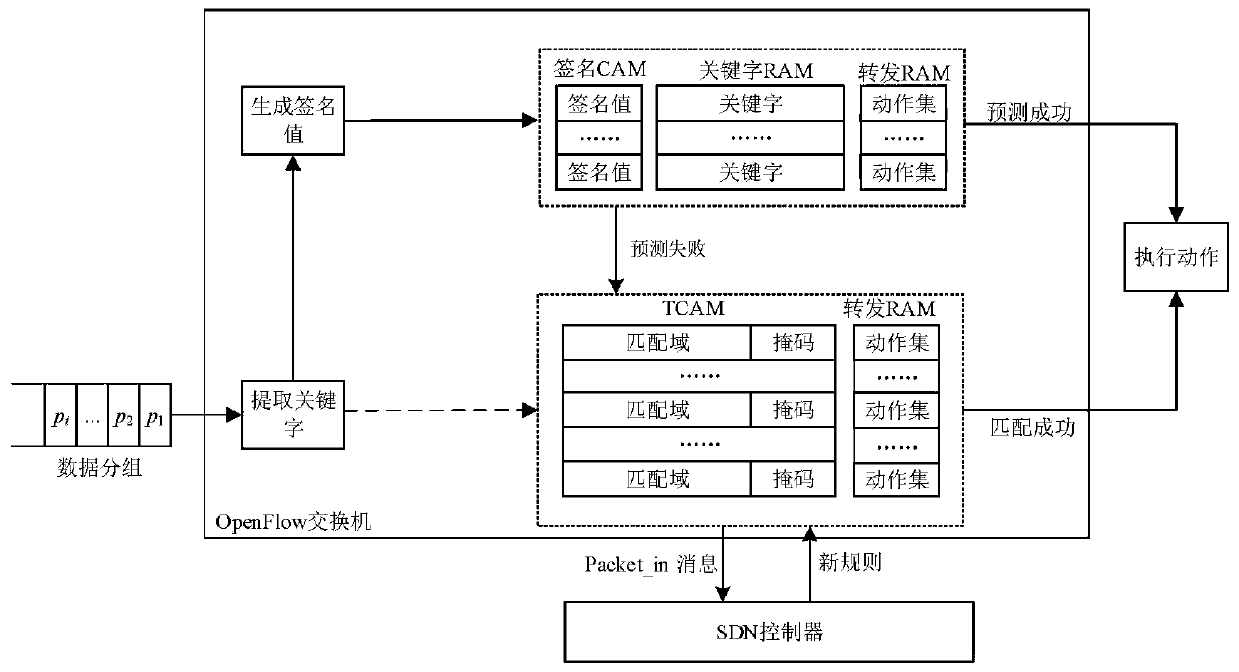
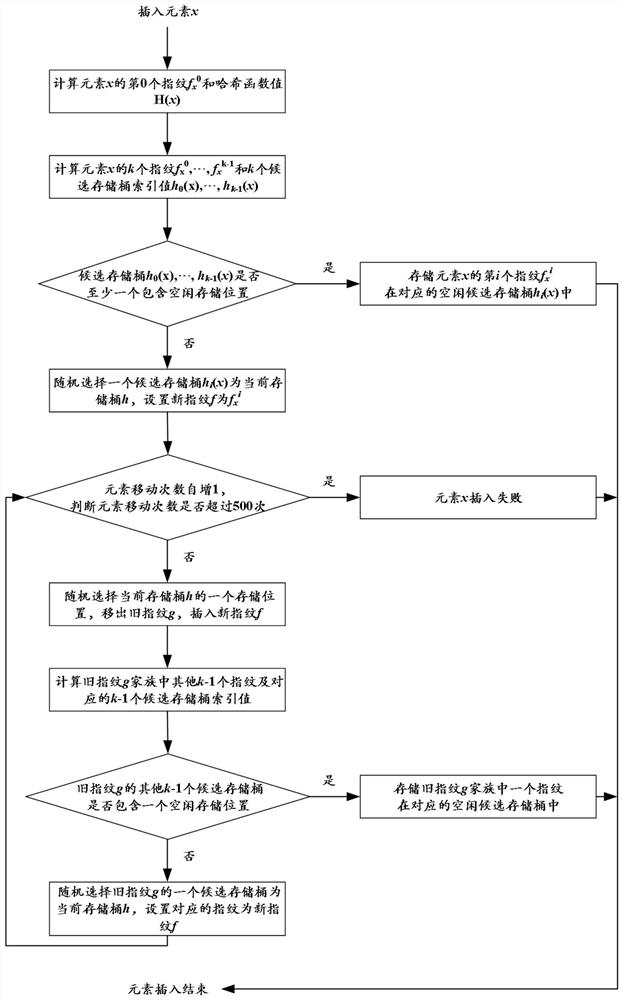
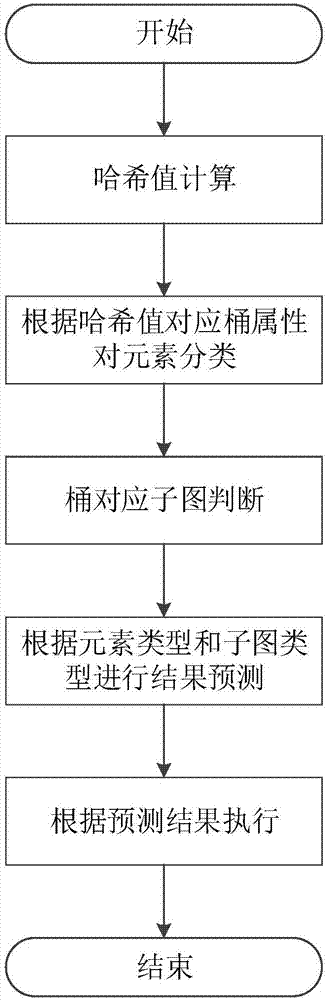
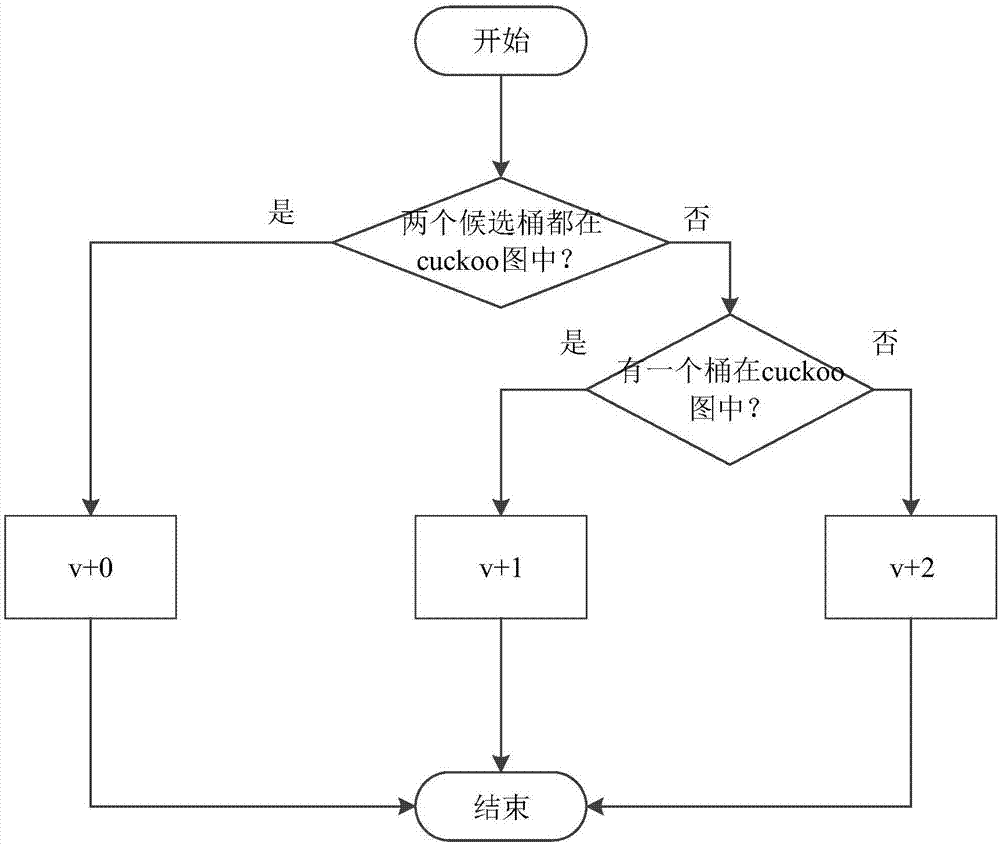
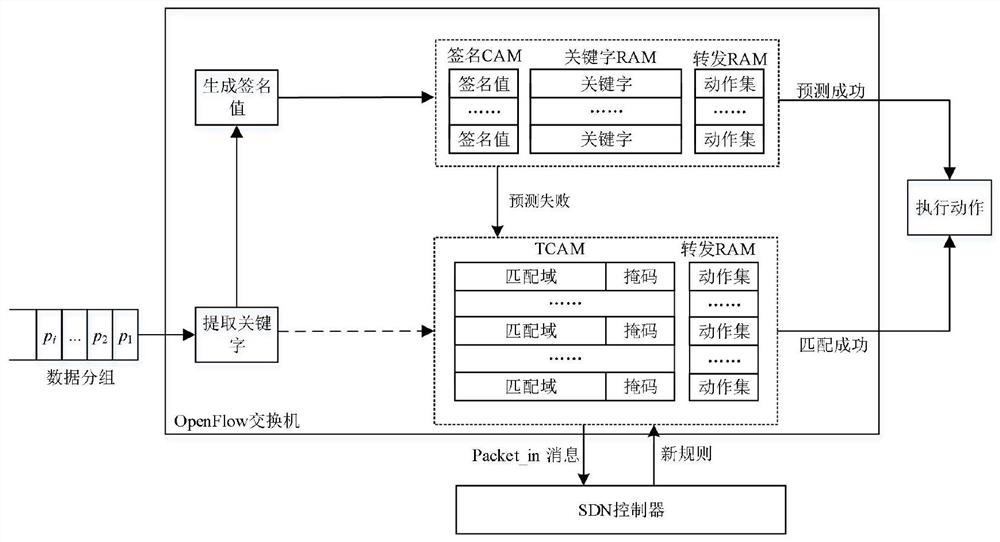
Cuckoo hash calculation-based data storage optimization method and system
ActiveCN107256130ASolve the infinite loop problemImprove storage efficiencyInput/output to record carriersData storeUtilization rate
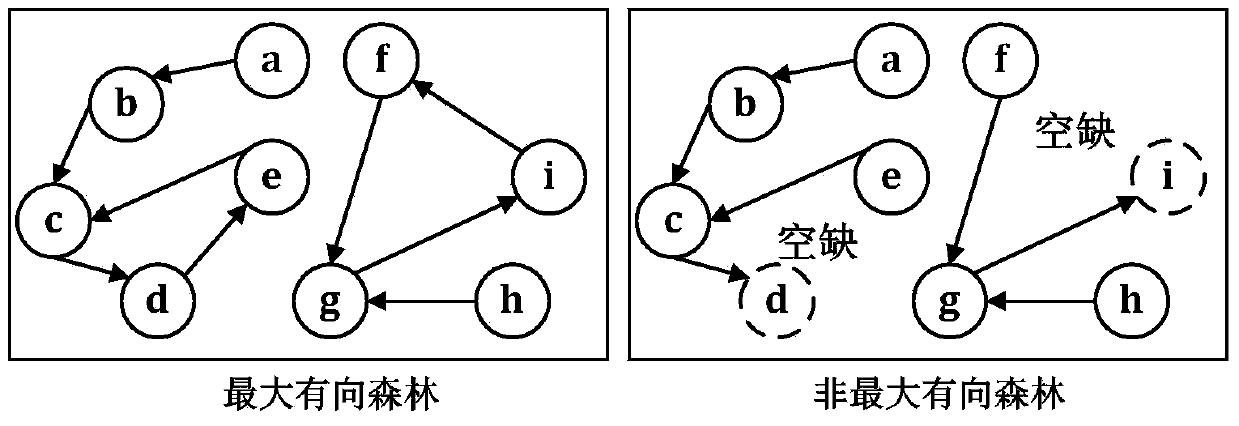
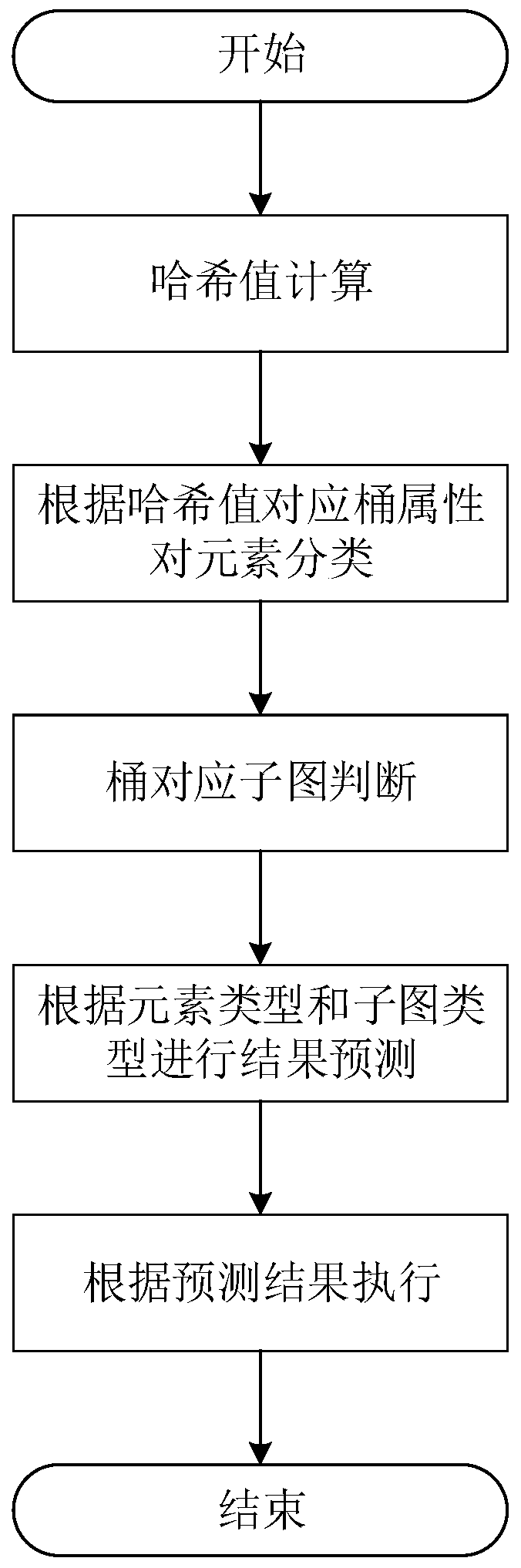
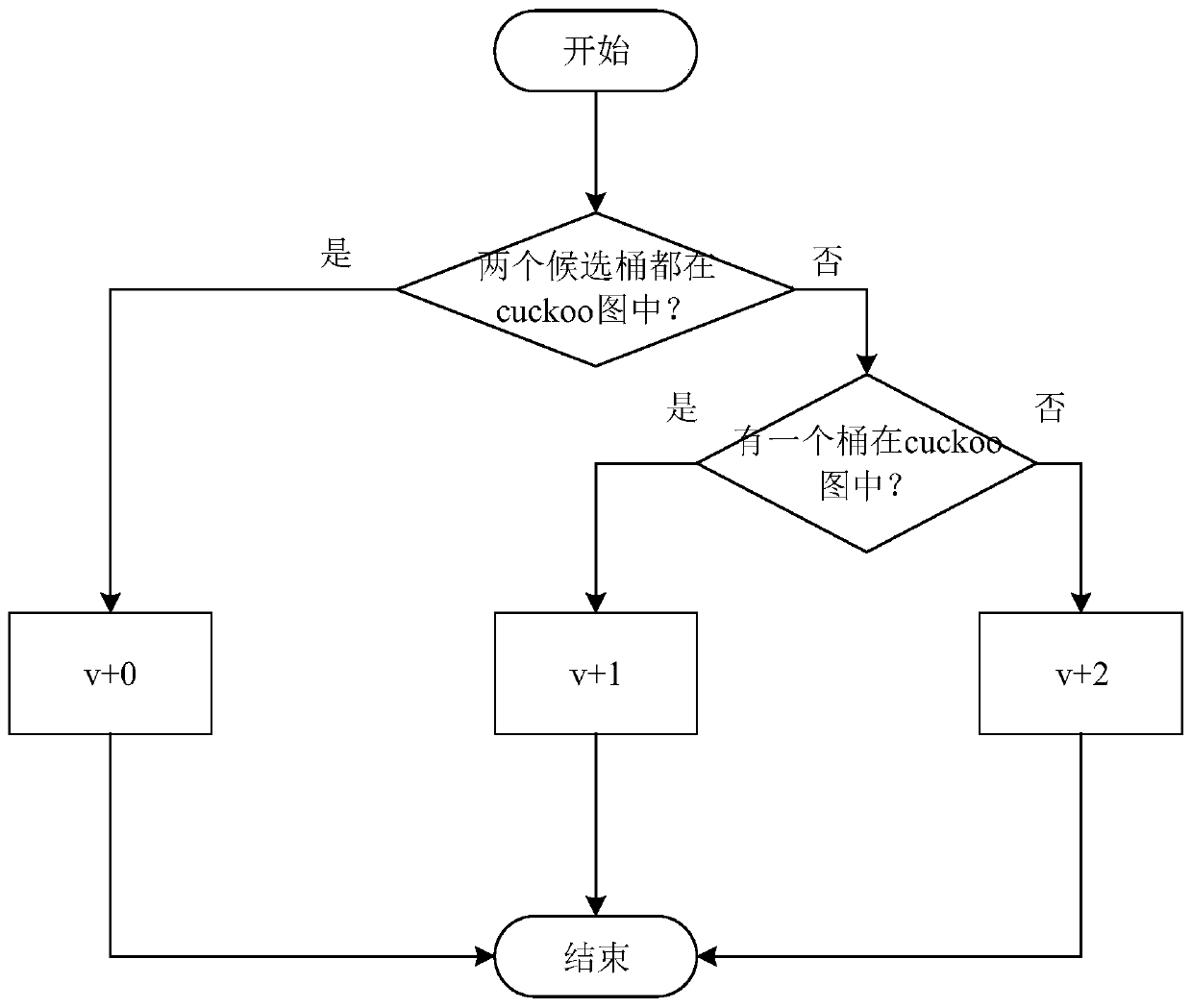
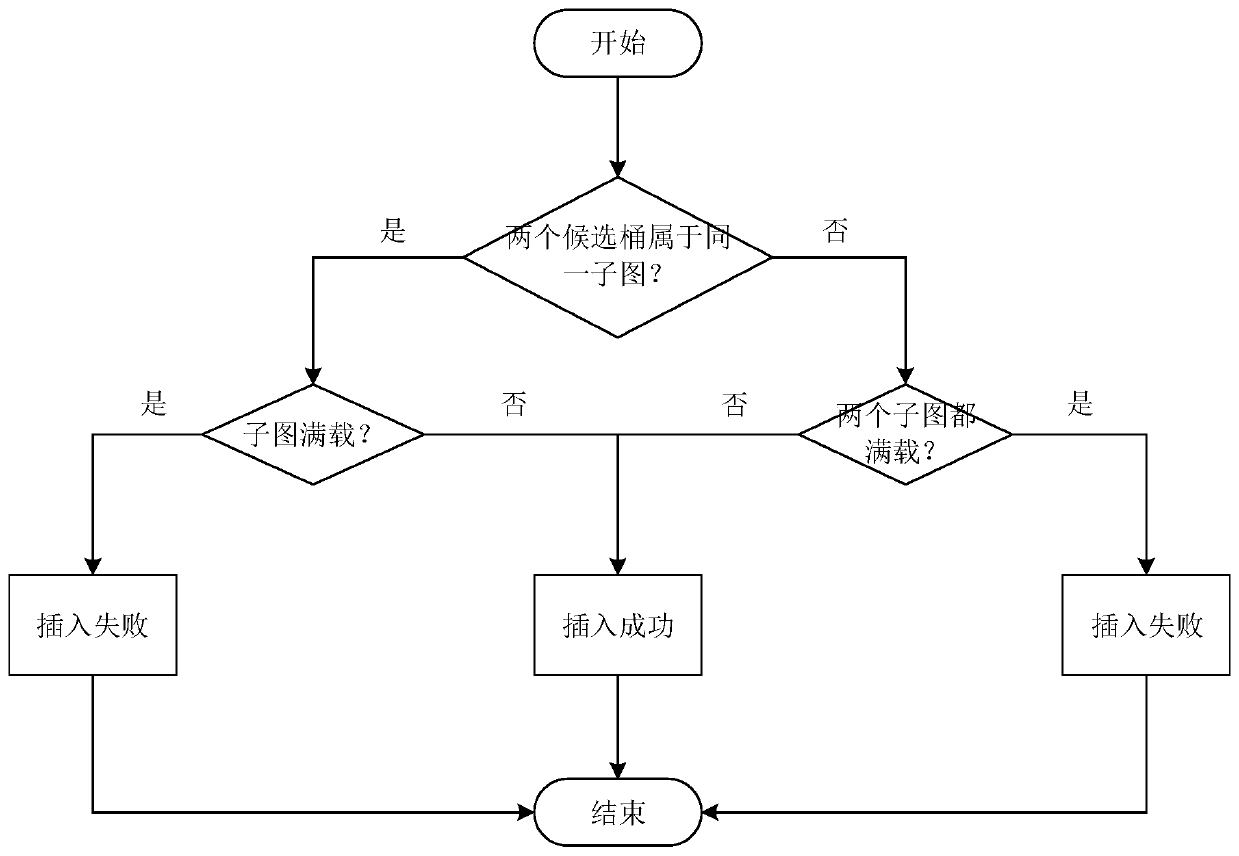
The invention discloses a Cuckoo hash calculation-based data storage optimization method and system. The method comprises the following steps of: considering each barrel in an index table as a subgraph node, considering each element stored in the table as an edge, and pointing from practical storage positions to candidate positions of the elements so as to form the whole index table into a diagraph comprising a plurality of connected subgraphs; recognizing one or two subgraphs of each element through hash calculation before the element is practically inserted; predicting an insertion result according to states of the subgraphs; and finally executing an insertion operation according to the prediction result or directly storing the prediction result into a temporary space. According to the method and system, mass data is flat hashed to the whole index table by utilizing a Cuckoo hash mechanism, so that the hash conflict of data in sets is reasonably solved, the load is balanced under the condition of ensuring the query efficiency, the utilization rate of the index table is effectively improved and the data insertion result is predicted in advance; and through predicting the result before data storage, the ineffective kicking overhead is avoided and the data storage efficiency is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
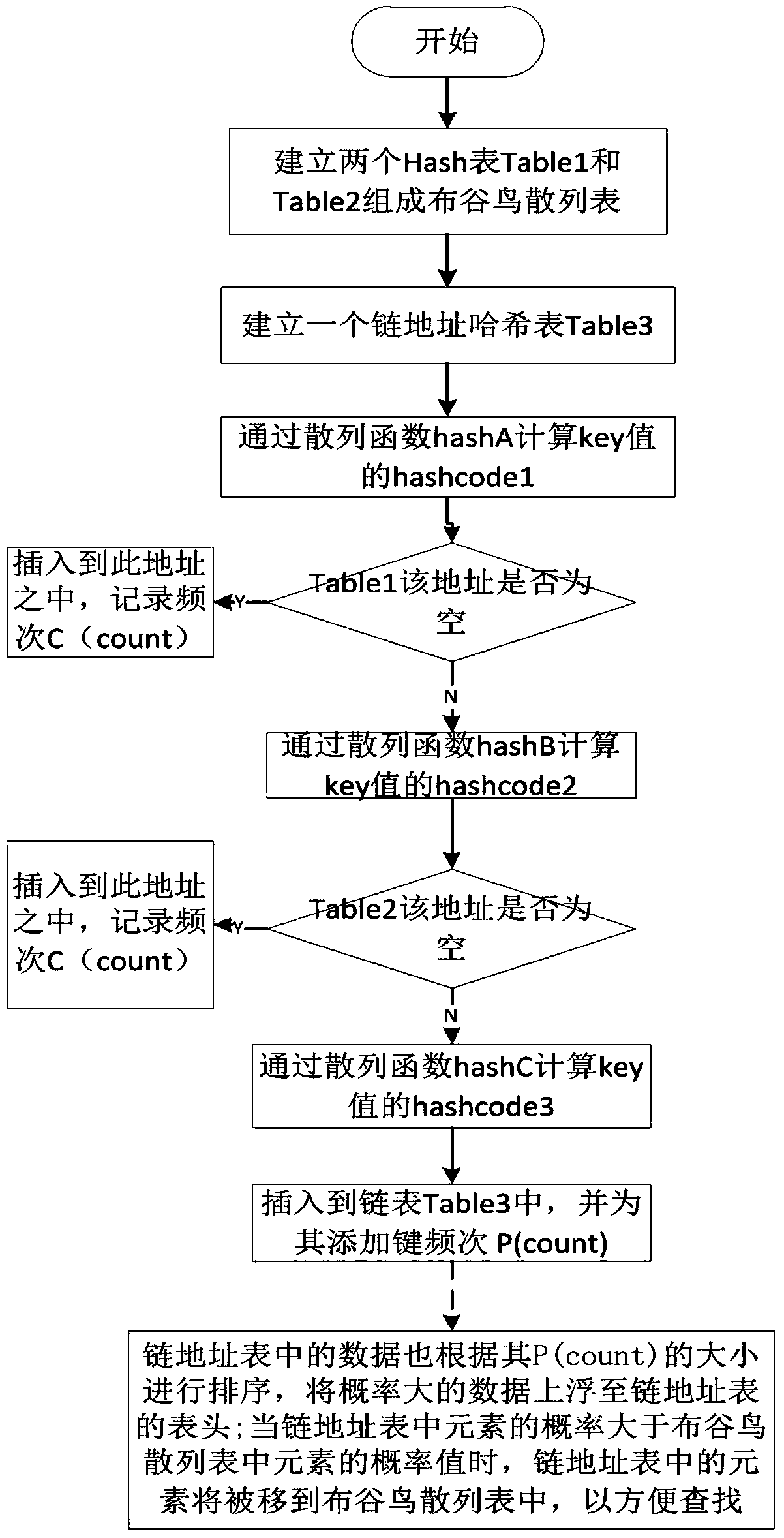
Method for efficiently and quickly solving hash conflicts
ActiveCN109800228ASimple structureOptimize search efficiencyDatabase indexingTheoretical computer scienceHash table
The invention relates to a method for efficiently and quickly solving hash conflicts. The invention relates to a method for efficiently and quickly solving hash conflicts, which realizes a hybrid hashtable searching method by combining a cuckoo hash idea with a chain address method algorithm and introducing an LRU algorithm for optimization, can optimize hash table construction and searching efficiency, and meanwhile, improves the utilization rate of hash tables. And the indexing process of the hash addressing key can be greatly accelerated.
Owner:深圳竹云科技股份有限公司
Method and device for determining same service data based on privacy protection
ActiveCN111460510AReduce the number of comparisonsReduce productionDigital data protectionSpecial data processing applicationsPrivacy protectionHash table
The embodiment of the invention provides a method for determining the same service data of multiple service parties based on privacy protection. Four hash tables are respectively set in each service party according to the same rule; the cuckoo hash and the hash value storage position coincidence principle of the same service data are adopted, so that the data comparison frequency between every twoservice parties is greatly reduced, for example, the data comparison frequency is reduced to the product of 8 (the number of sub-tables) and the number of service data owned by a service party with more service data; and on the other hand, an equality comparison mode based on secret sharing is adopted to carry out two-party data comparison at a corresponding position, and a method of randomly extracting a part of bits for comparison is adopted in the data comparison process, so that the calculation amount in the security comparison process is reduced, and the comparison efficiency is improved. In a word, the technical concept of the specification can improve the efficiency of determining the same service data of a plurality of service parties on the basis of privacy protection.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
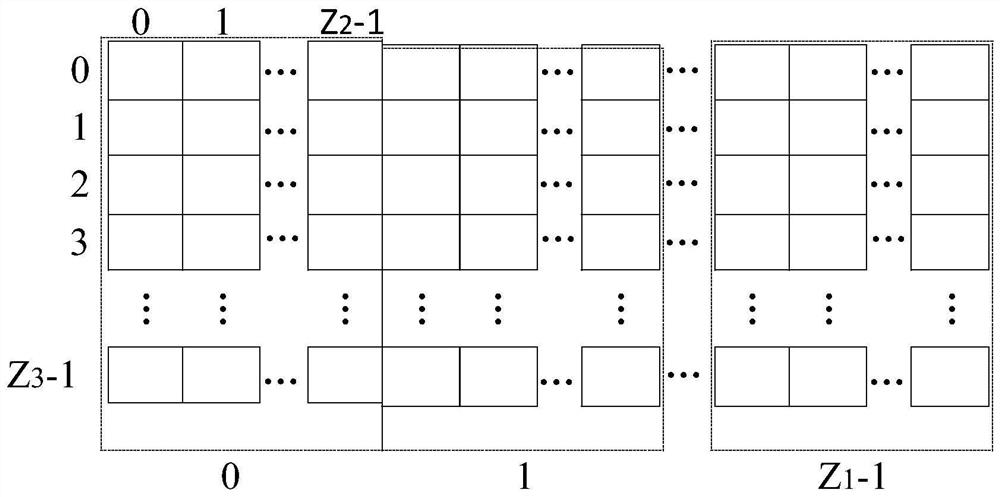
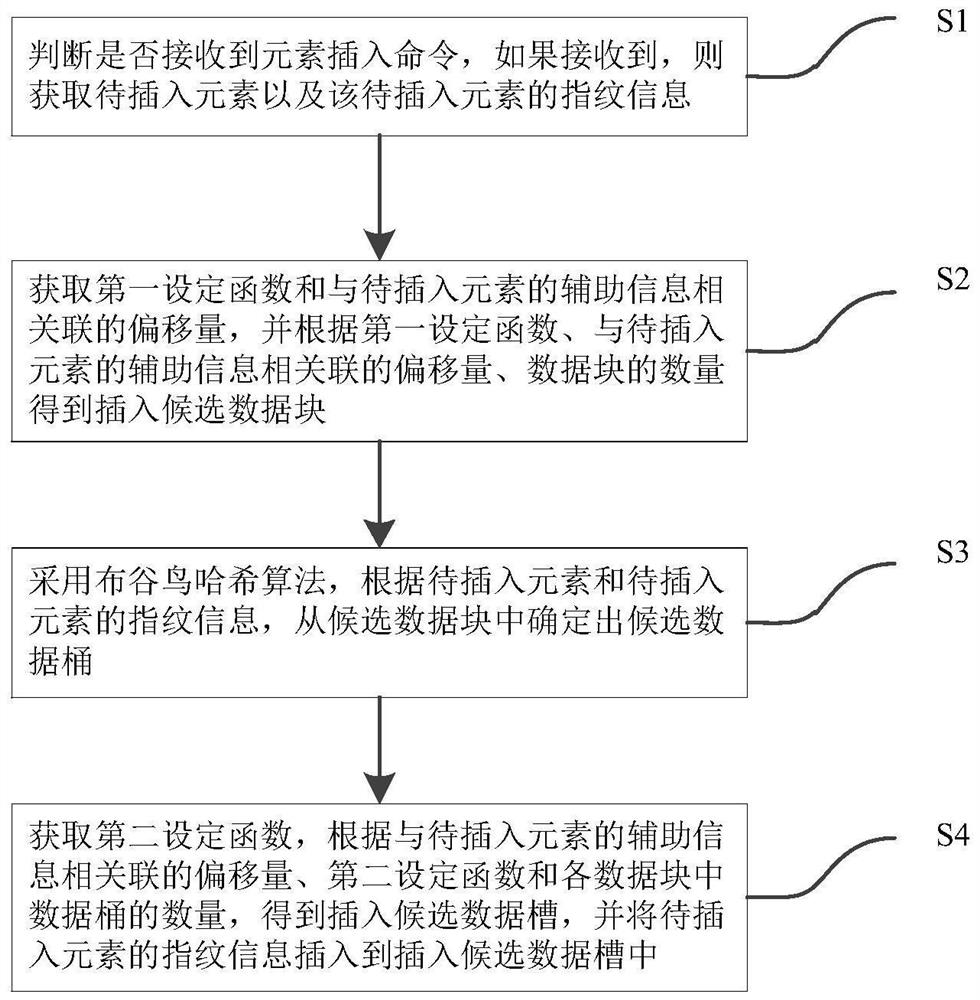
High-efficiency dynamic set management method and system
PendingCN114706834AImprove space utilizationData structure space friendlySpecial data processing applicationsDatabase design/maintainanceHash functionDynaset
The invention relates to an efficient dynamic set management method and system, a dynamic set is provided with a plurality of data blocks, each data block is provided with a plurality of data buckets, each data bucket is provided with a plurality of data slots, and the data slots are used for storing fingerprint information of elements. Obtaining a to-be-inserted element and fingerprint information thereof; obtaining a first hash function, and obtaining insertion candidate data blocks according to the first hash function, the offset and the total number of the data blocks; determining insertion candidate data buckets from the insertion candidate data blocks by adopting a cuckoo Hash algorithm according to the to-be-inserted elements and the fingerprint information of the to-be-inserted elements; obtaining a second hash function, and obtaining insertion candidate data slots according to the second hash function, the offset and the number of the data buckets in each data block; and inserting the element to be inserted into the candidate data slot. According to the technical scheme, the space efficiency of the dynamic set can be improved, and the false positive probability is reduced.
Owner:NAT UNIV OF DEFENSE TECH
Data processing method and device in multi-party privacy intersection and electronic equipment
ActiveCN113489583AShorten the timeImprove the efficiency of privacy claimsEncryption apparatus with shift registers/memoriesAlgorithmEngineering
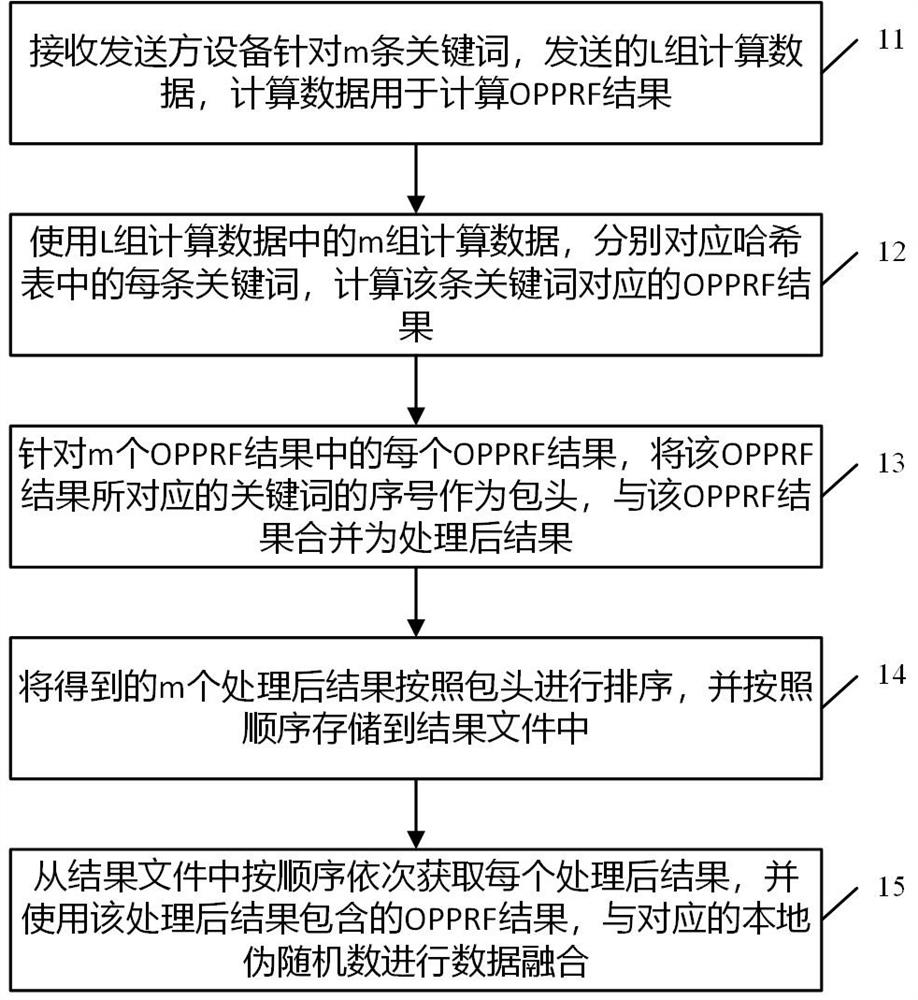
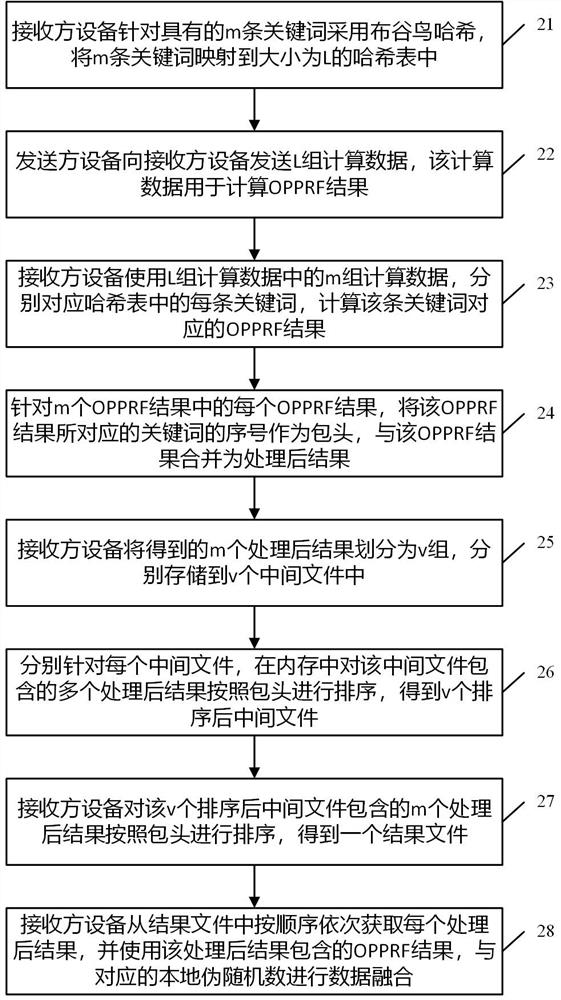
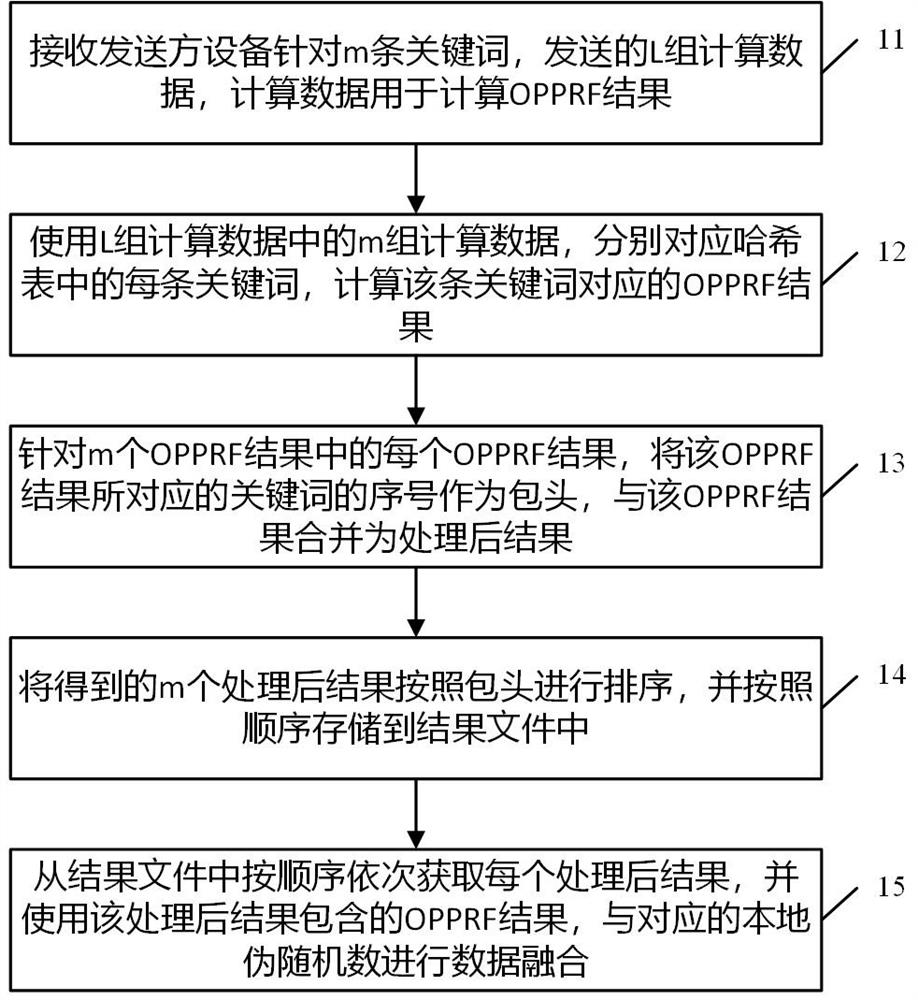
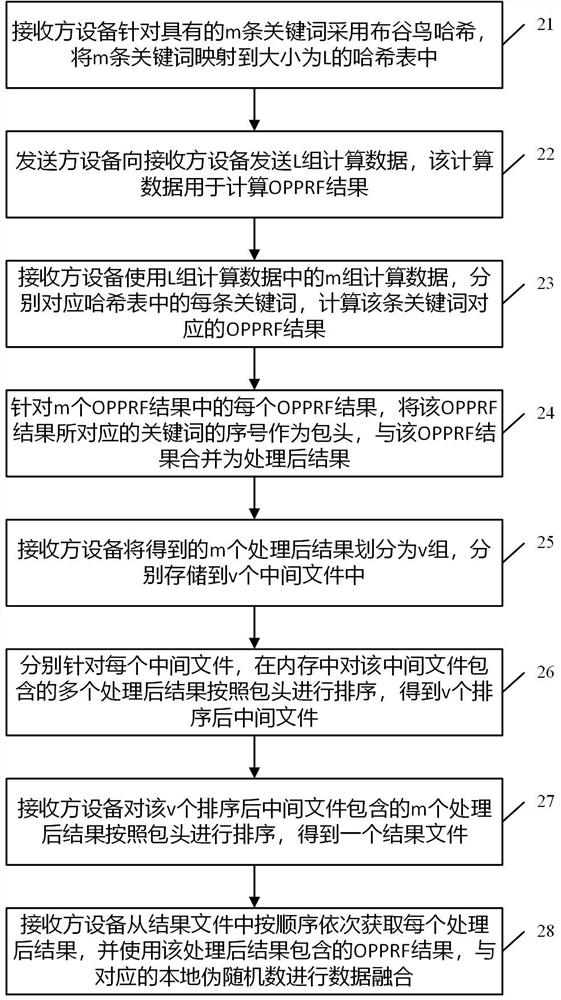
The invention discloses a data processing method in multi-party privacy intersection, which is applied to a receiver device. M keywords of the receiver device are mapped to a hash table with the size of L by adopting cuckoo hash. The method comprises the following steps: receiving L groups of calculation data sent by a sender device for the m keywords; using m groups of calculation data in the L groups of calculation data to respectively correspond to each keyword in the hash table, and calculating an OPPRF result corresponding to the keyword; for each OPPRF result in the m OPPRF results, taking the serial number of the keyword corresponding to the OPPRF result as a packet header, and combining the packet header with the OPPRF result to form a processed result; sorting the obtained m processed results according to packet headers, and storing the m processed results in a result file according to a sequence; and sequentially obtaining each processed result from the result file according to a sequence, and carrying out data fusion on the OPPRF result contained in the processed result and the corresponding local pseudo-random number. By adopting the scheme, the multi-party privacy intersection efficiency is improved.
Owner:HUAKONG TSINGJIAO INFORMATION SCI BEIJING LTD
Mechanism to support multiple-writer/multiple-reader concurrency for software flow/packet classification on general purpose multi-core systems
Methods and apparatus to support multiple-writer / multiple-reader concurrency for software flow / packet classification on general purpose multi-core systems. A flow table with rows mapped to respective hash buckets with multiple entry slots is implemented in memory of a host platform with multiple cores, with each bucket being associated with a version counter. Multiple writer and reader threads are run on the cores, with writers providing updates to the flow table data. In connection with inserting new key data, a determination is made to which buckets will be changed, and access rights to those buckets are acquired prior to making any changes. For example, under a flow table employing cuckoo hashing, access rights are acquired to buckets along a full cuckoo path. Once the access rights are obtained, a writer is enabled to update data in the applicable buckets to effect entry of the new key data, while other writer threads are prevented from changing any of these buckets, but may concurrently insert or modify key data in other buckets.
Owner:INTEL CORP
A compound index method and device
ActiveCN104536958BReduce space overheadImprove efficiencyRelational databasesSpecial data processing applicationsData streamTheoretical computer science
Owner:HUAWEI TECH CO LTD
Data processing method, device and electronic equipment in multi-party privacy seeking
ActiveCN113489583BShorten the timeImprove the efficiency of privacy claimsEncryption apparatus with shift registers/memoriesTheoretical computer scienceEngineering
This application discloses a data processing method in multi-party privacy seeking, which is applied to a receiver device. The m keywords of the receiver device are mapped to a hash table of size L by using cuckoo hash, including : Receive the L group of calculation data sent by the sending device for m keywords; use the m groups of calculation data in the L group of calculation data to correspond to each keyword in the hash table, and calculate the OPRF result corresponding to this keyword ; For each OPRF result in the m OPPRF results, the sequence number of the keyword corresponding to the OPPRF result is used as a header, and the OPPRF result is merged into a processed result; the obtained m processed results are sorted according to the header, and stored in the result file in order; each processed result is sequentially obtained from the result file, and the OPRF result contained in the processed result is used to perform data fusion with the corresponding local pseudo-random number. Adopting this scheme improves the efficiency of multi-party privacy seeking.
Owner:HUAKONG TSINGJIAO INFORMATION SCI BEIJING LTD
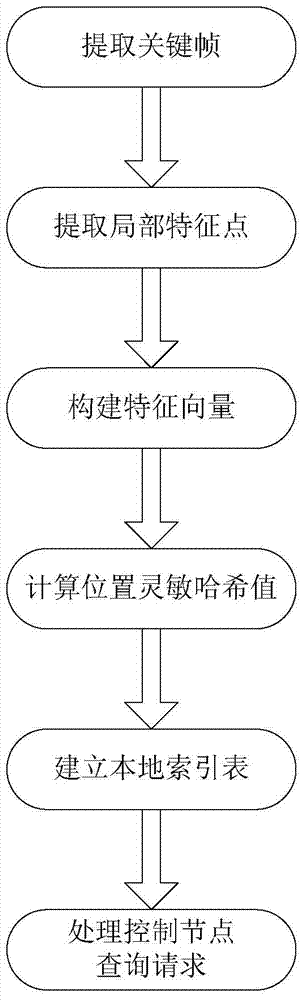
A method and system for detecting duplicate video based on correlation characteristics
ActiveCN104657383BEfficient managementGuaranteed detection effectSpecial data processing applicationsHash functionData store
The invention belongs to the technical field of computer data storage and discloses a repeated video detection method and system based on correlation properties in a mass storage system. The method uses position-sensitive hash functions to map repeated videos or similar videos to the same set of an index table, and accordingly the corresponding set can be directly located to perform finding when querying, traversing is not needed, the querying range is greatly shortened, and the querying speed of the repeated video detection method is improved. In the set, a Cuckoo Hashing mechanism is used for performing flat addressing in the whole index table, Hash collision in the set is reasonably solved, the index table maintains the correlation properties on the whole, the querying speed is not influenced, and accordingly the load balance is realized, and the use ratio of the index table is effectively improved.
Owner:HUAZHONG UNIV OF SCI & TECH
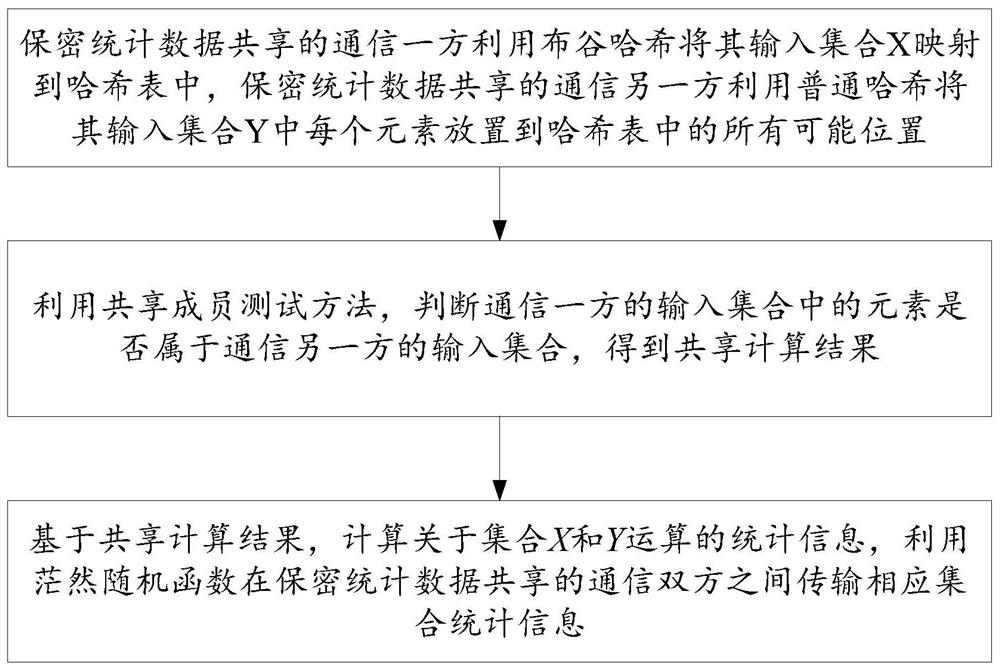
Method and system for sharing confidential statistical data based on set operation
ActiveCN111984984BTraffic optimizationConfidential StatisticsDigital data protectionComputer networkEngineering
The invention belongs to the field of information security and provides a confidential statistical data sharing method and system based on set operation. Among them, the confidential statistical data sharing method based on the set operation includes that the communication party of the confidential statistical data sharing uses cuckoo hash to map its input set X to the hash table, and the other communication party of the confidential statistical data sharing uses ordinary hash to input it Each element in the set Y is placed in all possible positions in the hash table; use the shared membership test method to judge whether the elements in the input set of the communication party belong to the input set of the other party in the communication, and obtain the shared calculation result; based on the shared calculation result , calculate statistical information about the set X and Y operations, and use the dazed random function to transmit the corresponding set statistical information between the communication parties sharing the confidential statistical data.
Owner:SHANDONG UNIV
A QOS-supporting openflow flow table energy-saving storage architecture and method thereof
ActiveCN110808910BGuaranteed flow table lookup performanceGuaranteed service qualityData switching networksQos quality of serviceParallel computing
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
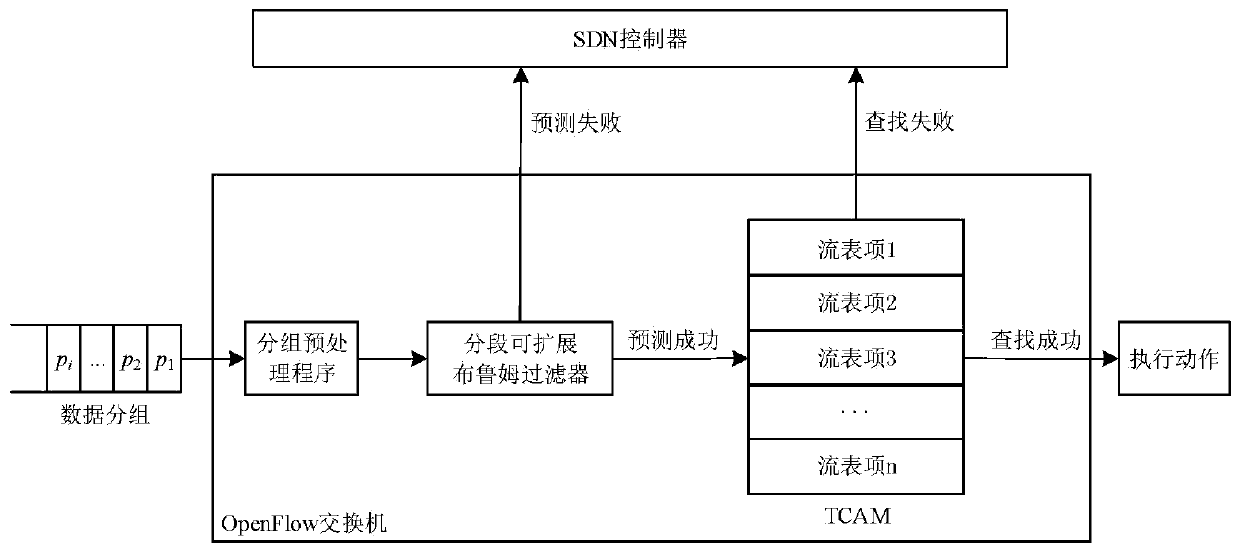
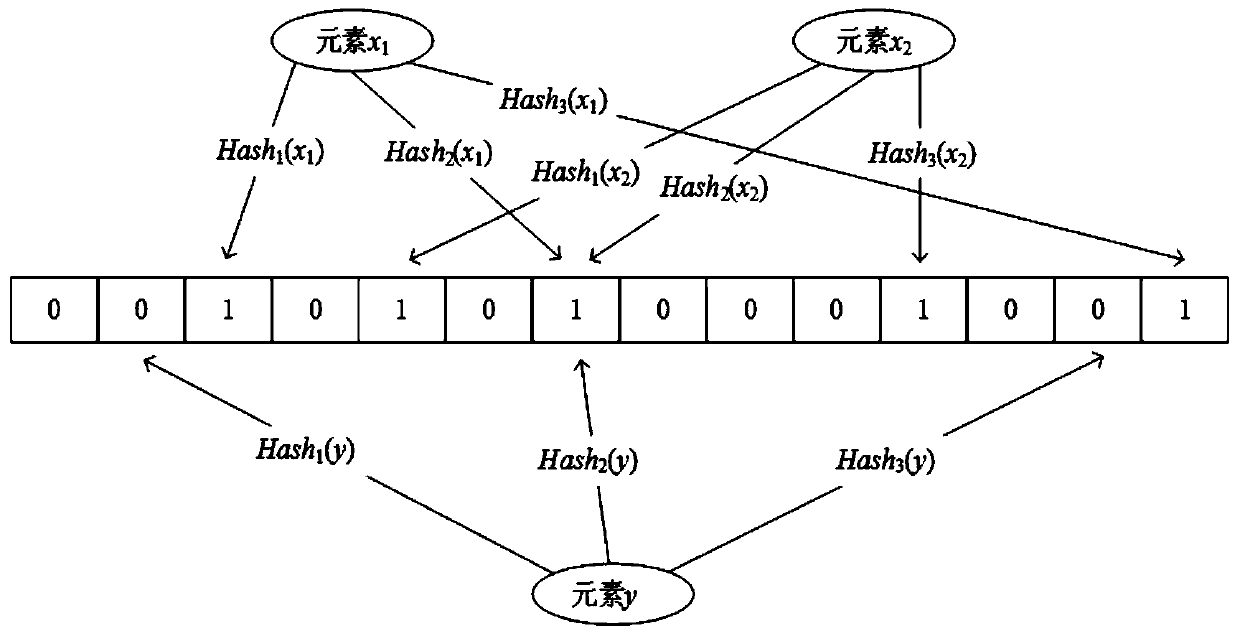
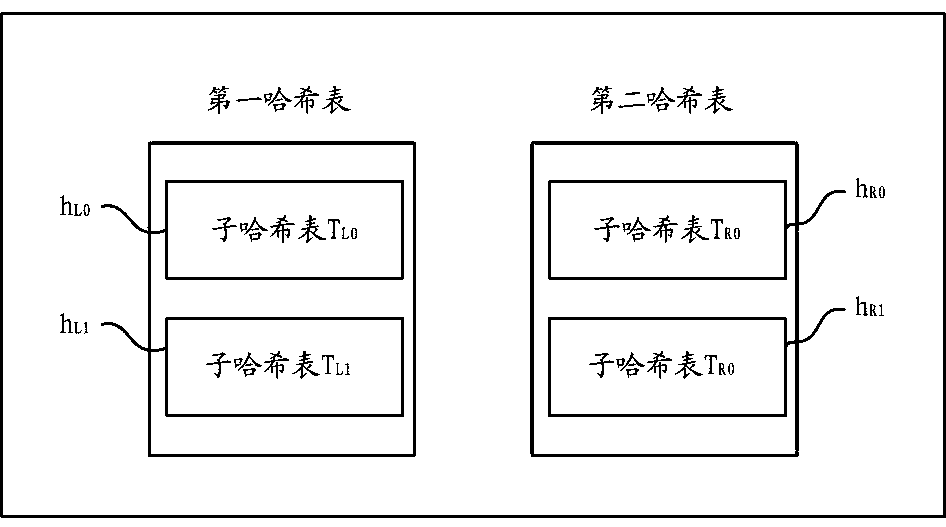
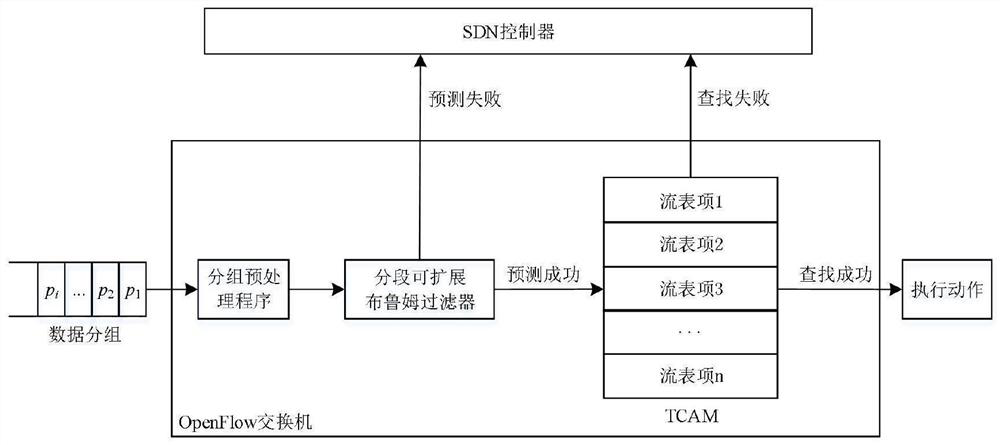
Hash table building method based on cuckoo hash and Bloom filter
ActiveCN108647289BReduce restrictionsImprove space utilizationDatabase indexingBloom filterHash table
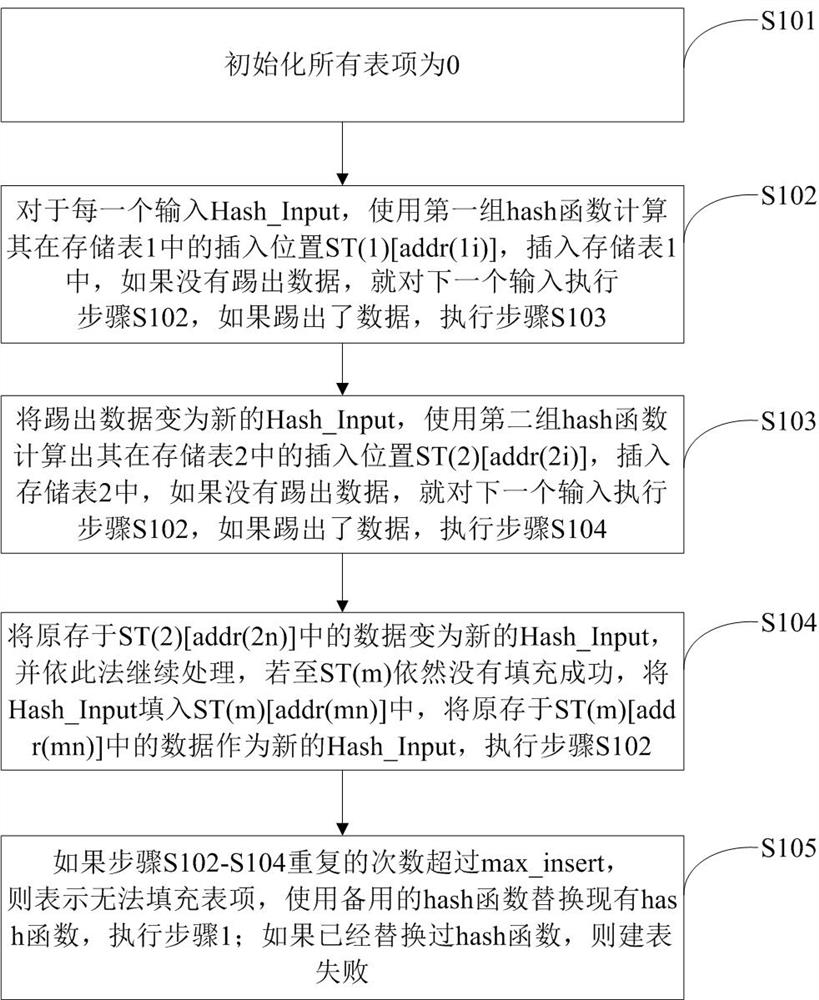
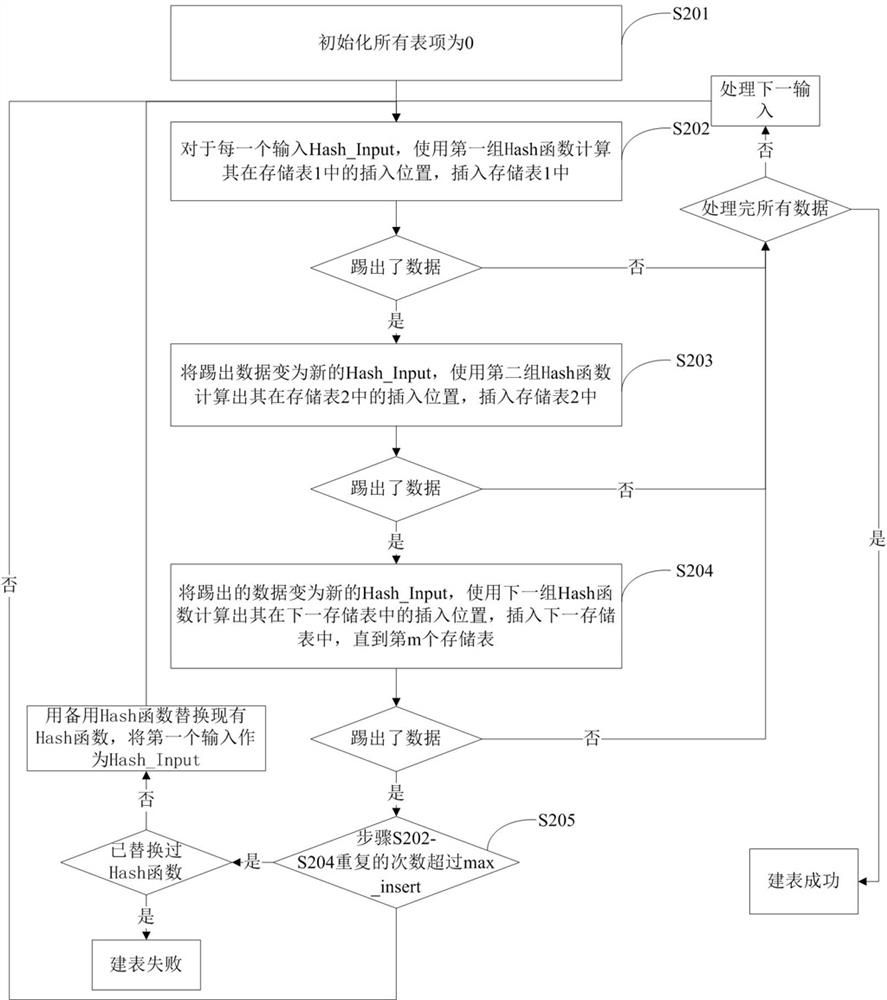
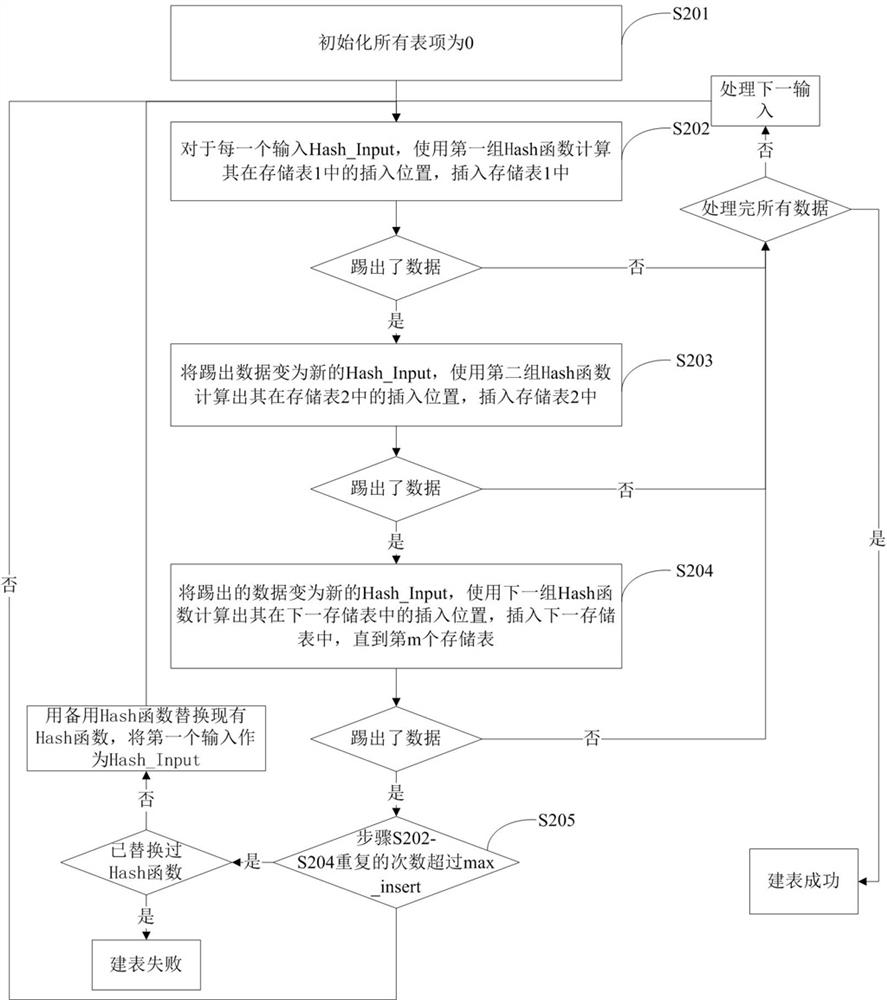
The invention relates to a Hash table building method based on cuckoo hash and Bloom filter. The present invention divides the storage space into m groups, each group includes a storage table and n filter tables, each filter table corresponds to a Hash function, and there are m*n different Hash functions; in addition, m*n different Hash functions are selected The Hash function is reserved; define a max_insert value, if the number of operations on a certain input data exceeds the max_insert value, it means that the form filling fails. The table building method provided by the invention effectively improves the space utilization rate and is beneficial to design and development in limited hardware storage space. And there is no limit to the value of m. m can take any value that the designer thinks is appropriate. Compared with many traditional Hash table building methods, it has higher flexibility. Simultaneously, the present invention eliminates the restriction on Hash function selection, and is easier to use.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
Data storage optimization method and system based on cuckoo hash calculation
ActiveCN107256130BSolve the infinite loop problemImprove storage efficiencyInput/output to record carriersData storeUtilization rate
Owner:HUAZHONG UNIV OF SCI & TECH
A QoS-aware openflow flow table lookup method
ActiveCN111131084BGuaranteed packet forwarding performanceReduce the average flow table lookup timeTransmissionHigh level techniquesData packNetwork packet
The invention discloses a QoS-aware OpenFlow flow table hierarchical storage architecture and its application. The architecture of the invention stores high-priority flows in TCAM, which ensures the packet search performance of high-priority flows; adopts Cuckoo hash structure to design accurate flows The cache mechanism stores low-priority and no-priority active precise flows, so that the data packets in these precise flows directly hit the cache, and then quickly find the corresponding SRAM flow table entries, significantly reducing the average flow table lookup time and improving the performance of OpenFlow switches. The method of the present invention provides corresponding flow table search speeds for network flows of different priorities: network packets in high priority flows directly hit the TCAM flow table, and quickly find corresponding flow entries; network packets in low priority flows search and hit The Cuckoo cache directly locates the corresponding SRAM flow entry; most packets in the non-priority flow can directly hit the Cuckoo cache, and a small number of packets need to further use the tuple space search method to search the SRAM flow table, and the overall search efficiency is high.
Owner:CHANGSHA NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com