Private data hiding and sharing method
A technology of private data and data, applied in the field of private data hiding and sharing, it can solve the problems of leaking and intersecting feature data, and achieve the effect of protecting the privacy and security of private data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
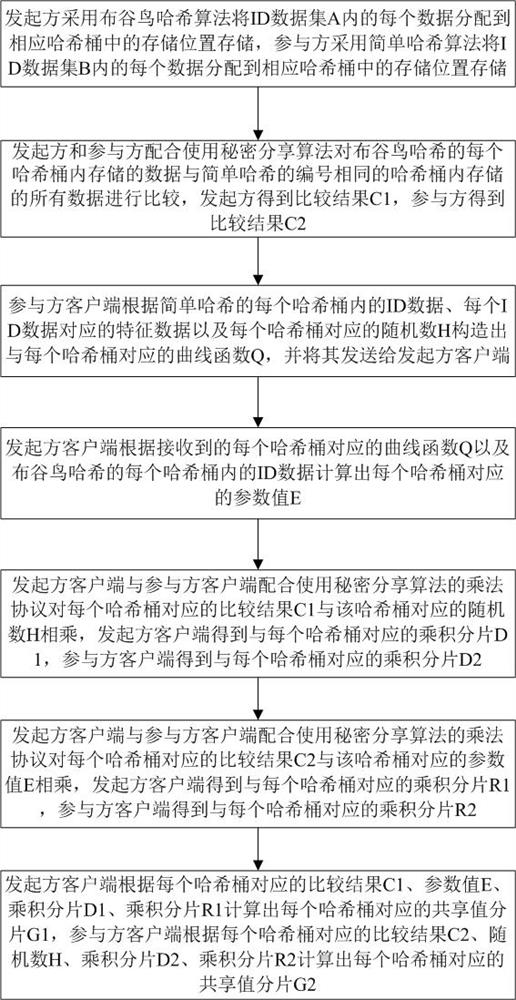
[0058] Embodiment: a private data privacy sharing method of this embodiment, such as figure 1 shown, including the following steps:
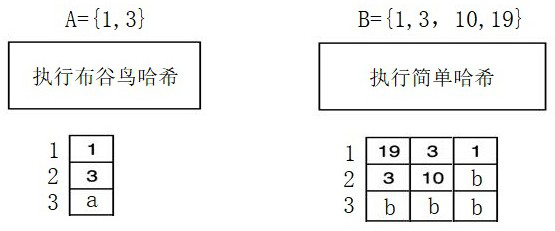
[0059] S1: The initiator client reads the ID data set A in the initiator database to be intersected, and the initiator client uses the cuckoo hash algorithm to assign each ID data in the ID data set A to the corresponding ID data in the cuckoo hash The storage location in the hash bucket is stored. Cuckoo Hash has K hash buckets, each hash bucket has only one storage location, and the storage location that is not assigned to the ID data is stored in the random number a;
[0060] The participant client reads the ID data set B to be intersected in the participant database, and the participant client uses a simple hash algorithm to assign each ID data in the ID data set B to the corresponding hash bucket of the simple hash The corresponding storage location is stored, the simple hash has K hash buckets, each hash bucket has d storage locations, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com