A network deception defense method and device based on host fingerprint hiding
A fingerprint and host technology, used in secure communication devices, digital transmission systems, electrical components, etc., can solve problems such as usability not reaching a practical level, and achieve the effect of easy promotion and implementation and increased difficulty.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be further described below in conjunction with the accompanying drawings.
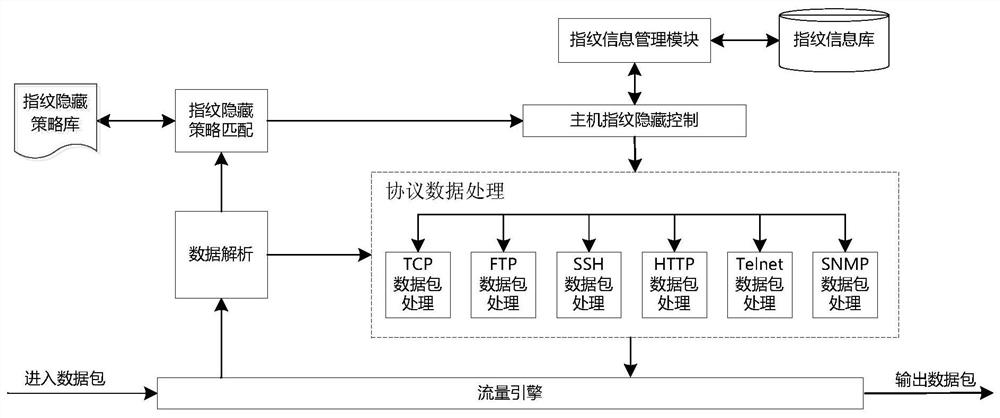
[0033] A network spoofing defense method based on host fingerprint hiding. This method performs fingerprint camouflage and obfuscation processing on the protocol packets sent by the host, and presents the attacker with a limited or even completely concealed or wrong attack surface, resulting in attack complexity and attacker The price increases. The method specifically includes the following steps:
[0034] (1) Analyze the scanning rules of common scanning software and the Banner information of common services to form a host fingerprint information database;
[0035] (2) Formulate a host fingerprint hiding strategy, using the host IP address and protocol type as an index. The hiding strategy includes two fingerprint hiding methods of camouflage and confusion, and the type of false fingerprint information specified for the fingerprint camouflage method;
[0036] (3) A...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com