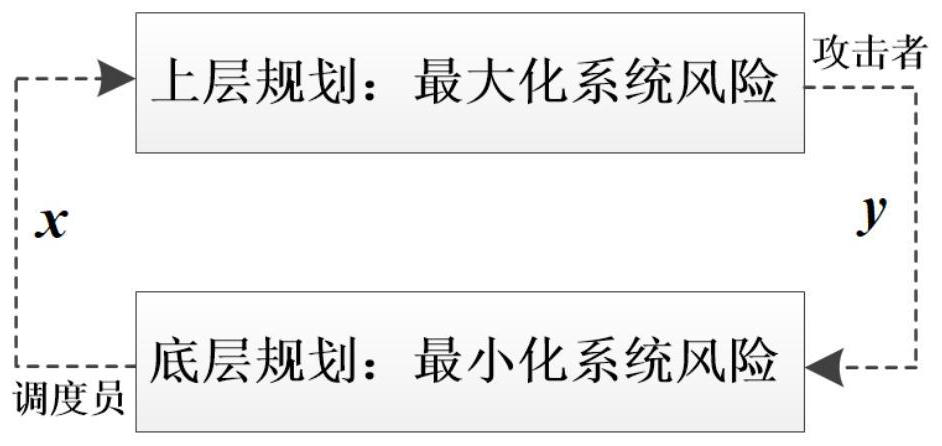
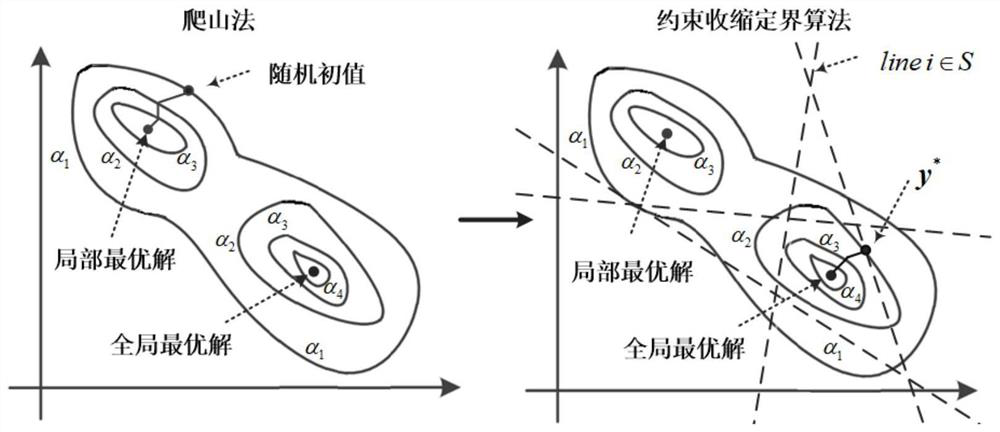
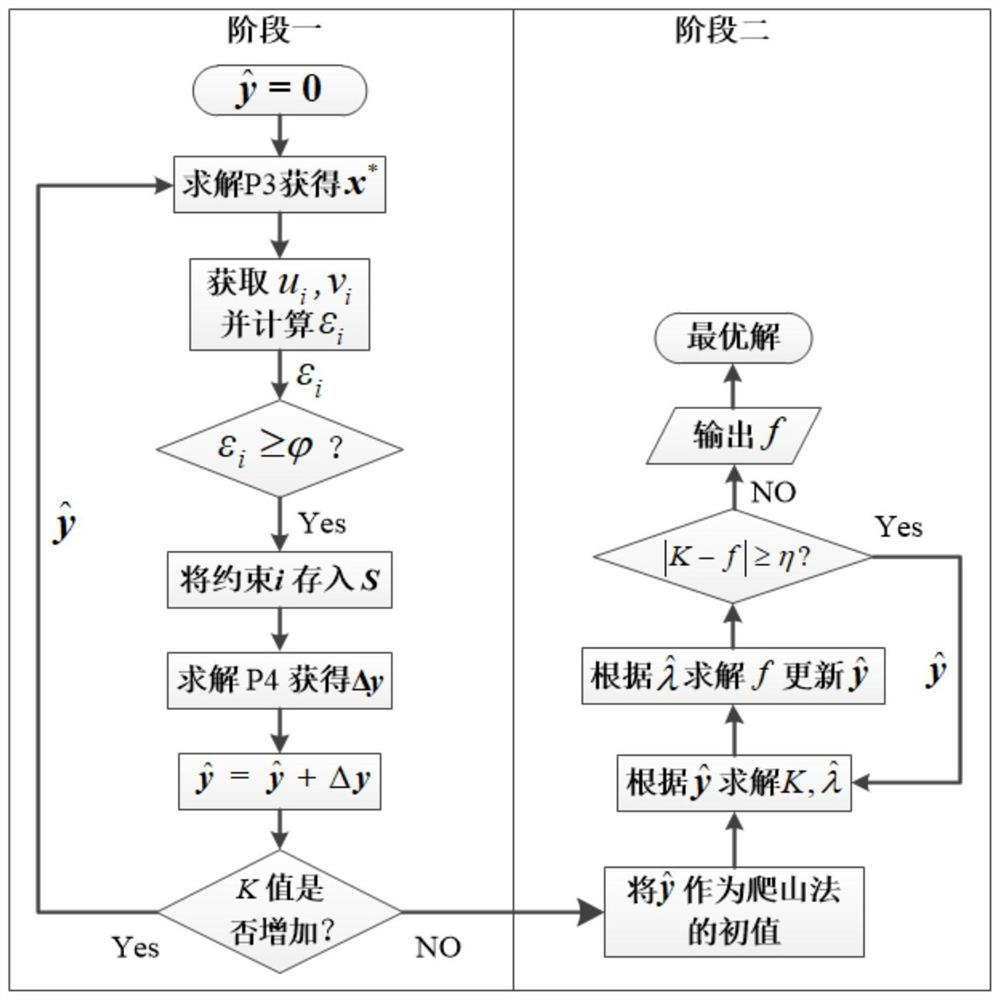
A power network security risk assessment method and system
A power network and security risk technology, applied in the field of power system cyber-physical security, can solve problems such as difficulty in handling large-scale power systems, large gaps in global optimal solutions, and inability to guarantee calculation accuracy. Overcome the effects of computational inefficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0130] In the present invention, we use the IEEE RTS-24 node system to test the established power network security risk assessment model. Without loss of generality, we choose load shedding as the quantitative index of system network security risk. For the IEEE RTS-24 node system, the calculation method based on KKT, the hill-climbing method and the method based on the present invention are used respectively to compare the obtained results. Attached Tables 1-4 give the comparison results.
[0131] Table 1: Test results based on KKT conditional calculation method
[0132] Table 2: Test results based on the hill-climbing method
[0133] Table 3: Test results based on the proposed method of the present invention
[0134] Table 4: the test result (different )
[0135] For the load level in the test system, without loss of generality, we select 1.0, 1.1, 1.2, 1.3, 1.4, and 1.5 times the benchmark load as the load level, and compare the final load shedding and solution time cal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com