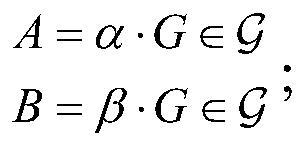Digital signature method and system with security only depending on discrete logarithms
A digital signature and discrete logarithm technology, applied in the field of information security, can solve problems such as long signature data, and achieve the effects of short signature data, high efficiency, and low computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
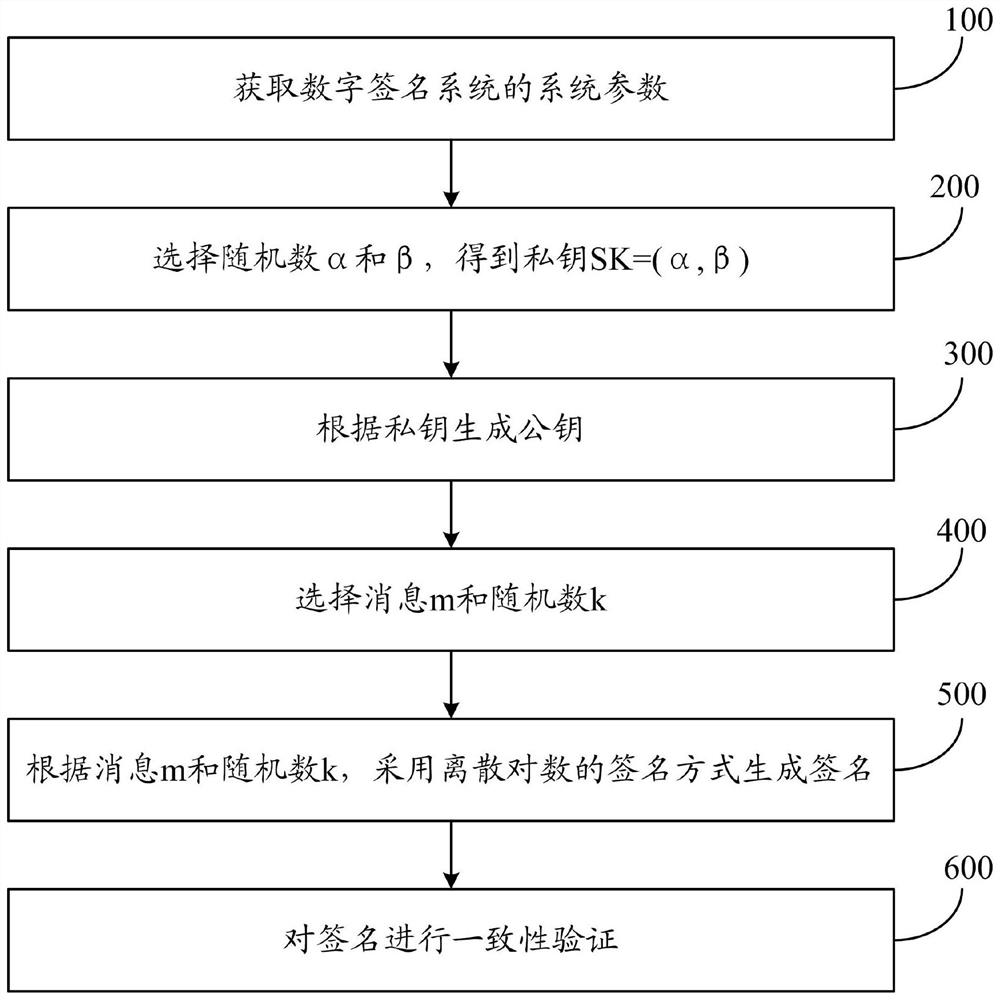
[0081] This embodiment is a digital signature method based on elliptic curve discrete logarithm, and the process is as follows:
[0082] System parameter generation: finite field is F q , the elliptic curve y 2 =x 3 +ax+b in the finite field F q The two parameters above are a, b. point group on elliptic curve The generator of is G, and its order is a large prime number n, where n>2 160 , the system parameters are:
[0083]
[0084] Key generation: choose a random number As private key SK=(α,β);
[0085] Calculated as follows
[0086]
[0087]
[0088] Then the public key is PK=(A, B).
[0089] Signature: choose message m ∈ Z n ,random number Using the formula (x 1 ,y 1 )=k·G to determine the new coordinate point (x 1 ,y 1 ), G is the coordinate point, after calculation with k, a new coordinate point (x 1 ,y 1 ).
[0090] According to the abscissa x of the new coordinate point 1 , using the formula σ 1 =x 1 modn calculates the first parameter σ...
Embodiment 2
[0103] This embodiment is a digital signature based on discrete logarithm, and the specific process is as follows:
[0104] System parameter generation: select a large prime number q,p, where q≥2 160 ,p≥2 1024 , and q|p-1. The generator of the cyclic group G is g, and its order is q, then the system parameters are SP=(G,g,q,p)
[0105] Key generation: choose a random number As the private key SK=(α,β), it is calculated as follows
[0106] A=g α mod p∈G
[0107] B=g β mod p∈G
[0108] Then the public key is PK=(A, B).
[0109] Signature: choose message m ∈ Z n ,random number calculate
[0110] X=g k mod p
[0111] σ 1 =X mod q
[0112] σ 2 =k -1 (α+m+β·σ 1 ) mod q
[0113] If σ 1 = 0 or σ 2 = 0, reselect the random number k and recalculate σ 1 ,σ 2 ;
[0114] If σ 1 ≠0 and σ 2 ≠0, then the signature is determined to be (σ 1 ,σ 2 ).
[0115] Verification: check σ 1 ,σ 2 Whether they all belong to [1,q-1], if not, the signature verification is rej...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com