Network safety state evaluation and attack prediction method
A technology for network security and status assessment, applied in computer security devices, character and pattern recognition, instruments, etc., can solve the problem of lack of assessment of security status in attack phase
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
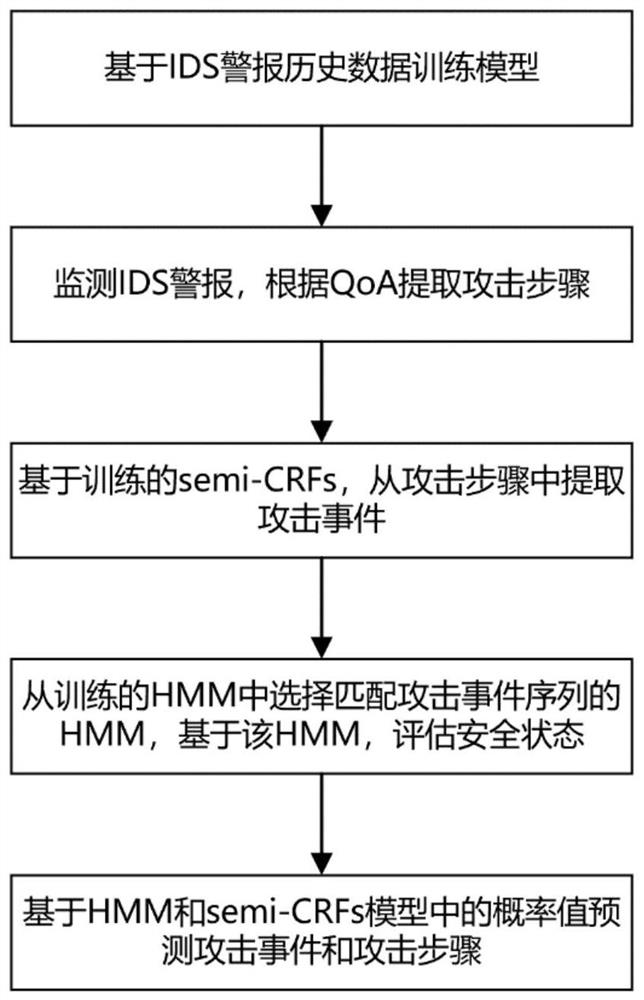
[0076] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0077] In order to verify the method of the present invention and compare it with previous methods, the present invention selects the LLDOS1.0 attack scene in the DARPA2000 data set for experimentation. In this attack scenario, there are five attack stages:
[0078] (1) The attacker scans the network to determine which hosts are up.
[0079] (2) The attacker uses Sadmind ping to find weak hosts running Sadmind service among the active hosts.
[0080] (3) The host is invaded by the Sadmind buffer overflow vulnerability.
[0081] (4) Install DDOS Trojans on the controlled host.
[0082] (5) Use the controlled host to initiate a DDOS attack.
[0083] The invention uses Snort as a network intrusion detection system to generate an intrusion alarm, and uses python to write and implement a program.
[0084] First, the most representati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com