A trusted loading and verification method for streaming microservices based on blockchain
A verification method and micro-service technology, applied in the field of trusted loading and verification of streaming micro-services based on blockchain, can solve problems such as network security risks, achieve the effect of realizing security services and avoiding malicious behaviors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
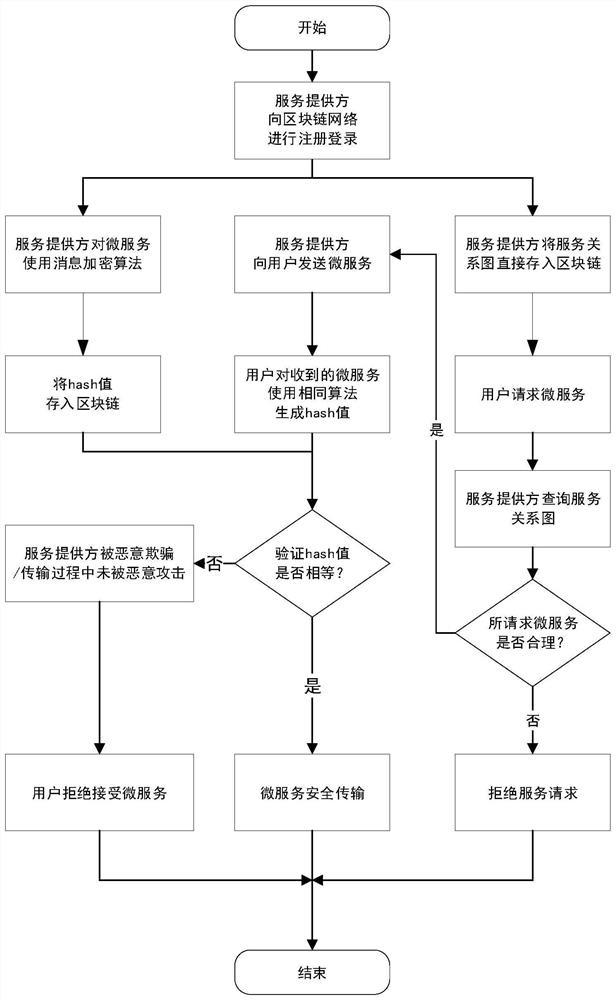
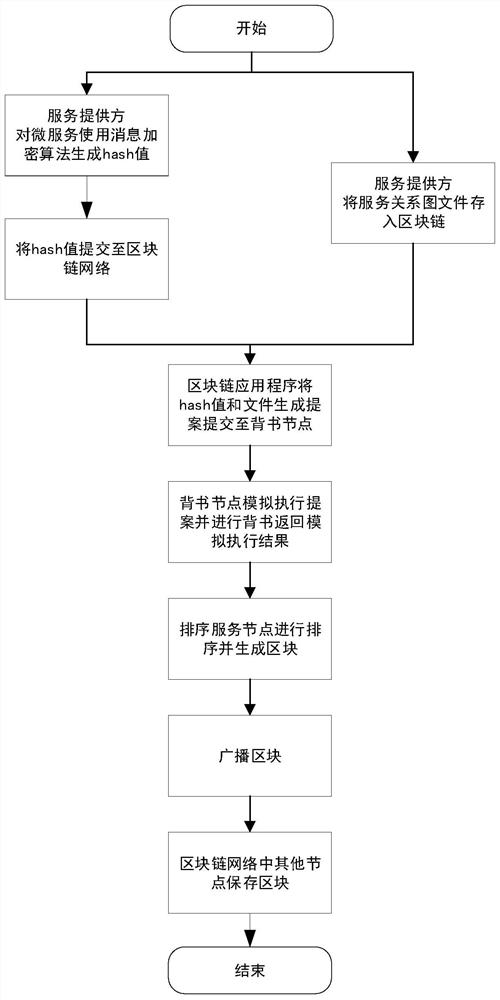
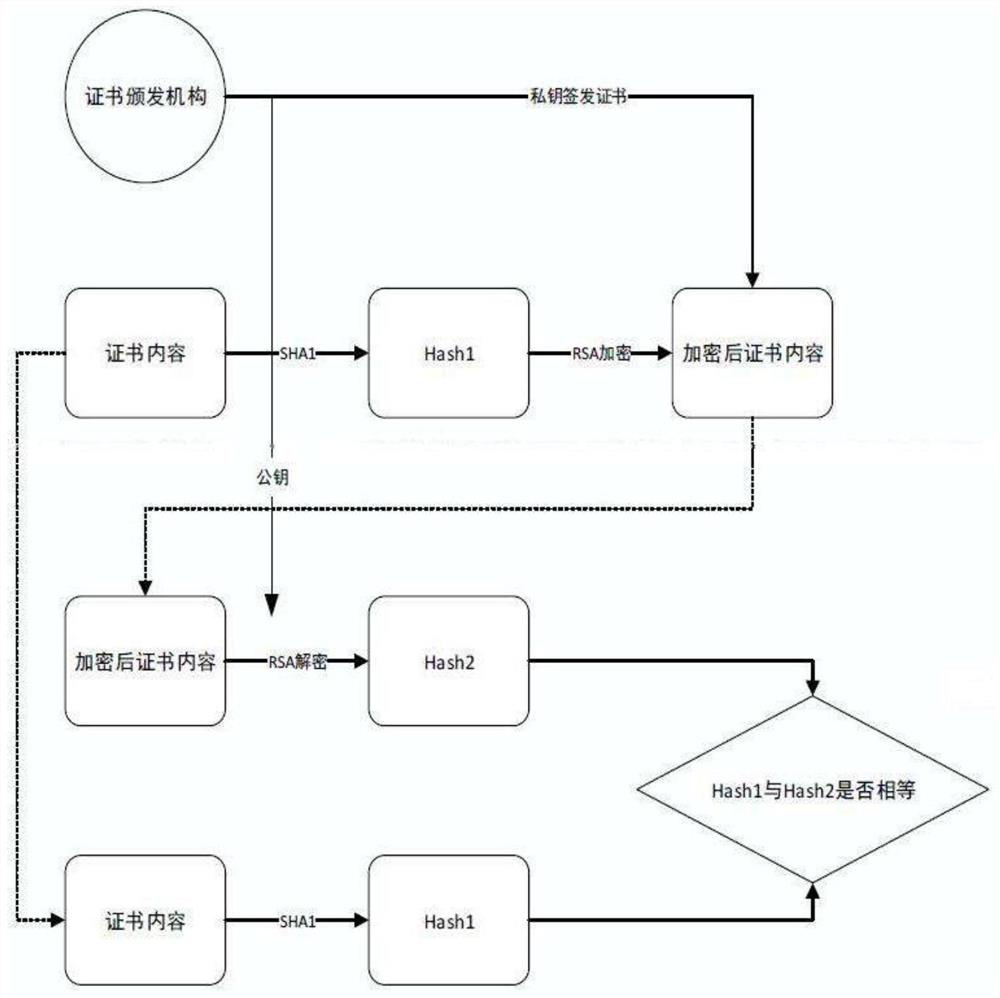
[0072] In the edge computing scenario of block streaming as a service, the divided App application blocks are microservices that are streamed and loaded in cloud service providers and IoT devices. Take the consortium blockchain Hyperledger Fabric as an example:
[0073] After the cloud service provider registers in Fabric's certificate authority and successfully logs in, it first stores the microservice and the microservice relationship diagram in Fabric, including the hash value; before the IoT device requests the service, it can query Fabric to provide the required The service provider of the microservice requests the microservice from the designated cloud service provider;
[0074] When the cloud service provider receives the request, it queries the microservice relationship graph through Fabric, and after verifying the rationality of the microservice request, it securely transmits the microservice executable file to the IoT device. After the IoT device receives the file, i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com