Fraud number identification method based on space-time diagram
A spatio-temporal map, spatio-temporal technology, applied in the information field, can solve the problems of difficult to capture, concealed fraud patterns, and low recognition accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings.
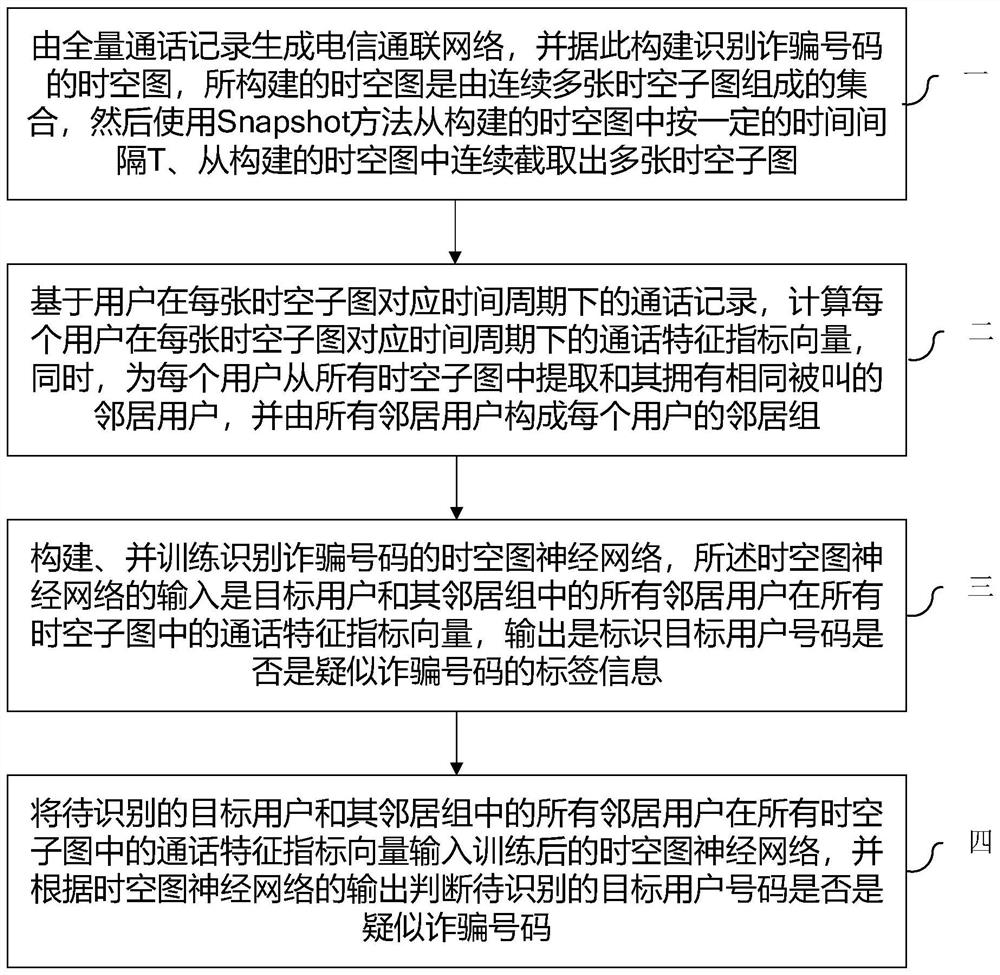
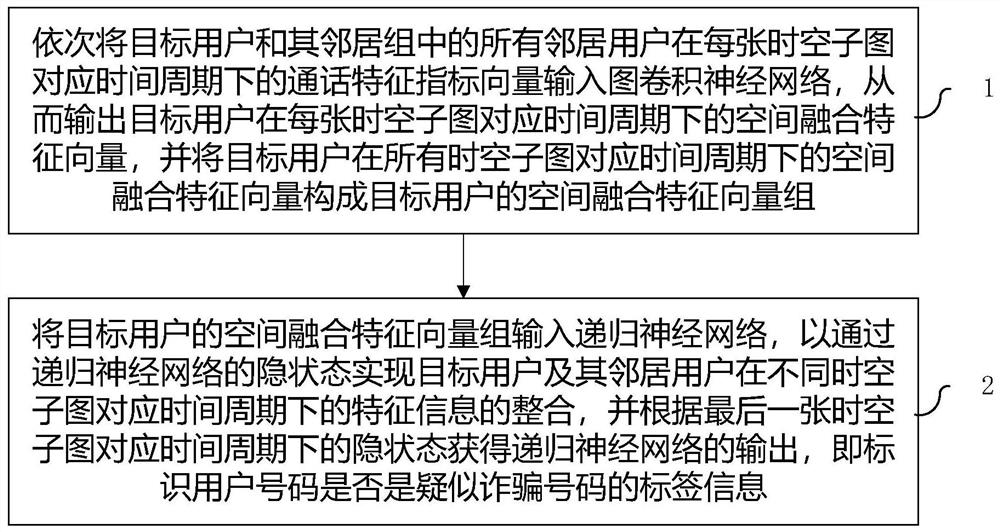
[0019] Such as figure 1 As shown, a method for identifying fraudulent numbers based on time-space diagrams of the present invention includes:
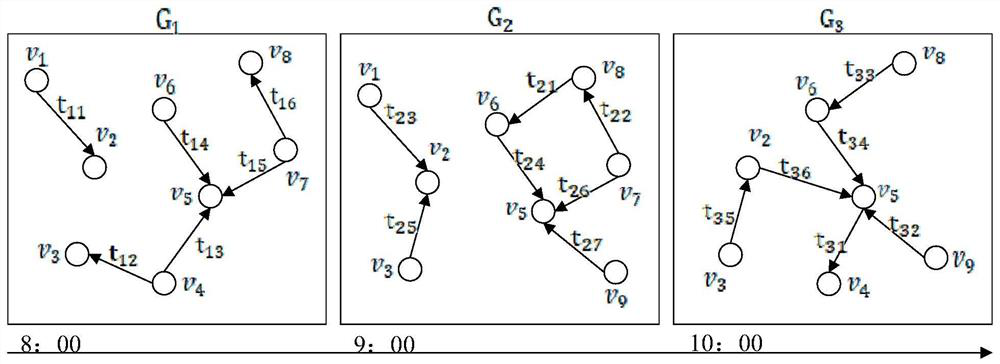
[0020] Step 1. Generate a telecommunication network from the full call record: G={V, E, Y}, and construct a spatio-temporal map for identifying fraudulent numbers based on this. The constructed spatio-temporal map is a collection of consecutive spatiotemporal sub-graphs. Among them, V represents the node set of all communication users, v i ∈V, v i Represents the node of user i, E represents the set of call relations between all user nodes, e ijt =(v i , V j , T) ∈ E, e ijt Represents the call made by user i to user j at time t, Y represents the set of manually labeled user identities, y i ∈Y, y i It is the identity of the ar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com