Traffic mirroring method, device and equipment
A technology of mirroring and traffic, applied in the computer field, can solve problems such as difficulty in extracting business data, difficulty in data reorganization and restoration, and large consumption of computing resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
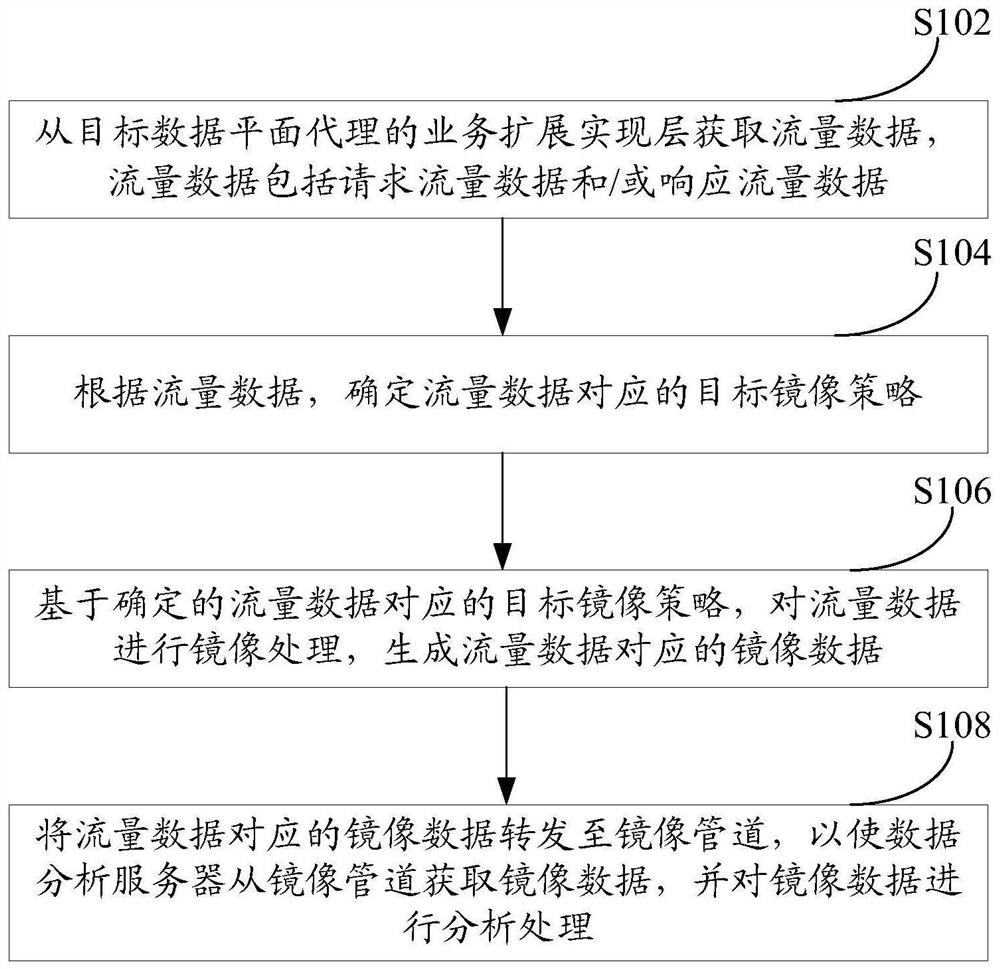
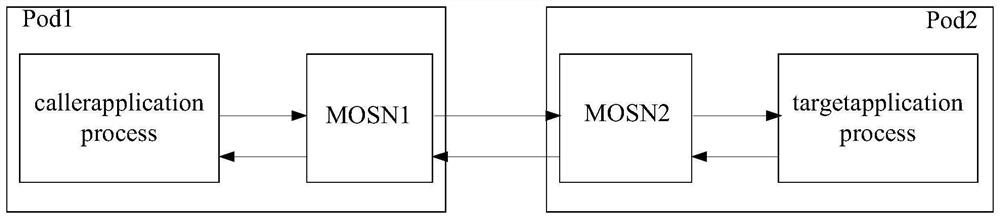
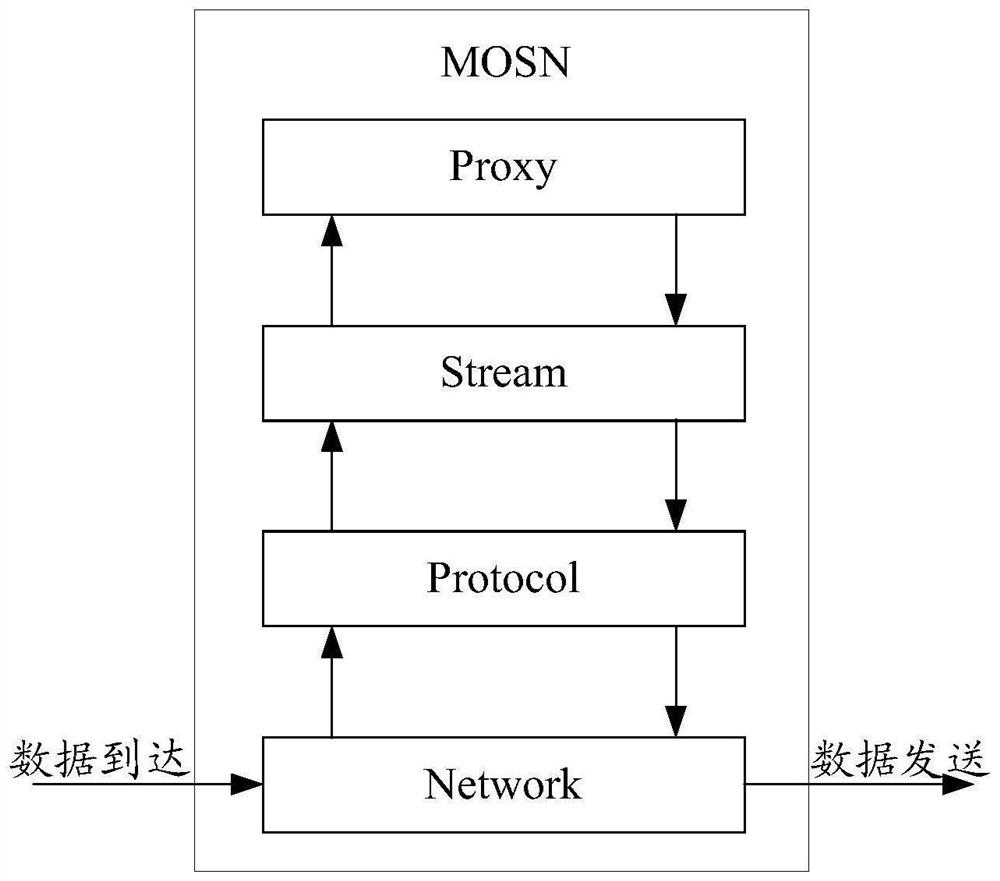
[0019] In order to achieve the purpose of this specification, the embodiment of this specification provides a traffic mirroring method, device and equipment, by obtaining traffic data from the service extension implementation layer of the target data plane proxy, the traffic data includes request traffic data and / or response traffic data , according to the traffic data, determine the target mirroring policy corresponding to the traffic data, and then, based on the determined target mirroring policy corresponding to the traffic data, mirror the traffic data, generate the mirror data corresponding to the traffic data, and convert the mirror data corresponding to the traffic data Forwarding to the mirroring pipeline, so that the data analysis server obtains the mirrored data from the mirroring pipeline, and analyzes and processes the mirrored data. In this way, the traffic data is obtained from the business expansion implementation layer of the target data plane proxy, avoiding the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com