Blockchain user identity supervision method and system considering privacy protection
A technology of privacy protection and user identity, which is applied in the blockchain user identity supervision method and system field that takes into account privacy protection, and can solve the problem that it does not have substantial functions, does not realize the authentication of user identity, and the supervision of big data analysis technology is not simple and effective, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
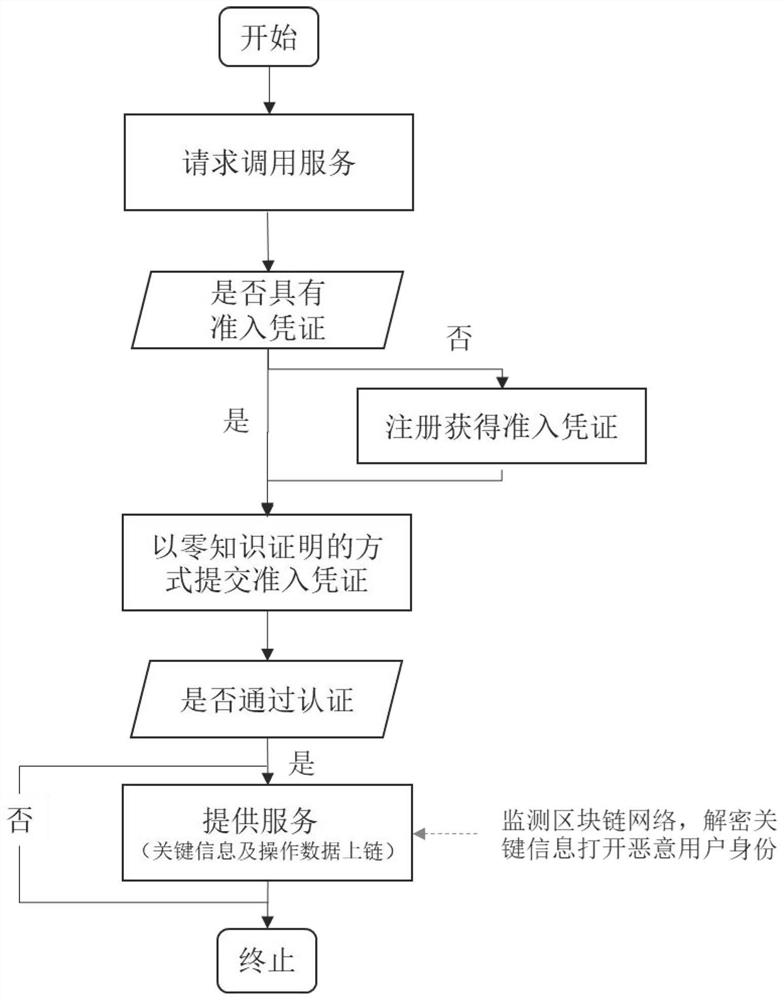
[0052] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail through the following examples.
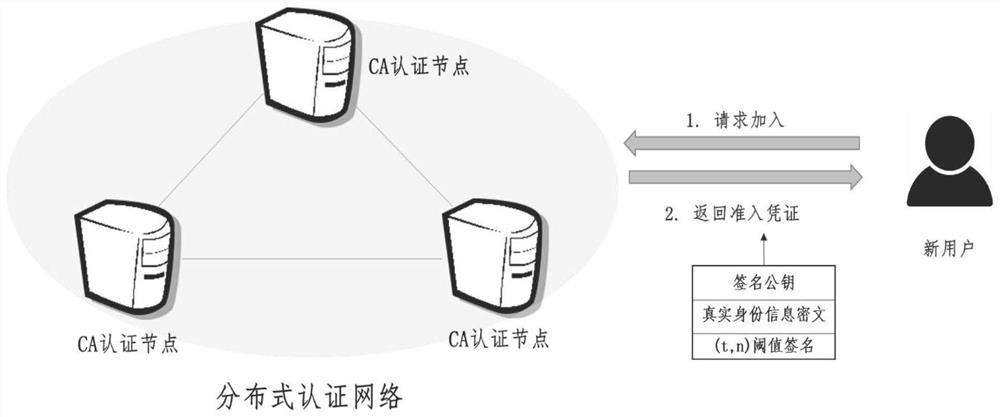
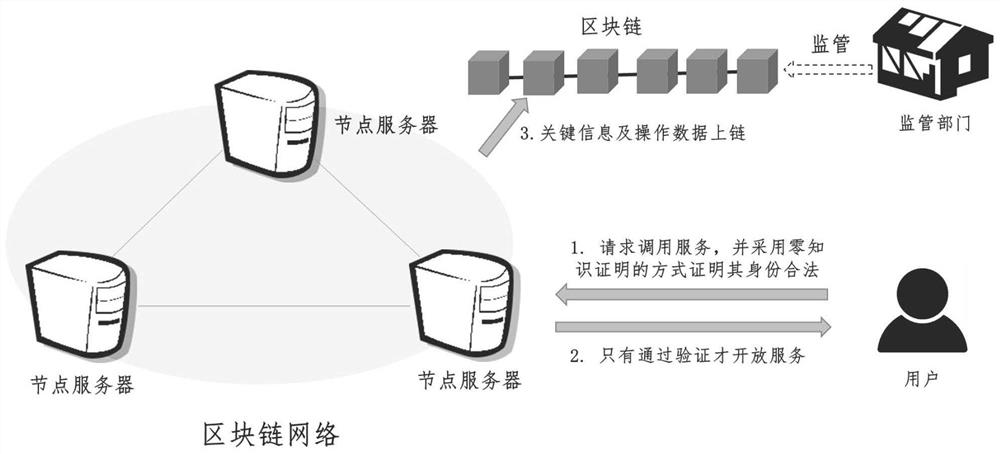
[0053] The privacy protection blockchain user identity supervision system of the present invention includes the following four types of entities: CA authentication node, (block chain) node server, supervision department and (block chain) user;
[0054] 1. The CA authentication node has a signature private key share of the (t,n) threshold signature algorithm: authenticate the user and obtain its real identity information; call the public key encryption algorithm with the public key of the supervision department for the real identity information Encrypt and generate the corresponding ciphertext; run the corresponding protocol with other t-1 CA authentication nodes to generate the (t,n) threshold signature of the ciphertext of the real identity information and send it to the user as an ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com