Blockchain-based offline process evidence obtaining and storing method
A block chain and offline technology, applied in the direction of instrument, platform integrity maintenance, digital data protection, etc., to reduce overhead, improve reliability, and avoid risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
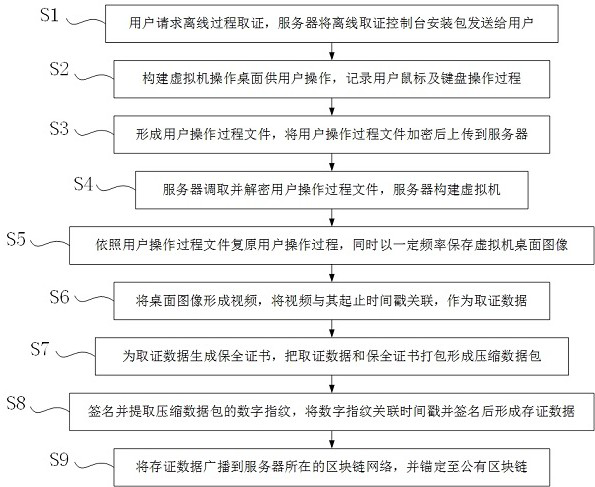
[0016] A blockchain-based offline process evidence collection and evidence storage method, such as figure 1 shown, including the following steps:
[0017] S1. The user requests offline process forensics, and the server sends the offline forensics console installation package to the user.
[0018] The offline forensics console installation package builds a virtual machine operating desktop on the user's computer for the user to operate. The virtual machine operating desktop is a window, and the window provides application icons. When the user clicks on the application icon, the window calls the corresponding application on the user's computer. , and adjust the position and window size of the newly created application window so that it falls into the operating desktop of the virtual machine.
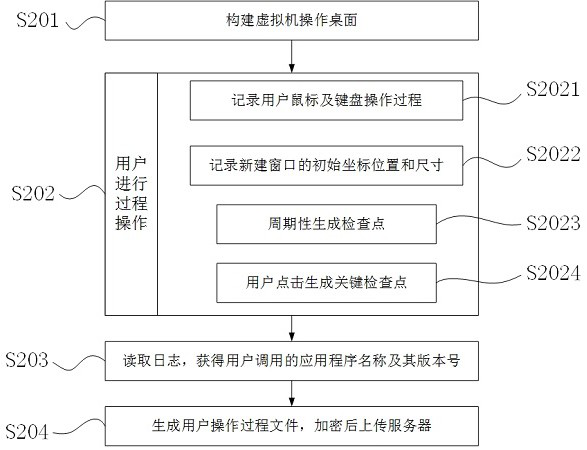
[0019] S2. Build a virtual machine operation desktop on the user's computer for the user to operate, record the user's mouse and keyboard operation process, and record the initial coordin...
Embodiment 2
[0039] A block chain-based offline process evidence collection and evidence storage method, this embodiment further improves the user's operation process collection on the basis of the first embodiment. In this embodiment, the virtual machine operation desktop provides users with a key checkpoint button. When the key checkpoint button is clicked, the desktop image of the virtual machine operation desktop is saved as a key checkpoint, and the user operations before and after the key checkpoint are compared with the key checkpoint. Association, including the key checkpoints of the associated user's previous and subsequent operations into the user operation process file upload server, when the server restores the user's operation process, check whether there is a desktop image that matches the key checkpoint between the associated user's previous and subsequent operations, and if so If the key checkpoint passes, otherwise, the key checkpoint fails, and the user is notified that th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com