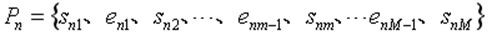Defense effectiveness evaluation method applied to network target range
A technology for performance evaluation and shooting range, applied in electrical components, transmission systems, etc., to solve problems such as lack of defense quantification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
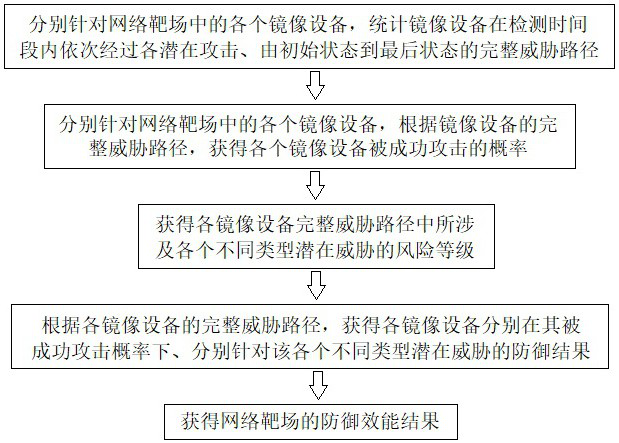
[0045] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings.
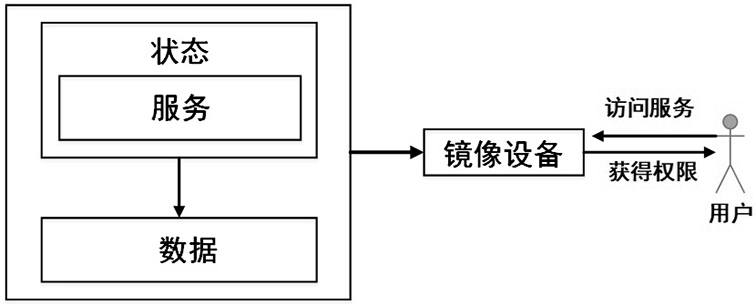
[0046] The network shooting range is composed of several mirroring devices connected to each other, and each mirroring device provides functional services to other mirroring devices through the network, such as figure 1 As shown, the mirrored equipment in the network shooting range is the carrier of a series of data collections, and the user accesses the functional services of the equipment in the system through the network.
[0047] For each mirrored device in the network range, use the set Represents all data contained on a mirrored device.
[0048] The mirroring device provides an interface for interacting with the outside through the functional services provided by the Service. A mirroring device may contain several functional services. Each of its services is denoted by S, and the collection of data used and affe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com