Decentralized Internet-of-Things cross-domain access authorization method and system
A decentralized and Internet of Things technology, applied in the field of Internet of Things and network security, can solve problems such as complex information flow between application domains, difficult maintenance, and unreadable authorization information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0082] see Figure 1-2 .
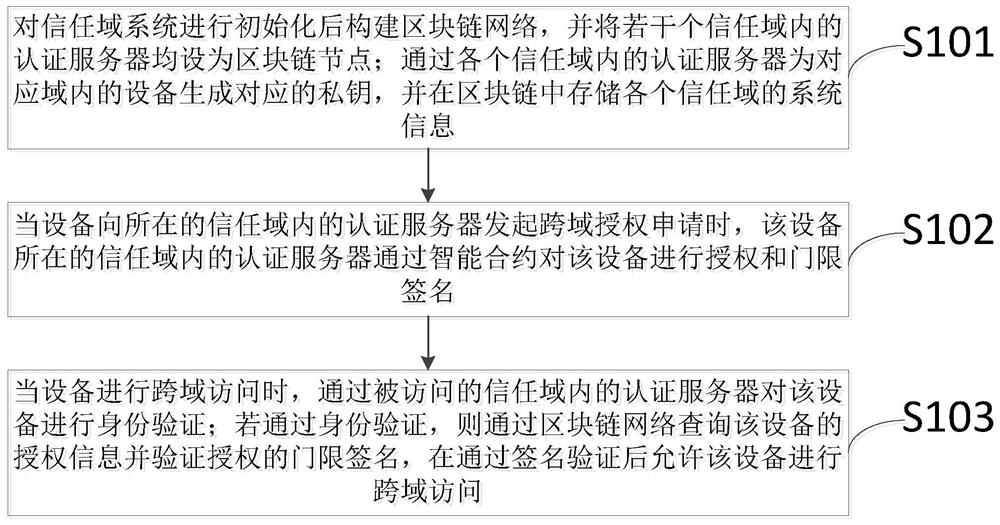
[0083] Such as figure 1 As shown, this embodiment provides a decentralized Internet of Things cross-domain access authorization method, at least including the following steps:
[0084] S101. Build a blockchain network after initializing the trust domain system, and set the authentication servers in several trust domains as blockchain nodes; generate corresponding private keys for devices in corresponding domains through the authentication servers in each trust domain, And store the system information of each trust domain in the blockchain;
[0085] In a preferred embodiment, the step S101 is specifically:
[0086] Initialize the system parameters of the trust domain through the authentication server, including the additive cyclic group and multiplicative cyclic group used to initialize the system parameters, and the hash function used to generate the identity;
[0087] Generate the system master key through the authentication server, and generate...
no. 2 example
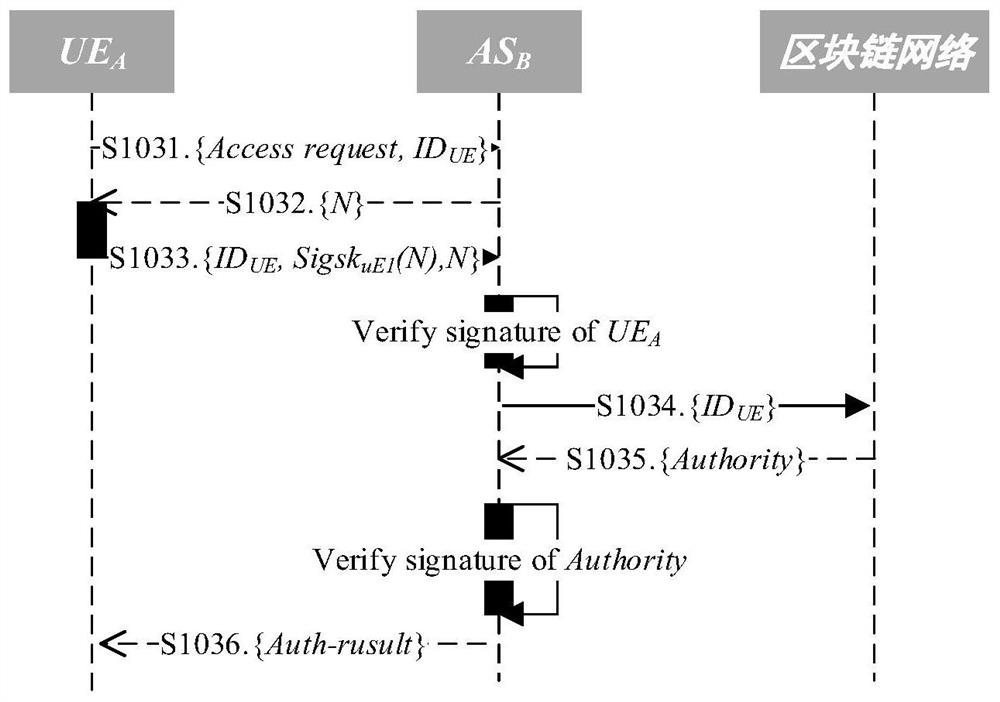
[0152] see Figure 3-4 .
[0153] Such as image 3 As shown, this embodiment provides a decentralized Internet of Things cross-domain access authorization system, including:
[0154] The trust domain system initialization module 100 is used to build a blockchain network after initializing the trust domain system, and set the authentication servers in several trust domains as blockchain nodes; The device generates the corresponding private key and stores the system information of each trust domain in the blockchain;
[0155] The authorization issuance module 200 is used to authorize and sign thresholds for the device through the smart contract when the device initiates a cross-domain authorization application to the authentication server in the trust domain where the device is located;
[0156] The cross-domain access module 300 is used to authenticate the device through the authentication server in the accessed trust domain when the device is accessed across domains; if the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com