Protocol conflict matching method and system, storage medium and computer equipment
A matching method and protocol technology, applied in transmission systems, electrical components, etc., can solve problems such as difficulty in analyzing characteristics between protocols, manual intervention, and incompatibility between protocol A and protocol B.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
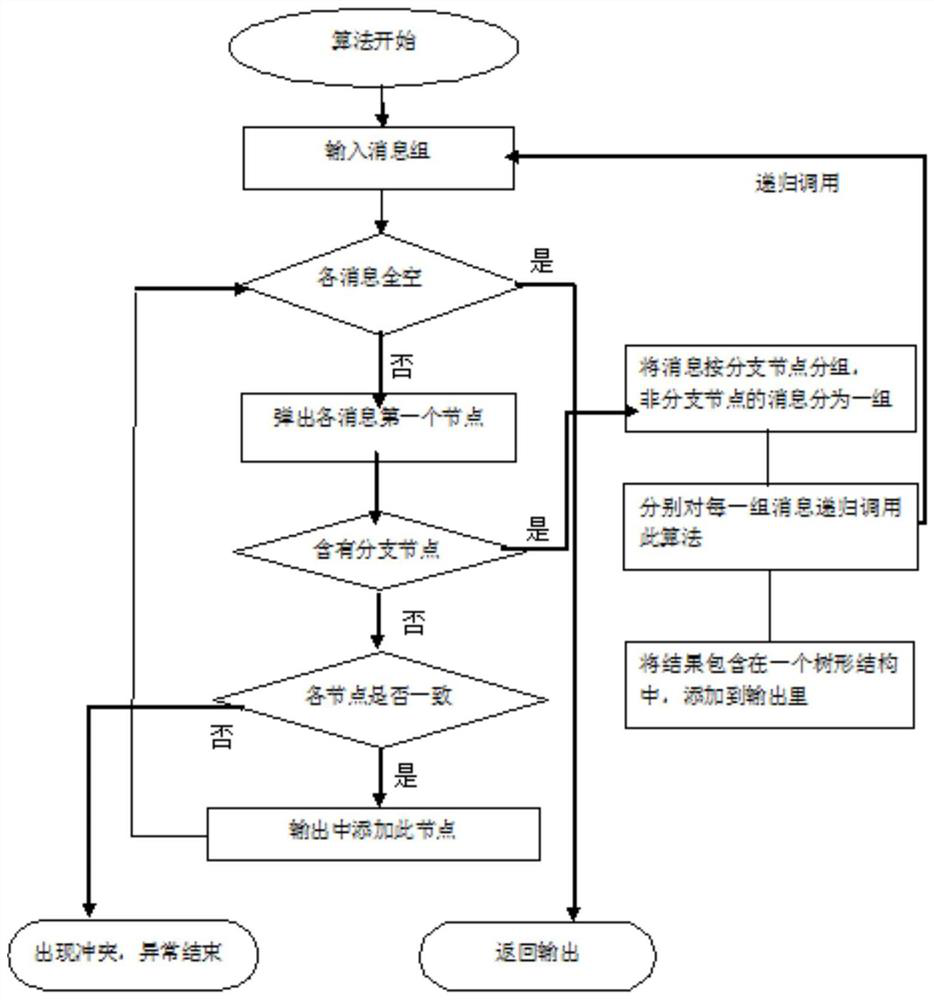
[0024] Such as figure 1 As shown, in the present embodiment, the protocol conflict matching method of the present invention is realized by using a structured protocol parser syntax tree generation algorithm, which mainly includes the following steps:
[0025] Step S1. Define a data protocol representation method based on action nodes, so that each action corresponds to a node in the syntax tree of the protocol parser.
[0026] In this embodiment, use the node Int8: a to read an 8-bit integer number from the data source and name it a; use the node Int16: a to read a 16-bit integer number from the data source and name it a; use The if statement in a high-level programming language, that is, the node if($0>1), judges whether the value of the 0th node of the message is greater than 1, where $0 represents the value of the 0th node.
[0027] Step S2, dividing the nodes in step S1 into "branch nodes" and "non-branch nodes".
[0028] In this embodiment, the nodes Int8 and Int16 are ...
example 1
[0058] Example 1. Failed to generate syntax tree
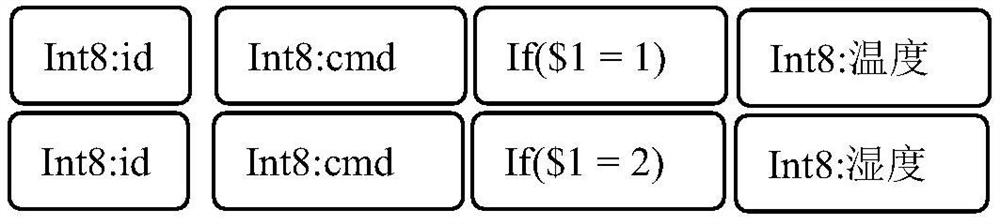
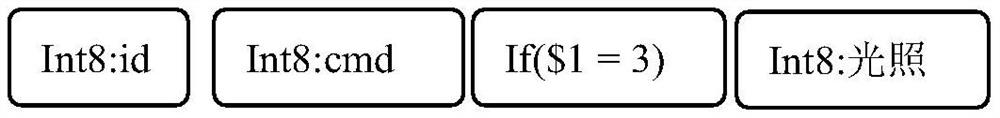
[0059] Merge Protocol A, Protocol B, and Protocol C into one message group (adjust the order of the messages for the next demonstration, but in fact the order of the messages is irrelevant) First, enter the synthesized message group as shown in Table 5:
[0060]
[0061] table 5
[0062] Each message (each row) in this group of messages has a node, so it is not all empty; the 0th node of each row of messages pops up, as shown in Table 6, if a row is already empty, then define a node that represents empty Replace the pop-up node, or directly judge that there is a conflict, and end the algorithm.
[0063]
[0064] Table 6
[0065] Because the 0th node does not contain an if node, it does not contain a branch node; and because the pop-up nodes are all Int8:id, they are consistent and there is no conflict; so add this node to the output.
[0066] Then, enter the remaining nodes in the synthesized message group, as shown i...
example 2
[0090] Example 2, normal generation of syntax tree
[0091] In the case of failure to generate the syntax tree, protocol C is removed, only protocol A and protocol B are merged, and protocol A and protocol B are merged into one message group.
[0092] First, enter the merged message group, see Table 14:
[0093]
[0094] Table 14
[0095] Each message (each row) in this group of messages has nodes, so it is not all empty; the first node of each row of messages pops up, see Table 15:
[0096]
[0097] Table 15
[0098] Because the first node does not contain an if node, it does not contain a branch node; and because the pop-up nodes are all Int8:id, they are consistent and there is no conflict. Add this node to the output.
[0099] Then, enter the remaining nodes, see Table 16:
[0100]
[0101] Table 16
[0102] Since each message (each row) in this group of messages has a node, it is not all empty; the first node of each message pops up, see Table 17:
[0103...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com